Business Intelligence
Why do you need Internet compliance?
Some malicious users in the organization are intentional, difficult to spot and difficult to manage. Massive online behavior logs contain unlimited value. In-depth analysis not only perceives high risk user behavior on an organizational level but also detects more business value. Users need a comprehensive platform that can simply and efficiently excavate business value.
- How do you trace internal leaks?
- How the internet affects productivity?
- How do you identify and prevent data exfiltration?
- What are the main trends in internet usage?
- How do you identify and eliminate high risk user activity?
- How to check bandwidth usage across your network?
The Look of Innovation
Sangfor Business Intelligence Platform (BI) is the newest major innovation within Sangfor IAG. It is based on IAG’s massive internet log and conducts in-depth modelling analysis of user unauthorized behaviour characteristics. It constantly utilizes behavioural awareness applications in different scenarios and continuously uncovers valuable data, helping organizations understand behaviour risk and simplify O&M.
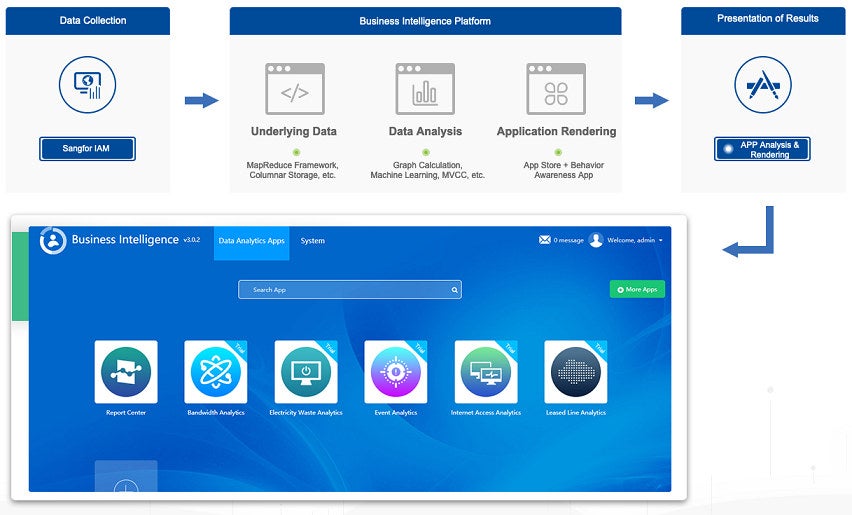
Behaviour Analysis for Every Scenario
Each application helps you discover and analyse specific types of risky behaviour.
Report Center
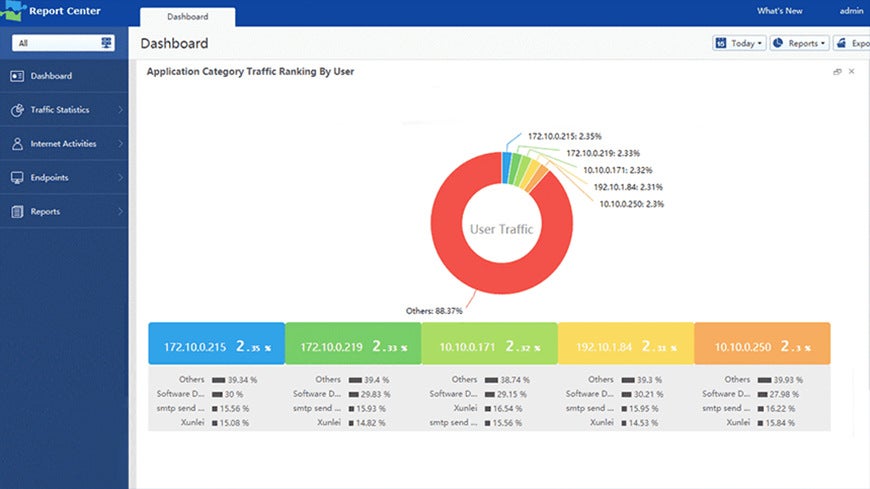
- Log all users unauthorized internet access behavior and generate reports about network traffic.
- Comprehensive & intuitive reports: Application, user bandwidth and quota ranking.
- Step-by-Step troubleshooting: Analyse the bandwidth step-by-step to find to the root cause of network issues.
Bandwidth Analytics
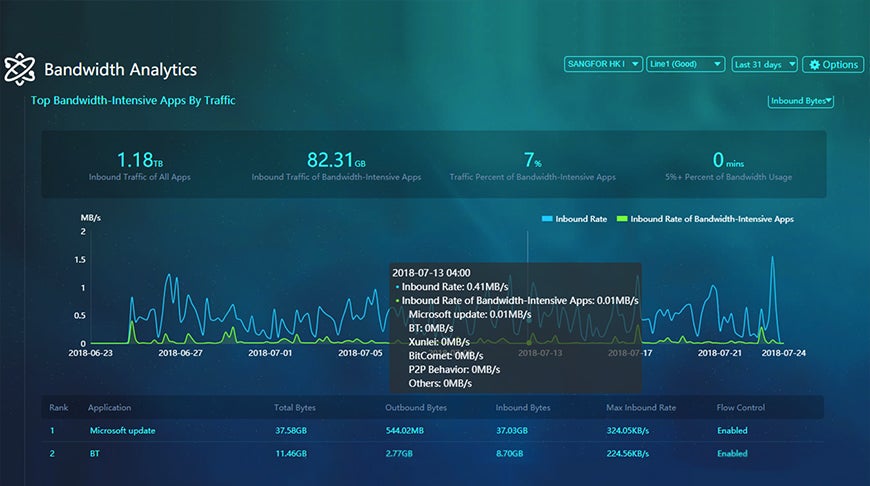
- Analyze general internet bandwidth usage and evaluate bandwidth-consuming applications.
- Bandwidth quality analysis: Analyze the bandwidth quality for a specific period of time and offer suggestions for internet bandwidth expansion.
- Bandwidth consuming application analysis: Analyze bandwidth-consuming application traffic and offer suggestions on control policy setup.
Electricity Waste Analytics
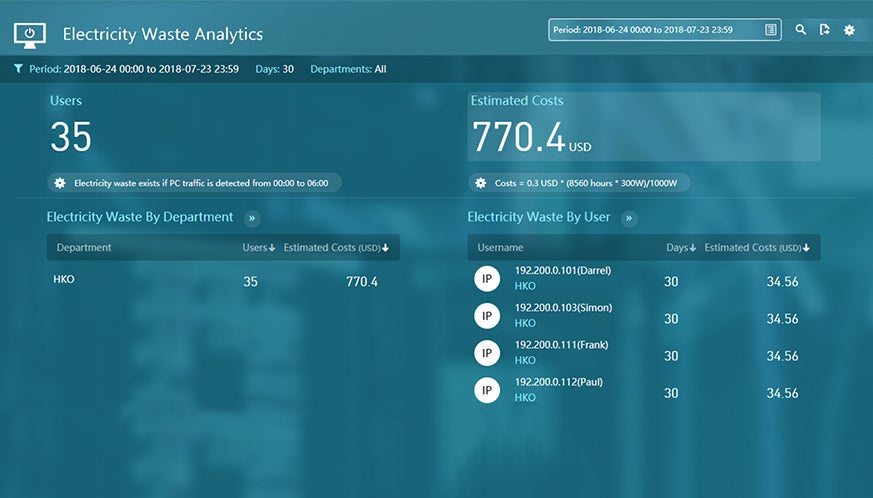
- Analyze office computer power waste outside business hours and save money on electricity.
- Office computer electricity power waste analysis: Reports on all PCs running outside business hours with user and department ranking display.
Internet Access Analytics
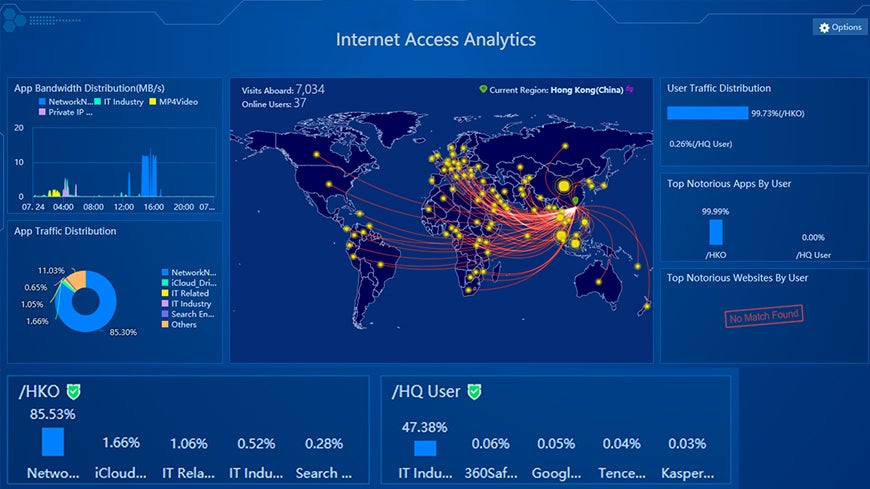
- Display the overall traffic status of the whole network with easy to read reports.
- Improve work productivity: No need to log into the device to check traffic status with easy-to-read report display.
- Risk assessment at a glance: Abnormal user behavior and security risks are reported in real time helping to quickly identify any risk to the network.
Event Analytics
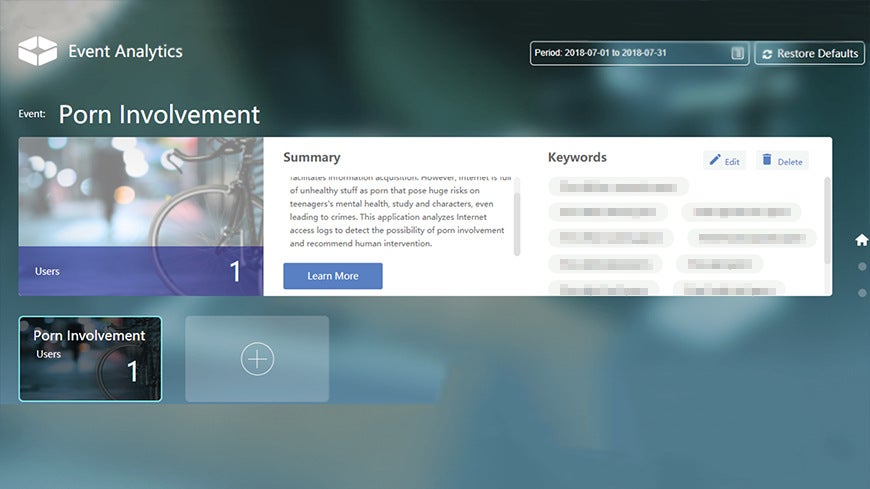
- Analysis of unauthorized user behavior allowing for a full understanding of the user risks as well as network risks.
- Keyword based analysis: Analyze unauthorized user behavior based on keywords. The customizable application offers flexible access to dedicated incidents.
- Proactively address any risk: When high risk user activity is discovered you can proactive speak to the users, avoiding any potential legal risk which may harm your company’s reputation.
Leased Line Analytics
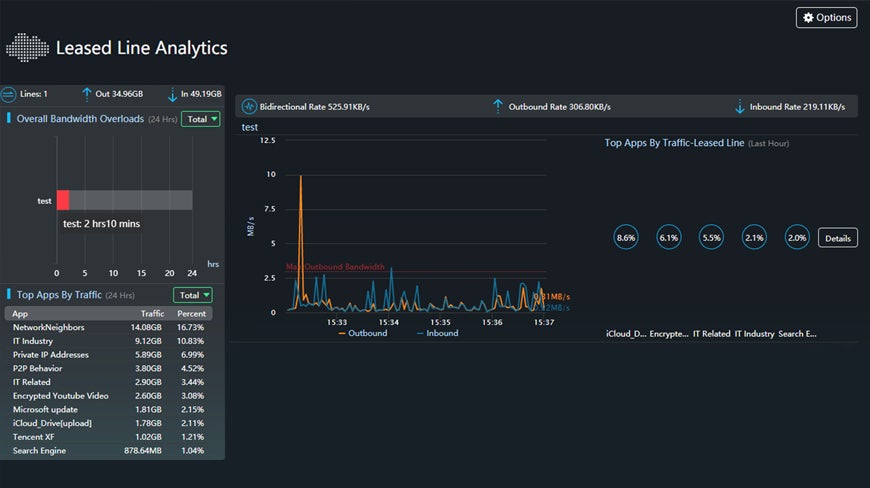
- Analyze the leased line quality and assist in the line expansion decision making.
- Decision-making assistance: Report on the quality of the leased line and more informed decisions on when to expand the leased line bandwidth.
- Leased line traffic visualization: Provide visibility into the tunnel and the user to achieve awareness of the whole network.
Intelligent Solutions
Multi-system integration - data acquisition and data analysis
- IAG is responsible for collecting data, and BI is responsible for data analysis and display.
- BI and IAG are deeply integrated to realize the intelligent linkage between data analysis and Internet behavior control.
Business Intelligence Applications
- Various data analysis methods are imbedded into various applications. Each BI application helps users solve a business problem. In addition, the applications are decoupled from the platform and can be obtained on demand.
Application Store
- The application store provides centralized management of all BI applications. Application installation, update and removal are as simple as app management on a mobile phone.
Our Advantages
In-House Developed Independent Data Analysis Platform (IterateDB)
- 100% in-house developed TB level data analysis platform performing queries on the second level.
- MapReduce distributed software framework is integrated into the platform, ensuring excellent expansion capability.
- Utilizing a unique component-based mode where components can be disposed of after use, providing significant savings in performance overhead.
Data Analysis is More Accurate
- Integration of graphic computing and machine learning technology to make modeling analysis more scientific.
- Human-Machine flow separation technology eliminates irrelevant flow interference, making statistical analysis more accurate.
