What is CVE - Common Vulnerabilities and Exposures?
CVE, short for common vulnerability and exposure, is a database of publicly disclosed IT security vulnerabilities and exposures.
CVE also refers to individual vulnerabilities and exposures that are assigned a unique CVE identifier (CVE ID) and added to the database (CVE List). A CVE Record is published for each CVE to provide details of the vulnerability to the public free of charge.
The Difference Between Vulnerability and Exposure
Vulnerabilities are flaws in computer software, firmware, hardware, and service components that can be exploited by a threat actor to gain unauthorized access and carry out a cyber-attack.
Exposures are errors not inherent to the software, firmware, hardware, or service component that put it at risk of being exploited, such as misconfigurations, open ports, and weak credentials.
Vulnerabilities in computer software (including software applications, operating systems, kernels, and software components) are the most recorded and exploited and, therefore, this article mainly refers to vulnerabilities in the context of software vulnerabilities.

The Importance of CVEs
Accelerated digital transformation of recent years has spurred the use of information technology in business settings. Nowadays, organizations rely on a multitude of applications, systems, and devices from various vendors to run their operations. This has widened their attack surface and presented cybercriminals with more options for launching successful attacks. Indeed, software vulnerabilities are one of the most exploited attack vectors (path of network intrusion) in cyber-attacks.
Cybercriminals are on the constant lookout for software vulnerabilities and are extremely fast at developing the malware and techniques to exploit them. Vulnerabilities have been exposed in widely used products from prominent software vendors, such as Microsoft, VMware, and Apache to name a few. Notorious vulnerabilities like Log4Shell, ProxyLogon, and EternalBlue have led to widescale cyber-attacks, including the infamous WannaCry global ransomware attack in 2017.
Keeping track of CVEs is thus vital to sound vulnerability management and can help organizations stave off devastating cyber-attacks. Read on to learn about the CVE Program and how to make use of CVEs to protect your organization.

How Does the CVE Program Work?
The CVE database is managed by the National Cybersecurity FFRDC, a Federally Funded Research and Development Center dedicated to cybersecurity and operated by the MITRE Corporation. MITRE Corp is a U.S. not-for-profit organization funded by the Cybersecurity and Infrastructure Security Agency (CISA), part of the U.S. Department of Homeland Security (DHS).

Vulnerabilities and exposures are regularly discovered by software vendors, security researchers, and even users. When a vulnerability is discovered, it is reported to a CVE Numbering Authority (CNA), also known as a CVE Program participant or partner. CNAs are entities authorized by the CVE Program to assign CVE IDs to vulnerabilities and publish CVE Records within their own scopes of coverage (e.g., vulnerabilities in their own products). As of October 2022, there are 240 CNAs from 35 countries participating in the CVE Program. They are mostly large software vendors (e.g., Microsoft, Google, Adobe, Red Hat), as well as open-source projects, coordination centers, bug bounty service providers, hosted services, and research groups.
When a CNA is made aware of a vulnerability, it assigns the vulnerability with a CVE ID and creates a CVE Record (previously known as CVE Entry). In fact, CNAs are issued blocks of CVE IDs, which they hold in reserve to assign to newly discovered vulnerabilities. At this point, the vulnerability is not yet disclosed to the public and goes through further investigation, validation, and remediation. Once this process is complete, the CNA submits details of the vulnerability, including the vulnerability type, affected versions, impact, root cause, and solutions such as patches and workarounds. Once the minimum data elements have been submitted, the CVE Record is published to the public for downloading and viewing.
CVE Records are published on CVE’s official website and the National Vulnerability Database (NVD), which is part of the National Institute of Standards and Technology (NIST). CNAs also publish their own security advisories on their official websites, as do security companies such as Sangfor.
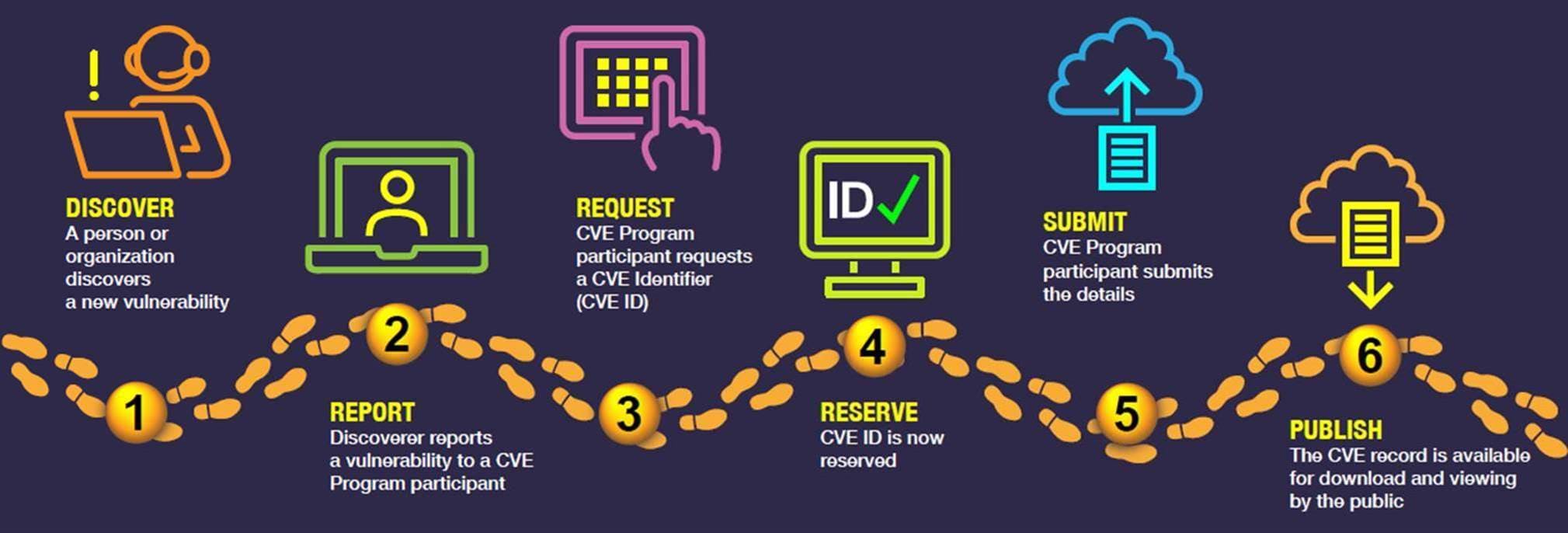
The CVE Record Lifecycle (image courtesy of cve.org)
What is Included in a CVE Record?
As alluded to above, a CVE Record contains various data elements about a particular vulnerability. We will go through each one of these in a more detail to help you understand their relevance.
CVE ID
The CVE ID is a vulnerability’s unique identifier. The standard format of a CVE ID is "CVE-YYYY-NNNN", where CVE is a fixed prefix, YYYY is the year in which the CVE ID was assigned (not necessary the same as when the CVE Record was published), and NNNN is a random number with at least four digits. CVE IDs are especially helpful for distinguishing vulnerabilities in the same product that may be very similar but are ultimately different.
Description
This section provides a short summary of the vulnerability, including its type, the root cause, and the kind of impact that it could lead to. This information helps users better understand the nature and risks of the vulnerability.
Severity
The severity of a vulnerability is measured using the Common Vulnerability Scoring System (CVSS). The current version of CVSS is v3.1. There are three different CVSS Scores: Base, Temporal, and Environmental.
- The Base Score is derived from the inherent characteristics of the vulnerability and does not change over time.
- The Temporal Score is based on the vulnerability’s status at a particular point in time, such as whether any patches are available or whether it has been exploited in the wild.
- The Environmental Score is a customized score based on an organization’s IT environment. Organizations can calculate an Environmental Score using the CVSS Score calculator.
A CVE Record typically only provides the CVSS Base Score, and thus, this is the score that will be discussed in greater detail.
The CVSS Base Score ranges from 0 to 10, with 10 the most severe and 0 posing no risk.
| CVSS Base Score | Severity |
|---|---|
| 0 | None |
| 0.1 – 3.9 | Low |
| 4.0 – 6.9 | Medium |
| 7.0 – 8.9 | High |
| 9.0 – 10 | Critical |
The CVSS Base Score is derived from various inherent characteristics of the vulnerability, which are further divided into Exploitability, Scope, and Impact.
Exploitability Metrics
Exploitability metrics reflect the ease and technical means by which the vulnerability can be exploited. There are four exploitability metrics, Attack Vector, Attack Complexity, Privileges Required, and User Interaction.
- Attack Vector: Attack vector refers to the level of access the attacker needs to exploit the vulnerability. The four attack vectors in the order of decreasing difficulty are: Network, Adjacent, Local, and Physical. Network means that the vulnerability can be exploited remotely over the internet, while Physical means that physical interaction with the vulnerable software is needed for exploitation.
- Attack Complexity: Attack complexity refers to whether there are any conditions beyond the attacker’s control that must be present to exploit a vulnerability. These conditionals include certain configurations and additional user interaction. Attack complexity is rated either Low or High, where Low means little or no such conditions and High means the existence of such conditions.
- Privileges Required: Privileges required refers to the level of access privileges the attacker needs to exploit a vulnerability. Privileges is rated None, Low, or High, where Low means basic user access and High means admin or root permissions.
- User Interaction: User interaction refers to whether the attacker needs to manipulate the user into carrying out certain actions to exploit the vulnerability, such as clicking on a link. User interaction is rated either Yes or No.
Scope
Scope refers to the vulnerability’s ability to impact another piece of software or component beyond its resources and privileges. For example, a vulnerability in a piece of software may allow an attacker to access to the underlying operating system. Scope is rated either Changed or Unchanged.
Impact Metrics
Impact metrics measure the potential effects of an attack that successfully exploits the vulnerability. There are three impact metrics, Confidentiality, Integrity, and Availability, which are rated None, Low, or High.
- Confidentiality: The amount of data that an attacker gains access to.
- Integrity: The extent to which an attacker can alter data.
- Availability: The extent to which an attacker can make data unavailable.
References
This section provides a list of references relating to the vulnerability. At least one reference is required for the CVE Record to be published. References is the all-important section for users as it includes the security advisory published by the software vendor. Vendor advisories include the patches and workarounds needed to remediate or mitigate the vulnerability. Other resources such as third-party advisories and proof of concepts by security companies are also helpful for learning more about the vulnerability.
Affected Versions
This section lists the versions of the software or component that are affected by the vulnerability. This information helps users verify whether they are using a vulnerable version and need to take relevant action.

The Value of CVE to Enterprises
The CVE Program is a valuable tool that helps organizations with vulnerability management. IT security administrators can learn of any vulnerabilities in the software used by the organization and are provided with guidance on fixing the issue. Moreover, CVSS Scores help administrators plan and prioritize remediation efforts, as there may be many vulnerabilities across all software at any given point in time. A CVSS Environmental Score derived from the CVSS Score calculator further helps security administrators gauge the risk of the vulnerability to their organization.
Vulnerability Management Best Practices

However, with so many kinds of software used in the environment, it can be overwhelming to keep track of all the vulnerabilities. That is why it is recommended to carry out a thorough asset identification exercise where all software and other IT assets are counted and sorted. This will go a long way in helping IT security administrators ensure that all software is up to date.
This process can be facilitated with certain security tools, such as Sangfor Cyber Command. Cyber Command is a Network Detection and Response (NDR) solution that provides complete visibility of users, devices, applications, and services running on the network through continuous traffic monitoring and analysis. This enables NDR to not only detect hidden threats in the network but also identify outdated software and services. Security administrators will always know when to install updates to ensure timely vulnerability remediation.
Visit the Cyber Command webpage to discover its features and capabilities, use cases, industry recognitions, videos, and more.
Sangfor FarSight Labs Threat Intelligence
Users can also conveniently keep track of the newest vulnerabilities by following Sangfor FarSight Labs at https://sec.sangfor.com/security-vulnerability?lang=EN-US or a selection of the most relevant and critical vulnerabilities at https://www.sangfor.com/farsight-labs-threat-intelligence.
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





