What is SIEM?
Today, Security Information and Event Management (SIEM) is the cornerstone of most security operations. SIEM aggregates, analyzes, and stores event data to detect security threats, facilitate incident response and perform forensics. Data is collected from different log sources (such as servers, security products and network devices) to identify, track and mitigate abnormal activity across the organization. Log management and reporting are also used to meet regulatory compliance requirements.
Benefits of SIEM
As a well-established tool, SIEM is used in many mid-size and large organizations globally. There are currently over 20+ SIEM vendors so the available market is quite large.
Some of the benefits of SIEM are:
- Significantly shorten the time to identify threats, and thus minimizing potential damage.
- More granular threat detection and security alerts, enabling quicker and easier analysis of security issues, leaks, or breaches.
- Storage of all enterprise event data in a centralized and easily accessible location, thus providing a holistic view of almost the entire information security environment.
- Scalability for organizations with a large amount of data, or those expecting to compile a large amount of data in the future.
- Flexibility for using the data, logs, security programs to support audit & compliance reports, help desk and network troubleshooting.
Limitations of SIEM
However, SIEM does have practical limitations on its effectiveness and ROI. For example, traditional SIEM solutions are not very dynamic because they rely heavily on preconfigured correlation rules and attack patterns to identify suspicious events. Being log based, there is still much activity that SIEM cannot see and correlate making it difficult to detect new and unknown threats or attacks.
SIEM presents a variety of limitations including:
- High initial cost and higher operation costs.
- A long implementation period (often 90+ days) due to integration and correlation with various security controls, products, and hosts throughout the infrastructure.
- A skilled security is required for successful SIEM deployment and tuning while often requiring integrating into security operations center (SOC).
- Easy misconfiguration of SIEM tools is common, making risk management less effective due to noise from too many false positive alerts.
- Poor correlation response with network and endpoint devices.
- Performance issues when processing and managing extremely large amounts of incoming log data.
- Logs are vulnerable to tampering: attackers can cover their tracks by turning off, modifying, or erasing logs.
- Cannot see events not in logs because some devices (like IoT) do not generate logs or capture layer 3 events.
Due to these SIEM limitations, many new or unknown attacks or risks are missed.
How is Sangfor Cyber Command Different from SIEM?
SIEM is based solely on events from system and application logs. But if there is no log then there is no event.
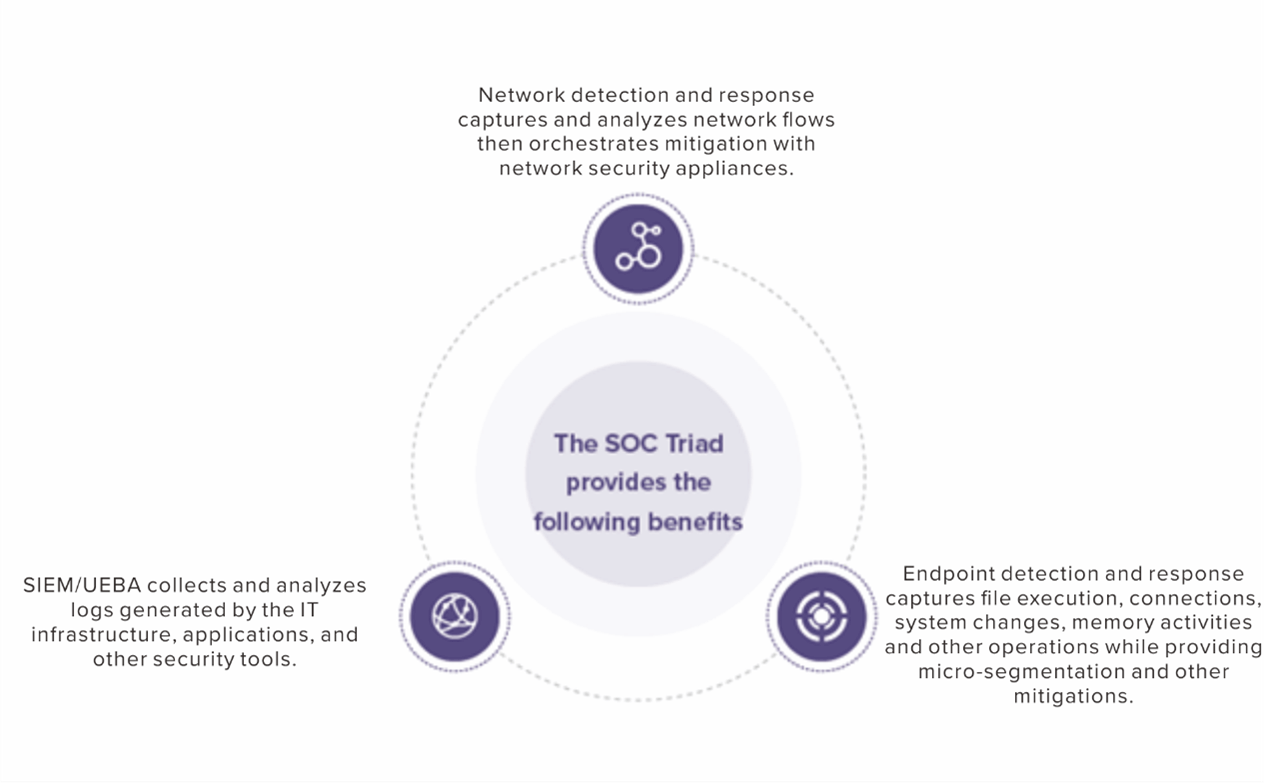
Sangfor Cyber Command defines the category of enterprise-level prevention, detection, and response that integrates event, endpoint, and network data to stop sophisticated attacks. By using Cyber Command as the foundation, you can easily implement most SOC operation models such as the Gartner SOC Visibility Triad that promote better holistic visibility of an organization’s security posture.
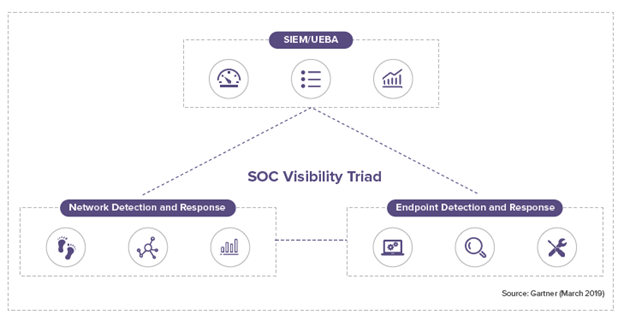
Source: Gartner (March 2020)
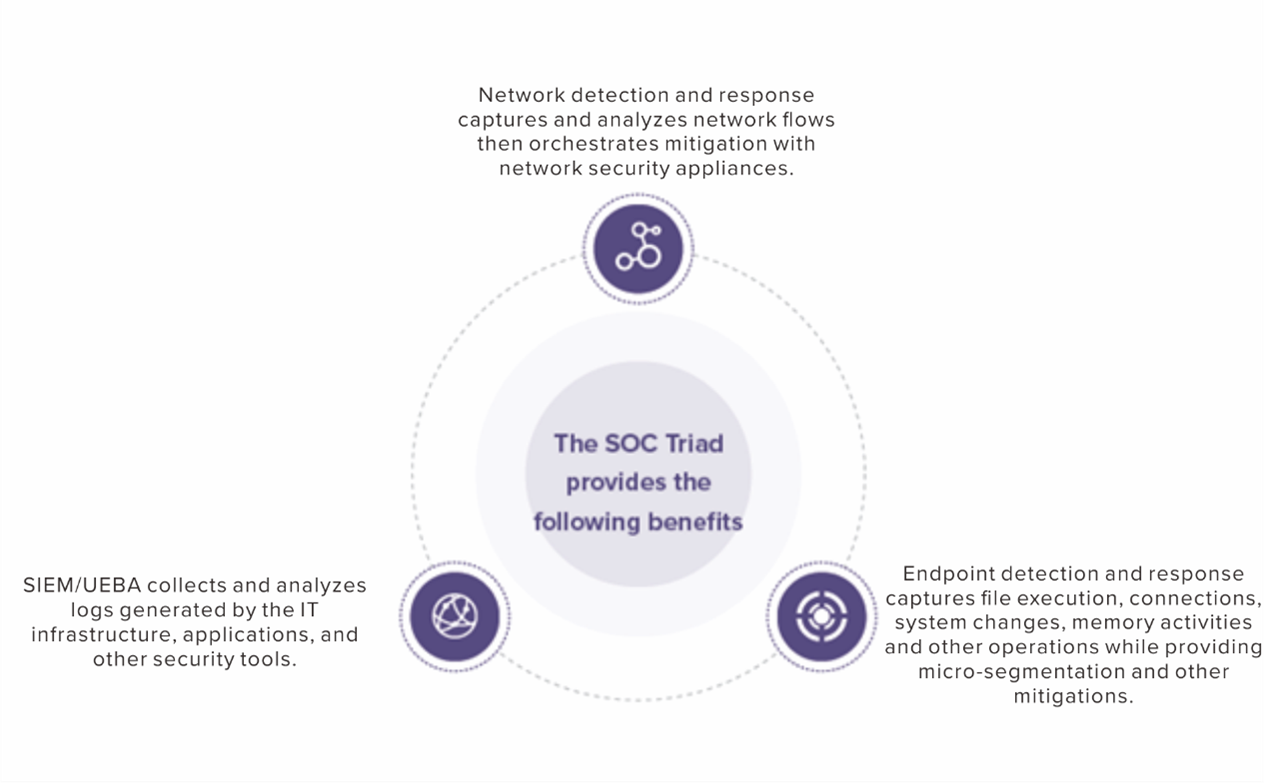 Cyber Command is unique in that it can meet all three corners of the SOC Visibility Triad standalone using included network and endpoint sensors as well as event ingestion from 3rd-party security products. Automatic endpoint response orchestration is standard. Cyber Command’s core capabilities are easily enhanced using the Sangfor XDDR security framework to integrate other Sangfor security products as sensor data and for more robust response orchestration.
Cyber Command is unique in that it can meet all three corners of the SOC Visibility Triad standalone using included network and endpoint sensors as well as event ingestion from 3rd-party security products. Automatic endpoint response orchestration is standard. Cyber Command’s core capabilities are easily enhanced using the Sangfor XDDR security framework to integrate other Sangfor security products as sensor data and for more robust response orchestration.
How is Cyber Command Different?
The Flexible SOC
Sangfor has a complete portfolio of security products including Sangfor NGAF, IAG, and Endpoint Secure that fully integrate with Cyber Command using the Sangfor XDDR security framework. This allows any organization to quickly deploy a foundation for a modern SOC based on any implementation model.
Full Integration
Cyber Command directly integrates with NGAF, IAG, Endpoint Secure, and Neural-X (including cloud sandboxing) to collect & correlate data and orchestrate coordinated rapid response.
Threat Hunting
Cyber Command’s numerous AI analysis models for threat hunting helps customers discover attack surfaces for entry points, breach root-cause and residual threats.
User Experience
Cyber Command has comprehensive multi-dimensional visibility of all internal and external attacks, all managed server & PC assets, unknown & rogue assets, and all related communications across the entire network. The Cyber Command dashboard immediately displays the attack kill chain during attacks as well as recommended remediation strategy.
Technical Innovation
Sangfor has always prioritized the security effectiveness of products and invests significantly to further technological innovation every year. Sangfor’s award winning malware detection engine, Engine Zero, detects zero-day malware, real-time ransomware encryption, and uses multiple AI and machine-learning models to detect anomalies.
Summary
SIEM can be a useful tool for event driven Threat Detection and Response. However, SIEM lacks visibility into any network activity as well endpoint activity limiting its capability to identify and contain novel, unknown threats. More importantly, most SIEM vendors do not have their own network or endpoint sensors, thus lacking the ability to completely correlate and coordinate their response capability against both network and system attacks.
Gartner predicts threats escalating in sophistication and destruction requiring organizations to use every available source of data for threat hunting, detection, and response. As a minimum, network-based technologies enable technical professionals to obtain quick threat visibility across an entire environment without the need for logs or agents. Cyber Command inherently does that. Cyber Command also significantly enhances the value of SIEM tools by providing complementary functionality that overcome any limitations.





