What’s an Incident Response Plan and why is it important? Let’s take a look at the recent example. Affordable housing provider in the United Kingdom, Clarion Housing, experienced a cybersecurity incident that disrupted their systems, forcing them to go offline. The series of disruptions began on the week of June 13th when the company began experiencing technical issues with its online account.

The incident response emergency situation at Clarion Housing Residents.
Source: X
Clarion began tweeting about the issues they had been facing with their online account on June 13th. Clarion later reported that they had resolved and urged customers who had previously been unable to access their accounts to reset their accounts on the following day. In the days that followed, the company continued to report issues with its systems, providing an alternative number for customers to use for emergency repairs. On the June 21st, they released a statement pointing toward the seriousness of the issue.
Finally, on June 23rd, Clarion announced that a cyber security incident had caused a disruption leading to IT system issues. The housing provider’s phone and email systems were down, affecting their customer communications.
“We have updated the information relating to the cyber security incident which has caused significant disruption to our services. As our work continues it is clear that the damage to our systems is extensive. This will result in a long period of disruption while we rebuild our infrastructure,” their latest update read. “We are now confident that our Customer Relationship Management (CRM) system, which is our main store of customer data, was not accessed. We are continuing the investigation into the extent to which data held in other repositories may have been impacted.”
The company is currently working with its cyber security partner to resolve the incident.
Instances such as this one should be a constant reminder to organizations of the importance of an incident response plan. Mitigating risk before the damage is too severe hinges on the ability of businesses to detect threats and act quickly; this is the purpose of an incident response plan. But how many organizations can safely say they have one in place?
What is a Cybersecurity Incident Response Plan?
An incident response plan is a set of procedures put in place to action a response in the event of any incidents that may occur in an organization’s cyber environment. The National Institute of Standards and Technology (NIST), defines an incident response plan as “the documentation of a predetermined set of instructions or procedures to detect, respond to, and limit consequences of a malicious cyber attacks against an organization’s information system(s)”. An effective incident response plan must take into consideration many of the steps that a disaster management plan would entail. This includes aspects such as preparedness, response, and recovery, but covers to a greater extent, responses to cyber security incidents including but not limited to ransomware attacks, data breaches, loss of sensitive data, data leaks, malware, and more.
How to Create a Cybersecurity Incident Response Plan?
Determining which data and systems are critical and valuable is the first step to understanding which potential vulnerabilities your business may have. Thereafter, assessing your cyber infrastructure’s potential points of failure is a key step in understanding which existing and potential threats need immediate addressing. In completing these two steps, you can better understand how to respond to future threats, and you can mitigate risk and set up security measures that meet your needs.
Following the response, a business continuity plan can be put into place to ensure recovery and full continuation of business activities.
A strong incident response plan will cover the following aspects of potential incidents: preparedness, detection, containment, eradication, and recovery.
Cybersecurity Incident Response Plan Checklist
Prepare
Preparation ensures that in the event of any cyberattack, there are measures in place to be taken to navigate the incident. This also involves training staff and stakeholders on how to react and make sure that all the resources required to manage all systems affected are available.
Identify/Detect
Detection can go a long way in determining just how much damage an organization sustains, as a result of cyber incidents. It can also determine how long it takes to trace, detain, and eradicate a threat. Platforms such as Sangfor Cyber Command are designed specially to detect and respond to various threats around the clock. By automating the detection and response, threats are identified as quickly as possible with immediate response.
Contain/Detain
Containment stops the spread of a breach for organizations to control the situation. It also presents the opportunity to develop counter solutions where initial ones may have failed/been late.
Eradicate
Eradication means eliminating the threat at its root. This involves tracing the incident to its cause and strengthening security to prevent the same incident from occurring in the future. Eradication also involves eliminating the threat where it may have spread.
Recover
Perhaps the strongest test of whether an incident response plan is strong is the organization’s ability to recover from the incident. Resuming business activities is the goal, and without the steps above this is difficult (if not impossible). Organizations must ensure that they have the resources needed to substitute any losses sustained, and continue to meet business goals. Another essential part of recovery is resilience. The ability to make sure that similar incidents/attacks do not occur.
Sangfor Incident Response Plan
Partnering with a reliable cybersecurity services and solutions vendor such as Sangfor is essential to your business success. Sangfor will assess your organization’s current cyber structures and security strategies. As such, this is one of the best ways to ensure you are able to find a cybersecurity incident response plan that protects your organization against the endless amount of cyber threats that exist.
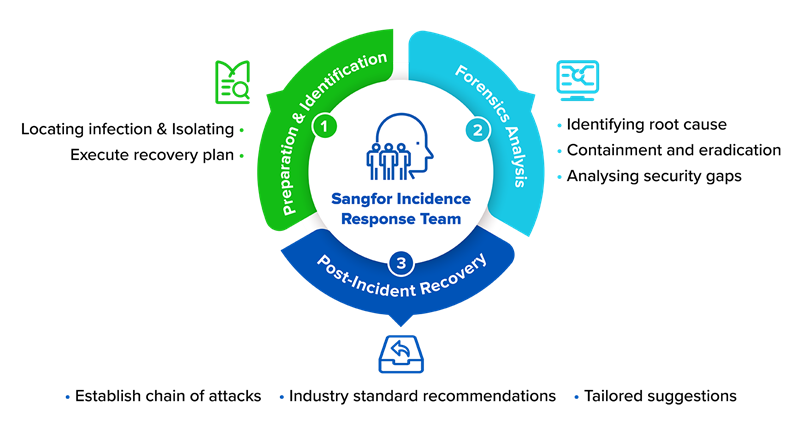
At Sangfor, we understand the struggles of not knowing what to do and how to manage a situation when under attack. Our First Responder team is backed with experience that spans over 5000 manhours in Incident Response. It is also adept at conducting malware discoveries on a frequent basis and having the latest TTPs. At Sangfor, we pride ourselves in having a motivated team culture, having served more than 250 cases.
The first step in rectifying the problem is to identify the fingerprints through activity logs that have been left by the attacker pointing to the root cause. The fingerprints reconstruct the flow of events and exploits used. We then build a remediation plan for you to prevent future attacks.
Our report includes realistic remediation and approach, hidden cyber gaps, and the sharing of industry best practices relevant to you. We also provide follow-up activities to find any residual or persistent malware after the investigation has been concluded to keep you answerable to the stakeholders.
An incident response plan can be what stands between a business and its survival. Planning for incidents allows organizations to detect and respond to threats not only when they occur, but also before they do. Sangfor Incident Response conducts assessments to see the gaps in your organization’s security before recommending solutions that will fill these gaps and more. Sangfor also identifies potential gaps to allow you to enhance your security, strengthen your cybersecurity structures, and improve your response plan.





