Introduction to the Purdue Model
The Purdue Model is a widely recognized framework for securing Industrial Control Systems (ICS) and Operational Technology (OT) environments. This model, which organizes network architecture into a series of hierarchical layers, plays a critical role in maintaining cybersecurity in industries such as energy, manufacturing, and transportation. By employing network segmentation, the Purdue Model ensures secure operations across diverse industrial systems. As IT and OT systems become increasingly interconnected through technologies like the Industrial Internet of Things (IIoT) and cloud computing, the Purdue Model OT has evolved to meet new challenges while still offering a solid foundation for cybersecurity.
The Evolution of the Purdue Model
The Purdue Model was developed in the 1990s by researchers at Purdue University to address the growing complexity and vulnerabilities of industrial systems. Initially designed for isolated ICS networks, the model aimed to provide a structured approach to network segmentation and security in industrial environments. While not directly formalizing the Purdue Model, standards like ISA-95 and ISA-99 have played a crucial role in supporting the model’s principles. These standards provide complementary guidance for industrial automation and security, helping standardize practices that align with the Purdue Model’s layered approach.
Over time, the Purdue Model was formalized through international standards such as ISA-95 and ISA-99 , and has since become a cornerstone in ICS and OT security.
With the convergence of IT and OT systems, along with the rise of cloud computing and the IIoT (Industrial Internet of Things), the traditional Purdue Model has had to adapt. As industrial environments become more interconnected and dynamic, the model has evolved to address modern challenges, such as securing data flows across increasingly complex, hybrid networks.
Understanding the Purdue Model Diagram
The Purdue Model is traditionally structured into five levels (0–4). In modern implementations, a sixth logical layer (Level 3.5 or Industrial DMZ) and even a Level 5 (cloud/business planning) are added to accommodate modern architectures.
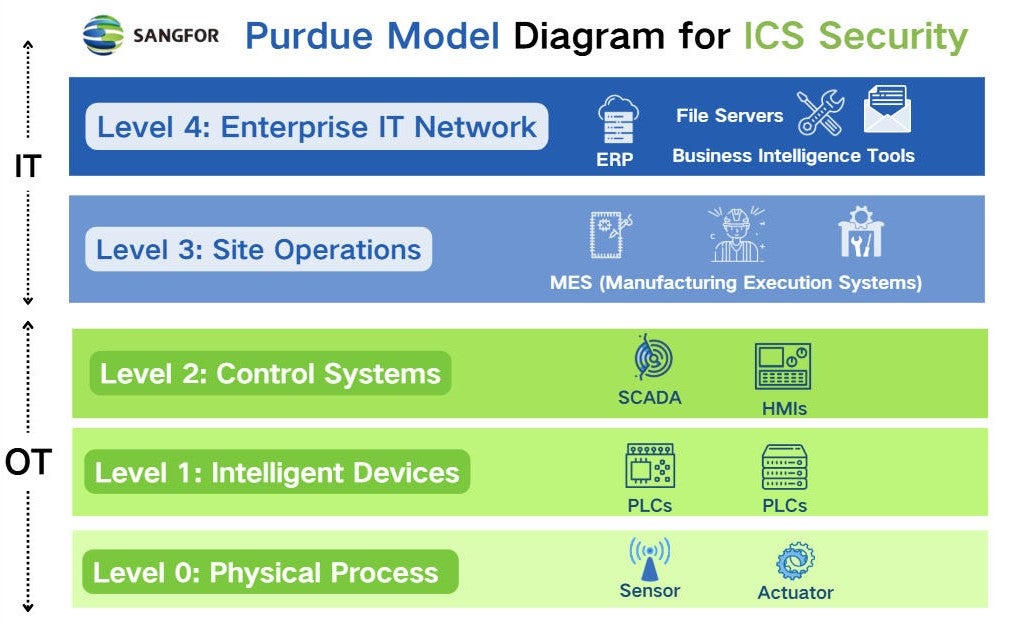
The Purdue Model diagram visually represents a layered approach to industrial network security, each with distinct functions and security requirements:
- Level 0: Physical Process – This level includes sensors, actuators, and machinery that directly interact with physical processes.
- Level 1: Intelligent Devices – Devices such as PLCs (Programmable Logic Controllers) and IEDs (Intelligent Electronic Devices) control physical processes, enabling automation and real-time control.
- Level 2: Control Systems – SCADA (Supervisory Control and Data Acquisition) systems and HMIs (Human-Machine Interfaces) monitor and manage operations at the control level, ensuring smooth functioning of critical systems.
- Level 3: Site Operations – Manufacturing Execution Systems (MES) and batch controls coordinate operations at the site level, linking plant-level activities with enterprise IT systems.
- Level 3.5: Industrial DMZ – An isolation zone between IT and OT networks, the Industrial Demilitarized Zone (iDMZ) is designed to prevent lateral movement of threats between the two environments.
- Level 4: Enterprise IT Network – This level consists of systems such as ERP (Enterprise Resource Planning), business intelligence tools, and file servers, typically used for business operations and data processing.
- Level 5: Cloud/Business Planning – The highest layer includes cloud platforms, remote access services, and global supply chain management systems.
Each layer in the Purdue Model plays a critical role in ensuring the overall security of ICS and OT systems by limiting unauthorized access and protecting sensitive data.
ICS & OT Use Cases for the Purdue Model
The Purdue Model has been successfully applied across multiple industries to enhance cybersecurity and streamline operations. Some key use cases include:
- Energy: In power generation and substations, the Purdue Model ensures secure communication protocols, helping to mitigate the risk of cyberattacks that could disrupt critical energy infrastructure.
- Oil & Gas: In this sector, the model segregates drilling automation systems and other critical networks to prevent cyber threats from spreading across operational systems.
- Manufacturing: The Purdue Model helps control the flow of sensitive data and restricts the spread of malware by isolating different parts of the factory network, ensuring that cyber threats don’t compromise the entire production line.
- Pharmaceuticals: The model aids in meeting validation and compliance requirements by segmenting networks, making it easier to control access to sensitive production and testing environments.
As industries such as Smart Cities, Healthcare, and Transportation continue to adopt more connected devices and systems, the Purdue Model is adapting to meet the evolving security needs of these sectors.
Implementing the Purdue Model
Adopting the Purdue Model for ICS and OT security requires a systematic approach to network segmentation and access control. The following steps can help organizations successfully implement the model:
- Asset Inventory: Begin by cataloging all devices, systems, and network components within each layer. For example, identify PLCs at Level 1 and SCADA systems at Level 2.
- Network Segmentation: Define clear security zones based on operational needs. This helps to isolate critical systems from less-sensitive areas and limits the impact of potential security breaches.
- Access Control: Establish strict access policies that regulate communication across layers. Limiting cross-layer communication reduces the attack surface and prevents unauthorized access to critical systems.
- Monitoring and Logging: Deploy tools such as Intrusion Detection/Prevention Systems (IDS/IPS) and Security Information and Event Management (SIEM) systems to continuously monitor network traffic and identify potential security incidents.
By following these steps, organizations can effectively apply the Purdue Model to secure their ICS and OT environments, reducing the likelihood of cyberattacks and improving overall network resilience.
Purdue Model in the Age of Cloud and Zero Trust
New technologies such as cloud computing, IIoT and Zero Trust have significantly reshaped the way the Purdue Model is applied. These advancements bring both opportunities and challenges for securing ICS and OT systems.
- Zero Trust: The Zero Trust model assumes that threats can exist both inside and outside the network. By enforcing strict verification for every access request, Zero Trust enhances security by limiting lateral movement within the network. This model is particularly effective in environments where traditional network perimeters are no longer sufficient.
- Cloud: With the rise of cloud services, organizations can now extend the Purdue Model’s segmentation to cloud environments. Layer 5 in the Purdue Model (Cloud/Business Planning) often includes cloud platforms, which are becoming an integral part of modern industrial operations.
The Purdue Model for OT has evolved to meet new challenges, including the dynamic, interconnected nature of modern industrial environments. These technologies require more flexible security measures to ensure that OT systems are adequately protected.
Real-World Example: NotPetya Malware
The NotPetya ransomware attack in 2017 serves as a stark reminder for organizations failing to properly implement network segmentation. Initially, the malware infiltrated the IT network via a compromised software update (specifically, the MeDoc software used by Ukrainian firms), and from there, it spread to the internal network. It leveraged the EternalBlue exploit to rapidly move laterally, ultimately affecting OT systems in critical sectors like energy, manufacturing, and logistics.
Had the Purdue Model been properly implemented, particularly its Industrial DMZ (Level 3.5) and the isolation between IT and OT networks, the malware’s ability to move laterally across networks would have been significantly constrained. The segmented network zones would have limited the malware’s impact, preventing its spread from the IT network (Level 4) to the OT systems (Level 0-3), and thus reducing downtime and potential damage.
This incident underscores the importance of adhering to established cybersecurity frameworks such as the Purdue Model, which emphasizes strong network segmentation. Furthermore, integrating emerging security concepts like Zero Trust and micro-segmentation can further strengthen defenses by ensuring that every device and user is verified before granting access, thus minimizing the potential attack surface.
References:
- Cybersecurity and Infrastructure Security Agency (CISA), "Alert (TA17-181A) - NotPetya Ransomware"
https://www.cisa.gov/uscert/ncas/alerts/TA17-181A - Microsoft Security Blog, "NotPetya: The Worst Cyberattack in History"
https://www.microsoft.com/security/blog/2018/07/24/notpetya-the-worst-cyberattack-in-history/
Conclusion
The Purdue Model remains a vital framework for securing ICS and OT environments. As industries evolve and adopt new technologies like cloud computing, IIoT, and Zero Trust, the Purdue Model continues to adapt, offering a flexible yet robust defense strategy. Organizations should not abandon the Purdue Model but rather evolve it to meet contemporary cybersecurity challenges, ensuring the protection of critical infrastructure and industrial operations.
Frequently Asked Questions
No, the Purdue Model remains a foundational framework for securing ICS and OT systems. While it requires adaptation to handle modern challenges, it continues to provide a solid foundation for network segmentation and security.
ICS refers to technologies like SCADA and PLCs used for control and monitoring of industrial systems, while OT encompasses a broader range of operational technology, including field devices and machinery.
Yes, the Purdue Model’s Level 5 has been adapted to include cloud platforms, which are increasingly important in modern industrial environments.
The Purdue Model traditionally consists of five layers (0–4). However, in modern implementations, a sixth logical layer (Level 3.5, or Industrial DMZ) is added to enhance network segmentation and security. Additionally, some implementations include a Level 5 (cloud/business planning) to accommodate the integration of IT and OT networks. These layers correspond to specific operational functions and security domains, allowing for tailored protection at each level of the network.





