3CX incident report reveals a double software supply chain attack
Last month, 3CX, a major supplier of business phone systems, suffered a massive supply chain attack. The attack has had far-reaching consequences given that the company serves over 160 countries and 600,000 business clients worldwide, with more than 12 million daily active users. In response, 3CX appointed Mandiant as its security incident response team to investigate the attack. On April 11, 3CX released an interim assessment in which Mandiant attributes the attack to a group identified as UNC4736. According to Mandiant, UNC4736 is believed to have connections with North Korea.
Image source: https://www.3cx.com/blog/news/mandiant-initial-results/
Recently, Mandiant published a blog article to report on the incident, revealing that 3CX had been compromised in a double software supply chain attack. In the first attack, UNC4736 tampered with X-TRADER, a professional trading application developed by US-based Trading Technologies International, Inc. Eric Chien, Technical Director of Symantec’s Security Technology and Response division, told The Hacker News in a statement that the attacks took place between September 2022 and November 2022.
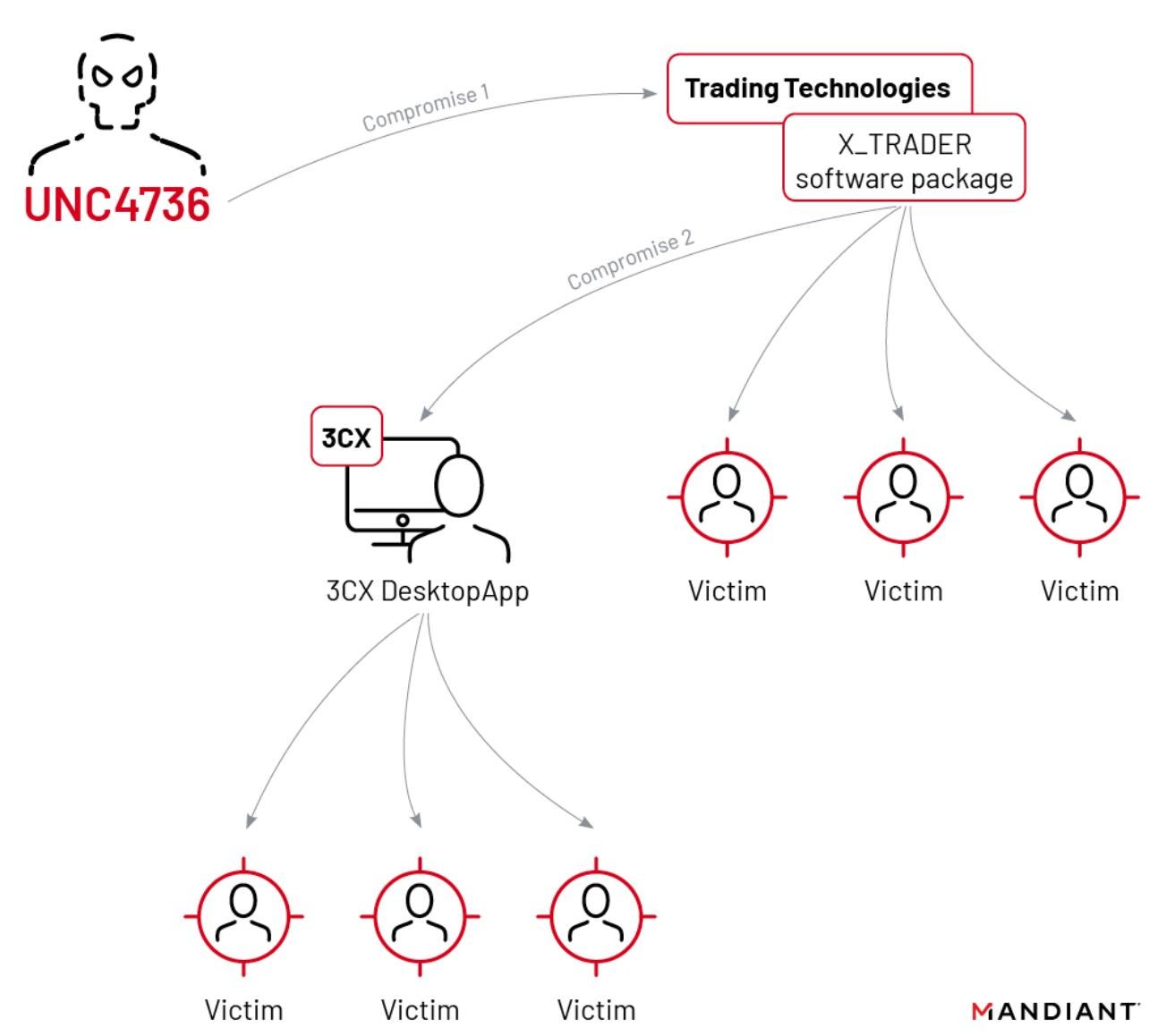
Image source: https://www.mandiant.com/resources/blog/3cx-software-supply-chain-compromise
While X_TRADER was retired in 2020, it was still available for download from the official Trading Technologies website in 2022. The digital certificate of the malware-laced X_TRADER installer and the executable file Setup.exe were signed by “Trading Technologies International, Inc” and was set to expire in October 2022. In a security update on April 20, 3CX disclosed that the breach occurred when a 3CX employee downloaded the trojanized X-TRADER application installer, giving the attacker access to the company’s internal network. Eventually, the attacker was able to compromise the Windows, Linux, and macOS build environments, altering code, and implanting backdoors. Sangfor FarSight Labs captured a Linux-based sample whose code features are similar to those mentioned in Mandiant’s article on the incident. We suspect that this could be one of the components used by the group to target Linux platforms and have conducted a detailed analysis of the component.
The Symantec Threat Hunter Team later reported that the trojanized X_TRADER installer was used to breach two critical infrastructure organizations in the energy sector and two other businesses involved in financial trading, confirming that the X_TRADER software supply chain attack affected more organizations than 3CX.
Rising exploitation of digital certificates
Digital certificates are issued by a trusted certificate authority (CA) for software and applications. With a valid digital certificate installed for a specific software or application on your computer, you will not encounter alerts when launching it.
However, in recent years, threat actors have developed various methods to bypass the security authentication mechanisms of digital certificates. One common technique is using valid digital certificates of legitimate software and applications to sign malware. Since malware signed with valid certificates are typically deemed secure by most endpoint security software, they are more challenging to detect and thus exhibit greater boldness in executing malicious activities. According to a study by Venafi, Machine Identities Drive Rapid Expansion of Enterprise Attack Surface, the number of cyberattacks that misuse machine identities increased by more than 700% over the last five years (machine identities refer to digital certificates and encryption keys like SSL/TLS certificates and SSH keys that are used to authenticate and safeguard interconnected computers and devices). Sangfor FarSight Labs has also detected an increase in malware samples with valid digital signatures.
There are two primary reasons that contribute to this trend:
- Digital certificate leakage: For instance, in February 2022, the Lapsus$ hacker group leveraged two stolen code signing certificates used by NVIDIA to sign its drivers and executables to distribute malware. The breach resulted in a significant amount of data being stolen from NVIDIA and the attacker started leaking the data online after NVIDIA refused to negotiate with them.
- CAs' lack of rigorous validation process: For instance, Microsoft rolled out a new driver signing policy starting from Windows 10, version 1607, which requires all drivers to be submitted to the Windows Hardware Developer Center Dashboard portal (Dev Portal) to be digitally signed by Microsoft. However, due to oversight in the validation process, Microsoft mistakenly signed the malicious FiveSys rootkit with a valid digital certificate, allowing the malware to evade detection and slip unnoticed onto users’ Windows systems.
New threat actor dubbed YoroTrooper responsible for attacks against various countries in Eastern Europe and Central Asia
Since March 2022, Sangfor FarSight Labs has observed attacks by an unknown threat actor targeting various countries in Eastern Europe, the Middle East, and Central Asia. The attacks had previously been attributed to the Kasablanka group due to the use of LodaRAT. However, further analysis led to the identification of a new group, dubbed YoroTrooper or APT-LY-1006 in March 2023. The first attack of the group could be traced back to March 2022, at the onset of the Russo-Ukrainian War in February 2022. Based on the targets, we surmise that this new group emerged as a result of the ongoing conflict between Russia and Ukraine and thus named the group WarSunflower.
Our analysis reveals that this group has launched numerous attacks across Commonwealth of Independent States (CIS), including Russia, Belarus, Azerbaijan, Turkmenistan, Uzbekistan, Kyrgyzstan, Tajikistan, and Kazakhstan, as well as Bulgaria, Afghanistan, and India. The group mainly targets government entities and the energy and aerospace industries with the intention of stealing sensitive information. Based on the targeted countries and entities, motive, active time zones (between UTC+2 and UTC+4), and language characteristics, it can be inferred that this threat actor is a cyber espionage group based in Eastern Europe or Central Asia.
Analysis of their toolkit shows that it excels at modifying open-source tools instead of developing their own. It mainly relies on spear-phishing attacks to gain initial access, but no advanced infiltration techniques have been detected thus far, suggesting that this group possesses low to medium technical capabilities.
Patchwork returns with improved techniques to launch new attacks against educational and scientific research institutes in China
Recently, Sangfor Security Service Emergency Response Center identified new attacks targeting universities and scientific research institutes in China. Leveraging the Hybrid Graph AI Model developed by Sangfor Research Institute of Innovation, we have attributed the attacks to the Patchwork APT group.
Patchwork, also known as Monsoon, Dropping Elephant, APT-Q-36, and APT-C-09, is an APT group from South Asia. It mainly carries out cyber-espionage attacks in China, Pakistan, and other countries in Asia, with the intention of stealing sensitive information. This group was first observed in November 2009 and has been active ever since. Its attacks in China mainly target government agencies and scientific research and educational institutes.
In the recent campaign, Patchwork used phishing emails with attachments named Guiding Opinions on Protecting Women's Rights and Interests [Revised by ACWF in 2023]*, Notice on Application Guidelines for Four Key Projects, including Advanced Structures and Composite Materials, in 2023*, and 2023 Recruitment Announcement of CISPDR*.
*Translated from the original version in Chinese
These emails contain a description of sexual harassment in the workplace, a notice on a project application, and recruitment information, respectively, tricking users into opening a password-protected compressed file. The compressed file contains an INK file that downloads BADNEWS RAT as the second-stage payload. After analysis, we found that this group has updated BADNEWS by improving the call sequence and method of its key functions, replacing control commands and adjusting the implementation of relevant functions, and replacing some key strings.
Sangfor’s AI Model confirms that the CNC APT group forged legitimate files to steal data from universities and scientific research institutes
Recently, Sangfor FarSight Labs and Sangfor Security Service Emergency Response Center detected new attacks against universities and scientific research institutes in China. The attacks have been attributed to CNC (APT-C-48) based on analysis using the aforementioned Hybrid Graph AI Model. Scientific research institutes in China have increasingly been targeted by international APT groups since Northwestern Polytechnical University suffered a cyberattack in 2022. Based on our monitoring, CNC has conducted multiple cyber-espionage attacks against educational and scientific research institutes in China since January 2023. The group was also found to have attacked a university in Pakistan and has been active in the Philippines and Indonesia for the first time.
Based on currently known information, CNC was first detected in 2019 and has carried out frequent spear-phishing attacks against military, educational, scientific research, and aerospace institutions in China. Its objective is to steal high-tech research materials or plans from its targets. The group is suspected to be linked with the Patchwork APT group.
This group is known for masquerading malware as legitimate files of Chinese software, and such technique was also detected in recent attacks with file names such as imagedrvhost.exe, YoudaoDictHelp.exe, and YoudaoDictDesk.exe. Analysis of the components involved in the attacks reveals that their functions are the same as those of the USB-based Trojan previously attributed to CNC. The communication characteristics, such as the communication mode and URL format, also correspond with the group's known practices.





