1. Summary
| Vulnerability Name | PHP Remote Code Execution Vulnerability (CVE-2022-31626) |
|---|---|
| Release Time | June 10, 2022 |
| Component Name | PHP |
| Affected Versions | 8.1.0 ≤ PHP < 8.1.7 8.0.0 ≤ PHP < 8.0.20 7.0.0 ≤ PHP < 7.4.30 |
| Vulnerability Type | Remote Code Execution |
| Exploitability | Attack Vector: Network Attack Complexity: Low Privileges Required: Low User Interaction: None |
| Impact | Severity: CVSS v3 Base Score: 8.8 (High) Confidentiality Impact: High Integrity Impact: High Availability Impact: High |
2. About CVE-2022-31626
2.1 Introduction
PHP (recursive acronym for PHP: Hypertext Preprocessor) is a widely used open-source general-purpose scripting language for web development and can be embedded into HTML.
2.2 Summary
On June 10, 2022, Sangfor FarSight Labs received a notice about a PHP remote code execution vulnerability (CVE-2022-31626), which is classified as high severity with a CVSS score of 8.8.
A buffer overflow vulnerability was found in PHP when processing passwords in mysqlnd/pdo in mysqlnd_wireprotocol.c. When using the pdo_mysql extension with mysqlnd driver, if a third party is allowed to connect to the host and supplies a MySQL database server password in the mysqlnd driver, a password of excessive length can trigger a buffer overflow in PHP. This flaw allows a remote attacker to pass a password (with an excessive length) via PDO to the MySQL server, triggering arbitrary code execution on the target system.
3. Affected Versions
8.1.0 ≤ PHP < 8.1.7
8.0.0 ≤ PHP < 8.0.20
7.0.0 ≤ PHP < 7.4.30
4. Solutions
4.1 Remediation Solutions
4.1.1 Check the Component Version
Option 1. Check PHP Command
Enter the following command in the PHP installation path (this operation can be performed in any directory of PHP configured with environment variables)
php -v or php --version

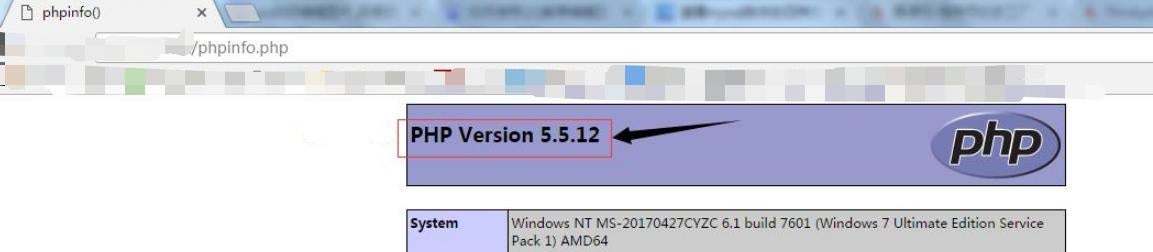
Option 2. Check phpinfo Page
Create a phpinfo.php file in the root directory of the website with the following content:
<?php phpinfo(); ?>
Visit this page after creation to view the current version.
4.1.2 PHP Solution
Users can update their affected products to the latest version to fix the vulnerability.
- For Windows Users: https://windows.php.net/download
- For Linux Users: https://www.php.net/downloads.php
4.2 Sangfor Solutions
4.2.1 Active Detection
The following Sangfor products and services actively detect assets affected by the PHP Remote Code Execution Vulnerability (CVE-2022-31626):
Sangfor Cyber Guardian (Managed Detection and Response)
4.2.2 Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the PHP Remote Code Execution Vulnerability (CVE-2022-31626):
- Sangfor Cyber Command (Network Detection and Response)
- Sangfor Cyber Guardian (Managed Detection and Response)
5. Timeline
On June 10, 2022, Sangfor FarSight Labs received a notice about the PHP Remote Code Execution Vulnerability (CVE-2022-31626).
On June 10, 2022, Sangfor FarSight Labs released a vulnerability alert with remediation solutions.
6. Reference
https://bugs.php.net/bug.php?id=81719
7. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





