Sangfor Engine Zero
What is Engine Zero?
Background
Malicious software or Malware is in the business of doing harm to data, devices and people. Viruses, worms and spyware are all variants of a very dangerous and quick growing menace to your safety and that of your business. In recent years the majority of devastating attacks were launched using notorious Ransomware and Cryptojacking programs costing millions.
Malware is excellent at its job – and you need to be excellent at yours to defend against it. Traditional security systems and anti-virus are successful at identifying existing signatures but are defenseless against more recent highly malleable and malicious threats. Hackers often just create new variants of existing malware or leverage effective zero-day techniques against you and your business. How do you defend against this constantly evolving threat? You need to evolve.
Innovation Overview
Artificial Intelligence technology has empowered Sangfor to develop its own in-house malware detection engine to defend against threats known, and unknown. Our dedicated R&D and Security team - composed of data scientists, security analysts and white hat researchers, are continuously developing & enhancing this engine in conjunction with one of the most exciting technological advancements of our time - AI.
“Engine Zero” has been created to ensure that zero threats will affect your network and give you complete and wholistic protection against zero-day vulnerabilities. Engine Zero is only one of many malware inspection engines embedded in Sangfor’s network security solutions, end point solution and Neural-X cloud platform.
Traditional Approaches
Signature Based Detection
Often used by traditional anti-virus vendors, hash (MD5) of all known malicious files are computed and stored in an anti-virus database. Each time a suspicious file is inspected, its MD5 is computed and then compared against the other files existing in the AV database. While this method is effective, fast and industry-tested, it requires daily upkeep of a huge database of known malware samples, often hundreds of megabytes, and daily endpoint updates. While maintaining this constant vigilance is still valuable and effective at combating known malware, it is still ineffective against fast-evolving malware and malware variants.
YARA Type Script Engine
This script examines the suspected files/directories and matches strings as they are defined in the YARA rules with the file. YARA approach does a better job than AV in terms of covering more families of malware however still falls short in detecting newly created malware.
Virtual Execution/Sandboxing
Virtual execution and sandboxing is the process of detonating malware within a controlled virtual environment and monitoring the post execution behavior. The nature of malware presents several challenges to this method. Malware is getting smart enough to recognize when it’s in a sandbox environment and learns to avoid them in the future if the sandbox isn’t invisible (and they usually aren’t). The other challenge with sandboxing is that it takes a long time for inspection, and often not broadly deployed at all parts of the network, or even at many organizations, allowing malware to bypass it.
How Does It Work
Designed by dozens of Ph.Ds, scientists, security analysts and white hat hackers, Engine Zero combs the entire suspected file, categorizing it’s finds into multiple features. All agree that machine learning is powering the way we protect ourselves and also how technology will continue to grow, and Engine Zero employs several of these effective and jaw-dropping techniques.
Based on years of diligent security research on malware characteristics, Sangfor has developed a supervised learning model. To train and ensure the accuracy of this model, we then applied tens of millions of malware samples while using advanced Artificial Intelligence capabilities to enable our engines to run and teach themselves, expanding our capacity to discover unknown malware and their families.
Engine Zero is not the only line of defense within Sangfor’s security portfolio, including network gateways, endpoint protections and cloud-based security as a service. Other defense including threat intelligence, sandboxing, and botnet detection capabilities are all working in concert to provide a comprehensive coverage for malware detection.

Engine Zero Advantages
- Accurate: In recent tests our malware detection rate scored the highest in terms of accuracy, surpassing other vendors and open source alternatives.
- Fast: This engine is very efficient and utilizes very little resource. Only such efficiency can provide malware inspection on the network gateway with very little performance impact.
- Coverage: Coverage of known and zero-day attacks. Our engine released in June of 2017 has proven itself able to detect high-profile malware such as BadRabbit ransomware, first seen in Oct, 2017, without any previous signatures.
Engine Zero Validation: Unmatched Protection for Ransomware
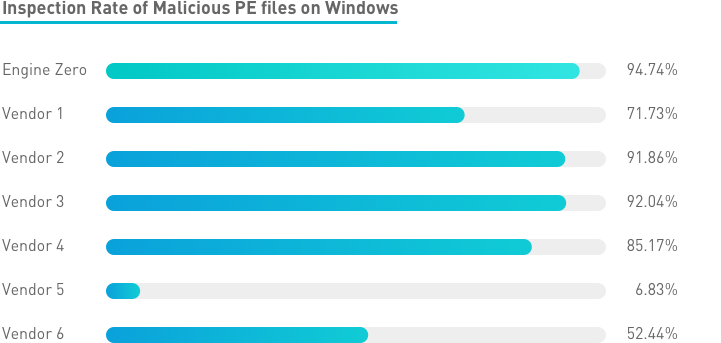
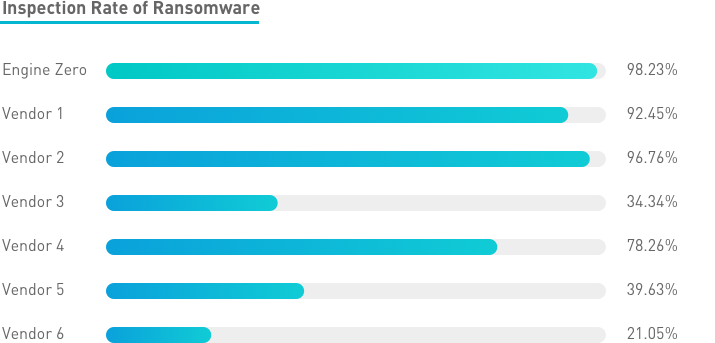
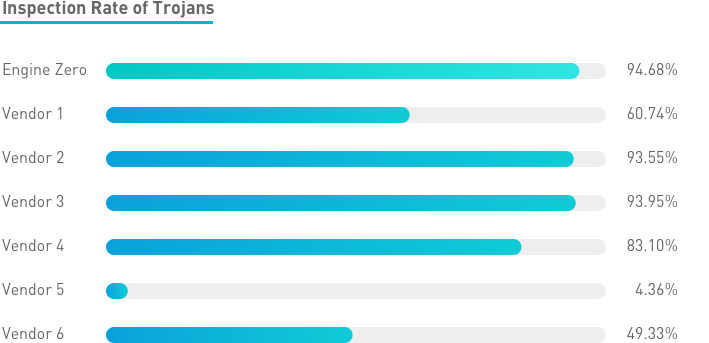
While money-motivated attackers have been developing and deploying more and more sophisticated ransomware, Engine Zero’s advanced AI capability has proven itself highly effective against it. The higher our success rate, the harder hackers need to work to create widespread weaponized tools that are unique or variations on known malware.
Click here to learn more about the history & evolution of Ransomware.
Engine Zero and Ransomware
Engine Zero’s supervised training and Artificial Intelligence has proven itself the best defense against ransomware offering:
- Adaptability: Demonstrated to offer the best coverage for known and unknown ransomware even without prior training (example: BadRabbit).
- Accuracy: In 60,000 recent ransomware sample tests, Engine Zero scored the highest among similar solutions.
- Speed: Customers using our next-generation firewall (NGAF) can use Engine Zero to detect ransomware at line rate.
