Summary
| Vulnerability Name | Craft CMS Remote Code Execution (CVE-2025-32432) |
| Released on | April 28, 2025 |
| Affected Component | Pixel & Tonic's Craft CMS |
| Affected Version | 3.0.0-RC1 ≤ Craft CMS < 3.9.15 4.0.0-RC1 ≤ Craft CMS < 4.14.15 5.0.0-RC1 ≤ Craft CMS < 5.6.17 |
| Vulnerability Type | Remote code execution |
| Exploitation Condition |
|
| Impact | Exploitation difficulty: easy. Attackers can exploit this vulnerability to execute arbitrary code without authorization. Severity: critical. This vulnerability may result in remote code execution. |
| Official Solution | Available |
About the Vulnerability
Component Introduction
Pixel & Tonic's Craft CMS is a popular content management system (CMS) dedicated to providing designers and developers with flexible tools to create beautiful websites and excellent digital experiences.
Vulnerability Description
On April 28, 2025, Sangfor FarSight Labs received notification of the remote code execution vulnerability in Craft CMS (CVE-2025-32432), classified as critical in threat level.
Specifically, Craft CMS contains a critical vulnerability. Unauthorized attackers can exploit this vulnerability in combination with the input validation vulnerability in the Yii framework (CVE-2024-58136) to compromise servers and steal sensitive data.
Details of this vulnerability have been disclosed, and in-the-wild exploits of this vulnerability have been reported.
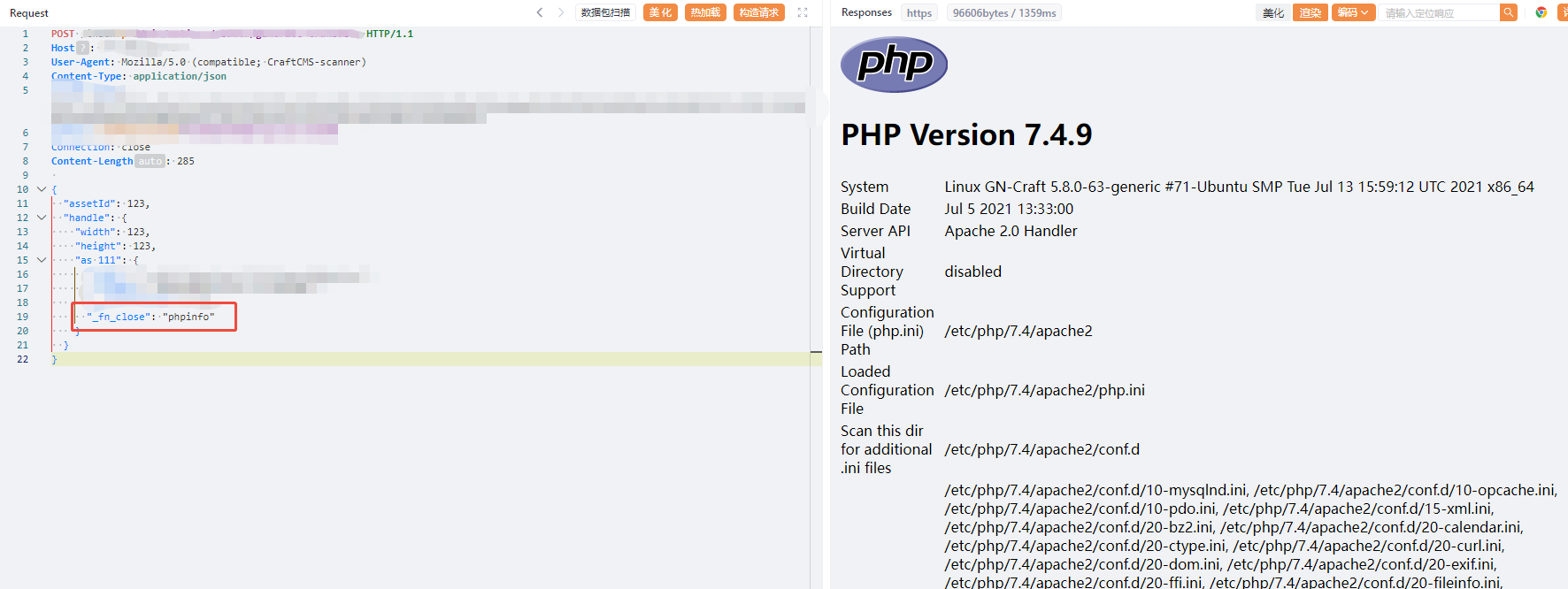
Affected Versions
The following Craft CMS versions are affected:
- 3.0.0-RC1 ≤ Craft CMS < 3.9.15
- 4.0.0-RC1 ≤ Craft CMS < 4.14.15
- 5.0.0-RC1 ≤ Craft CMS < 5.6.17
Vulnerability Reproduction
Sangfor FarSight Labs has reproduced this vulnerability.
Solutions
Remediation Solutions
Official Solution
The latest version has been officially released to fix the vulnerability. Affected users are advised to update Craft CMS to one of the following versions as needed:
- Craft CMS 3.9.15
- Craft CMS 4.14.15
- Craft CMS 5.6.17
Download link: https://github.com/craftcms/cms/releases
Sangfor Solutions
Risky Asset Discovery
The following Sangfor products can detect vulnerable Craft CMS assets in batch scenarios:
- Sangfor Endpoint Secure: Fingerprint ID 0030795
- Sangfor Host Security: Fingerprint ID 0030795
- Sangfor TSS: Fingerprint ID 0030795
Vulnerability Detection
- Sangfor Host Security: Rule ID SF-2025-00481 (May 4, 2025)
- Sangfor TSS: Rule ID SF-2025-00988 (May 12, 2025)
- Sangfor Cyber Guardian Platform: Rule ID SF-2025-00988 (May 12, 2025)
- Sangfor XDR: Rule ID SF-2025-00481 (May 4, 2025)
Vulnerability Monitoring
- Cyber Command: Rule ID 11027496 (May 9, 2025)
- Sangfor Cyber Guardian Platform: Rule ID 11027496 (May 9, 2025)
- Sangfor XDR: Rule ID 11027496 (May 9, 2025)
Vulnerability Prevention
- Network Secure: Rule ID 11027496 (May 9, 2025)
- Sangfor Web Application Firewall: Rule ID 11027496 (May 9, 2025)
- Sangfor Cyber Guardian Platform: Rule ID 11027496 (May 9, 2025)
- Sangfor XDR: Rule ID 11027496 (May 9, 2025)
Timeline
- April 28, 2025: Vulnerability reported to Sangfor FarSight Labs
- April 28, 2025: Public alert issued
References
Learn More
Sangfor FarSight Labs researches the latest cyber threats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyber threats, providing fast and easy protection for customers.





