1. Summary
| Vulnerability Name | Apache Spark Command Injection Vulnerability (CVE-2022-33891) |
|---|---|
| Release Time | July 19, 2022 |
| Component Name | Apache Spark |
| Affected Versions | Apache Spark ≤3.0.3 3.1.1≤ Apache Spark ≤3.1.2 3.2.0≤ Apache Spark ≤3.2.1 |
| Vulnerability Type | Command Injection |
| Exploitability | Attack Vector: Network Attack Complexity: Low Privileges Required: None User Interaction: None |
| Impact | Severity: CVSS v3 Base Score 8.8 (High) Confidentiality Impact: High Integrity Impact: High Availability Impact: High |
2. About CVE-2022-33891
2.1 Introduction
Apache Spark is an open-source, distributed system for processing big data workloads. It utilizes in-memory caching and optimized query execution for fast queries against data of any size.
Apache Spark provides APIs for popular programming languages, including Java, Scala, Python and R. It offers code reuse across many workloads such as batch processing, interactive queries, real-time analytics, machine learning, and graph processing.
2.2 Summary
On July 18, 2022, Sangfor FarSight Labs received a notice about the Apache Spark Command Injection vulnerability (CVE-2022-33891), classified as high severity with a CVSS Base Score of 8.8.
The Apache Spark UI offers the possibility to enable ACLs via the configuration option spark.acls.enable. With an authentication filter, this checks whether a user has access permissions to view or modify the application. If ACLs are enabled, a code path in HttpSecurityFilter can allow someone to perform impersonation by providing an arbitrary user name. A malicious user might then be able to reach a permission check function that will ultimately build a Unix shell command based on their input, and execute it. This will result in arbitrary shell command execution as the user Spark is currently running as.
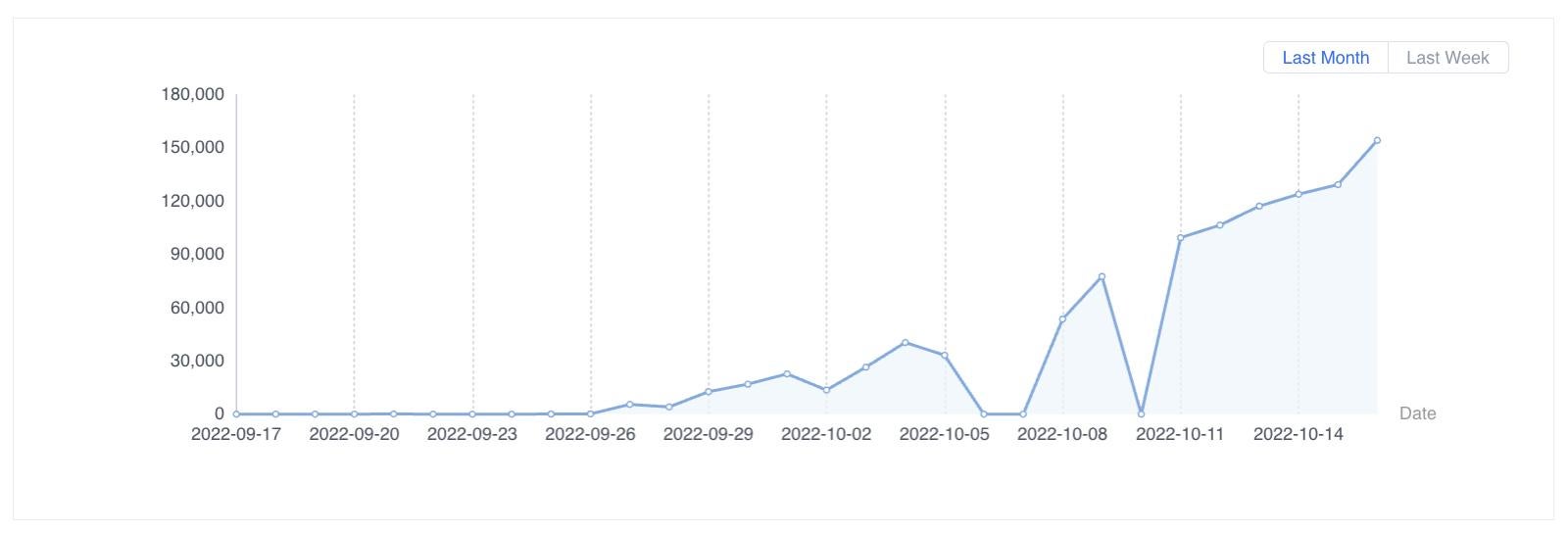
Figure 1. Exploits of CVE-2022-33891 detected by Sangfor from Sep 17 to Oct 16, 2022
3. Affected Versions
Apache Spark ≤3.0.3
3.1.1≤ Apache Spark ≤3.1.2
3.2.0≤ Apache Spark ≤3.2.1
4. Solutions
4.1 Remediation Solutions
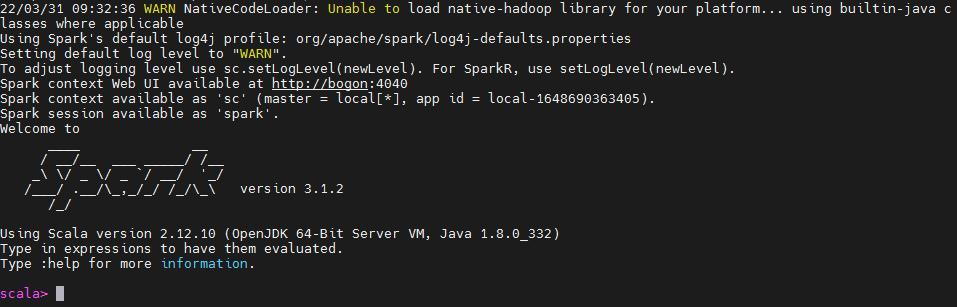
4.1.1 Check the Component Version
Run spark-shell command. The version information will be displayed.
4.1.2 Apache Solution
Users can update their affected products to the latest version to fix the vulnerability:
https://spark.apache.org/downloads.html
4.2. Sangfor Solutions
4.2.1. Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the Apache Spark Command Injection vulnerability (CVE-2022-33891):
- Sangfor Cyber Command (Network Detection and Response)
- Sangfor Cyber Guardian (Managed Detection and Response)
4.2.2. Security Protection
The following Sangfor products and services provide protection against the Apache Spark Command Injection vulnerability (CVE-2022-33891):
- Sangfor NGAF (Next Generation Firewall)
- Sangfor Cyber Guardian (Managed Detection and Response)
5. Timeline
On July 18, 2022, Sangfor FarSight Labs received a notice about the Apache Spark Command Injection vulnerability (CVE-2022-33891).
On July 19, 2022, Sangfor FarSight Labs released a vulnerability alert with remediation solutions.
6. Reference
https://nvd.nist.gov/vuln/detail/CVE-2022-33891
https://github.com/apache/spark/pull/35946
7. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





