As we turn into 2024, we would like to kick off the year with some predictions on trends that will impact cybersecurity this year. As always, these are predictions and may not come to pass.
1. Ransomware is here to stay, it will never die
Ransomware attacks set new records in 2023 according to Corvus Insurance, with attacks up over 110% in November 2023 compared to 2022. Going into 2024, ransomware will become even more sophisticated than in 2023 as AI is increasingly being weaponized to create smarter, stealthier code that is better able to evade detection using fileless (memory injection based) attacks. Rust is also becoming the programming language of choice because the code generated is more secure and more difficult to reverse engineer for analysis. But the biggest shift will be away from encrypting data for ransom to just stealing it outright and extorting ransom to prevent the release of the data.
2. AI will have the biggest impact on both sides
Artificial intelligence will cause a huge boom in technology. It will be used to digitize and understand business use cases, build self-learning & self-correcting machine learning models, and develop algorithms for deeper threat detection and analysis. Yes, AI will itself develop new or refined detection and analysis models. We are already seeing threat researchers using AI to represent both the red & blue teams in attack simulations. This means blue teams can use AI to develop better responses to attacks by tracking red team behavior. But unlike red teams that play fair, real attackers will continue to exploit and weaponize AI to build stealthier and more sophisticated malware as well as new social engineering and phishing attacks.

3. AI is not trustworthy
AI and chatbots such as ChatGPT had a meteoric rise in 2023. They became almost ubiquitous in search tools, plug-ins for business and general-purpose apps, and dedicated informational and database systems to quickly collate and, to some extent, curate responses to natural language questions. But then users discovered there was a bit of HAL (from 2001: A Space Odyssey) in them. There were many documented cases of chatbots making up answers to questions, something people call “lying”, but the AI community chose to label it as “hallucinating”. More problematic is that AI researchers are not sure if it is possible to completely prevent chatbots from providing false or incorrect information. So, users really need to check the chatbot’s work as you would an errant teenager.
4. Mo’ money, Mo’ Money, Mo Money!
Regardless of which analyst group you subscribe to, all agree that security and risk-related spending will increase 14% or more over 2024, reaching between $212B and $215B USD. New global and regional regulatory and compliance requirements are a key driver for spending as meeting compliance is not cheap and security implementations, configurations, and policies & procedures will need to be upgraded and updated. Transitioning securely to the cloud and the rearchitecting of business workflows and processes is another key driver as companies become less afraid of the cloud and want to reduce CAPEX and O&M costs. Oh, and remember the weaponization of AI? That is a key driver for upgrading or replacing security products to better defend against that.
5. Zero Trust is where it’s at
The pandemic made traditional network perimeters obsolete because of work from anywhere and Bring-Your-Own-Device (BYOD) policies at work. New security design architectures were needed to deal with effectively making the secure perimeter into Swiss cheese. A very old military security methodology, rebranded as Zero Trust, will now become the de facto security architecture. The concept of Zero Trust is simple; trust no one and only assign enough access and privileges for someone to do their job. Access control policies determine what local and cloud resources are available to an authenticated user based on their need, the device used to access, and the application used to access. Thus, an employee will have different levels of access to resources depending on if they access from the corporate network, their home, or from a Starbucks. Zero Trust helps organizations deal with serious threats, such as APTs including ransomware.
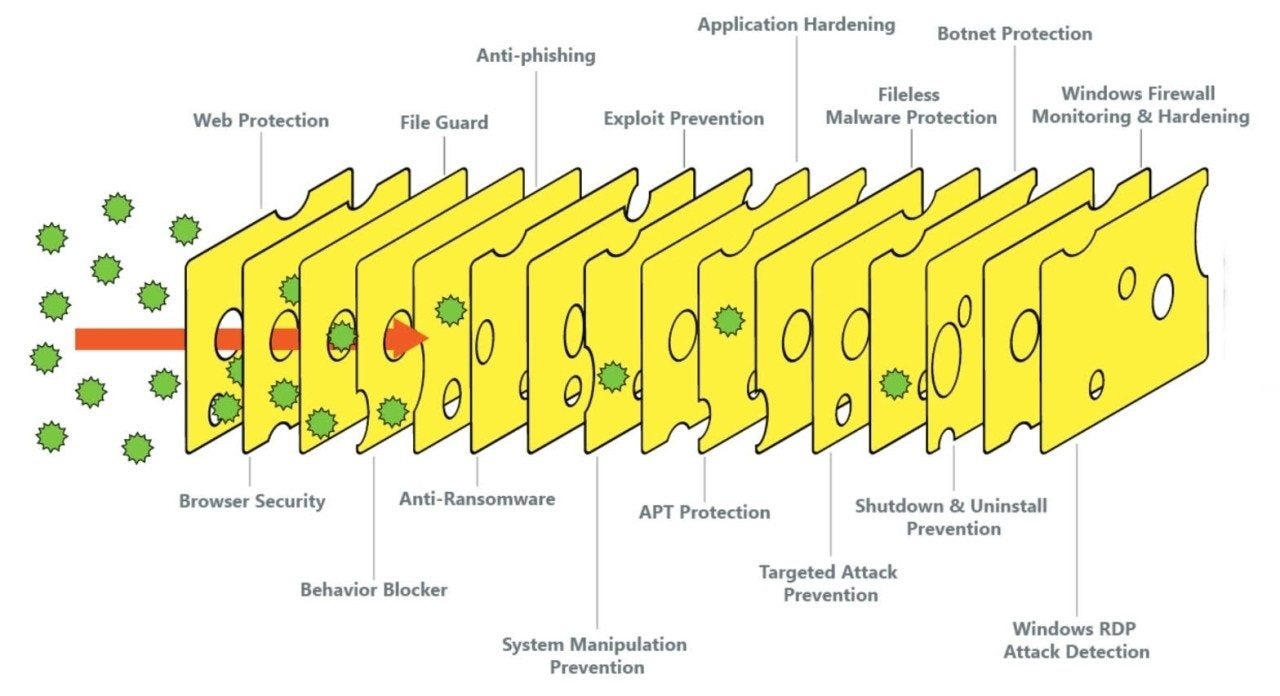
Image source: https://www.linkedin.com/pulse/swiss-cheese-model-cybersecurity-hicham-faik/
Zero Trust is becoming a mandatory business requirement to mitigate cyber risk. According to Okta’s “The State of Zero Trust Security 2022” whitepaper, 97% of companies have a Zero Trust initiative in the process. The 2021 “Executive Order on Improving the Nation’s Cybersecurity” signed by US President Joseph R. Biden Jr. established a Zero Trust strategy for the US federal government. The US National Institute for Standards & Technology (NIST) has released several guidelines related to the strategy and implementation of Zero Trust. This helped drive commercial and other organizations towards Zero Trust globally. Yet, according to Cisco, only 2% of organizations have mature Zero Trust deployments. Still, the trend is very encouraging.
6. The more things change, the more they stay the same
Going into 2024, organizations still face many of the same challenges as last year:
1. Skills shortage
There are still 3 million open cybersecurity positions globally and nowhere near enough people to fill them. Many organizations will turn to untrustworthy chatbots to try and manage the gap.
2. Unpatched vulnerabilities
Since there is still a skills shortage, many organizations, especially small and midsize, will not have the time or resources to address these in a timely manner. Yet this is the top attack vector for cyber criminals. It is hoped that as part of the increased cybersecurity spending, patch management tools will be included.
3. Phishing and Social Engineering will still be top attack vectors
Phish and social engineering attacks will be more sophisticated thanks to AI. We have already seen AI-generated emails that look better than human-generated ones and are generated in a fraction of the time.
4. Your IoT is their IoT
Despite laws such as SB 327, the California law that became effective in 2020 and regulates the privacy and security of Internet of Things (IoT) connected devices, these devices still have far to go to improve security.
7. Rise of the Supervillain
History is full of famous criminals: Adolf Hitler, Bonny & Clyde, Jack the Ripper, Al Capone, Pablo Escobar, and now, Arion Kurtaj. Now 18, Kurtaj was an underage teenage hacker from Oxford, UK, and a member of the Lapsus$ group, a mostly teenage threat actor group that attacked dozens of well-known companies and government agencies around the world in 2021 and 2022. Kurtaj and another underage teen hacker were arrested for a second time in March 2022 for breaching and stealing data from NVIDIA. They leaked some sensitive data as an incentive for NVIDIA to pay a ransom. After his arrest, Kurtaj was “doxxed” by a rival cybergang who posted his family’s personal information online. Kurtaj was moved to a Travelodge hotel for his safety, where he quickly hacked Rockstar Games, stealing and leaking clips of the unreleased Grand Theft Auto 6 game, using only a smartphone, an Amazon firestick, a Bluetooth keyboard and mouse, and his hotel room TV. Diagnosed with severe autism, a mental health assessment conducted as part of his sentencing hearing found Kurtaj "continued to express the intent to return to cyber-crime as soon as possible. He is highly motivated." The judge deemed that Kurtaj's skills and desire to commit cyber-crime meant he was a high risk to the public. Kurtaj was committed to a secure hospital for life until doctors deem him no longer a danger.
There will be more teenage criminals on the rise this year to take his place—disenfranchised teenagers who grew up practicing hacking from a very early age using tools and information readily found on the internet.
8. Conclusion
2024 will be a great year for keeping cybersecurity professionals employed. Unfortunately, these are only a fraction of the total number needed working today. Remember, 3 million vacancies. Also, unfortunately, cybersecurity professionals will be gainfully employed because the bad guys are getting better, faster, and smarter at breaching organizations. The Blue Team is always the defensive side and that is a problem. The attackers have the advantage with more resources to attack than organizations have to defend. But with new tools like AI and new strategies like Zero Trust, organizations have, at best, a better chance of detecting and mitigating attacks and, at worst, a good chance of reducing the damage and fallout from successful attacks.


