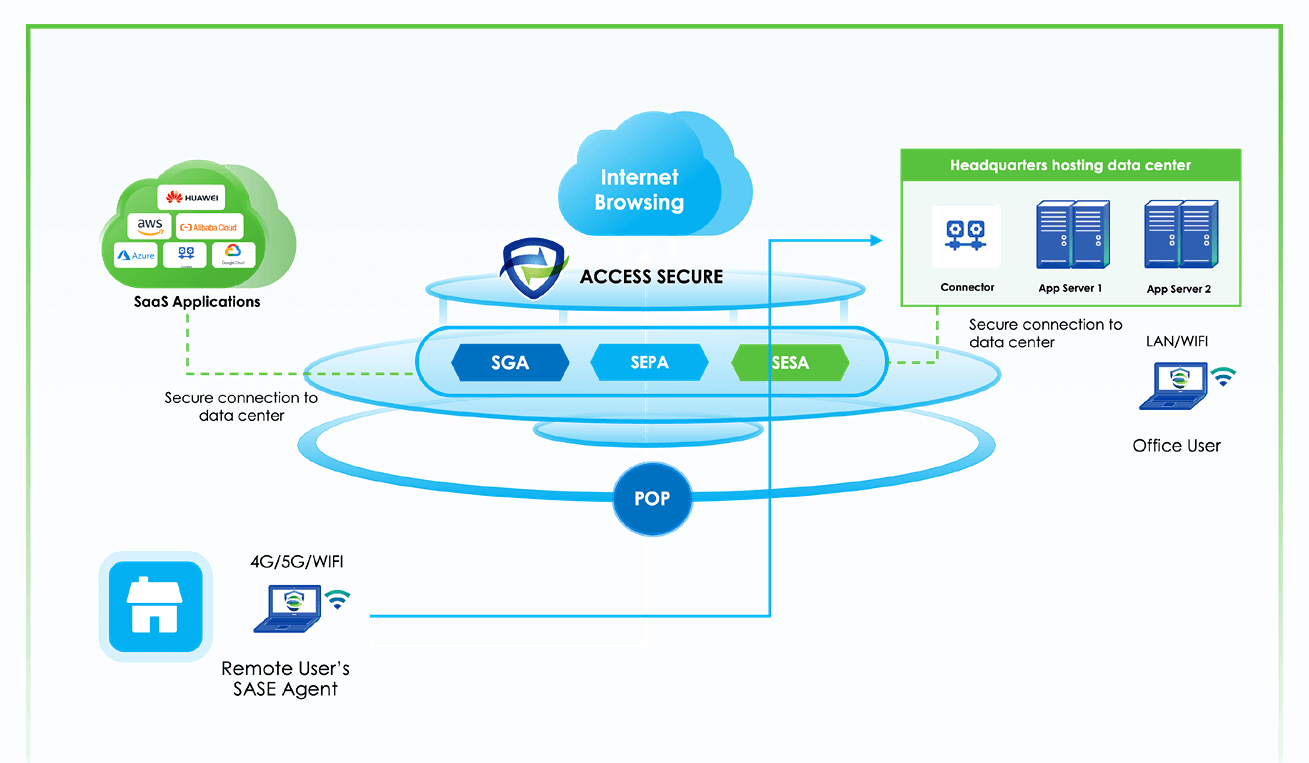
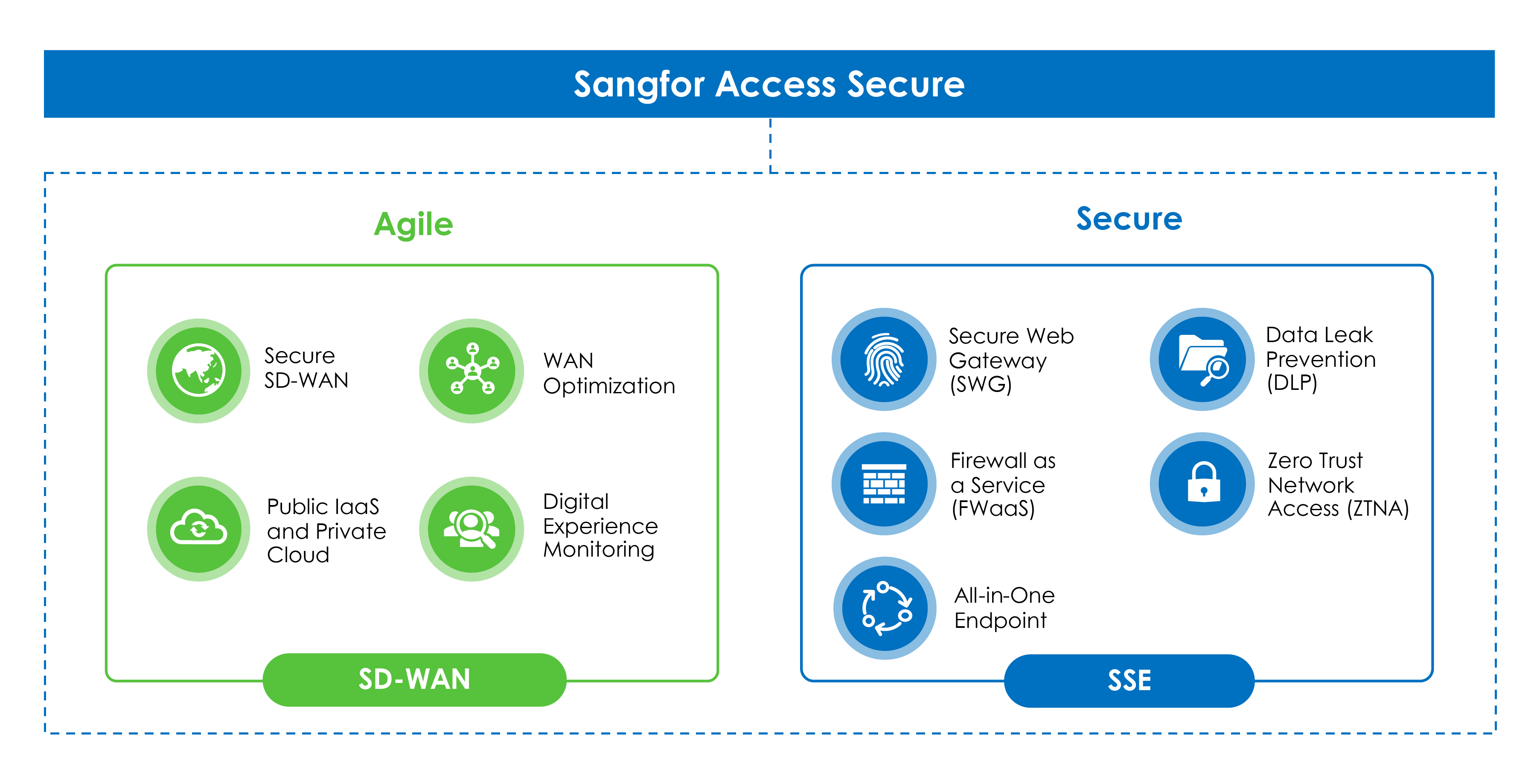
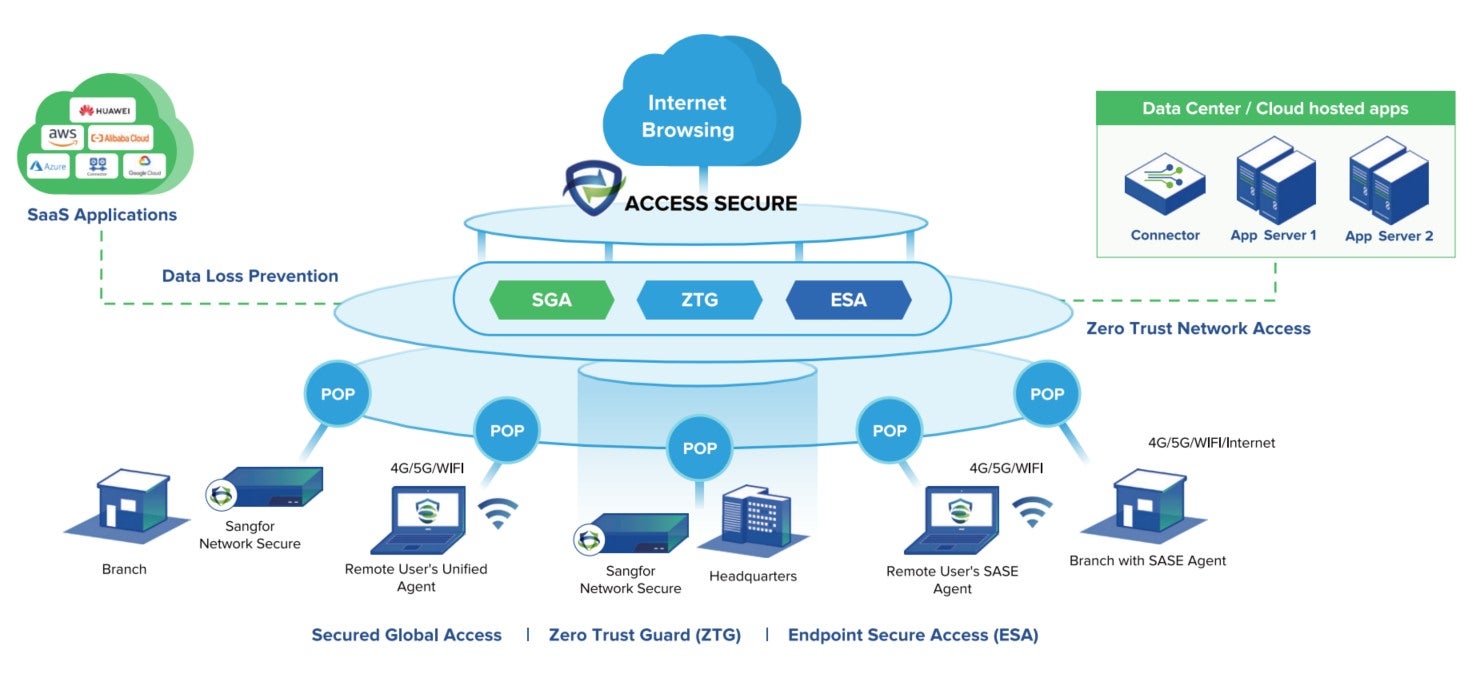
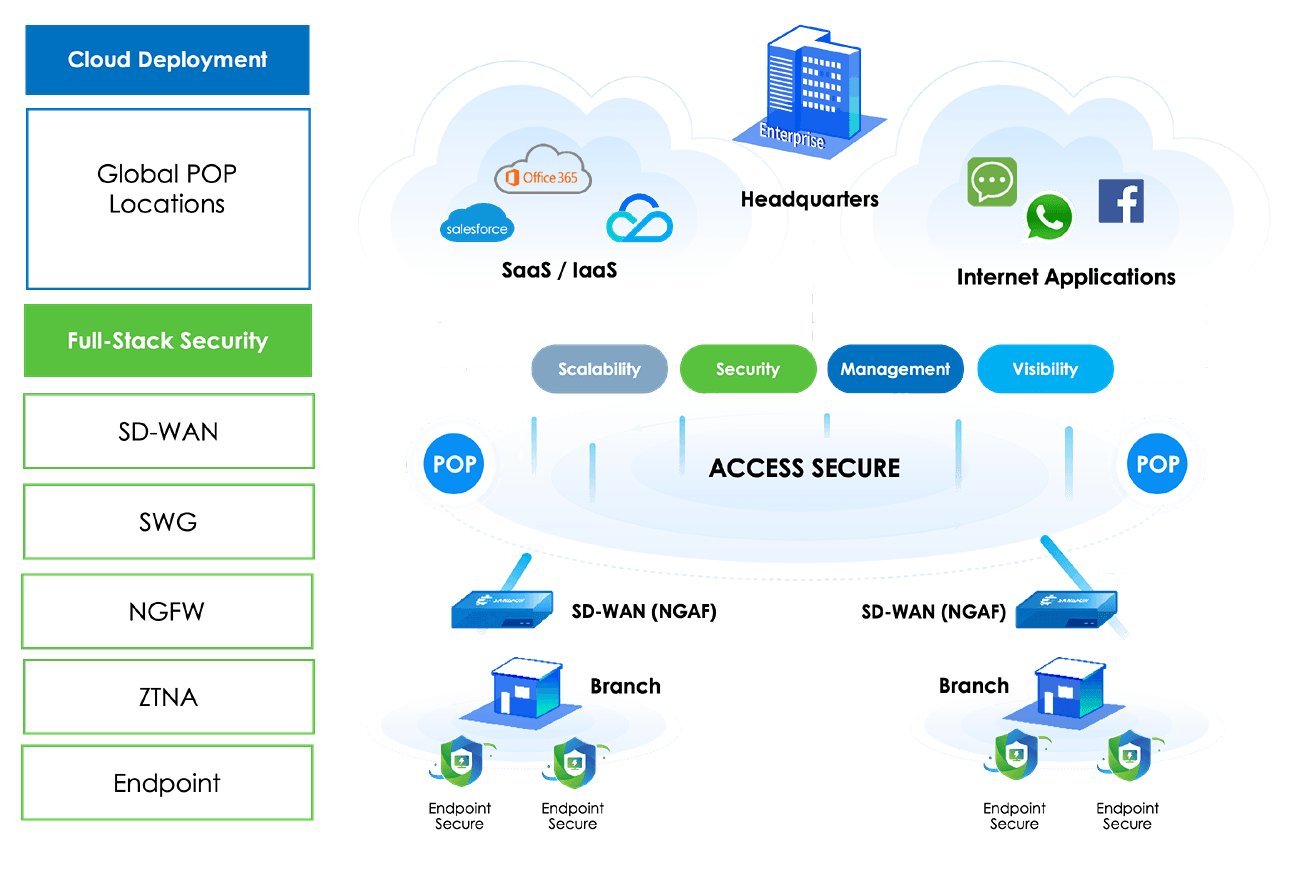
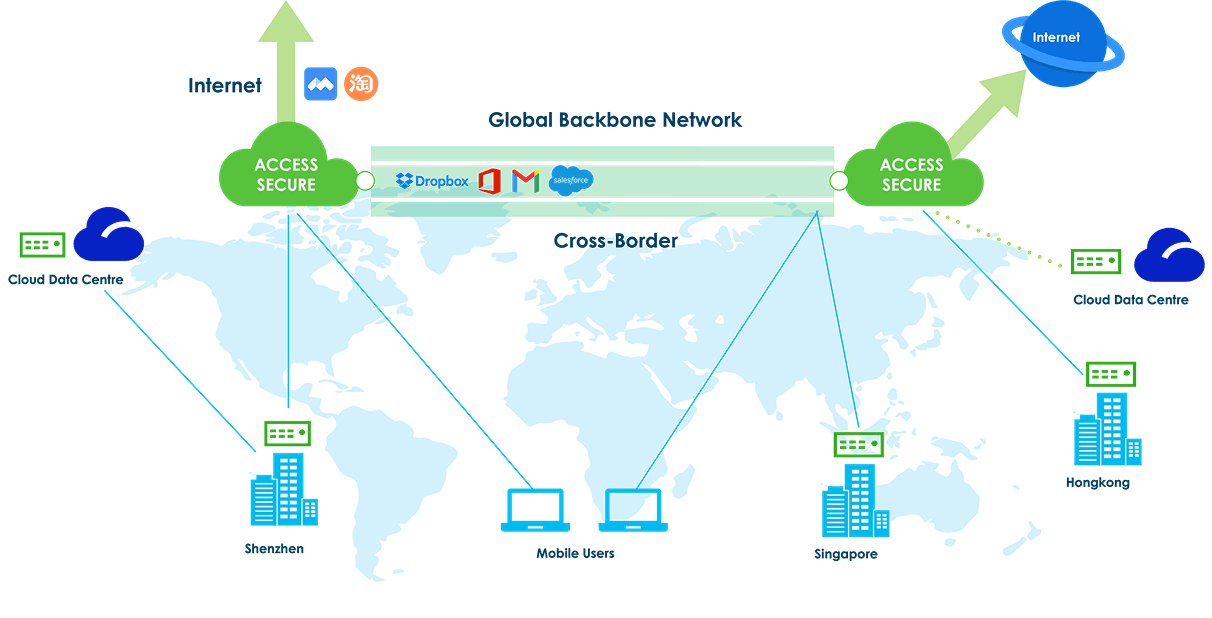
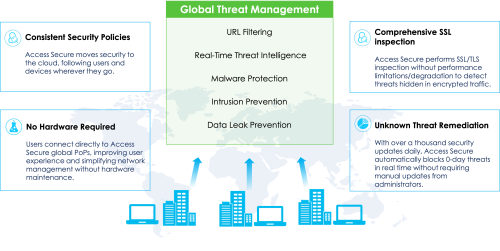
As hybrid work and cloud adoption grow, Secure Access Service Edge (SASE) is gaining traction as a key framework for secure, high-performance network access. But what’s the financial impact of adopting SASE? The Sangfor SASE ROI Calculator helps you quantify the cost savings and business value of implementing Sangfor SASE.
Your customized ROI Analysis Report provides detailed insights into workforce productivity gains, security risk reduction, and infrastructure cost savings. Try the calculator today!