The Role of AI in Cybersecurity
Artificial Intelligence (AI) is gaining increasing prominence in the field of cybersecurity. Statista forecasts that AI in cybersecurity will be worth USD 46.3 billion by 2027, a multifold increase from USD 10.5 billion in 2020. Its adoption is driven by an ever-evolving threat landscape where malicious actors are always finding new ways to hurt us. They have become highly adept at weaponizing AI in their malware to improve the potency of their attacks. For example, we now have malware that intelligently learns the environment it’s in and executes malicious code only when specific conditions are met.
The use of AI among attackers and defenders means that the side that develops the more powerful cybersecurity AI comes out on top. As a result, we’ve seen remarkable advancements in AI-based cybersecurity systems in recent years, particularly in threat detection. By leveraging AI technology, organizations can significantly augment their threat detection capabilities and strengthen their security posture. This is backed up by IBM's 2022 Cost of a Data Breach report, which found that "organizations that had a fully deployed AI and automation program were able to identify and contain a breach 28 days faster than those that didn’t, saving USD 3.05 million in costs."
We can all agree that the use of artificial intelligence in cybersecurity is a good thing, but have you ever wondered how it works? If you asked someone who uses or plans to use AI-enabled security technology to explain how it works, they likely wouldn’t be able to do so. But why does it matter? This lack of understanding can lead to several problems. These include:
- An inability to understand the value of AI-powered solutions compared to non-AI products
- An inability to articulate the value of investing in AI-enabled cybersecurity products to management
- An inability to set the right expectations for AI in cybersecurity products in terms of what they can and cannot do
- An inability to differentiate AI cybersecurity products offered by different vendors
- An inability to properly configure and operate cybersecurity AI products to maximize their effectiveness
This article bridges these gaps and enhances your understanding of how AI and cybersecurity work together. But before we delve into the intricacies, it’s a good idea to back up and make sure we have the correct understanding of AI and some of its related jargon.
Key Takeaways
- AI is revolutionizing cybersecurity by enabling faster, smarter, and more scalable threat detection and response across industries.
- Cybersecurity AI tools such as anomaly detection, Natural Language Processing (NLP), random forests, and graph analysis help identify both known and unknown threats in real time.
- Attackers are also leveraging AI, generating deepfake scams, automating exploits, and crafting advanced phishing campaigns.
- Future cybersecurity AI will evolve toward self-healing systems, adaptive learning, quantum-resistant encryption, and zero-trust integration.
- Sectors like finance, healthcare, and government are already benefiting from AI’s ability to process massive data sets and flag high-risk anomalies.
- Sangfor Technologies leads the industry with AI-powered platforms like NGAF, Endpoint Secure, and Cyber Command, built to detect and mitigate advanced threats proactively.
What is Artificial Intelligence?
Artificial Intelligence (AI) is the ability of computer systems to perform tasks that would typically require human intelligence, such as learning, reasoning, and problem-solving. This is achieved using sophisticated AI algorithm models to process and analyze large amounts of data. The trained AI model uses patterns and insights discovered from the data to perform tasks like making predictions and generating output.
AI algorithm: An AI algorithm is a set of instructions that define how an AI system processes data. For example, the CNN (convolutional neural network) algorithm defines how an AI system analyzes visual imagery.
AI model: An AI model is a trained instance of an algorithm that captures the learned knowledge and is used to perform tasks. For example, a trained CNN model is used to recognize and classify new and unseen images.
What is Machine Learning?
Machine Learning (ML) and AI are often discussed as if they were separate technologies, but this is not the case. In fact, ML is a specific approach within AI that focuses on enabling machines to learn and improve from experience without explicit programming. Instead of giving precise instructions, ML algorithms learn patterns in large volumes of data to make predictions or decisions.
To sum up, AI is a broader concept that includes the entire field of developing intelligent machines, while ML serves as a crucial component within AI, providing the means for machines to achieve artificial intelligence.
Key Benefits of AI in Cybersecurity
As cyber threats become more frequent and sophisticated, organizations are increasingly turning to AI in cybersecurity to strengthen their defenses. By automating detection and enhancing visibility, AI enables faster, smarter, and more proactive security strategies.
Here are the core benefits of deploying cybersecurity AI:
Faster threat detection and response
AI can process thousands of alerts in seconds and immediately flag suspicious behavior. This allows security teams to investigate and contain breaches faster, often reducing dwell time from weeks to hours.
Reduced false positives
AI models analyze behavioral context and known baselines to determine whether an alert truly warrants attention. This drastically cuts down on alert fatigue, enabling analysts to focus on real threats.
Scalability
Traditional tools often fail when data volume surges. AI systems, by contrast, can analyze terabytes of data in real time, making them ideal for large-scale enterprises or cloud-based environments.
24/7 monitoring
AI never sleeps. It continuously analyzes network activity and user behavior across all endpoints, detecting signs of compromise at any time, day or night.
Predictive insights
By identifying patterns across historical and live data, AI can flag vulnerabilities or risky behaviors before they’re exploited. This allows organizations to take preemptive action instead of reacting after an attack occurs.
Real-World Use Cases of AI in Cybersecurity
Today’s AI cybersecurity tools are already being used across industries to defend against a wide range of digital threats. Below are some of the most common and effective use cases:
Threat detection
AI algorithms can detect known and unknown threats by analyzing behavior and anomalies in real time. Unlike traditional tools, AI doesn’t rely solely on signature databases, making it more adaptive to novel attacks.
Email filtering
NLP-powered filters evaluate language structure, intent, and embedded URLs to detect phishing and spam emails. These models are trained on millions of data points and improve with each new input.
Behavioral analysis
Through User and Entity Behavior Analytics (UEBA), AI builds unique behavior profiles for users and devices. It flags deviations, like a user logging in at an odd time or accessing unusual files, that could indicate account compromise.
Incident response
AI can trigger automated actions, such as isolating an endpoint, blocking a malicious IP, or disabling a compromised account. These rapid responses reduce the window of exposure and minimize manual effort.
Fraud prevention
Financial institutions use AI to track transaction histories, user habits, and location data. When an out-of-pattern event occurs, like a foreign login followed by a large withdrawal, the system can block or delay the transaction automatically.
Vulnerability management
AI analyzes security patches, system configurations, and known exploit trends to help prioritize patching. It enables teams to focus first on high-impact, high-probability vulnerabilities, improving remediation efficiency.
AI Techniques Used in Cybersecurity
AI in cybersecurity serves a variety of purposes, including threat detection, threat hunting, threat intelligence, and incident response. This article will focus exclusively on threat detection, which has truly embraced the use of AI. Among the widely adopted AI and cybersecurity techniques in threat detection are Anomaly Detection, Natural Language Processing (NLP), Random Forests, and Graph Analysis. Let’s explore them in more detail.
Natural Language Processing (NLP)
Natural language processing (NLP) is a branch of AI that enables computers to understand, interpret, and generate human language. It uses various AI and ML algorithms to process and analyze textual data. Trained NLP models are applied to tasks like translation, sentiment analysis, and named entity recognition (NER).

In the context of AI in cybersecurity, NLP plays a vital role in detecting language-based threats. A key use case is identifying malicious domains created through typosquatting, such as “g00gle.com” or “paypall.com.” These domains mimic legitimate ones with minor changes to trick users.
By applying NLP to a large set of known domains, models learn patterns, character combinations, and keywords that distinguish legitimate sites from malicious ones. This strengthens a system’s ability to block phishing attempts and suspicious URLs.
NLP is also essential for detecting threats like phishing emails, webshells, and website defacements, making it a powerful tool in modern cybersecurity AI defenses.
Random Forests
Before exploring random forests, it helps to understand decision trees. A decision tree predicts outcomes by branching through features — for example, determining if a car might break down based on age, mileage, or service history.
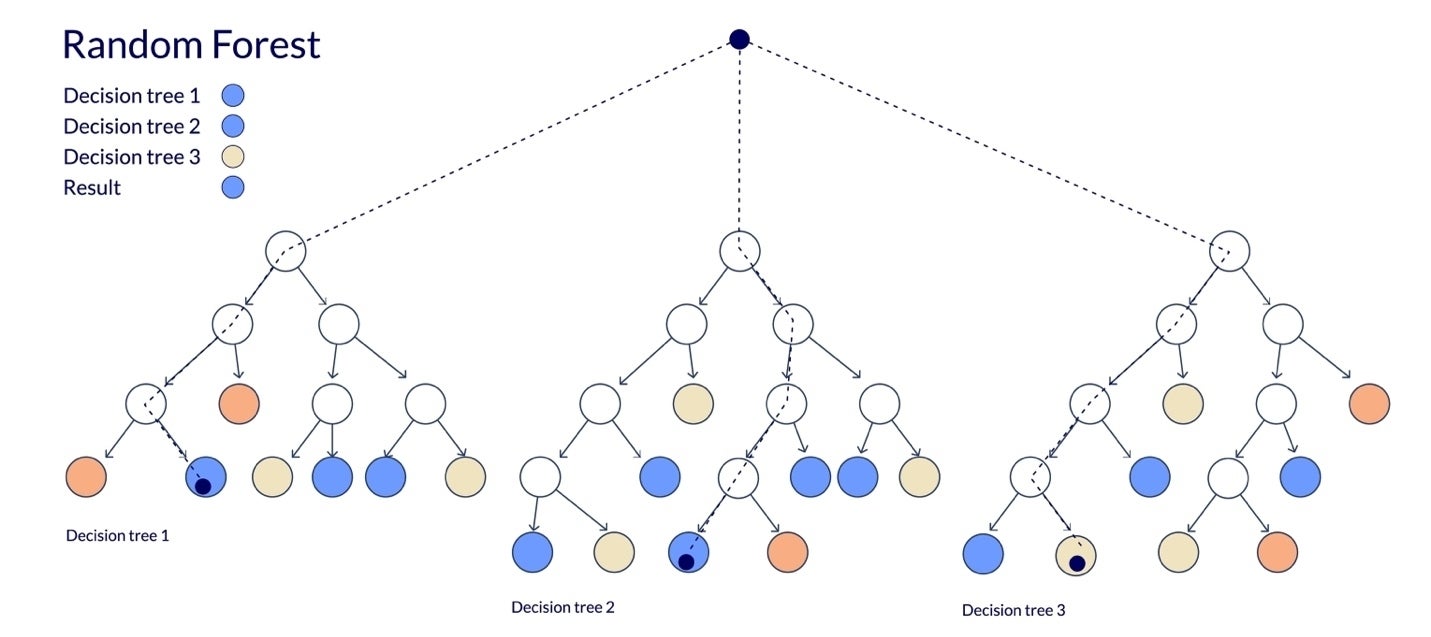
A random forest builds many such trees using random data samples and features. Each tree makes a prediction, and the result with the most “votes” becomes the final decision. This improves accuracy and reduces overfitting.
In cybersecurity AI, random forests are used to detect brute force attacks, especially on remote desktop services (RDP). The model learns from patterns like failed login attempts, time intervals, and login locations.
Beyond brute force detection, random forests also help uncover command-and-control (C2) communication and DNS tunneling, which are common in malware operations. Their ability to learn from varied input makes them an ideal fit for AI and cybersecurity applications.
Anomaly Detection
Anomaly detection identifies unusual behavior in a dataset — behavior that could indicate a potential threat. It starts by training a model on normal patterns of user or system activity, then flags deviations in real time.
This technique is vital in AI cybersecurity, especially for catching insider threats or stealthy attacks that bypass signature-based tools. With UEBA, systems learn baseline behavior for users, devices, and applications.

Detection is enhanced through correlation analysis, which connects different events to spot complex attack patterns. One odd login might seem harmless, but paired with unusual file access or data transfer, it could signal a breach.
Anomaly detection is particularly effective against data exfiltration — a common tactic used by APT (advanced persistent threat) groups. These attackers often disguise stolen data within regular traffic using fragmentation, timing, or trusted services. By analyzing traffic metadata, access logs, and communication behavior, anomaly models reveal hidden threats, making them essential to AI in cybersecurity strategies.
Graph Analysis
Graph analysis uses ML to understand relationships between entities, such as users, devices, or IP addresses. In a graph, each entity is a node, and its interactions are represented as edges.
In cybersecurity AI, this technique uncovers hidden connections and suspicious communication patterns. For instance, analysts can visualize how infected devices (nodes) interact and identify which one is acting as the command center.

One of the primary use cases is detecting botnets — networks of malware-infected systems used for malicious activities like distributed denial-of-service (DDoS) attacks, cryptomining, or malware distribution. These botnets are often geographically dispersed, making them hard to trace.
Graph analysis pinpoints “central” nodes coordinating such attacks and maps lateral movement across compromised devices. This makes it a powerful tool in AI and cybersecurity strategies for identifying and mitigating complex, multi-stage threats.
How Attackers Use AI to Outpace Defenses
Cybercriminals are also leveraging AI in cybersecurity, but for the wrong reasons. From crafting deceptive content to bypassing defenses, attackers now use AI to make their operations faster, stealthier, and harder to detect.
Here’s how threat actors exploit cybersecurity AI:
Generating phishing content
AI language models can craft hyper-personalized phishing emails that mimic corporate tone and branding. These messages are harder to detect and more likely to fool recipients.
Evading detection
Malware can use AI to alter its own behavior based on the environment. For example, it might stay dormant in a sandbox but activate only once inside a live system, making traditional detection tools less effective.
Automating vulnerability discovery
AI is used to scan large swaths of the internet or corporate infrastructure to find unpatched systems and weak configurations. This drastically reduces the time from discovery to exploitation.
Creating deepfakes
Attackers use AI-generated voice or video to impersonate executives in social engineering scams. These deepfakes have already been used in fraud schemes costing companies millions of dollars.
Where Cybersecurity AI Is Headed Next
The future of cybersecurity AI promises tools that are more autonomous, adaptive, and context-aware, capable of defending against next-generation threats.
Here are some trends that will shape what's next:
Self-healing networks
Future AI systems may not just detect problems; they’ll fix them. These networks could automatically reroute traffic, patch vulnerabilities, or restore affected systems without human input.
Adaptive AI
Instead of relying on static training data, future AI models will learn continuously from live threat feeds. This makes them more agile in responding to previously unseen attacks.
Zero-trust enforcement
AI will help apply zero-trust principles in real time, evaluating trust dynamically based on behavior, device posture, and access context, rather than static credentials alone.
Quantum-resistant AI
As quantum computing evolves, today’s cryptography may become vulnerable. AI is already being explored to help develop and manage post-quantum encryption systems that are resilient to quantum-enabled threats.
A Leader In AI-Enabled Cybersecurity
Sangfor Technologies is a pioneer of AI-enabled cybersecurity technology, releasing the world’s first AI-enabled next-generation firewall, Sangfor NGAF. Sangfor NGAF and Sangfor Endpoint Secure are both integrated with Sangfor Engine Zero, a state-of-the-art AI-powered malware detection engine. To maximize the accuracy of malware detection, Engine Zero is tested against millions of malware samples to enable it to run and teach itself, expanding its capacity to discover new and unknown malware. NGAF’s powerful capabilities and innovations have seen Sangfor recognized as a “Visionary" in the Gartner Magic Quadrant for Network Firewalls, awarded the "Recommended Rating" in the CyberRatings Enterprise Firewalls Test, and honored with the Frost & Sullivan "Company of the Year" award. Endpoint Secure received the "Top Product" award from AV-Test for achieving perfect test scores for protection, performance, and usability, as well as the "Advanced Approved Endpoint Protection" certificate for providing 100% protection against ransomware attacks.
Sangfor Cyber Command, our Network Detection & Response (NDR) solution, is the epitome of AI-driven security technology. Cyber Command harnesses multiple purpose-built AI models to detect a wide range of advanced threats hidden in network traffic. By using AI to analyze and correlate events from across the network, Cyber Command connects the dots between events from various data sources to uncover threats that are missed by point solutions. Event correlation provides security teams with highly contextualized alerts to streamline investigation and threat hunting, enabling rapid identification and response to threats. Cyber Command has earned Sangfor multiple industry recognitions, including a Top 5 NDR vendor in the world based on Gartner Market Share data, a "Representative Vendor" in Gartner Market Guide for NDR, and a "Notable Vendor" in Forrester Network Analysis and Visibility Landscape. Watch this webinar to learn how Cyber Command utilizes purpose-built AI models.
Sample of Purpose-Built AI Models Used in Sangfor Security Products
| Scenarios | Data | Algorithm | Products |
|---|---|---|---|
| DNS hidden tunnel | DNS Logs | Random Forests | Cyber Command, NGAF, Endpoint Secure |
| DGA domain name | DNS Logs | NLP, Graph Analysis | Cyber Command, NGAF, Endpoint Secure |
| New malicious domain name | DNS Logs | NLP, Anomaly Detection | Cyber Command, NGAF, Endpoint Secure |
| Botnet family variant tracking | DNS Logs | Graph Analysis | Cyber Command, NGAF, Endpoint Secure |
| HTTPS C&C | HTTPS Logs | Random Forests | Cyber Command, NGAF |
| Encrypt RDP and SSH slow brute force | RDP Logs, SSH Logs | Random Forests | Cyber Command, NGAF, Endpoint Secure |
| Website defacement | Web Access Logs | NLP | Cyber Command, NGAF |
| Engine-Zero files anti-virus | Files | XGBoost | Cyber Command, NGAF, Endpoint Secure |
| Webshell | HTTP Logs | NLP | Cyber Command, NGAF |
| Abnormal outbound behavior | Sessions | Anomaly Detection | Cyber Command |
| Abnormal login behavior | Login Logs | Anomaly Detection | Cyber Command |
| Attack path recovery | Multiple Logs | Knowledge Mapping | Cyber Command |
Contact Us for Business Inquiry
FAQ
AI in cybersecurity is a powerful tool, but it often raises questions for IT teams, business leaders, and end users. Here, we answer some of the most frequently asked questions to help you better understand this fast-evolving technology.
AI is used to automate threat detection, analyze massive data sets, and respond to cyber incidents in real time. It enables faster identification of threats while reducing manual workload on analysts.
No. AI is a powerful assistant, but not a replacement. Human oversight is essential for strategic decisions, interpreting context, and managing complex scenarios.
The biggest risks include overreliance on automation, adversarial attacks on AI models, and bias in training data. Regular audits and human checks are key to reducing these risks.
Sectors that handle sensitive data, like finance, healthcare, government, and education, benefit greatly from AI in cybersecurity, thanks to its ability to automate protection at scale.
Automation is safe when implemented thoughtfully. While AI can improve speed and accuracy, it must work alongside human review to avoid errors or blind spots.





