Zero-day exploits are rapidly becoming one of the most dangerous cybersecurity threats in the age of AI (artificial intelligence) and automation. These exploits take advantage of previously unknown software vulnerabilities—issues that vendors have “zero days” to fix once discovered. In the beginning of 2024, according to Rapid 7, 53% of successful cyberattacks were linked to zero-day exploits, highlighting their growing prevalence in both enterprise and government targets.
AI is transforming cybersecurity—not just in defense, but also as a tool of attack. From zero-day exploits to deepfake fraud, AI-generated phishing, and automated malware, cybercrime is entering a new era where speed, scale, and deception are driven by machine intelligence. As generative AI and automated threat tooling continue to evolve, zero-day vulnerabilities are being exploited faster and more efficiently than ever before. Attackers now use AI to scan for unpatched systems, craft targeted payloads, and launch adaptive malware in minutes—not days.
To counter this rising threat, organizations are turning to AI-powered automated threat detection systems, such as Sangfor Engine Zero, which can detect behavioral anomalies and block zero-day exploits before they cause widespread damage.
This article examines the evolution of zero-day attacks and explores how AI and automation are transforming both the threat landscape and the defensive strategies we must adopt.

Evolution of Cyber Threats
Cyber threats have evolved dramatically over the past four decades, from rudimentary viruses spread via floppy disks to today’s automated, AI-enhanced attacks targeting critical infrastructure. Understanding this evolution is key to contextualizing the modern threat of zero-day exploits.
1. From Early Malware to Signature-Based Defense
The journey began in the 1980s with the emergence of the first PC malware, most notably the Brain virus, which infected the boot sectors of floppy disks. These early threats gave rise to the first generation of legacy security solutions: signature-based antivirus software. While effective against known threats, these tools were reactive by nature and incapable of addressing novel or obfuscated attacks.
2. Rise of Zero-Day Exploits
As software systems grew more complex, attackers began to uncover zero-day vulnerabilities—previously unknown flaws in code that developers had no opportunity to patch. Unlike traditional malware, these exploits bypassed signature-based detection entirely, targeting soft spots no one knew existed. Following attacks demonstrated how zero-days could cripple both national infrastructure and global commerce:
- Stuxnet (2010): Exploited multiple zero-days to sabotage Iran’s nuclear centrifuges, marking the first known case of cyber sabotage on physical infrastructure.
- Heartbleed (2014): A critical flaw in OpenSSL allowing attackers to extract encryption keys and credentials from millions of servers.
- EternalBlue (2017): Leaked NSA exploit used in the WannaCry ransomware campaign, affecting hundreds of thousands of systems globally.
3. The APT Era and Strategic Infiltration
The 2010s ushered in the era of Advanced Persistent Threats (APTs)—long-term, targeted cyber campaigns often attributed to nation-states. These attackers combined zero-day exploits with stealth, persistence, and data exfiltration, operating undetected for months. In response, organizations began deploying Intrusion Detection Systems (IDS) and endpoint monitoring, but these tools still struggled to keep pace with rapidly evolving tactics.
4. From Zero-Click Exploits to AI-Enhanced Attacks
Between 2020 and 2025, the threat landscape became more volatile with the rise of zero-click exploits, supply chain attacks, and AI-assisted infiltration. Attacks like EchoLeak (2025) exploited Microsoft Copilot’s natural language interface to extract sensitive data without any user interaction—no click, no download. Meanwhile, adversaries began using generative AI to develop malware, impersonate identities, and automate multi-stage phishing campaigns. Software supply chains also became high-value targets, as seen in the MOVEit (2023) mass data breach. These attacks revealed the deep interconnectivity—and fragility—of today’s digital ecosystems.
How AI Expands the Attack Surface
Artificial intelligence is not only revolutionizing cybersecurity defense—it’s also supercharging the offensive capabilities of cybercriminals. By automating reconnaissance, optimizing exploit delivery, and mimicking human behavior, AI is rapidly expanding the attack surface and lowering the technical barrier for would-be attackers.
AI-Generated Phishing and Social Engineering
Traditional phishing relied on typos, broken grammar, or vague pretexts. Today, AI-generated phishing is contextually aware, linguistically flawless, and often hyper-personalized. Attackers can fine-tune emails based on LinkedIn profiles, company news, or even user behavior, thanks to natural language generation (NLG) models. In some studies, AI phishing emails reached over 50% click-through rates, far outperforming arbitrary human-crafted lures. Worse, AI enables mass-scaling of these attacks, generating thousands of localized phishing messages in dozens of languages within minutes. This makes social engineering not just more effective, but more dangerous at global scale.
Deepfakes, Voice Cloning, and Synthetic Identities
AI also fuels deepfake fraud and voice cloning, where attackers impersonate CEOs or family members to authorize wire transfers or bypass security checks. A 2024 survey found that 46% of financial institutions experienced an increase in fraud involving synthetic audio or video. Many voice-cloning platforms still lack misuse safeguards, enabling convincing impersonation with only seconds of training data.
Automated Malware and Zero-Day Phishing
AI accelerates the creation of custom malware, adapting payloads in real time to avoid detection. It can exploit new vulnerabilities faster than traditional reverse engineering allows, often launching zero-day phishing attacks within hours of disclosure. Combined with brute-force password cracking, attackers can now simulate weeks of effort in seconds.
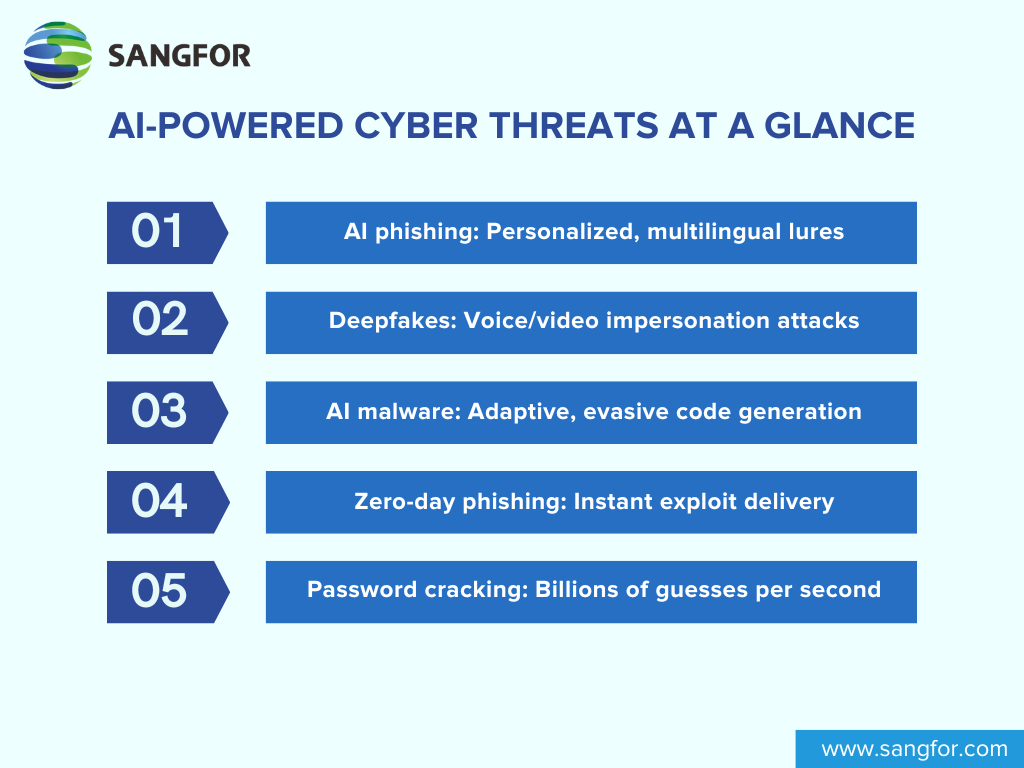
In short, AI is turbocharging the cyber kill chain. Defenders must evolve just as fast, or faster, to keep up.
The Rise of AI-Powered Cyber Defense
As cyberattacks grow faster, stealthier, and more automated, traditional defenses struggle to keep up. To counter AI-enabled threats, organizations are now embracing AI-powered cybersecurity solutions that can detect, interpret, and neutralize attacks in real time, often before humans are even aware.
From Passive Monitoring to Proactive Detection
Modern security platforms adopt machine learning and behavioral analytics to identify anomalies across networks, endpoints, and user sessions. Instead of relying solely on static rules or signatures, these systems learn what “normal” looks like, then flag unusual behavior. This is especially powerful for detecting zero-day exploits that bypass traditional defenses.
Products like Sangfor Endpoint Protection Platform (EPP), part of the Athena AI-powered security framework, combines AI behavioral analysis, dynamic threat detection, and deep memory protection to defend against zero-day malware, ransomware, and advanced persistent threats (APTs). Its integration with the Sangfor Engine Zero detection engine allows it to detect and mitigate both signature-based and unknown malware—making it especially effective in today’s zero-day-heavy threat environment.
Automated Threat Response and Incident Containment
AI doesn’t just detect threats, it reacts to them. Automated threat response systems can isolate compromised endpoints, disable suspicious user accounts, and block malicious traffic without manual intervention. Integrated Endpoint Detection and Response (EDR) tools now act autonomously to stop attacks before they spread. Simultaneously, AI-driven security orchestration platforms simulate attacks, run continuous red teaming, and optimize response workflows to improve readiness.
Enhancing Identity and Access Security
AI also strengthens identity-first security models. By analyzing login behavior, geolocation, device posture, and biometric signals, systems can assign dynamic risk scores to each login attempt. This enables adaptive MFA, risk-based authentication, and rapid mitigation of account compromise scenarios.
In sum, AI isn’t just augmenting security, it’s redefining it. But with greater intelligence comes greater complexity, and new risks, which we explore next.
Challenges and Risks of AI in Security
While AI is transforming cybersecurity defenses, it is not without its own vulnerabilities. As organizations embrace AI-driven security tools, they must also navigate a new set of risks that, if left unaddressed, can undermine the very systems meant to protect them.
False Positives and Alert Fatigue
Machine learning models, especially early-stage or poorly trained ones, are prone to false positives, flagging benign activity as malicious. Over time, this can lead to alert fatigue, where security teams become desensitized and may overlook genuine threats. Striking the balance between sensitivity and precision is a persistent challenge in AI-powered detection.
Adversarial Attacks and Model Drift
Just as AI enhances defense, attackers can exploit its weaknesses. Through adversarial inputs, carefully crafted data designed to confuse or mislead AI models, threat actors can evade detection entirely. Meanwhile, model drift occurs when an AI system's performance degrades over time due to changes in data patterns, requiring continuous retraining and validation.
Privacy, Compliance, and Governance
AI systems rely on vast amounts of data to function effectively, but that data can include sensitive personal or organizational information. Without proper controls, privacy risks and regulatory violations (such as under GDPR or HIPAA) may arise. Robust AI governance frameworks, covering data ethics, model transparency, explainability, and auditability, are essential to building trustworthy and compliant AI security operations.
In the face of these risks, organizations must go beyond deployment and adopt an architectural mindset, one that anticipates failure and builds in resilience from the ground up.
Building AI-Driven Cyber Resilience
As cyber threats become more intelligent and unpredictable, resilience, not just prevention, must become the core goal of cybersecurity. Resilience means anticipating failure, minimizing impact, and recovering swiftly—and AI plays a central role in enabling that shift.
Strategic Pillars of AI-Ready Defense
The first pillar is identity-centric security. Organizations must strengthen Identity and Access Management (IAM) through centralized control, adaptive multi-factor authentication, and behavioral analytics like login patterns or keystroke dynamics. These measures reduce the risk of credential theft, one of the most common entry points for attackers.
Second is stack unification. Fragmented security tools slow down detection and response. Platforms like Sangfor Engine Zero, when integrated with SIEM and EDR, allow for automated detection, cross-platform correlation, and faster containment—especially against zero-day threats.
Third, adopting a Zero Trust architecture ensures that no user, device, or API is trusted by default. Continuous verification, least-privilege access, and segmentation prevent lateral movement and contain breaches before they escalate.
| Pillar | Key Features |
|---|---|
| Identity-Centric Security | Centralized IAM, adaptive MFA, behavioral biometrics (e.g. keystroke dynamics) |
| Unified Security Stack | Integration of SIEM, EDR, and tools like Sangfor Engine Zero for real-time defense |
| Zero Trust Architecture | Continuous authentication, microsegmentation, least-privilege access enforcement |
Operational Execution: Turning AI into Action
Cyber resilience also requires operational maturity. AI should power real-time threat detection, automated playbooks, and predictive defense—not just compliance dashboards.
Equally critical is a security-first culture. Employees must understand evolving AI threats, participate in regular phishing simulations, and rehearse incident response plans. Cross-functional collaboration between IT, security, and compliance ensures that resilience is embedded into daily operations—not treated as an afterthought.
Future Outlook and Strategic Imperatives
Looking ahead, the cybersecurity landscape will become even more complex as AI evolves and quantum computing edges closer to mainstream deployment. Quantum machines may one day crack today’s encryption in minutes, forcing the development of quantum-resistant algorithms and post-quantum key exchange mechanisms.
Meanwhile, we’re entering an era of AI-versus-AI warfare, where defenders deploy learning models to counter adversaries using generative AI. Future systems must be adaptive, self-healing, and continuously learning, not just pre-programmed.
But as defenses get smarter, so do attackers. This intensifies the need for robust AI governance—covering model explainability, privacy safeguards, bias mitigation, and regulatory compliance. Organizations that fail to address these areas may face both legal and security consequences.
Importantly, human-AI collaboration will remain at the core of resilient cyber strategy. AI may accelerate analysis and automate workflows, but human oversight ensures ethical alignment, contextual reasoning, and strategic decision-making.
Conclusion: Intelligence Is AI with Human
Cybersecurity is no longer about blocking static threats, rather it’s about countering intelligent adversaries. AI is enabling attackers to move faster, craft more convincing lures, and exploit system vulnerabilities at machine scale. From zero-day exploits and voice-cloned scams to AI-generated malware, the nature of risk is changing. But so is the nature of defense.
Organizations that integrate AI into their core security posture, invest in identity-first strategies, and promote a culture of cyber resilience will be better prepared to navigate this new threat environment. In this evolving arms race, success doesn’t depend on perfection—it depends on readiness, intelligence, and speed. The future of cyber defense won’t be AI vs. humans. It will be AI with humans, working together to outsmart increasingly automated threats.





