In today’s fast-evolving cybersecurity landscape, organizations are forced to make a critical choice: should they rely on traditional security systems or adopt modern unified threat management (UTM) solutions? As we step further into 2025, this decision has never been more relevant. Both architectures promise protection, but they differ widely in strategy, cost, complexity, and effectiveness.
This article explores how unified threat management, traditional security, and next-generation firewalls (NGFWs) compare in 2025. Whether you’re a growing enterprise, an SMB with a lean IT team, or an industry leader modernizing cloud infrastructure, understanding these options can help future-proof your cybersecurity strategy.

What Is Unified Threat Management (UTM)?
Unified Threat Management (UTM) offers a simplified, centralized security solution. It consolidates multiple protective technologies into a single platform or appliance, combining:
- Firewall
- Antivirus
- Intrusion Prevention System (IPS)
- Web and email filtering
- VPN support
- Application control
Emerging in the early 2000s as a response to growing complexity in network security and cost of managing traditional multi-point security infrastructures, UTM was originally designed for small to mid-sized businesses seeking simplicity and cost-effectiveness.
By 2025, however, UTM has matured into a powerful platform that integrates a variety of key security features, including firewalls, intrusion detection and prevention systems (IDS/IPS), antivirus, virtual private network (VPN) support, content and URL filtering, data loss prevention (DLP), and sandboxing for zero-day threats. The hallmark of UTM lies in its single-pane-of-glass interface, allowing administrators to monitor and manage diverse security tasks from a unified dashboard.
Key Advantages of UTM
- Centralized management through a unified interface
- Lower total cost of ownership
- Simplified configuration and monitoring
- Rapid deployment, especially in branch offices or SMB environments
Modern UTM solutions also offer cloud-native deployment options, support for remote workers, and integration with SD-WAN, making them a viable option even in distributed and hybrid environments.
More advanced UTMs now come equipped with AI-based threat detection, behavior analytics, and automatic quarantine features, narrowing the capability gap between them and modular traditional setups.
What Is Traditional Security?
In contrast, Traditional Security, often referred to as “point security,” refers to a layered approach where different tools are deployed independently to handle specific threats. These may include:
- Hardware firewalls
- Standalone antivirus and antimalware
- Intrusion Detection Systems (IDS)
- VPN gateways
- Email security platforms
- Web filtering proxies
While this allows for deep customization and fine-grained control, it also introduces significant operational challenges.
In 2025, many organizations still use traditional stacks, especially those operating in regulated industries or requiring highly specialized configurations. However, managing a patchwork of tools often results in overlapping alerts, disjointed policies, and significant administrative overhead.
Key Characteristics of Traditional Security
- Best-of-breed approach: Each function is handled by a specialized product.
- High customization: You can tailor defenses per system or department.
- Decentralized management: Security teams must juggle multiple interfaces and vendors.
- Scalable (but complex): You can scale different components independently—but integration is not always seamless.
Traditional Security has historically been the preferred approach for larger enterprises, particularly in regulated industries where granular policy control, vendor diversity, and best-in-class components are non-negotiable.
However, with increasing sophistication in cyberattacks, the lack of integrated intelligence-sharing between point solutions has become a concern. Manual coordination between systems introduces latency in threat detection and response.
Moreover, traditional security requires a strong internal IT force. Organizations must maintain relationships with multiple vendors, apply patches separately for each tool, and perform comprehensive integration to unify logs, reports, and policies across tools. The time and expertise required for this can be substantial.
Market Trends and Adoption in 2025
Unified threat management continues to gain momentum globally. According to recent research by Grand View, the UTM market is valued at approximately USD 6.78 billion in 2024, with a projected compound annual growth rate (CAGR) of 15.3% through 2030.
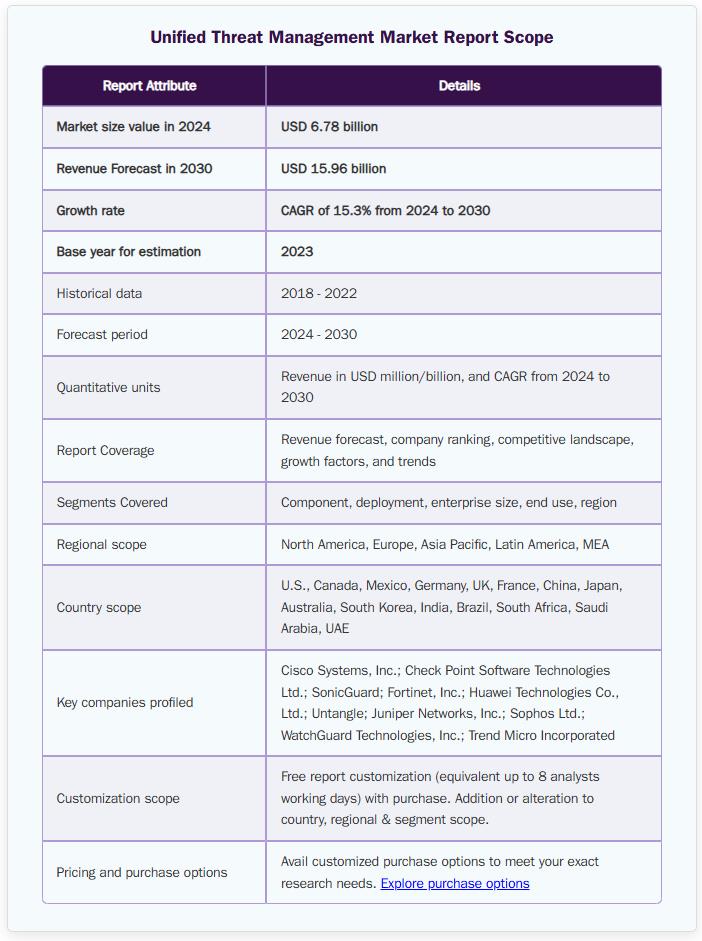
Unified Threat Management Market Report Scope, Source: Grand View
Several factors are fueling this growth:
- The increasing reliance on cloud-based services
- The rising adoption of IoT devices, and the growing need for integrated security solutions in small and medium-sized enterprises (SMEs)
- Remote and hybrid work models have driven the need for centralized security enforcement.
- The Asia-Pacific region is emerging as the fastest-growing UTM market, thanks to digital transformation and compliance pressures.
These trends highlight that UTM is no longer just an SMB solution—it’s becoming a foundational security approach for modern businesses.
UTM vs Traditional Security: A Deep Comparison
This article compares UTM and Traditional Security in following ways:
1. Architecture and Deployment
| Feature | UTM | Traditional Security |
|---|---|---|
| Structure | All-in-one appliance or software | Separate tools for each function |
| Deployment Speed | Quick and centralized | Time-consuming and distributed |
| Vendor Model | Single-vendor platform | Multi-vendor procurement |
UTM appeals to teams that need speed and simplicity, whereas traditional setups offer granular control but demand more time and skill to deploy and manage.
In fast-moving sectors like e-commerce or fintech, the ability to deploy quickly and react to emerging threats in real-time can be a distinct advantage. However, industries requiring deep auditability, such as healthcare or defense, may prioritize the meticulous layering of traditional tools.
The reduced deployment time of UTM also makes it suitable for rapidly expanding companies, or for organizations opening new branches where centralized, cloud-deployed security is ideal.
2. Performance and Scalability
UTM solutions, by nature of integrating multiple functions into one device, can suffer performance degradation under heavy loads. The more features enabled, the more pressure placed on a single CPU.
Traditional Security architectures offer dedicated processing power for each function, making them better suited for high-throughput environments.
| Metric | UTM | Traditional Security |
|---|---|---|
| Scalability | Moderate (vertical scaling) | High (horizontal & vertical) |
| Performance Under Load | May throttle | Generally stable |
| Custom Workload Optimization | Limited | Highly flexible |
Modern UTM platforms attempt to close this performance gap with multicore processing and hardware acceleration, but they rarely match the specialization of independent solutions.
Additionally, traditional systems can be fine-tuned to address the specific throughput needs of departments—for instance, data centers can use high-speed inspection tools, while endpoint defenses vary by location or device type.
3. Management and Usability
This is where UTM shines.
- UTM provides a single pane of glass to configure firewall rules, monitor traffic, apply antivirus updates, and analyze threat reports.
- Traditional Security requires logging into multiple portals, each with its own logic, logs, and policy system.
| Management Layer | UTM | Traditional Security |
|---|---|---|
| Interface | Unified | Fragmented |
| Policy Synchronization | Automatic | Manual or API-integrated |
| Monitoring | Streamlined | Requires aggregation tools (e.g., SIEM) |
If your IT team is small or overburdened, UTM saves precious time. However, enterprises with dedicated SOCs may prefer the flexibility of traditional stacks.
Furthermore, traditional setups can be enhanced with advanced orchestration tools such as SOAR platforms, allowing security analysts to build workflows across disparate tools. This increases response speed, but also complexity.
In contrast, UTMs bundle essential reporting and alerts, making them more plug-and-play for organizations without a security operations center.
4. Customization and Integration
Traditional security tools can be customized to a high degree, making them ideal for:
- Segmented networks
- Industry-specific compliance
- Custom APIs and orchestration platforms
UTMs are generally less customizable and cater to broad-stroke security policies that apply across many industries but may fall short in niche scenarios.
| Flexibility Aspect | UTM | Traditional Security |
|---|---|---|
| Custom Rule Sets | Basic | Advanced per tool |
| Third-party API Integration | Limited | Extensive |
| Role-Based Access Control | Often simplified | Granular per module |
While newer UTM platforms are expanding their API capabilities, they still lag behind traditional solutions that have matured within specific security domains.
Moreover, traditional security gives you the option to replace or upgrade individual components without overhauling the whole system—something rarely possible in an all-in-one UTM model.
5. Cost and Maintenance
A major reason why organizations opt for UTM is cost savings. Fewer vendors, licenses, and maintenance contracts translate into lower capital and operational expenses.
That said, Traditional Security—while more expensive upfront—can deliver greater long-term ROI for large organizations through superior performance, auditability, and threat adaptability.
| Cost Factor | UTM | Traditional Security |
|---|---|---|
| Initial Cost | Lower | Higher |
| Vendor Management | Single | Multiple |
| Staff Requirement | Minimal | Security specialists |
| Upgrade Complexity | Simple | Complex, per tool basis |
Organizations must also consider the hidden costs: poor visibility in UTM could delay detection of a breach, whereas the effort to manage traditional systems may lead to burnout or misconfigurations.
Another cost-related consideration is compliance. Some regulatory frameworks demand segregation of duties, customized logging, or high-grade encryption that may only be available in traditional toolsets.
The Role of NGFWs: Bridging the Gap
Enter the Next-Generation Firewall (NGFW)—a solution that blurs the lines between traditional firewalls and UTM. NGFWs provide deep-packet inspection, application awareness, AI-based anomaly detection, and even optional UTM modules, depending on the vendor.
While NGFWs are often positioned as enterprise-grade solutions, they are increasingly used as the foundation for UTM platforms. In 2025, many NGFWs offer UTM-like functionality out-of-the-box or via modular add-ons. This gives businesses the ability to scale their security stack according to need—without compromising visibility or control.
UTM and NGFW aren’t always mutually exclusive. In fact, NGFWs are frequently embedded within UTM solutions, providing a deeper security core while retaining the unified management benefits of UTM.
Use Case Scenarios
Here are some scenarios that suits each solution.
When UTM Is the Right Fit
For these environments, UTM systems deliver robust security with minimal complexity, often in a virtualized or cloud-native format:
- Startups and SMBs without full-time cybersecurity teams
- Branch offices that need quick deployment
- Educational institutions seeking basic content filtering and firewalling
- Organizations with limited budgets or lower risk profiles
- Companies that prioritize fast rollout and centralized control
When Traditional Security Wins
Larger enterprises or organizations with highly sensitive data may benefit from the layered control of traditional security stacks or advanced NGFWs. These options are especially useful for:
- Enterprises with complex networks and custom compliance needs
- Critical infrastructure with zero tolerance for latency or downtime
- Finance and healthcare sectors requiring in-depth logging and forensics
- Companies needing layered defense models across physical and virtual infrastructure
- Teams with mature cybersecurity talent that can leverage fine-grained tools
In such cases, investing in a best-of-breed, multi-vendor stack might offer better flexibility, even at the expense of higher cost and complexity.
Common Misconceptions
“UTM is outdated.”
Not true. In 2025, UTMs are more powerful than ever, offering cloud-native deployment, AI-based anomaly detection, and SD-WAN integration.
“Traditional security is too expensive.”
While true for some SMBs, the scalability and specialization of traditional security make it more cost-effective for larger enterprises in the long run.
“I have to choose one or the other.”
Actually, many companies adopt a hybrid model—UTMs for edge locations and traditional stacks for core systems.
Final Verdict: Which Is Better in 2025?
It depends on your organization’s size, risk exposure, and IT maturity.
| Organization Type | Recommended Security Model |
|---|---|
| Small Office / SMB | UTM |
| Regional Office / Mid-size Org | UTM or Hybrid |
| Large Enterprise / SOC-enabled | Traditional Security |
If your top priorities are simplicity, speed, and centralized management, UTM is a logical starting point.
However, organizations that are rapidly scaling or need more control should seriously consider a Next-Generation Firewall (NGFW)—which offers the performance, application-layer visibility, and automation capabilities that can fully replace traditional UTM appliances.
In today’s multi-vector threat environment, agility matters. Some organizations even transition from UTM to NGFW-centric security architecture as they grow, adopting a solution that delivers both consolidated protection and intelligent threat handling at scale.
While UTM simplifies security for smaller organizations, NGFWs deliver future-ready protection—with deeper inspection, integration, and scalability—making them the superior choice for forward-looking security strategies.
Sangfor’s Approach: Integrated Security Built for the Future
Sangfor Athena NGFW delivers next-gen protection at every network edge—blocking 99% of external threats with real-time AI. As the world’s first NGFW with built-in NGWAF, SOC Lite, and native integration with Sangfor’s full security ecosystem (EPP, SWG, NDR, XDR, MDR, SASE), it redefines what a firewall can do.
For organizations in Asia-Pacific and beyond, Sangfor Athena NGFW offerings deliver enterprise-grade protection without overwhelming complexity.
Contact Us for Business Inquiry
Frequently Asked Questions
Yes, UTM remains highly relevant, especially for small to mid-sized businesses that need fast, centralized protection without the complexity of managing multiple security tools. However, for organizations planning to scale or requiring deeper visibility and control, transitioning to a Next-Generation Firewall (NGFW) provides a more future-proof solution.
Absolutely. NGFWs offer all the core functionalities of UTM—firewalling, threat detection, VPN, content filtering—but with greater performance, Layer 7 visibility, AI-driven analytics, and seamless integration with broader security ecosystems. For most growing organizations, an NGFW not only replaces a UTM but enhances protection in ways UTM cannot.
While some large organizations may still deploy UTM appliances at branch offices for simplicity, the trend is shifting. Enterprises increasingly prefer NGFWs for both edge and core protection due to their scalability, threat intelligence integration, and ability to support complex network environments. UTM can be part of a hybrid strategy—but NGFWs are becoming the new standard.





