2020 was dominated by surviving the pandemic, be it mentally, physically, or professionally. 2021 has been a year of rebirth and a slow return to all the things we didn’t even realize we missed, but human-kind hasn’t been the only group being revitalized. Cyber criminals have also had a renaissance of sorts, developing new tools and tactics for cyber-attack as fast as we can create new protections.
Cyber criminals were not above taking advantage of the pandemic, adapting, and even thriving through the outbreak, preying on people’s fears, and cashing in on their attempts to buy some peace of mind. Governments were attacked, hospitals were overwhelmed, and the rest of us were forced into various stages of lockdown.
Working remotely followed, allowing (or forcing depending on your point of view) many to realize a dream they had dreamed many times, but with all the joyful reality we normally find when woken from dreams. Now a desk space, quiet time, and long, uninterrupted hours to focus on work were in short supply, while distractions, scams and devastating ransomware attacks were almost hourly.
READ SANGFOR 2021 MALWARE REPORT NOW!
What Was the Cost of Cybercrime?
Did you know that cybercrime costs the global economy around $1 trillion USD, 50% more than 2018 predictions? The average cost of a data breach in 2020 was $3.86 million, rising to $4.24 million in 2021. Data has been the main target, with data breaches costing $50 million on average, but reaching as high as $392 million. It’s obvious that cyber-threat is growing and not going away.
What Are the Top 5 Threats to Working Remotely?
The top 5 threats to remote workers, and thus, their employers, in 2021 are:
- Phishing Schemes. People have become less diligent in checking email working remotely than before the pandemic.
- Weak Passwords. Some things never change.
- Unencrypted File Sharing. Sensitive data is being shared insecurely over public and home networks.
- Insecure Home Wi-Fi. It is very difficult for organizations to secure an employee’s home network which was likely wide open to begin with.
- Working from Personal Devices. It is very difficult for organizations to secure an employee’s private laptop or mobile device.
Organizations educating employees is the easiest way to decrease risk, as most of these issues stem from unsafe or lax browsing or internet practices. But there are many risks to remote employees that are out of an employer’s control.
Combat Cyber-Threat Misconceptions
We are increasingly aware of cyber-crime but are learning just enough to be dangerous. There are so many common misconceptions that people have about cyber-attack.
- Paying the ransom means you will have your data returned quickly and in full. Sadly, many cyber criminals are selling stolen data on the dark web, even before the ransom deadline has passed, hoping for a double pay day; this is called Double Extortion. As with the famous Colonial Pipeline attack, after paying and receiving the decryption keys, decryption proved to be much slower than using backups to restore systems.
- Backing up data makes you immune to ransomware or malware consequences. Nope, sorry! Ransomware and malware attack in different ways and will target your online back-ups. Poor configurations might even lead attackers to your back-ups.
- Once a ransomware attack is over, it really is over. Ransomware and malware can lie dormant in your system forever if it’s not removed correctly. Ransomware usually has two parts: the “stub” software that originally infects a system and the ransomware “payload” that does all the really malicious stuff like encrypting data. Most ransomware “removal” finds and deletes the payload (which is the easy part), but rarely the stub which can then download the payload again. The only way to assure that an attack is over, is to enlist the professionals.
Data is the new “Oil”
Data breaches have lasting financial effects on hospitals,” says Forbes, “More than 90 percent of all healthcare organizations reported at least one security breach in the last three years.” Our data is becoming our most valuable resource, and cyber attackers have noticed.
Endpoint Security is Key
According to Statista, there are about 21.5 billion interconnected devices in the world. Cyber attackers have seen their opportunity in the millions of vaguely protected devices and are taking advantage. Endpoints, whether laptops, servers, or mobile devices need security software running on them to detect attacks, malicious software being downloaded and installed, or malware that is running and attacking other systems. Your consumer or free version of anti-virus (AV) software is not designed to stand up to ransomware. You need enterprise grade protection with AI to combat the new AI-enabled malware.
READ SANGFOR 2021 MALWARE REPORT NOW!
Sangfor Anti-Ransomware Solution
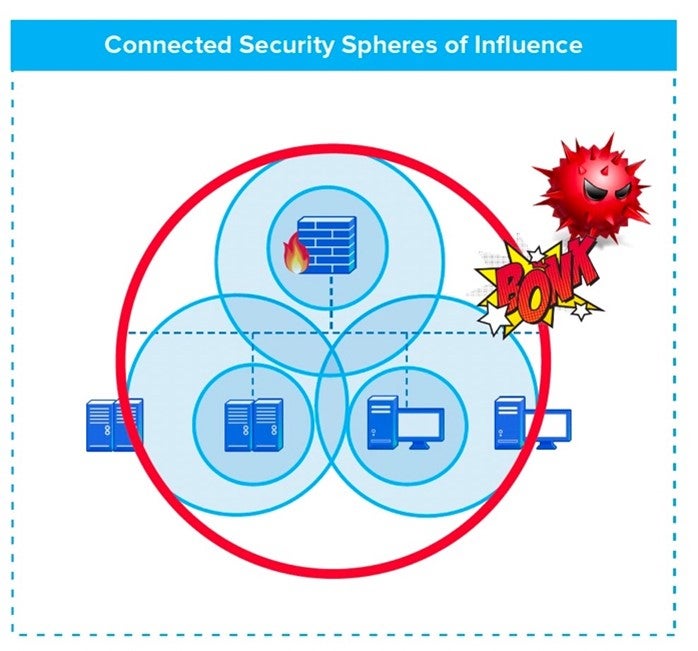
Ransomware is over 95% successful. Ransomware uses a specific sequence of events called a “Kill Chain,” to infect, encrypt, and spread. This Kill Chain is controlled by AI to find and exploit the gaps between different security point product spheres of influence making it easy for ransomware to breach and infect.
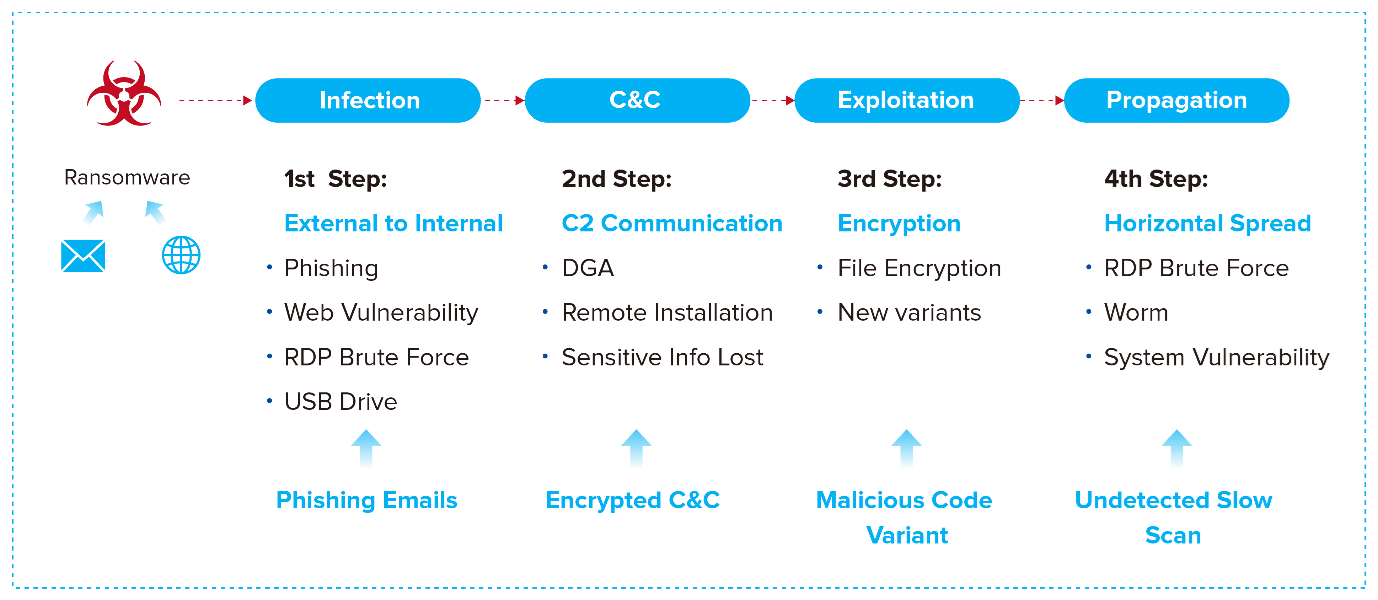
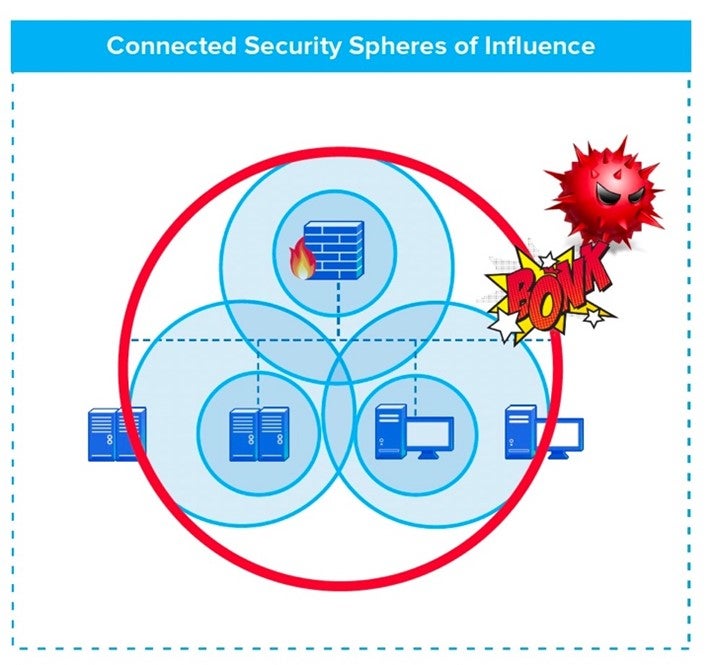
Organizations have been lulled into a false sense of security with network firewalls, email gateways, and anti-virus/anti-malware solutions. A more holistic anti-ransomware solution is needed to completely break the cycle. The Sangfor Security Solution for Ransomware provides an innovative strategy that successfully mitigates ransomware attacks, by overlapping security spheres of influence and breaking every step in the Kill Chain.
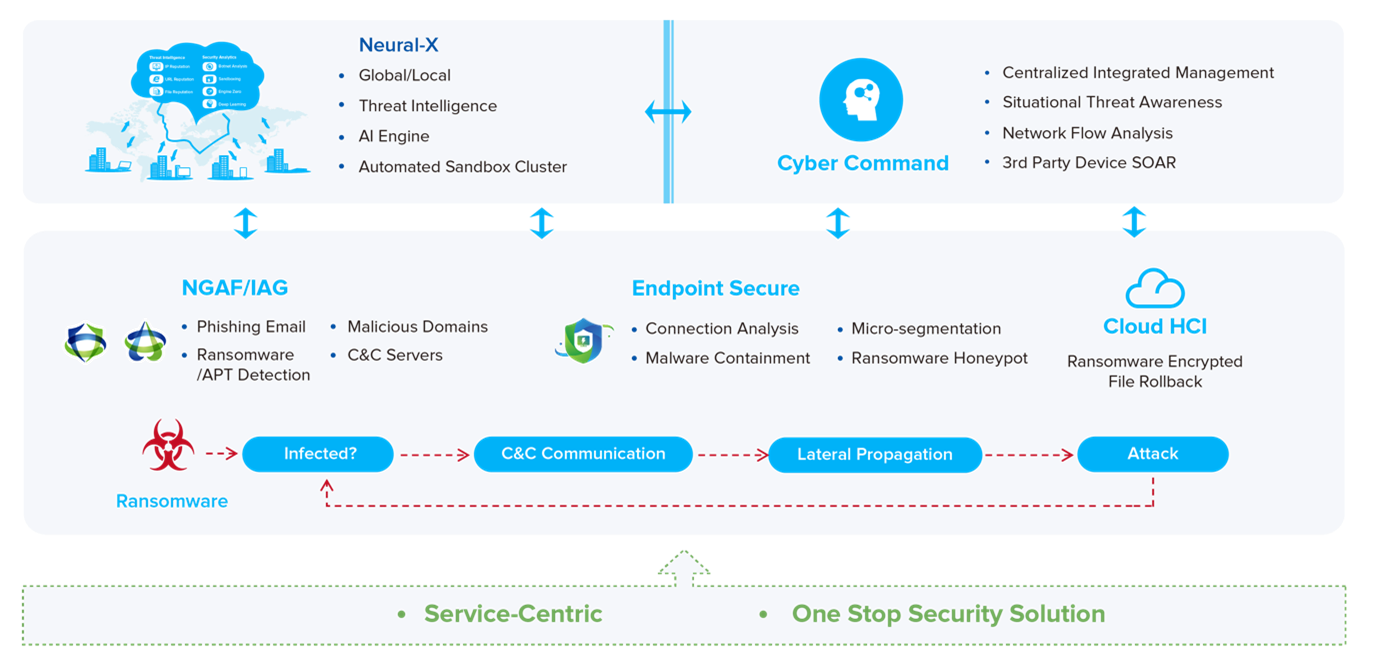
Sangfor’s Security Solution for Ransomware is the only complete, holistic security solution to prevent and mitigate ransomware attacks in real-time. No other solution can impact every step in the ransomware kill chain and no other solution is modular enough to be tailored to the requirements and budget of the organization.
- Only solution that is proven to block every step in the ransomware kill chain
- Only solution with direct integration between firewall and endpoint agents and not using TI or management console as go-between
- NGAF can block C2 communications and lateral propagation based on direct endpoint input
- NGAF can verify that endpoint is infected based on C2 communications
- Only solution with a ransomware honeypot that effectively stops the encryption process and identifies the controlling application network wide
Frequently Asked Questions (FAQs)
What is Malware?
Malware (malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. Malware includes various attack methods and types, including spyware, adware, ransomware, rootkits, worms, viruses and keyloggers, among countless others.
What is the best protection against malware?
In general, the best protection against malware is education, and the ability to think critically about risk when you see it. Follow these tips for the best and most common-sense approach to malware protection.
- Keep your computer and software updated
- Use a non-administrator account whenever possible
- Think twice before clicking links or downloading anything
- Be careful about opening email attachments or images
- Don't trust pop-up windows that ask you to download software
- Limit your file-sharing
- Avoid untrusted or insecure websites
- Use a long, difficult password including a phrase, numbers and symbols.
- Use different passwords for all accounts, and make use of an encrypted password manager to keep track of them.
What are the best methods for malware detection?
Signature-based detection, is where each file is analysed and added to a database, for recognition in the event of any further malware attacks. This is no longer the go-to solution, as modern malware is designed to evade this detection. Threat hunters now use other techniques, including several Next-Gen and Other Malware Detection Techniques and Blocking Methods:
- AI/Machine-Learning-Based Static Analysis
- Application Blacklisting and Whitelisting
- Endpoint Detection and Response
How to Prevent Malware Attacks?
We know that stopping a malware or ransomware attack is difficult, but there are several easy ways to reduce the overall risk of attack, without any investment and with very little time needed. Sangfor Technologies is a global leader in network security technology, and based on years of in-depth research, suggests reading and memorizing Sangfor's Top Security Tips for malware prevention!
- Deploy email mitigating measures
- Install Anti-virus software.
- Regularly update software.
- Only buy Apps from trusted sources.
- Don't click on suspicious links or download attachments from unknown sources.
- Install Firewall.
For more information on the latest in cyber security and malware, read the Sangfor 2021 Malware Report, published by Sangfor Technologies, in conjunction with Holger Schulze, CEO and Founder of Cybersecurity Insiders. Visit Sangfor online for information on their vast suite of security, cloud and infrastructure solutions for the APAC region and the world!






