Filter web biasanya digunakan oleh organisasi untuk membatasi akses internet pengguna ke konten aplikasi web tertentu dan semakin tidak efektif terhadap aplikasi penghindaran proxy. IAG berkolaborasi dengan Endpoint Secure untuk menerapkan Proxy Avoidance Protection dalam setiap upaya pengguna dalam menggunakan aplikasi ini untuk melewati batas keamanan secara lebih efektif. R&D Sangfor Technologies mempekerjakan tim ahli keamanan dengan tanda tangan aplikasi khusus yang dapat terus mengelompokan dan menambahkan aplikasi penghindaran proxy terbaru dalam memastikan tingkat deteksi dan kemampuan pemblokiran yang up-to-date.
Sangfor IAG – Internet Access Gateway & Solusi Penyaringan Web
Mengikuti tren percepatan modern seperti mengadopsi aplikasi cloud, perpindahan tempat kerja hybrid, dan peningkatan penggunaan perangkat seluler demi kebutuhan pribadi maupun pekerjaan, semuanya tentu memberikan tekanan yang besar pada organisasi untuk memastikan lingkungan kerja yang aman dan maksimal. Pada saat yang sama, peningkatan aplikasi terenkripsi, aplikasi penghindaran proxy, dan ketersediaan aplikasi VPN pihak ketiga yang semakin terjangkau juga telah memberlakukan tanggung jawab lebih lanjut untuk organisasi dimana mereka dapat dengan mudah melewati parimeter keamanan anda tanpa diketahui. Tentunya Anda memerlukan perlindungan gateaway yang ekstensif, tidak hanya untuk melindungi organisasi Anda dari ancaman umum yang ada, tetapi juga sebagai aset penting untuk menjaga perilaku pengguna dalam akses internet.
Mengapa Sangfor IAG?
Sangfor IAG memungkinkan Anda untuk mengidentifikasi, menganalisis, dan mengambil tindakan segera atas perilaku akses internet para pengguna.
Keunggulan Produk
Perlindungan Penghindaran Proksi
Manajemen Lalu Lintas Cerdas
Sangfor IAG meningkatkan pemanfaatan bandwidth hingga lebih dari 30% dengan menggunakan tiga solusi manajemen lalu lintas utama yang unik. Dynamic Traffic Control secara otomatis menyesuaikan kebijakan kontrol lalu lintas dan secara cerdas mengalokasikan sumber daya bandwidth yang tidak digunakan. Intelligent Flow Control secara tepat mengelola kedua lalu lintas P2P up-link dan down-link yang dapat menyesuaikan "paket" lalu lintas untuk pengguna yang berbeda, mengalokasikan kuota lalu lintas tertentu dan membatasi bandwidth ke pengguna yang lebih banyak.
Dekripsi Gateway dan Klien untuk Mengungkap Lalu Lintas Terenkripsi
Biasanya, sebagian besar lalu lintas internet dilindungi oleh enkripsi SSL/TLS. Meskipun enkripsi membantu menjaga data pengguna dan perusahaan tetap terlindungi, enkripsi juga menciptakan tantangan keamanan terkait dengan pesatnya pertumbuhan infeksi malware dan konten berbahaya lainnya. Sangfor IAG menawarkan kedua metode dekripsi gateway dan dekripsi klien untuk mengatasi tantangan ini. Hal ini memungkinkan organisasi memiliki fleksibilitas untuk menjalankan salah satu atau keduanya secara paralel untuk mengungkap lalu lintas terenkripsi sesuai dengan strategi dan perencanaan TI perusahaan Anda.
Manajemen Seluruh Jaringan Terpadu dari semua Klien
Sangfor IAG menyediakan Manajemen Terpadu dan secara efektif mengontrol jaringan Kabel dan Nirkabel untuk seluruh jaringan. Dengan metode autentikasi yang intuitif dan fleksibel, sepenuhnya menjamin keamanan kontrol akses, mendukung berbagai metode autentikasi tradisional seperti nama pengguna/sandi, pengikatan IP/MAC, dan beragam metode autentikasi marketing (kode QR, SMS , WeChat, Media sosial, akun OA, SAML 2.0, sistem pihak ketiga, dll.). Izin dikontrol berdasarkan jenis pengguna, aplikasi, lokasi, dan klien saat menggunakan pengontrol nirkabel IAG atau pihak ketiga sebagai server autentikasi terpadu, membangun jaringan nirkabel yang lebih cepat dan lebih hemat biaya.
Kontrol Aplikasi yang Tepat dan Akurat
Sangfor IAG mengelola dan mengontrol aplikasi jaringan secara lebih komprehensif, akurat, dan nyaman dengan basis data tanda tangan aplikasi terbesar di Asia, yang dapat mengidentifikasi lebih dari 6.000+ aplikasi, termasuk 700+ aplikasi cloud, 1.000+ aplikasi seluler, 300+ aplikasi web, dan diperbarui setiap 2 minggu. Selain itu, ini mengontrol aplikasi secara tepat sesuai dengan fungsi spesifiknya, seperti membedakan pengunggahan, pengunduhan, dan tindakan lain dalam jaringan. Yang terpenting, mode manajemen massal untuk perusahaan besar tentunya dapat meningkatkan efisiensi manajemen.
Performa Pembongkaran Saat Menggunakan Integrasi ICAP Dengan Sistem Pihak Ketiga
Sangfor IAG dapat bertindak sebagai klien ICAP untuk digunakan dengan alat jaringan apa pun yang mendukung server ICAP dengan membongkar perlindungan ancaman atau layanan bernilai tambah lainnya. Selain itu, Sangfor IAG menyediakan mode inspeksi permintaan dan tanggapan sambil mengaktifkan grup server ICAP untuk berjalan pada kondisi round-robin atau bersamaan.
Perangkat Onboarding Aman Dengan Postur Keamanan Endpoint
Sangfor IAG mengidentifikasi dan mengamankan perangkat endpoint dengan atau tanpa agen, hal ini membantu memastikan perangkat ini terhubung dengan sesuai dan aman. Anda mendapatkan visibilitas penuh dan mengontrol apa yang ada di lingkungan Anda tanpa memengaruhi kinerja jaringan Anda.
Perlindungan Penghindaran Proksi
Filter web biasanya digunakan oleh organisasi untuk membatasi akses internet pengguna ke konten aplikasi web tertentu dan semakin tidak efektif terhadap aplikasi penghindaran proxy. IAG berkolaborasi dengan Endpoint Secure untuk menerapkan Proxy Avoidance Protection dalam setiap upaya pengguna dalam menggunakan aplikasi ini untuk melewati batas keamanan secara lebih efektif. R&D Sangfor Technologies mempekerjakan tim ahli keamanan dengan tanda tangan aplikasi khusus yang dapat terus mengelompokan dan menambahkan aplikasi penghindaran proxy terbaru dalam memastikan tingkat deteksi dan kemampuan pemblokiran yang up-to-date.
Manajemen Lalu Lintas Cerdas
Sangfor IAG meningkatkan pemanfaatan bandwidth hingga lebih dari 30% dengan menggunakan tiga solusi manajemen lalu lintas utama yang unik. Dynamic Traffic Control secara otomatis menyesuaikan kebijakan kontrol lalu lintas dan secara cerdas mengalokasikan sumber daya bandwidth yang tidak digunakan. Intelligent Flow Control secara tepat mengelola kedua lalu lintas P2P up-link dan down-link yang dapat menyesuaikan "paket" lalu lintas untuk pengguna yang berbeda, mengalokasikan kuota lalu lintas tertentu dan membatasi bandwidth ke pengguna yang lebih banyak.
Dekripsi Gateway dan Klien untuk Mengungkap Lalu Lintas Terenkripsi
Biasanya, sebagian besar lalu lintas internet dilindungi oleh enkripsi SSL/TLS. Meskipun enkripsi membantu menjaga data pengguna dan perusahaan tetap terlindungi, enkripsi juga menciptakan tantangan keamanan terkait dengan pesatnya pertumbuhan infeksi malware dan konten berbahaya lainnya. Sangfor IAG menawarkan kedua metode dekripsi gateway dan dekripsi klien untuk mengatasi tantangan ini. Hal ini memungkinkan organisasi memiliki fleksibilitas untuk menjalankan salah satu atau keduanya secara paralel untuk mengungkap lalu lintas terenkripsi sesuai dengan strategi dan perencanaan TI perusahaan Anda.
Manajemen Seluruh Jaringan Terpadu dari semua Klien
Sangfor IAG menyediakan Manajemen Terpadu dan secara efektif mengontrol jaringan Kabel dan Nirkabel untuk seluruh jaringan. Dengan metode autentikasi yang intuitif dan fleksibel, sepenuhnya menjamin keamanan kontrol akses, mendukung berbagai metode autentikasi tradisional seperti nama pengguna/sandi, pengikatan IP/MAC, dan beragam metode autentikasi marketing (kode QR, SMS , WeChat, Media sosial, akun OA, SAML 2.0, sistem pihak ketiga, dll.). Izin dikontrol berdasarkan jenis pengguna, aplikasi, lokasi, dan klien saat menggunakan pengontrol nirkabel IAG atau pihak ketiga sebagai server autentikasi terpadu, membangun jaringan nirkabel yang lebih cepat dan lebih hemat biaya.
Kontrol Aplikasi yang Tepat dan Akurat
Sangfor IAG mengelola dan mengontrol aplikasi jaringan secara lebih komprehensif, akurat, dan nyaman dengan basis data tanda tangan aplikasi terbesar di Asia, yang dapat mengidentifikasi lebih dari 6.000+ aplikasi, termasuk 700+ aplikasi cloud, 1.000+ aplikasi seluler, 300+ aplikasi web, dan diperbarui setiap 2 minggu. Selain itu, ini mengontrol aplikasi secara tepat sesuai dengan fungsi spesifiknya, seperti membedakan pengunggahan, pengunduhan, dan tindakan lain dalam jaringan. Yang terpenting, mode manajemen massal untuk perusahaan besar tentunya dapat meningkatkan efisiensi manajemen.
Performa Pembongkaran Saat Menggunakan Integrasi ICAP Dengan Sistem Pihak Ketiga
Sangfor IAG dapat bertindak sebagai klien ICAP untuk digunakan dengan alat jaringan apa pun yang mendukung server ICAP dengan membongkar perlindungan ancaman atau layanan bernilai tambah lainnya. Selain itu, Sangfor IAG menyediakan mode inspeksi permintaan dan tanggapan sambil mengaktifkan grup server ICAP untuk berjalan pada kondisi round-robin atau bersamaan.
Perangkat Onboarding Aman Dengan Postur Keamanan Endpoint
Sangfor IAG mengidentifikasi dan mengamankan perangkat endpoint dengan atau tanpa agen, hal ini membantu memastikan perangkat ini terhubung dengan sesuai dan aman. Anda mendapatkan visibilitas penuh dan mengontrol apa yang ada di lingkungan Anda tanpa memengaruhi kinerja jaringan Anda.
Kisah Sukses
Di bawah ini Anda akan menemukan semua Kisah Sukses Sangfor, yang diklasifikasikan berdasarkan Industri, seperti Perusahaan, Pemerintahan, Sekolah & Universitas, dll.
Partner Success with Sangfor: Global Sapphire's Growth Partnership & Development








Kasus Penggunaan
Tanpa Sangfor IAG, lingkungan kantor dapat disamakan dengan warnet di mana pengguna dan staf dapat dengan bebas mengakses video, media sosial, dan hiburan tanpa henti. Administrator TI kesulitan untuk mengidentifikasi dengan tepat pengguna mana yang menggunakan bandwidth berlebih, mencegah kontrol yang efektif atas perilaku penelusuran pengguna. Sangfor IAG dapat mengidentifikasi dan mengontrol aplikasi yang tidak terkait dengan pekerjaan di jaringan sambil memungkinkan perusahaan untuk mengawasi manajemen bandwidth mereka, di mana mereka mengalokasikan semua bandwidth yang tersedia untuk kebutuhan bisnis utama, dan meningkatkan efisiensi dan produktivitas bisnis. Sejumlah fitur manajemen lalu lintas profesional memungkinkan IAG mengalokasikan sumber daya bandwidth secara rasional dan memaksimalkan penggunaan bandwidth. Untuk organisasi dengan banyak cabang, IAG menyediakan platform manajemen terpadu dan mendukung pencadangan tautan 3G, menjadikan manajemen jaringan lebih efisien dan andal.
Karena pelanggan memiliki prosedur autentikasi yang sangat berbeda, setiap jaringan internal memerlukan integrasi autentikasi pengguna dengan AD, Radius untuk mencapai SSO. Otentikasi tamu IAG menyediakan akses mudah melalui Facebook, WeChat, SMS dan menawarkan solusi otentikasi terpadu, yang mengelola pengguna yang terhubung dengan kabel dan nirkabel dalam satu platform IAG. Sangfor IAG juga menawarkan kemampuan kontrol akses pengguna berbasis sakelar untuk membantu mengontrol akses pengguna LAN. Akhirnya, Sangfor IAG dapat diintegrasikan dengan vendor WLAN seperti Cisco, Aruba untuk memungkinkan Pusat Otentikasi Terpadu secara drastis menyederhanakan proses integrasi dan manajemen jaringan.
Untuk melindungi pengguna dari ancaman web, gateway web yang aman adalah pertahanan yang efektif terhadap ancaman berbasis web dan memungkinkan akses internet yang aman. Sangfor IAG dapat bekerja dengan aplikasi lokal dan lalu lintas internet Anda. Dengan kinerja dekripsi SSL yang dipercepat, semua lalu lintas HTTP dan HTTPS akan dipantau dan dianalisis dengan IAG, yang merupakan hambatan besar dari solusi lain seperti NGFW atau UTM. Platform intelijen ancaman berbasis AI menyediakan layanan pemfilteran web dan meningkatkan kemampuan untuk mengidentifikasi ancaman yang dikenal dan tidak dikenal. Itu juga membuat pengguna terlindungi sambil memastikan mereka menikmati pengalaman web yang aman dan terlindungi.
Karena penggunaan jaringan yang tidak sah menjadi lebih umum, banyak negara dan wilayah sedang mengembangkan dan menegakkan undang-undang yang mengatur perilaku akses internet pengguna. Database aplikasi internal IAG secara komprehensif mencatat aktivitas pengguna yang berbahaya termasuk unggahan file, posting BBS, email, riwayat penelusuran, dan aplikasi yang diakses. Solusi audit ini membantu kepatuhan pelanggan terhadap peraturan hukum setempat dan berfungsi sebagai sumber daya investigasi yang berharga jika terjadi insiden penggunaan jaringan ilegal.
Pertanyaan Yang Sering Diajukan
Silakan lakukan berikut ini:
- Langkah 1. Tambahkan Server LDAP baru di bawah Server Autentikasi Eksternal.
- Langkah 2. Masukkan detail seperti Nama Server, Alamat IP dari server otentikasi eksternal, nama pengguna dan kata sandi akun admin dan pilih BaseDN. Setelah memasukkan semua detail, klik Uji Validitas untuk memeriksa apakah dapat menghubungkan server autentikasi eksternal atau tidak.
- Langkah 3. Setelah diuji validitasnya, sebuah pesan akan keluar untuk menunjukkan hasilnya.
- Langkah 4. Klik Sinkronkan dengan semua server LDAP untuk menyinkronkan semua data. Sekarang, konfigurasi berhasil diatur.
Dalam lingkungan biasa, SWG digunakan untuk memblokir akses ke situs web atau aplikasi yang tidak pantas, mencegah infeksi malware, dan menegakkan kepatuhan internet perusahaan. SWG mirip dengan firewall yang mencegah aktivitas jahat dan memberikan perlindungan keamanan jaringan yang diperlukan. Namun, perbedaan utamanya adalah SWG menekankan pengamanan orientasi pengguna dan peningkatan produktivitas. Adalah umum bagi perusahaan untuk menggunakan SWG dan firewall untuk memperkuat pertahanan mereka karena keduanya, biasanya saling melengkapi. Untuk info lebih lanjut tentang penggunaan IAG dan NGAF, silakan merujuk ke halaman web blog ini.
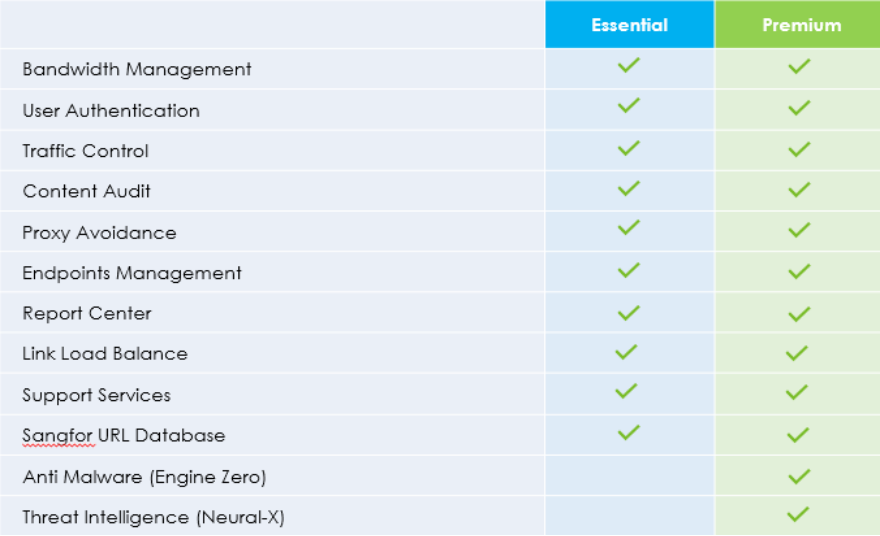
Perbedaan utamanya adalah Premium Bundle akan memiliki semua komponen Essential Bundle dengan tambahan perlindungan Anti-malware (Engine Zero) dan intelijen ancaman (Neural-X).
Webinar Terbaru

Sangfor International Roadshow 2025 – Thailand
Sangfor's Bangkok Roadshow united 400+ attendees for a day of tech insights, cybersecurity trends, and cloud innovation under "Digital Plus | IT Minus".
Sangfor International Roadshow 2025 – Jeddah, Saudi Arabia
Building on the electrifying momentum from Riyadh, Sangfor Technologies successfully brought the energy to Jeddah with an unforgettable stop on our 2025 Roadshow on May 20th!
Sangfor International Roadshow 2025 – Riyadh, Saudi Arabia
We are excited to share the outstanding success of the Sangfor 2025 Roadshow held in Riyadh, Saudi Arabia, on 18th May.
Blog Terbaru

Qantas & Hawaiian Airlines Cyber Attacks Expose Growing Aviation Threats
Qantas confirms breach of 6M accounts as Hawaiian Airlines faces cyberattack threat. Scattered Spider and ransomware raise global aviation security alarms.
Apa Itu MDR (Managed Detection and Response)? Keuntungan dan Cara Kerjanya
Apa itu MDR? MDR adalah solusi keamanan siber yang dikelola oleh pihak ketiga untuk membantu perusahaan dalam mendeteksi dan merespons secara real-time.
Sangfor vs Fortinet (FortiGate): Which Next-Gen Firewall Is Better in 2025?
Compare Sangfor Athena NGFW with Fortinet FortiGate. Discover which firewall offers better value, performance, and support in 2025.
Berita Terbaru

Sangfor Technologies Unveils Sangfor Athena: A Bold New Brand for Its Cybersecurity Business
Sangfor Athena unifies advanced security solutions under one brand, powered by SynergyAI for proactive cyber defense. Discover intelligent, integrated protection today!
Sangfor Honored with Frost & Sullivan’s 2025 APAC XDR Customer Value Leadership Recognition
Sangfor wins Frost & Sullivan’s 2025 APAC award for XDR, recognized for AI-driven threat detection, automation, and customer-centric innovation.
Sangfor Technologies Named Winner of Coveted Global InfoSec Awards at RSAC 2025
Sangfor Technologies wins multiple awards at RSAC 2025 for their AI-driven cybersecurity solutions, including Security GPT, XDR, and Cyber Guardian MDR.











