
Recently, a new version of ransomware appeared globally with the suffix "Yanluowang." According to international security researchers, Yanluowang ransomware accesses the user's intranet AdFind domain information query tool for lateral network detection and collects intranet endpoint information to prepare for follow-up invasion and expansion of the infection of intranet shared volumes.
Yanluowang ransomware scans and maps endpoint system processes and files before encryption. The ransomware records all processes and remote machine names in processes.txt, then terminates the endpoint security processes according to data in txt file, including SQL processes and the backup solution Veeam. Yanluowang then encrypts the files on the system, modifying the file extensions to “.yanluowang” after encryption, and leaving a blackmail letter.
With vast knowledge and experience with mitigating new ransomware strains, Sangfor Endpoint Secure has a complete plan for mitigating each link of the ransomware kill chain.
Source-RDP Remote Login Protection
Sangfor's Endpoint Security team has constructed and tested hundreds of different ransomware attack scenarios, by tracing and analysis of massive ransomware attack events. Remote desktop login was found to be the most common breach method used for ransomware attacks, and the attack usually has the following characteristics:
- The attacker uses information from the earlier intranet reconnaissance to perform RDP brute force login on target hosts. Logins are usually in the early morning, holidays, or other idle periods when they are not easily detected by security monitoring personnel.
- The internal network is infiltrated through the target host, and hacker tools are used to conduct security countermeasures against anti-virus software. Even if security software is deployed on the internal network, it cannot guarantee protection against artificial intelligence-based countermeasures by attackers.
- The ransomware then evades and bypasses any security software.
Since an attacker has the freedom to operate at will after a successful intrusion, remote desktop login protection is particularly important.
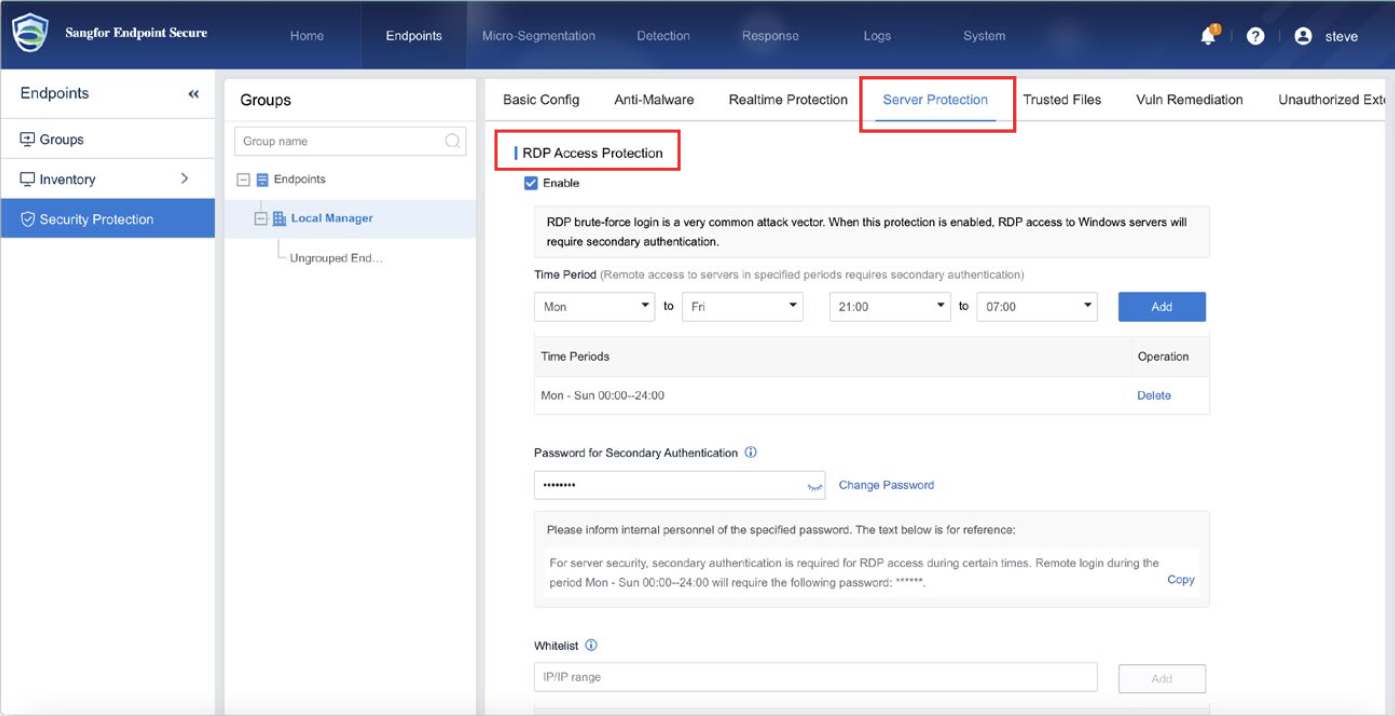
Sangfor Endpoint Secure has built-in remote login protection for remote desktop login ransomware attack scenarios. After enabling it, you can configure the remote login protection to require secondary authentication during scheduled times.
Even if attackers log into the server via remote desktop, they still need to provide the secondary verification password in a following window to operate. This not only blocks ransomware attacks from malicious sources, it also effectively defends against other attacks implemented through a remote desktop.
Internal Network Isolation - XDDR prevents lateral spread
To increase the probability of users paying the ransom, in addition to data theft and encryption, ransomware gangs conduct horizontal detection of users' intranets in the early attack stages to expand the amount of infection as much as possible throughout the organization.
Sangfor’s XDDR security integration between Endpoint Secure, Cyber Command and NGAF can quickly respond to high-risk events on endpoints, block designated IPs, isolate compromised hosts, and prevent further horizontal spread of malware.
Endpoint Secure collects security logs from the host, facilitating the analysis, traceability and evidence collection capabilities of Cyber Command and the next-generation firewall NGAF to detect and kill network threats to endpoints.
Cyber Command collects data from the network security detection probes one the intranet network, identifies potential threats and attacks on the network side, scans and kills them on the endpoint side, then issues a coordinated response strategy to the firewall to reinforce perimeter defense.
NGAF provides internal and external network perimeter defense and full traffic analysis. Once multiple C&C communications are detected in the incoming and outgoing traffc, the firewall will use XDDR to analyze the host correlation and synchronize the security data with both Endpoint Secure and Cyber Command to develop a coordinated network and endpoint response.
Security administrators can use the XDDR integration between Endpoint Secure, Cyber Command and NGAF to quickly find common ransomware behaviors, such as abnormal port scanning & communications and brute force cracking, and then implement automatic response to the threats. If a ransomware playbook scenario is triggered, the designated IP can be blocked to prohibit inbound and outbound traffic. All risky ports of the risky are automatically blocked, and the host is immediately isolated and issued a scan and kill order to prevent the virus from spreading horizontally.
Ransomware Detection and Killing - Multi-Engine Real-Time Protection
Sangfor Endpoint Secure's real-time monitoring uses multi-engine AI-based detection methods including Engine Zero’s artificial intelligence malware detection engine, Neural-X cloud-based detection and sandboxing, and local reputation databases.
Endpoint Secure detects malicious software through both static file analysis and dynamic behavior analysis to quickly fingerprint and identify common active ransomware families as well as unknown threats.
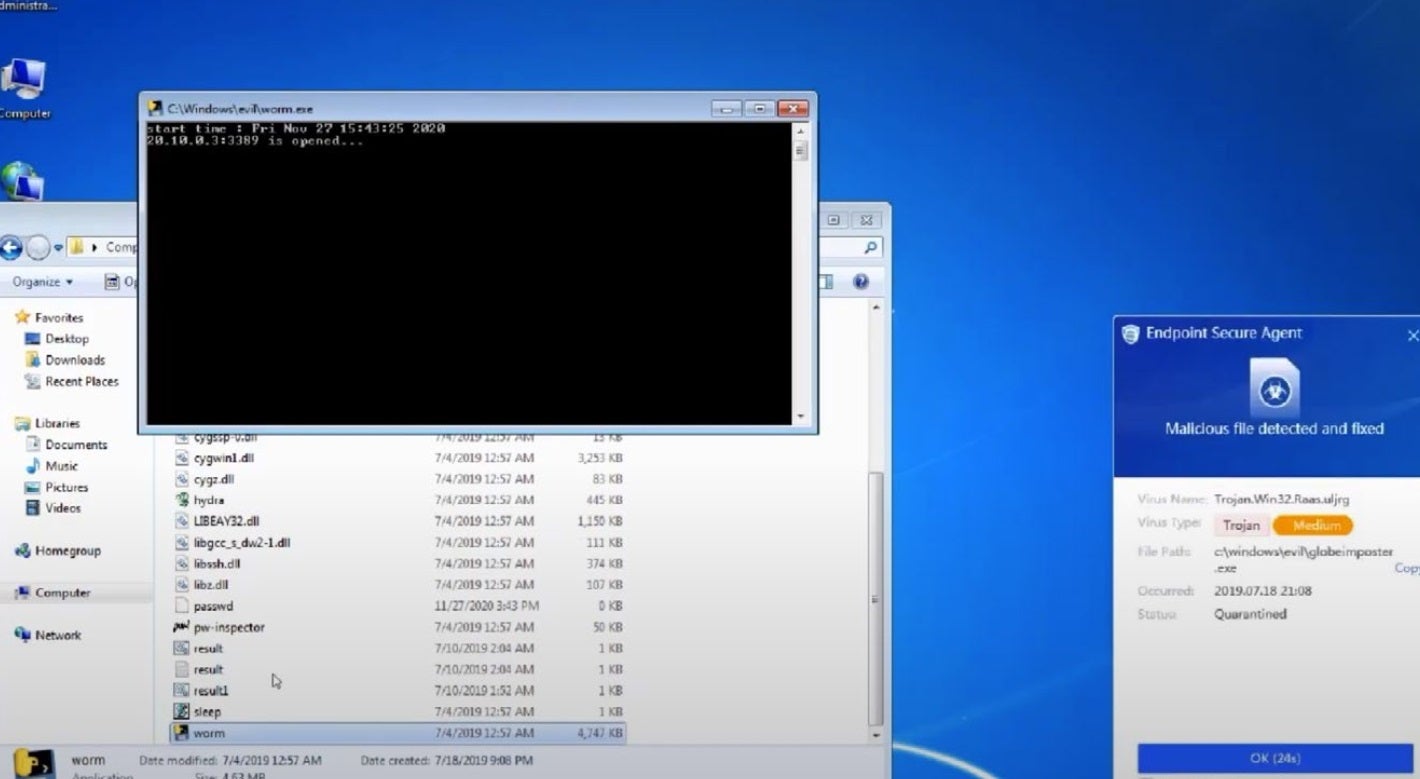
In addition, Sangfor Endpoint Secure has a built-in ransomware honeypot which seeds ransomware decoy files in the key system directories. Real-time monitoring of changes (deleted, modified, renamed, encryption) to the bait file will identify whether the endpoint has been by infected by ransomware and the processes and files related to it. The ransomware honeypot can see where it was previously impossible to detect and kill new ransomware and provide endpoints with more comprehensive ransomware protection.
Endpoint Reinforcement - Timely Repair of Vulnerabilities
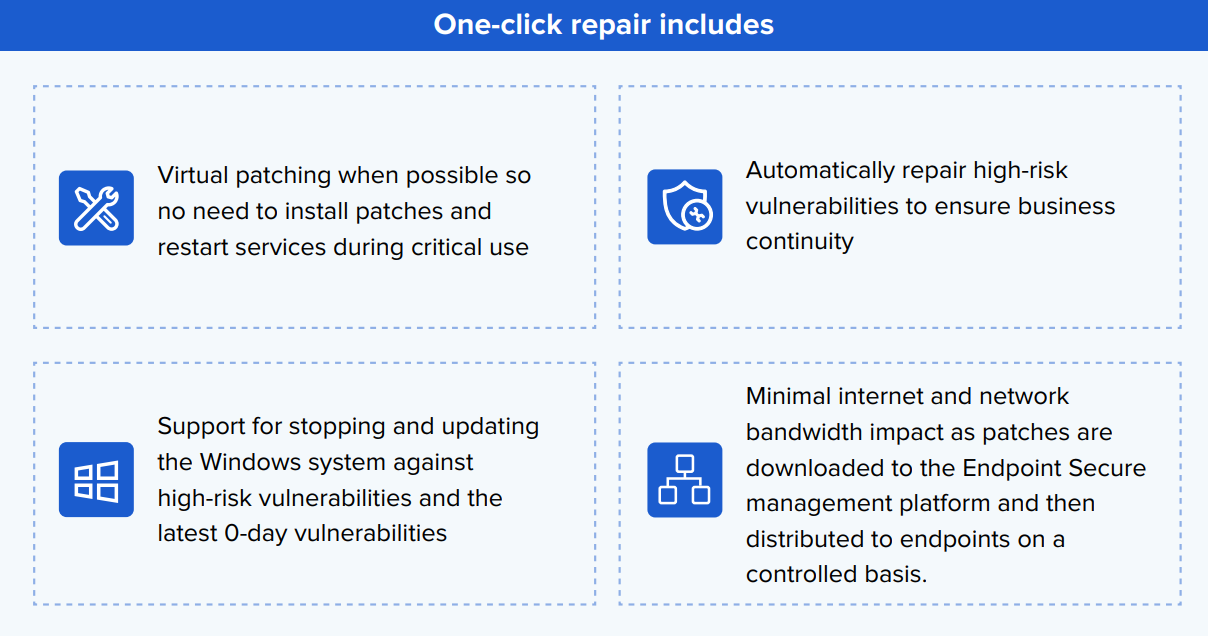
Vulnerability exploitation is a primary attack method used by ransomware groups to invade and expand infection across the organization. Repairing system vulnerabilities in a timely manner is the key to defending against ransomware attacks. Sangfor Endpoint Secure's vulnerability scan module can detect and repair Windows system vulnerabilities. It detects and repairs vulnerabilities belonging to five types of exploitation including remote code execution, denial of service, privilege escalation, security function bypass, and information leakage.
Endpoint Secure can patch the listed vulnerability types with a one-click repair function
Best Practices to Prevent Ransomware and other APT Attacks
- Companies need to be alerted to ransomware attacks during non-working or off-hours
- Companies need to have a regular patching schedule for Windows.
- Companies need to run regular vulnerability scans and quickly deploy critical patches to mitigate high-risk vulnerabilities.
- Create regular cold or remote backups that ransomware cannot encrypt from any system.
- Regularly test the restore of backups.
- People are the weakest link in corporate security (weak passwords, phishing), making it very important to improve internal security awareness (consider zero-trust where appropriate).
- The access control of core data assets needs to be strengthened, and internal firewalls or access control devices are recommended for management and control.
- Any vulnerability or botnet host in the enterprise may become a breach entry point, thus antivirus and C&C communication monitoring are essential.
- Don't underestimate the vulnerability of branch locations using private networks, closed networks, or WAN connections. It is recommended that each branch join the private network with border control equipment such as firewalls for isolation control.
- Enhance the synergy of the security products deployed throughout the organization to improve and enhance automated response capabilities.





