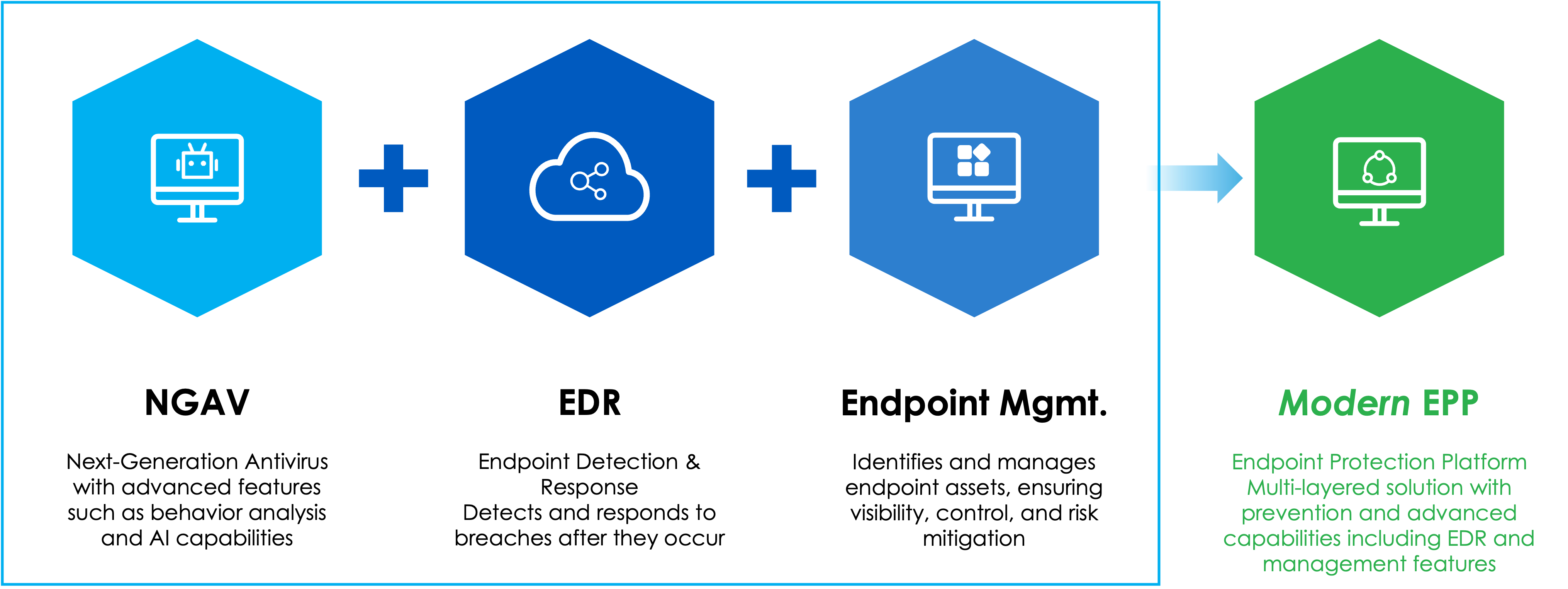
1. EPP vs. Antivirus:
Antivirus is a basic security tool that detects and removes known malware based on signature databases.
EPP includes antivirus as one component but goes further by integrating multiple layers of defense (e.g., behavioral analysis, machine learning, and vulnerability assessment) to prevent, detect, and respond to both known and unknown threats.
2. EPP vs. EDR (Endpoint Detection and Response):
EDR is focused on detecting, investigating, and responding to advanced threats that bypass traditional defenses. It provides deep visibility into endpoint activities and supports threat hunting and forensic analysis.
EPP is preventive by design, aiming to stop threats before they can cause harm. Some modern EPP solutions also include EDR capabilities, but full EDR platforms are more robust for post-compromise detection and response.