What is a Bring Your Own Vulnerable Driver (BYOVD) Attack?
BYOVD, short for Bring Your Own Vulnerable Driver, is an adversarial technique where attackers implant a vulnerable legitimate driver into a targeted system. They then exploit the vulnerable driver to perform malicious actions. Because legitimately signed drivers are trusted by security software, they are neither flagged nor blocked. Moreover, the drivers involved in BYOVD attacks are usually kernel-mode drivers. Successful exploitation allows attackers to achieve kernel-level privilege escalation, which grants them the highest level of access and control over system resources on a target. Attackers leverage this escalated privilege by disabling endpoint security software or evading their detection. Once endpoint security defenses are compromised, attackers are free to engage in malicious activities without any obstruction. This technique is gaining traction and poses new challenges to endpoint security.
Initially, the BYOVD technique was used by top-tier APT groups such as Turla and the Equation Group. However, as the cost of attacks decreased, other threat actors have also begun leveraging it to achieve their objectives. If we search for BYOVD on BleepingComputer, we can find evidence of different threat groups using this technique in real-world attacks.
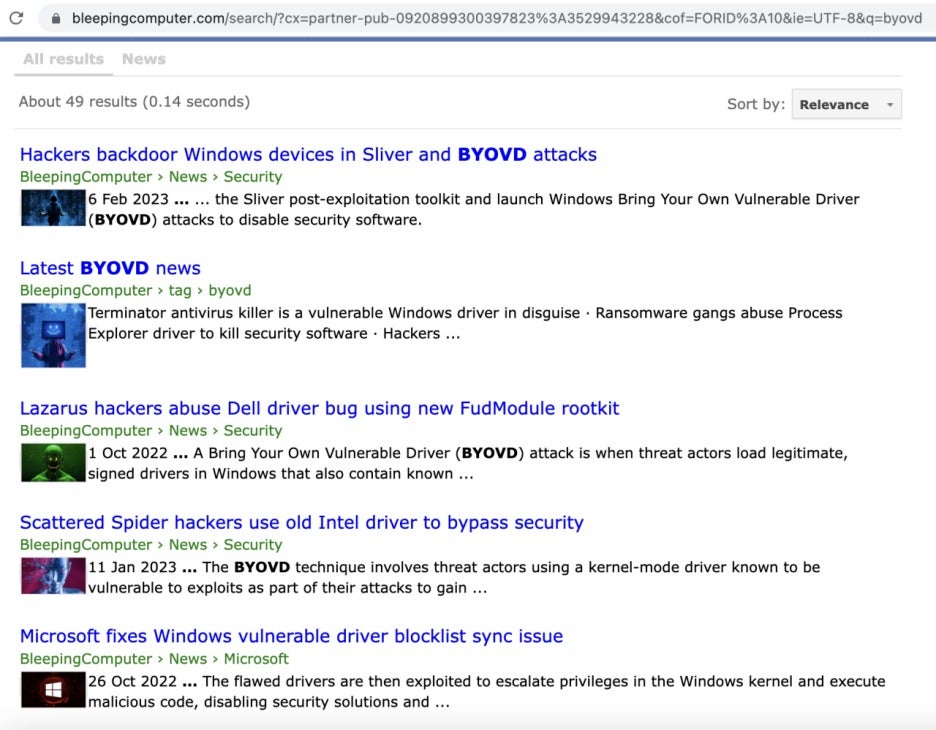
Notable BYOVD Attacks in H1 2023
Here are some notable vulnerable driver attacks reported in the first half of 2023. This list shows that BYOVD is widely used among threat actors, including APT and ransomware groups.
January:
- The threat actor Scattered Spider (UNC3944) exploits the iqvw64.sys driver with the vulnerability CVE-2015-2291. iqvw64.sys is an old Intel Ethernet diagnostics driver patched in 2015. (Reported by CrowdStrike)
February:
- Attackers use malvertising to distribute malware and exploit a renamed version (Иисус.sys) of the PROCEXP152.sys driver. PROCEXP152.sys is a part of Process Explorer, the process management tool in Windows OS. (Reported by SentinelOne)
- A threat actor distributes the Sliver toolkit using the Sunlogin remote desktop application and exploits the mhyprot2.sys driver. mhyprot2.sys is an anti-cheat driver for the popular video game Genshin Impact. (Reported by AhnLab)
March:
- The UNC2970 APT group used the LIGHTSHOW tool to exploit ene.sys. ene.sys is a vulnerable driver provided by ENE Technology Inc and signed with a certificate issued by Ptolemy Tech Co. (Reported by Mandiant)
April:
- Ransomware groups used the AuKill tool to exploit the vulnerable driver of Windows Process Explorer version 16.32. The renamed PROCEXP.SYS was dropped alongside the original PROCEXP152.SYS. (Reported by Sophos)
May:
- Earth Longzhi, a subgroup of APT41 or Winnti, used the SPHijacker tool to exploit a renamed version (mmmm.sys) of the vulnerable zamguard64.sys driver. zamguard64.sys is used by the security software Zemana Anti-Malware. (Reported by TrendMicro)
June:
- The BlackCat ransomware group used the spyboy Terminator tool to exploit the zamguard64.sys/zam64.sys driver. (Reported by CrowdStrike here and here)
BYOVD Attack Tools & Resources
Attackers may develop their own tools or incorporate open-source tools, which has helped lower the cost of BYOVD attacks. Some custom tools are modified based on open-source projects. For example, during the first half of 2023, the UNC2970 APT group and LockBit ransomware group used their custom BYOVD tools called LIGHTSHOW and AuKill, respectively. AuKill shares similarities with the open-source tool Backstab. The figure below highlights some of the similar functions between Backstab and AuKill.
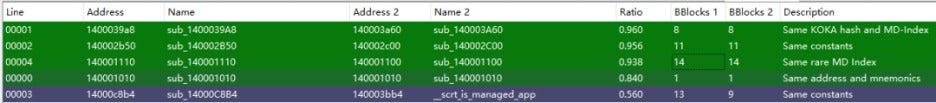
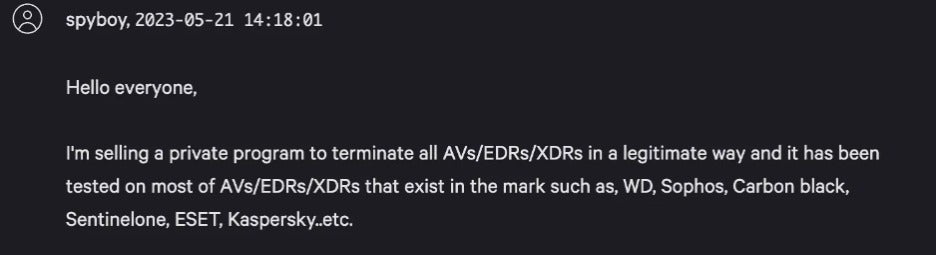
Indeed, LockBit integrated the Backstab tool in a ransomware attack in November 2022. Another BYOVD tool used by ransomware groups is called "Terminator." This program is promoted by a threat actor with the moniker "spyboy" and has been for sale on a Russian hacking forum since May 2023. Spyboy claims that this tool can terminate twenty-three AVs/EDRs/XDRs, including products by Windows, Sophos, VMware, SentinelOne, and ESET. The Terminator tool has been observed in attacks by the BlackCat ransomware gang.
Furthermore, many BYOVD exploitation tools can be found through searches on GitHub. These tools have advanced functions such as disabling anti-virus callbacks, killing anti-virus processes, disabling/enabling the Protected Process Light (PPL) mechanism, and disabling/enabling driver signature enforcement. These functions cover most requirements needed to bypass security measures. Attackers can also reverse engineer these tools to grasp the principles of exploiting driver vulnerabilities, allowing them to discover and develop new driver exploits.
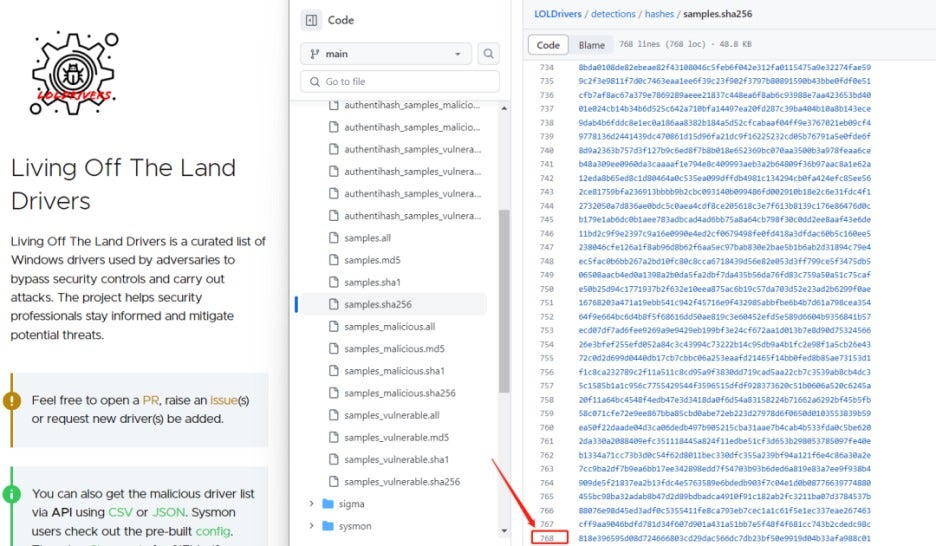
The cost of BYOVD attacks has also decreased due to the availability of vulnerable driver libraries. For example, the Living Off The Land Drivers (LOLDrivers) project records over 700 legitimate drivers that attackers can exploit. Additionally, undocumented, or attacker-exclusive drivers can also be used for malicious activities. This means that attackers have ample weapons for launching BYOVD attacks.
Protecting against BYOVD Attacks
Due to the lower cost and, thus, the greater accessibility of BYOVD attacks, endpoint security products that lack purpose-built protection against BYOVD techniques are highly susceptible to compromise. While vulnerable driver libraries like LOLDrivers can be abused by attackers, they also benefit defenders. For example, Microsoft’s vulnerable driver blocklist and Elastic's VulnDriver YARA rules are available to facilitate security audit work.
Microsoft's vulnerable driver blocklist is a list of known vulnerable drivers that defenders can use to identify and create rules to block dangerous drivers on endpoints.
Elastic's VulnDriver YARA rules are rules written in the YARA language. These rules target driver vulnerabilities and help defenders detect and mitigate potential BYOVD attacks.
By utilizing these resources, defenders can enhance the protection against BYOVD threats by quickly identifying and addressing driver vulnerabilities. This proactive approach helps minimize the risk of compromise and strengthen the overall security posture of the endpoint security products.
Sangfor Endpoint Secure’s ransomware protection module and Sangfor Engine Zero provide automated protection against BYOVD threats. When such an attack occurs, Endpoint Secure will trigger a threat alert and automatically execute response actions.
The Future of BYOVD Attacks
In general, attacks that exploit zero-day driver vulnerabilities in the Windows kernel still constitute a small percentage of overall attacks. However, recent real-world incidents and evaluations of security products have shown that even known vulnerable drivers pose significant threats. This technique is gaining popularity among various threat actors, such as ransomware and APT groups, and its frequency of use is likely to increase in the future, potentially becoming more automated. Therefore, it is becoming crucial to incorporate purpose-built BYOVD protection modules in endpoint security products.





