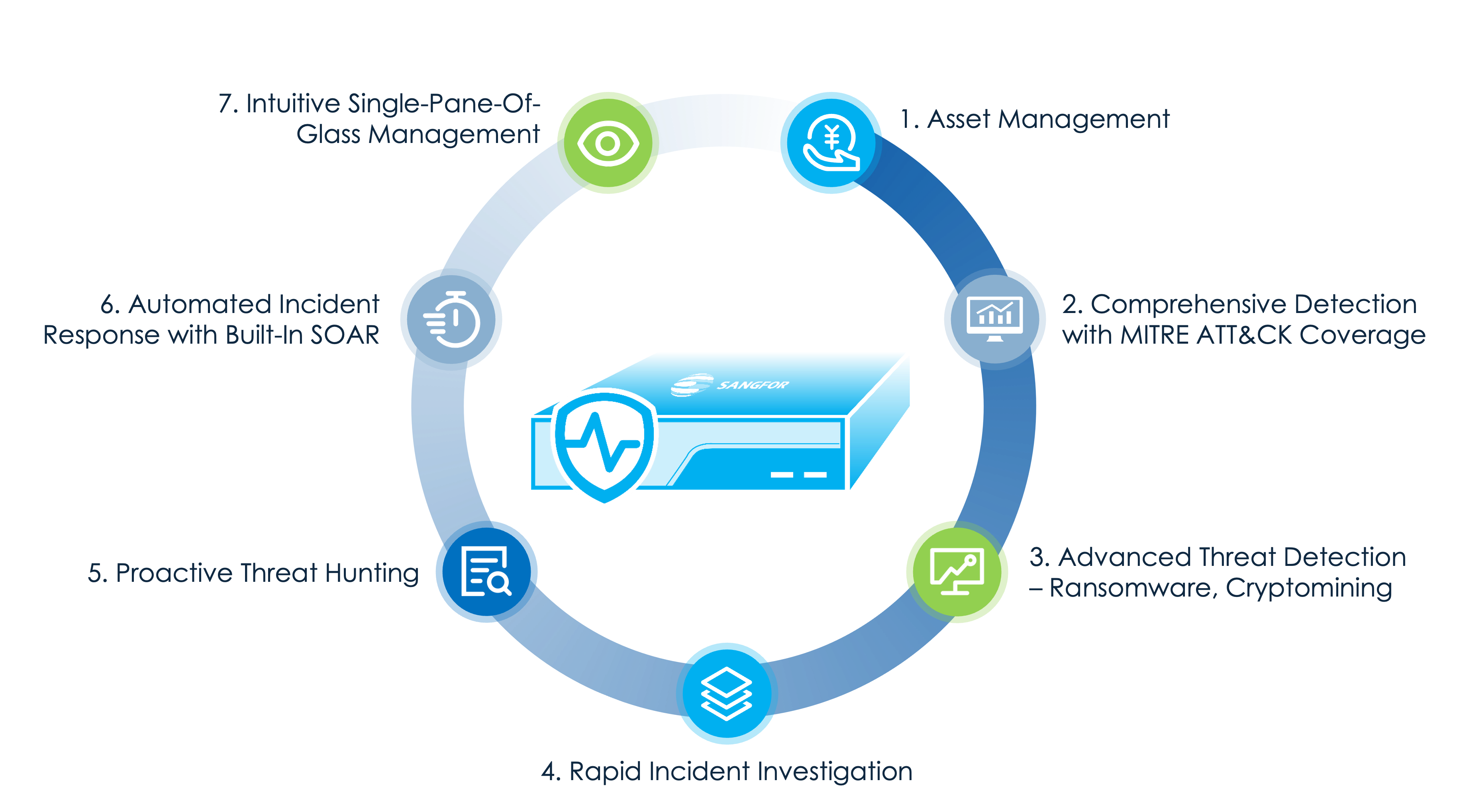
Athena NDR menangkap traffic jaringan penuh dan log-log security di seluruh segmen jaringan—baik -south maupun east-west—lalu menganalisis data tersebut menggunakan AI, analisis perilaku, threat intelligence, dan teknologi lainnya.
Dengan membangun baseline untuk aktivitas normal, Athena NDR mampu mengidentifikasi anomali yang menandakan adanya ancaman canggih seperti advanced persistent threats (APTs), ransomware, lateral movement, dan insider threats—yang sering terlewat oleh security tools terpisah. Hasilnya, organisasi mendapatkan deteksi ancaman real-time yang berarti di seluruh lingkungan jaringan.