Recently, many large and medium-sized enterprises across Asia have reported continuous ransomware attacks. After analysis and canvassing by The Sangfor Security Team, the attacks were determined to be caused by “Sodinokibi” ransomware. This ransomware family has been found to be extremely active lately, launching attacks against a number of industries. The cyber-criminals adhere to a policy of, “first breach one host and then take the entire network,” using Sodinokibi ransomware to encrypt users, hosts and intranets. Enterprises feeling the strongest effects face intranet and server breakdown unless $28,450.00 is paid for decryption.
Early Discovery & Structure
The Sangfor Security Team first detected this ransomware in early April 2019. It was identified as a variation of “DeepBlue,” a ransomware variant which uses a random encryption suffix and changes the background of the host desktop to navy blue after encryption, and also having inherited it’s code structure from GrandCrab.
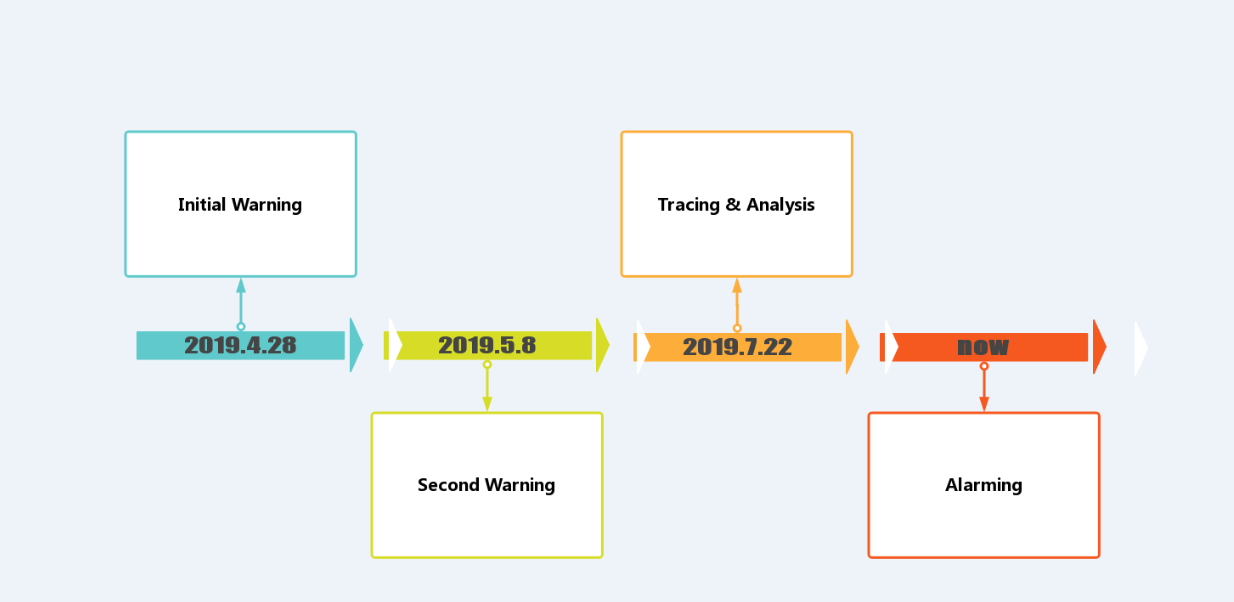
Later, security vendors subsequently issued reports of the ransomware strain “Sodinokibi.” The following shows the timeline our Security Team tracing the ransomware family.
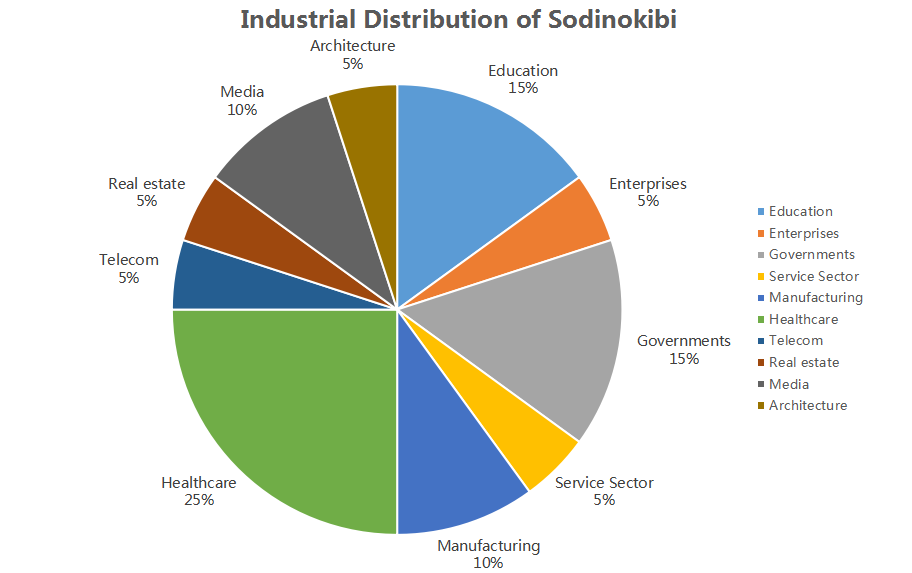
According to Sangfor Security Team statistics, since the advent of this ransomware, it has carried out targeted attacks against large and medium-sized users in various industries. From the distribution map of infected industries, the healthcare industry with weaker security protection is the most seriously affected, and other industries are also subject to attacks of varying intensities.
Efficient Attack & Professional Technique
During the initial phase of the ransomware activity, attackers launched attacks by exploiting vulnerabilities like Confluence (CVE-2019-3396), UAF (CVE-2018-4878) and Weblogic Deserialization (CVE-2019-2725). The attack process was complicated by a small target scope of vulnerability exploits. Its attacking techniques gradually evolved into a simpler and more efficient RDP brute-force attack.
The attack process is as follows. First, attackers use brute-force scanning and other techniques to obtain permissions from a weak host in the network. The then upload hack toolkits to perform brute-force scanning or password extraction, and select critical servers and PCs for encryption. The whole process can be described as “first breach one host and then take the entire network,” as shown below:
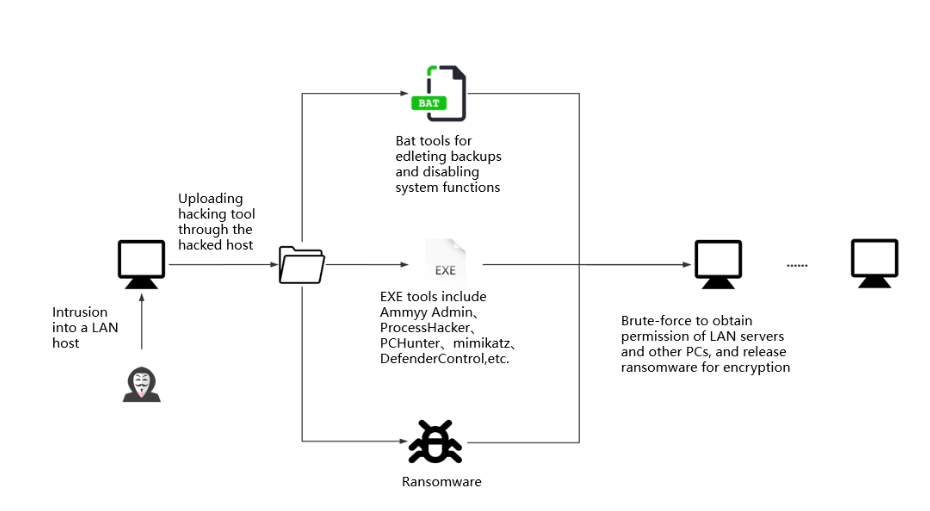
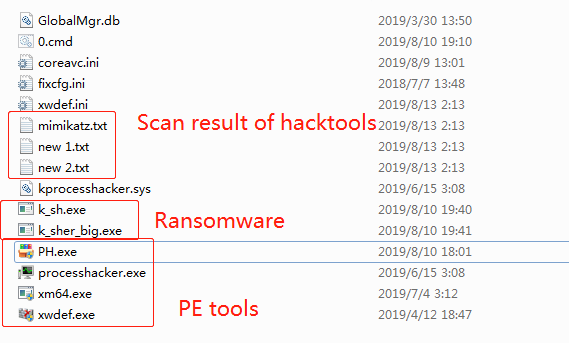
During the tracing process, The Sangfor Security Team found several toolkits left by attackers. Toolkits include ransomware vectors, open-source or existing scanners, control tools, as well as attacker’s self-made batch scripting tools.
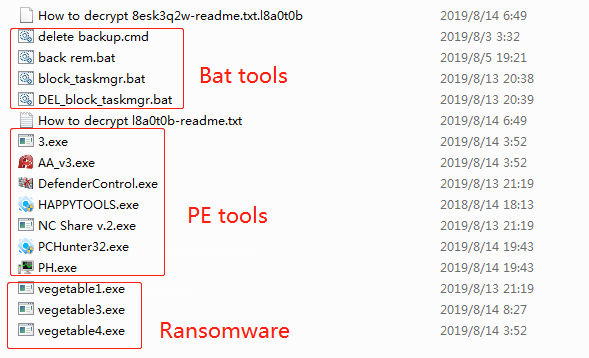
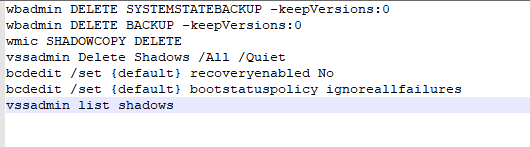
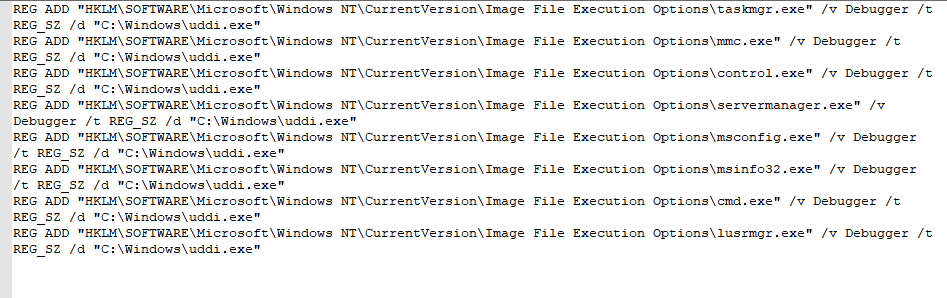
ProcessHacker, PCHunter, DefenderControl and xwdef are used to uninstall security software on the host and disable Windows Defender. Batch files are mainly used to delete system backup and disable system functions.
Attackers sometimes use “mimikatz” to extract passwords from the intranet, then employ a remote desktop or remote-control tools to connect to target hosts, making intranet devices vulnerable to attackers and causing unmeasurable damage.
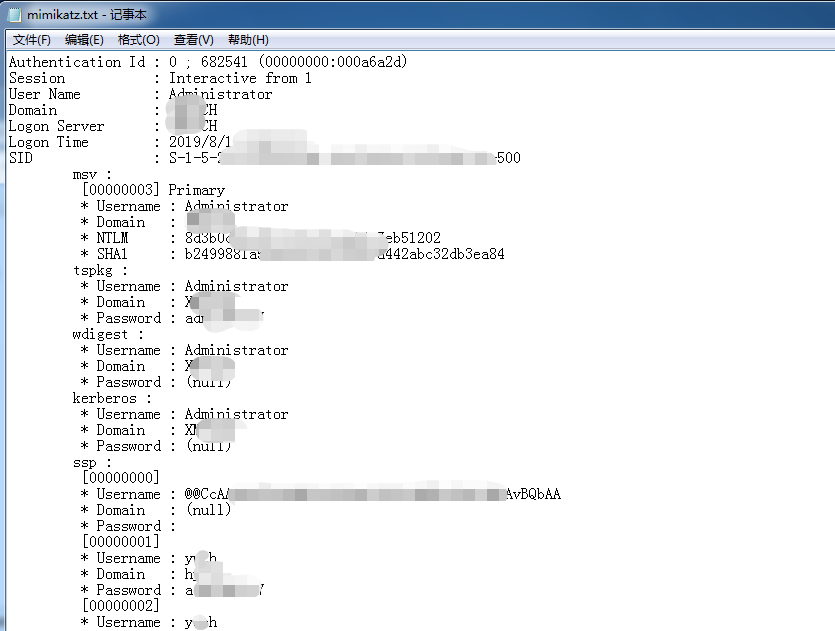
Industrialization of Sodinokibi Ransomware
The outbreak of the Sodinokibi ransomware is mainly due to its industrialized operation, i.e., the virus is operated by a team. Each member has his own duties and are paid based on their individual performance. Once the virus is executed on a compromised host, it leaves a .txt ransom note with random name like xxx-readme.txt, as shown below:
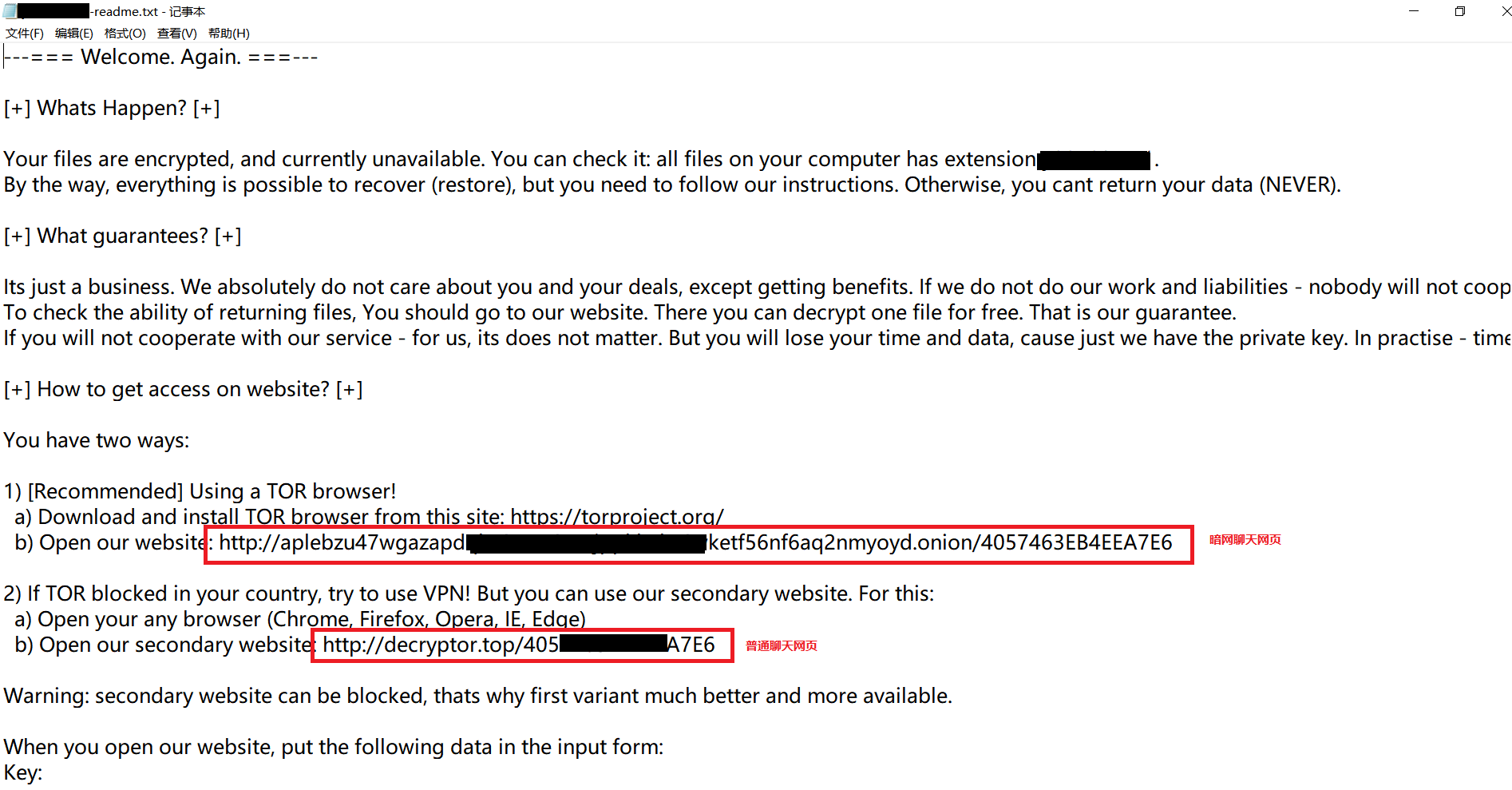
The ransom note contains two URLs for victims to contact hackers. One is a dark website for online chatting and the other is a normal website for online chatting. Victim enterprises can visit either one to get contact with hackers. After visiting the provided URL, victims can discuss the ransom amount and method of payment with hackers. The webpage design is very professional.
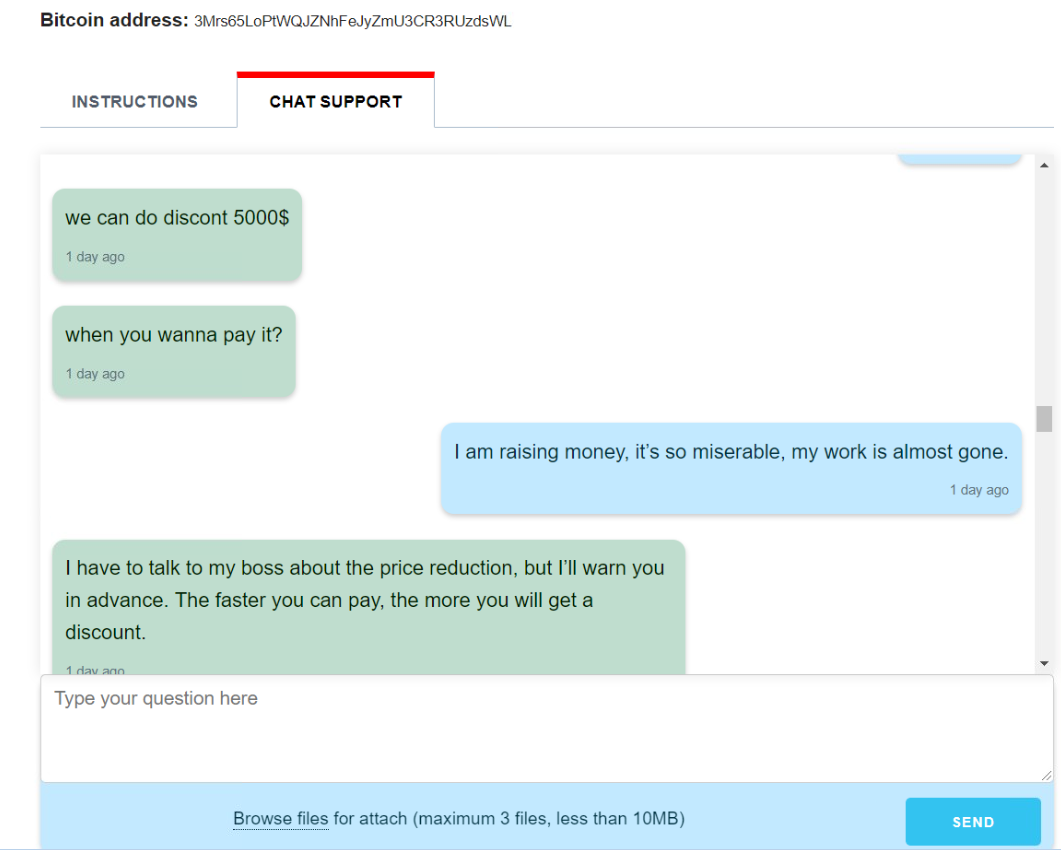
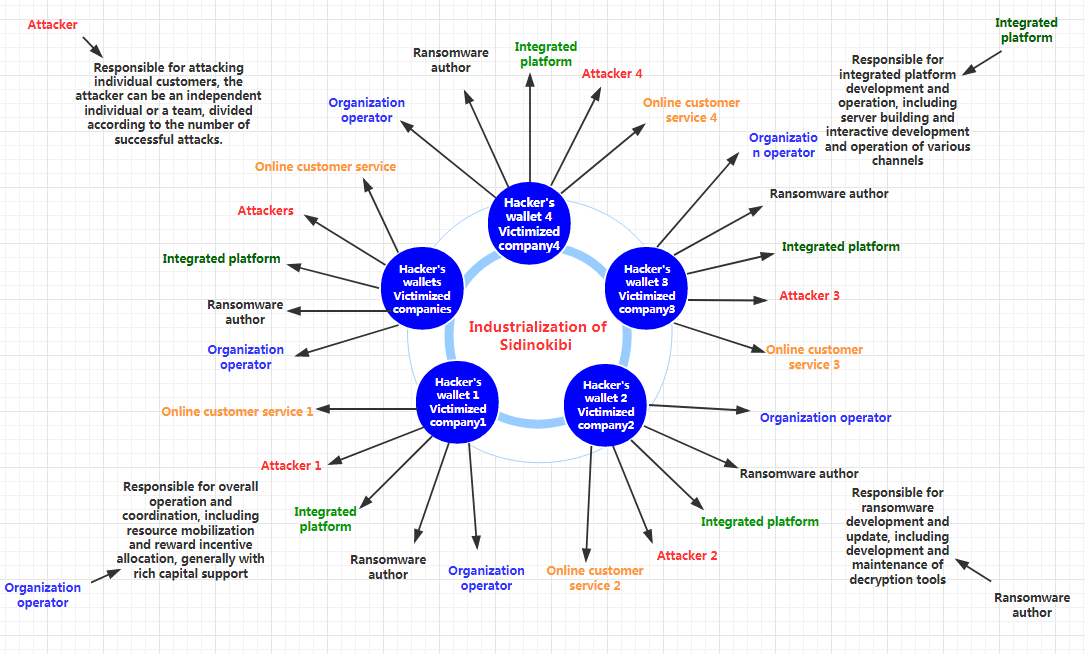
This hacker group has become an industrialized team. Hackers normally do not communicate with victims directly, instead hiring a group of unaffiliated personnel to provide 24/7 online customer service and negotiate ransom amount with victims. It is wise for hackers to outsource their customer service tasks, which are easy but require many of people and quite long working hours. Regardless of the customer service method, the ransom amount is ultimately decided by the Sodinokibi ransomware organizer.
The Sodinokibi ransom is high, ranging from 3 to 6 bitcoin. Its primary targets are large and middle-sized enterprises. Hackers aims to paralyze critical business networks forcing organizations to pay the ransom to recover their core business services.
Because the ransomware virus attack is industrialized, every participant can profit. As the Sangfor Security Team tracked this virus, they found that when victims transfer bitcoin to the attacker’s wallet, the bitcoin ransom is immediately transferred to another participants' wallet.
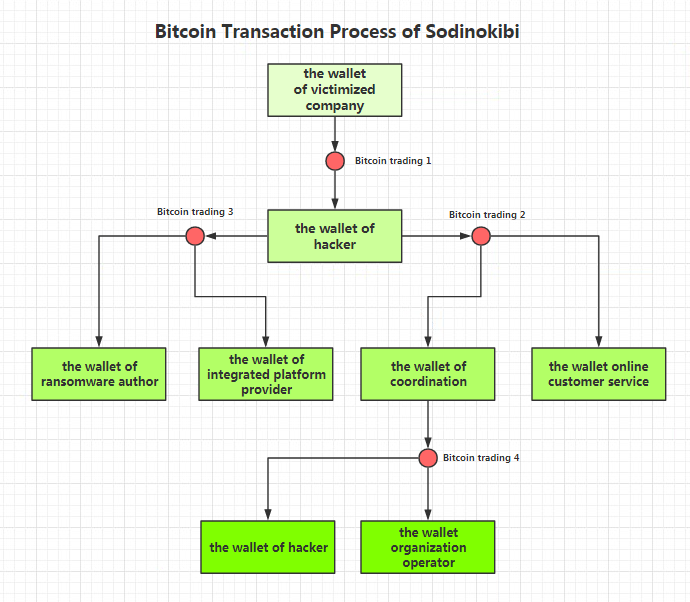
After the attack succeeds and ransom is paid, the ransom is transferred to four different electronic wallets in two different batches. These four wallets belong to the ransomware author, integrated platform provider, online customer service personnel and the hacker group respectively, as shown below:
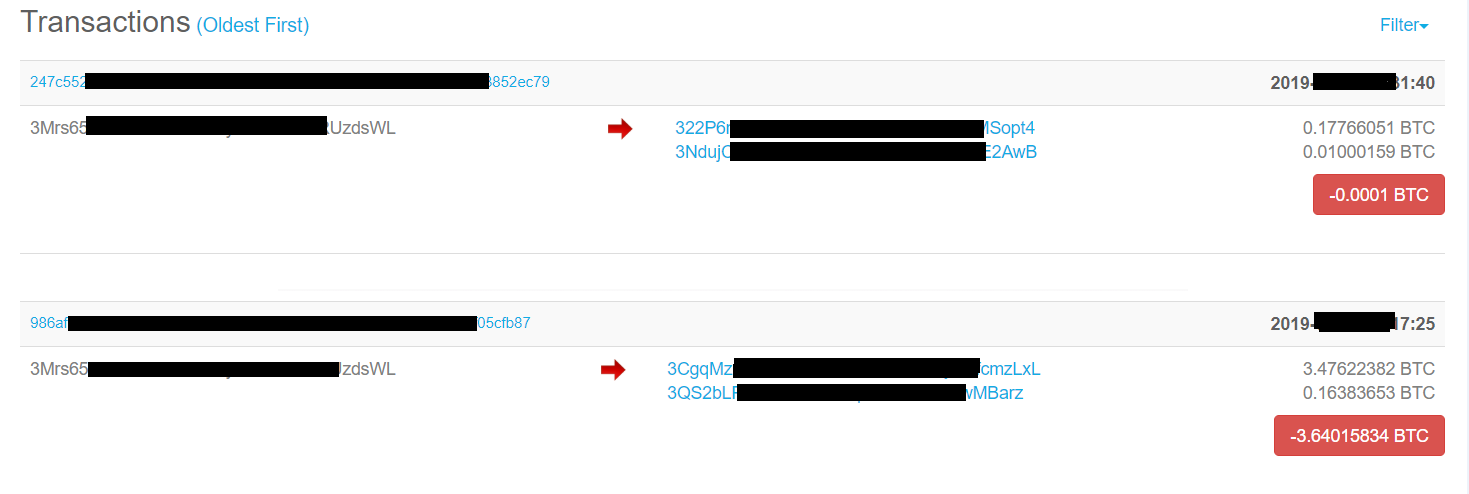
The ransomware author and integrated platform provider receive commissions for every transaction, so even though the profit for each attack is small, the total amount earned is quite large when combined. Online customer service personnel are paid based on performance, receiving payment for each ransom they collect. The customer service personnel are not paid particularly well because their work is relatively easy and they are replaceable.
A majority of the ransom obtained from every attack goes to the attacker and the event organizer. The former is an individual or penetration team who professionally attack enterprises and contribute the most to the security event. Any individual or team may join an attack, working like a sales team to gain considerable profits from every order. The organizer makes connections between different roles and all operations, thus receiving the greatest portion of the ransom.
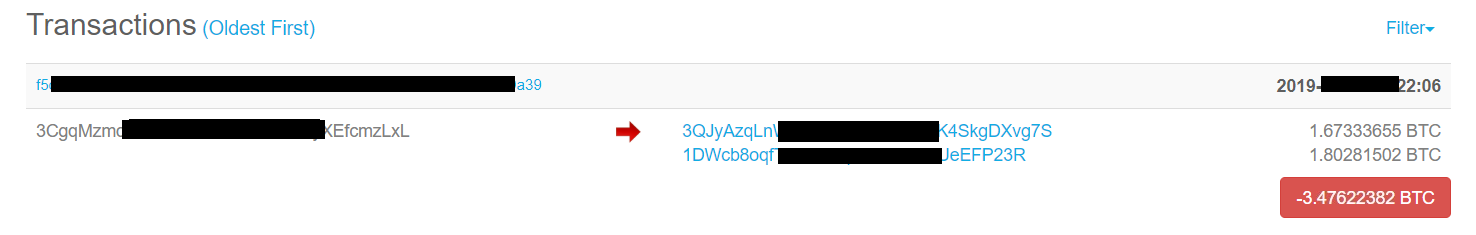
The transaction flow chart is as follows:
The industrial operations of Sodinokibi ransomware is as follows:
Solutions
Prevalence of this ransomware poses great risk to business systems. Sangfor has developed a complete solution from the perspective of vulnerability and response efficiency. As we know, weaknesses (vulnerabilities, weak passwords and open ports) in computers and servers are the root of and entry point for ransomware, though the organizations’ core servers are protected from brute-force attacks, weak passwords, etc. Ransomware is different from ordinary viruses, as it poses a short-term risk to enterprises and remediation must be professional, efficient and performed as quickly as possible to minimize impact.
The Sangfor Security Team Recommends:
1. Fix the vulnerability quickly by installing the corresponding patch on the host.
2. Back up critical data files regularly to other hosts or storage devices.
3. Do not click on any email attachment from unknown sources and do not download any software from untrusted websites.
4. Disable unnecessary file sharing.
5. Strengthen your computer password and do not use the same passwords for multiple computers to avoid compromising a series of computers.
6. Disable RDP if it is unnecessary for your business. When computers are attacked, use Sangfor NGAF or EDR to block port 3389 and stop the virus from spreading.
7. Sangfor NGAF and EDR can prevent brute-force attacks. Turn on brute-force attack prevention on NGAF and enable Rules 11080051, 11080027 and 11080016. Turn on brute-force attack prevention on Sangfor EDR.
8. For Sangfor NGAF customers, update NGAF to version 8.0.5 and enable AI-based Sangfor Engine Zero to achieve the most comprehensive protection.
9. Deploy Sangfor security products and connect to cloud-based Sangfor Neural-X to detect new threats.
10. Subscribe to the Sangfor Security Operations service to strengthen your existing security system and check security policies, threats, risks, relevant vulnerabilities and more, while subsequently updating policies to enhance security protection.
In the event of ransomware intrusion, you may reach us by any of the following means to gain consultancy and support services for free:
1) Call us at +60 12711 7129 (7511)
2) Follow Sangfor Tech Support public account on WeChat.
3) Visit Sangfor Community (http://community.sangfor.com) Live Chat.





