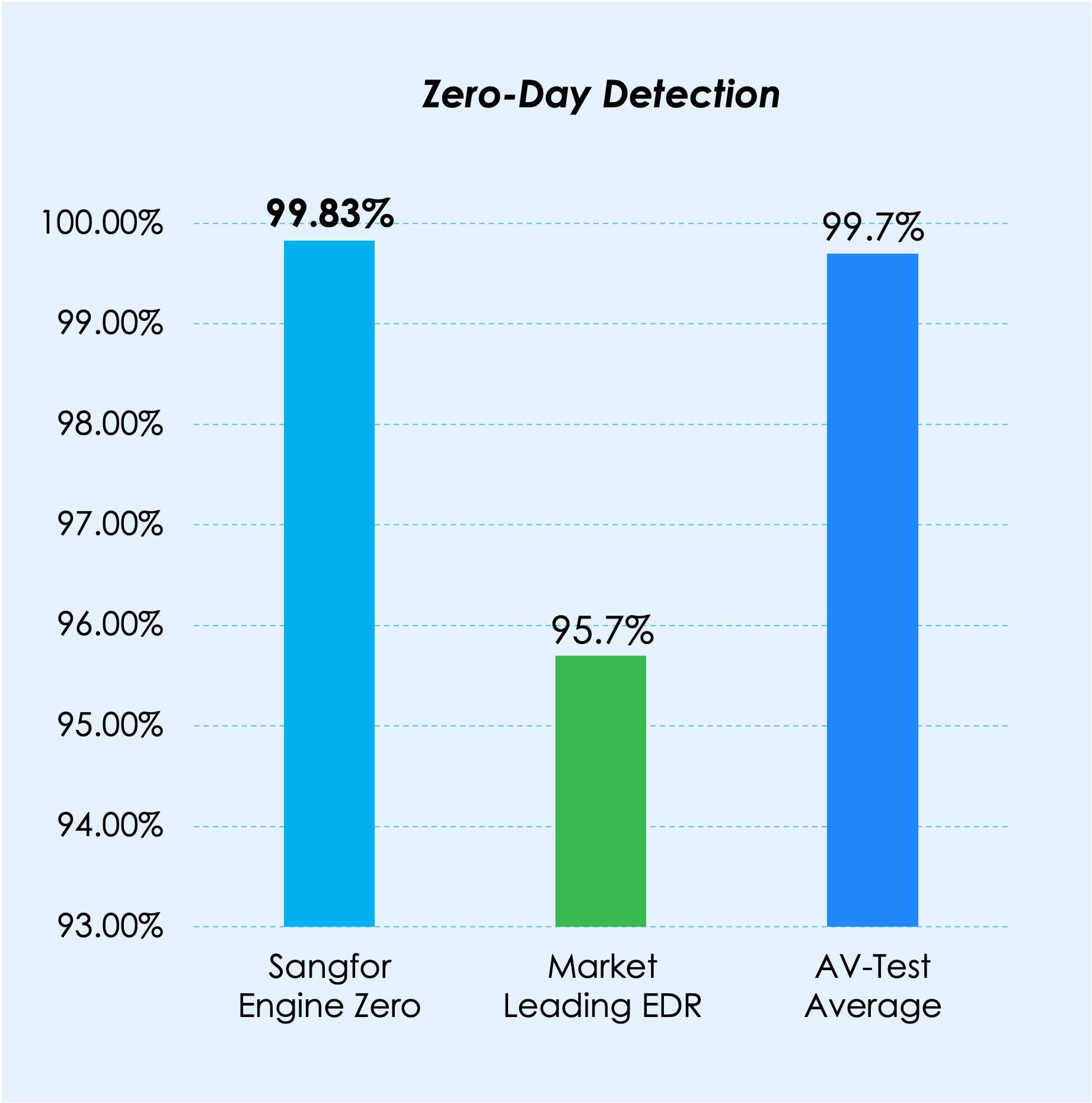
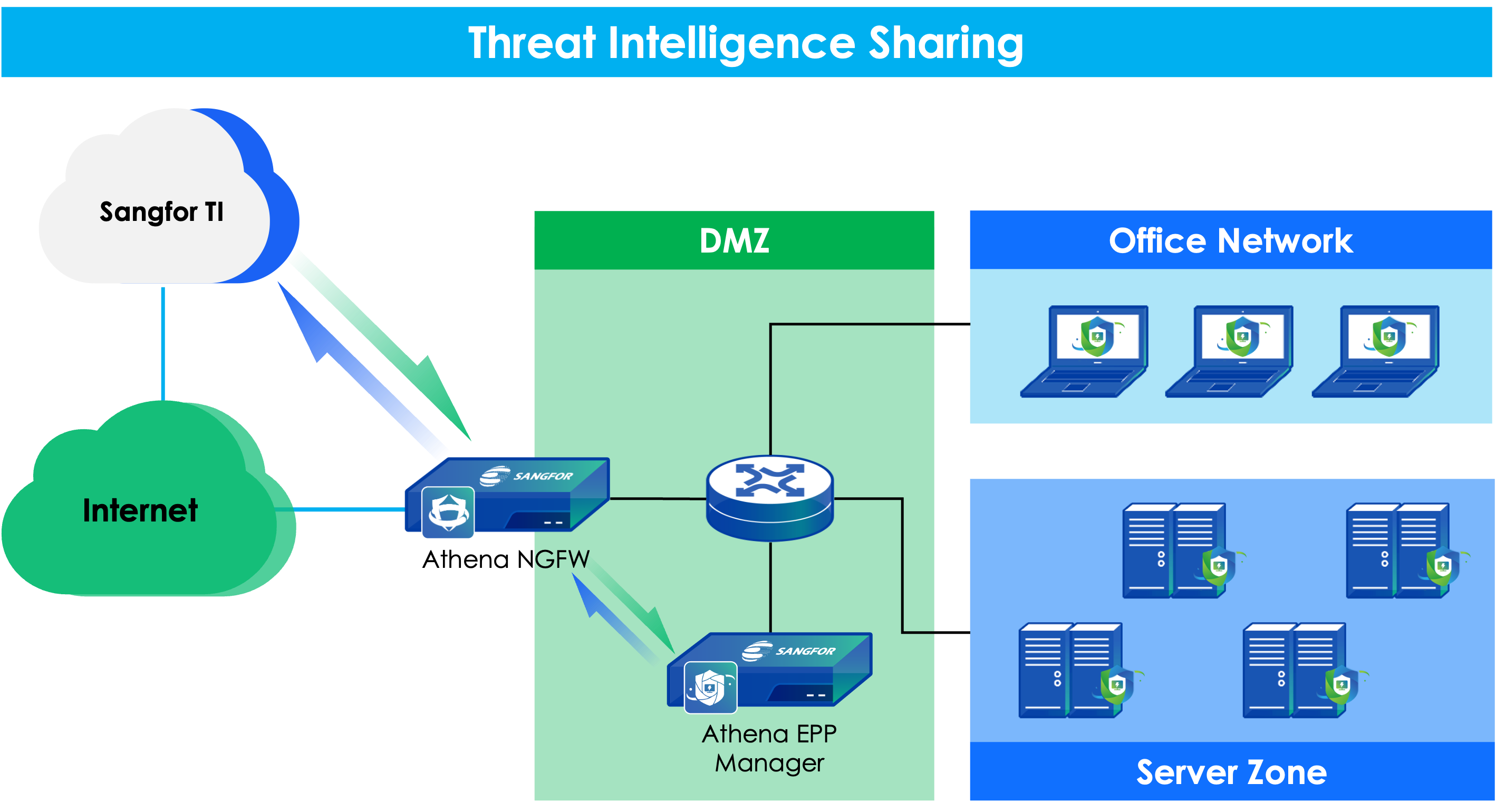
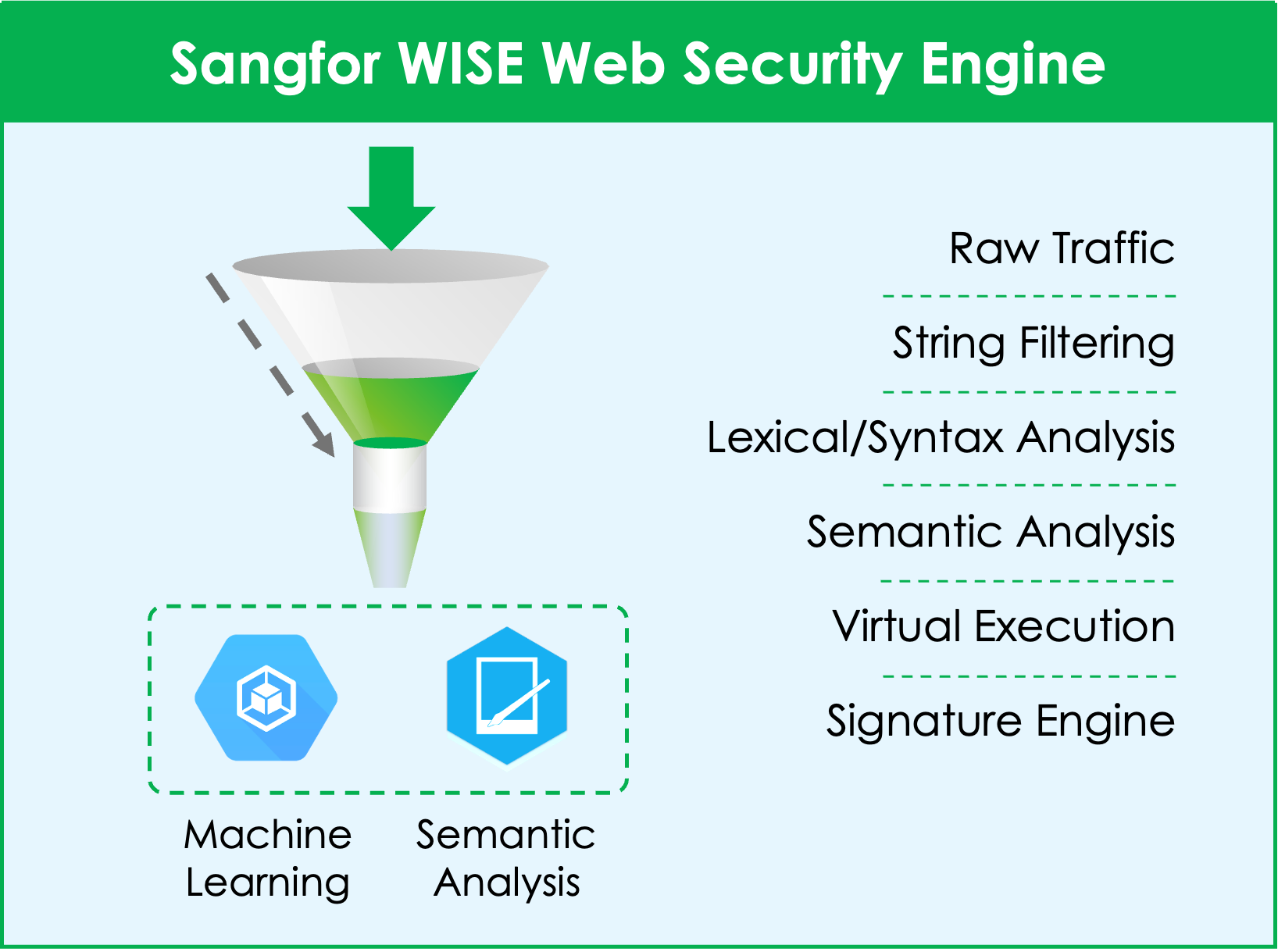
Athena NGFW terintegrasi dengan Sangfor Engine Zero, sebuah engine deteksi malware bertenaga AI. Engine Zero dikembangkan menggunakan model machine learning canggih dan algoritma AI , memungkinkan Athena NGFW mencapai tingkat deteksi 99,76% untuk malware yang sudah dikenal maupun yang belum dikenal di seluruh internet.