1. Summary of CVE-2021-43503
| Vulnerability Name | Laravel Remote Code Execution Vulnerability (CVE-2021-43503) |
|---|---|
| Release Time | May 2022 |
| Component Name | Laravel |
| Affected Versions | Laravel ≤ 5.8.38 |
| Vulnerability Type | Remote Code Execution |
| Exploit Condition | User Authentication: Not required. Precondition: Default. Trigger Mode: Remote |
| Description | Exploit Difficulty: Unknown Severity: Critical. Attackers can achieve remote code execution. CVSS Score: 9.8 |
2. About the Vulnerability
2.1 Introduction
Laravel is a free and open-source PHP web framework used for the development of web applications following the model–view–controller (MVC) architectural pattern and based on Symfony.
2.2 Summary
On May 12, 2022, Sangfor FarSight Labs received a notice about a remote code execution vulnerability (CVE-2021-43503) in Laravel, classified as critical with a CVSS score of 9.8.
A Remote Code Execution (RCE) vulnerability exists in h Laravel 5.8.38 via an unserialize() POP chain in the following php files:
- __destruct in \Routing\PendingResourceRegistration.php
- __call in Queue\Capsule\Manager.php
- __invoke in mockery\library\Mockery\ClosureWrapper.php
An attacker can use this vulnerability to construct malicious data for remote code execution attacks without authorization, thereby obtaining root or admin permissions.
3. Affected Versions
Laravel ≤ 5.8.38
4. Solutions
4.1 Remediation Solutions
4.1.1 Check the Component Version
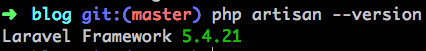
Method 1: Simply run the following artisan command (php artisan --version) from your CLI and it will return your Laravel version.
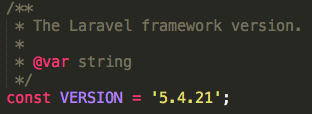
Method 2: Check vendor/laravel/framework/src/Illuminate/Foundation/Application.php for the version constant.
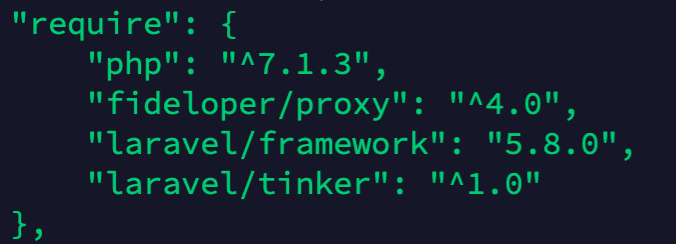
Method 3: View the composer.json file to obtain the component version.
4.1.2 Laravel Solution
Users can update their affected products to the latest version to fix the vulnerability at https://github.com/laravel/laravel
4.1.3 Workaround
Disable debug mode.
4.2. Sangfor Solutions
4.2.1 Security Monitoring
The following Sangfor products and services perform real-time monitoring of assets affected by the Laravel remote code execution vulnerability (CVE-2021-43503):
- Sangfor Cyber Command
- Sangfor Cyber Guardian Detection and Response Service
4.2.2 Security Protection
The following Sangfor products and services provide protection against the Laravel remote code execution vulnerability (CVE-2021-43503):
- Sangfor Next Generation Application Firewall (NGAF)
- Sangfor Cyber Guardian Detection and Response Service
5. Timeline
On May 12, 2022, Sangfor FarSight Labs received a notice about the Laravel remote code execution vulnerability (CVE-2021-43503).
On May 12, 2022, Sangfor FarSight Labs released a vulnerability alert with remediation solutions.
6. Reference
https://github.com/guoyanan1g/Laravel-vul/issues/2#issue-1045655892
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-43503
7. Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





