1. Summary
| Vulnerability Name | Windows LSA Spoofing Vulnerability (CVE-2022-26925) |
|---|---|
| Release Time | May 11, 2022 |
| Component Name | Local Security Authority (LSA) |
| Affected Versions | Windows 7, 8.1, RT, 10, 11 Windows Server 2008, 2012, 2016, 2019, 2022, 20H2 See Section 3 Affected Versions for details |
| Vulnerability Type | Remote Code Execution |
| Exploitability | Attack Vector: Network Attack Complexity: High Privileges Required: None User Interaction: None |
| Description | Severity: CVSS v3 Base Score: 8.1 (High) Confidentiality Impact: High Integrity Impact: High Availability Impact: High |
2. About CVE-2022-26925
2.1 Introduction
Local Security Authority (LSA) is the central component of the security subsystem in the Microsoft Windows operating system. LSA is responsible for managing interactive logons to the system. It authenticates and logs users on to the local computer.
2.2 Summary
On May 11, 2022, Sangfor FarSight Labs received a notice about the Windows LSA spoofing vulnerability (CVE-2022-26925), classified as high severity, with a CVSS Score of 8.1 (assigned by Microsoft).
An unauthenticated attacker could call a method on the LSARPC interface and coerce the domain controller to authenticate the attacker using Windows NT LAN Manager (NTLM). Once the attacker gets the NTLM hash by the NTLM relay attack, the attacker can further use the leaked main controller NTLM hash to attack the system.
The combined CVSS score would be 9.8 (critical) when this vulnerability is chained with the noted NTLM Relay Attacks on Active Directory Certificate Services (AD CS).
CVE-2022-26925 has been detected to be exploited in the wild and has been added to CISA's Known Exploited Vulnerabilities Catalog.
3. Affected Versions
Windows 7 for 32-bit Systems Service Pack 1
Windows 7 for x64-based Systems Service Pack 1
Windows 8.1 for 32-bit systems
Windows 8.1 for x64-based systems
Windows RT 8.1
Windows 10 Version 1607 for 32-bit Systems
Windows 10 Version 1607 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for x64-based Systems
Windows 10 Version 21H1 for 32-bit Systems
Windows 10 Version 21H1 for ARM64-based Systems
Windows 10 Version 21H1 for x64-based Systems
Windows 10 Version 21H2 for 32-bit Systems
Windows 10 Version 21H2 for ARM64-based Systems
Windows 10 Version 21H2 for x64-based Systems
Windows 10 for 32-bit Systems
Windows 10 for x64-based Systems
Windows 11 for ARM64-based Systems
Windows 11 for x64-based Systems
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2012
Windows Server 2012 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 R2 (Server Core installation)
Windows Server 2016
Windows Server 2016 (Server Core installation)
Windows Server 2019
Windows Server 2019 (Server Core installation)
Windows Server 2022
Windows Server 2022 (Server Core installation)
Windows Server, version 20H2 (Server Core Installation)
4. Solutions
4.1 Remediation Solutions
4.1.1 Check the System Patch Installation
1) Run "systeminfo" in a CMD window and it will display a list of details about the system, including what patches are installed as shown below.
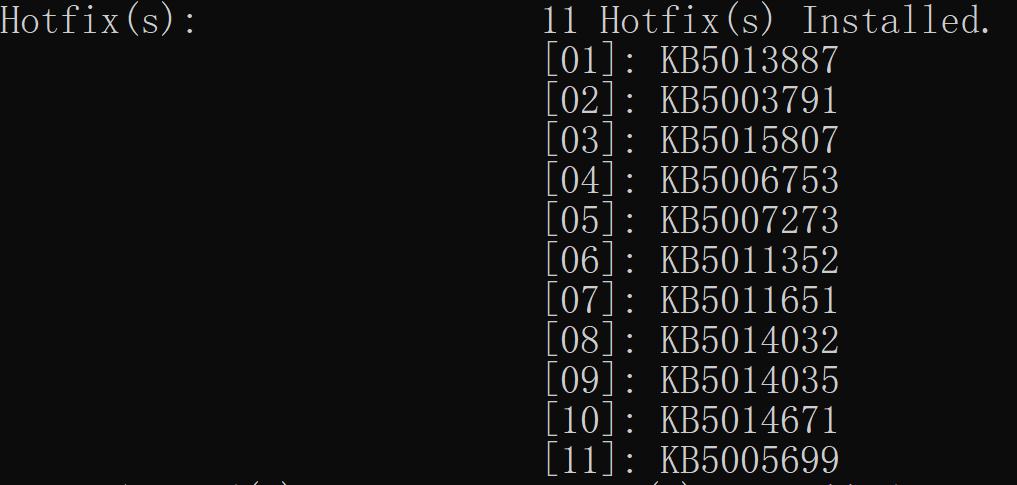
2) Check if the patch corresponding to your OS is installed. Patches for affected OS versions can be found in the link below: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-26925
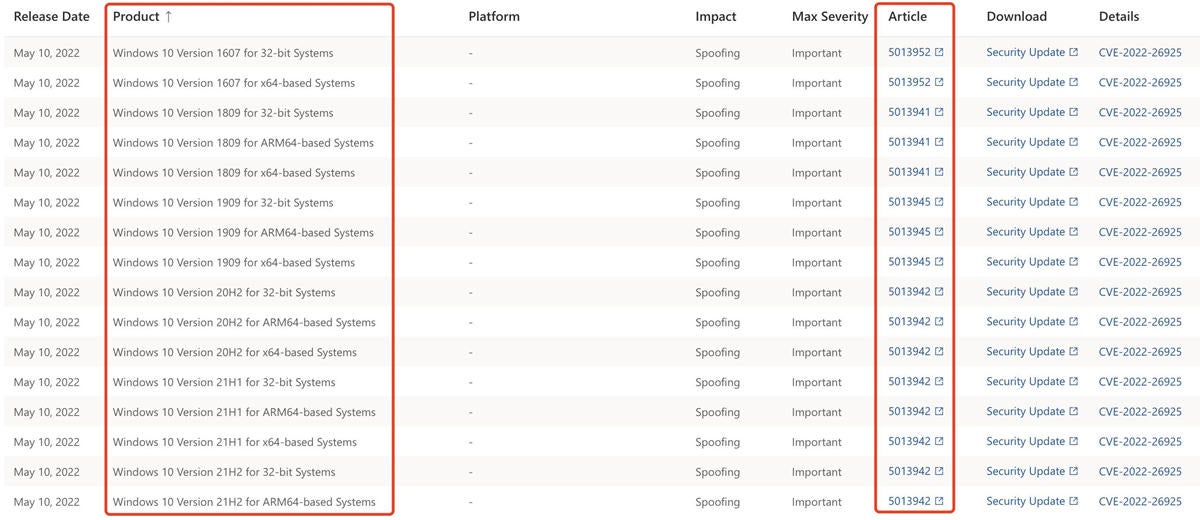
3) If the patch is not installed, proceed to "4.1.2 Microsoft Solution" to download and install the patch.
4.1.2 Microsoft Solution
Microsoft has released a patch for affected OS versions to fix this vulnerability. Please download the patch corresponding to the affected OS from the following link: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-26925
4.2 Sangfor Solutions
4.2.1 Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the Windows LSA Spoofing vulnerability (CVE-2022-26925):
4.2.2 Security Protection
The following Sangfor products and services provide protection against the Windows LSA Spoofing vulnerability (CVE-2022-26925):
- Sangfor NGAF (Next Generation Firewall)
5. Timeline
On May 11, 2022, Sangfor FarSight Labs received a notice about the Windows LSA Spoofing vulnerability (CVE-2022-26925).
On May 11, 2022, Sangfor FarSight Labs released a vulnerability alert with remediation solutions.
6. Reference
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-26925
7. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





