Summary
On December 10 (UTC+8), 2025, Microsoft released its December 2025 Security Updates, which included patches for a total of 70 CVEs, an increase of 2 CVEs compared to the previous month.
In terms of vulnerability severity, there were 3 vulnerabilities marked as "Critical" and 57 vulnerabilities marked as "Important/High". In terms of vulnerability types, there were primarily 24 remote code execution vulnerabilities, 29 privilege escalation vulnerabilities, and 10 information disclosure vulnerabilities.
Statistics
Vulnerability Trend
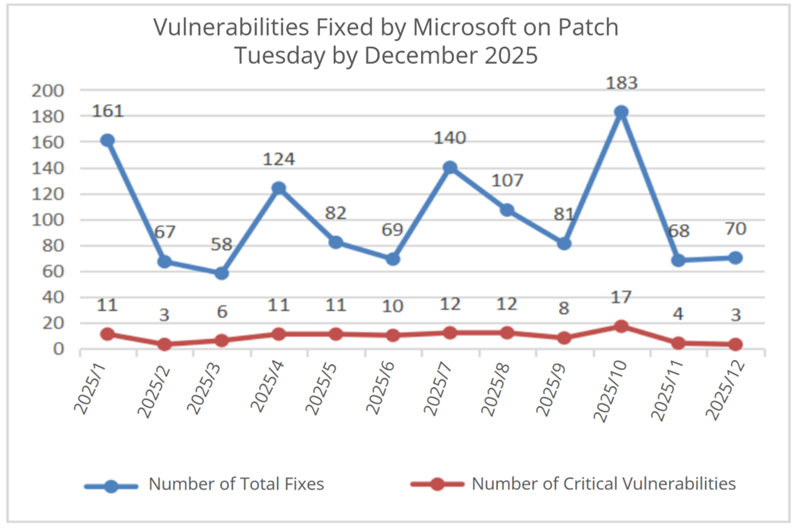
Figure1 Vulnerabilities Patched by Microsoft in the Last 12 Months
On the whole, Microsoft released 70 patches in December 2025, search results include 3 critical vulnerability patches.
Based on Microsoft's historical vulnerability disclosures and the specific circumstances of this year, Sangfor FarSight Labs estimates that Microsoft will announce more vulnerabilities in the coming January in comparison to December. We expect a figure of approximately 90 vulnerabilities.
Comparison of Vulnerability Trends
The following figure shows the number of patches released by Microsoft in the month of December from 2022 to 2025.
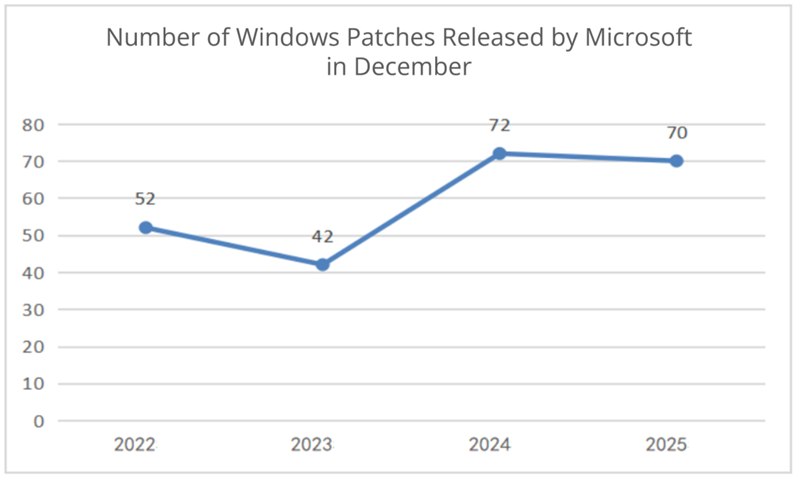
Figure2 Number of Windows Patches Released by Microsoft in December from 2022 to 2025
The following figure shows the trend and number of vulnerabilities at different severity levels addressed by Microsoft in December from 2022 to 2025.
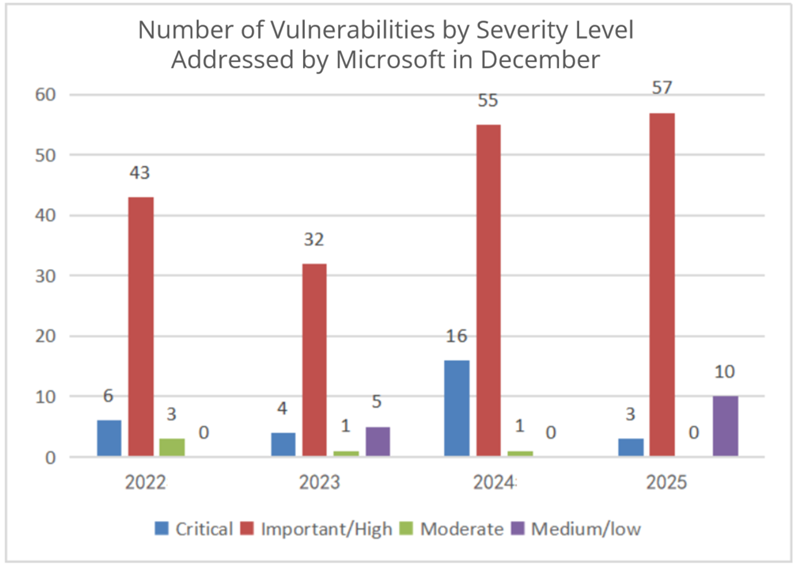
Figure3 Number of Vulnerabilities by Severity Level Addressed by Microsoft in December from 2022 to 2025
The following figure shows the number of vulnerabilities by type addressed by Microsoft in December from 2022 to 2025.
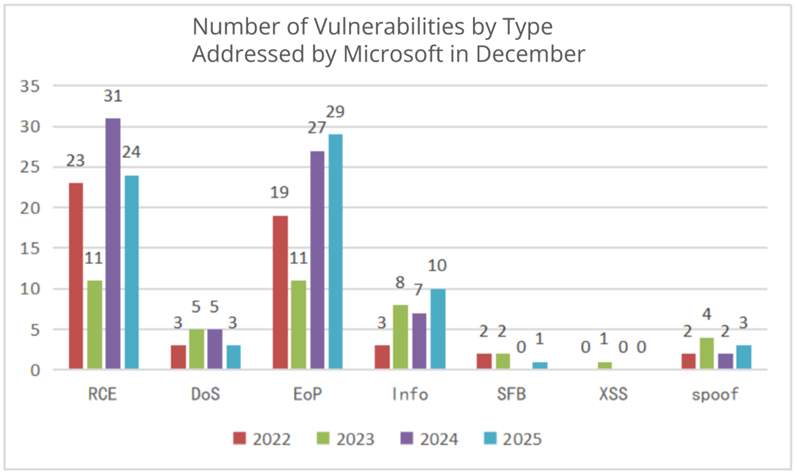
Figure4 Number of Vulnerabilities by Type Addressed by Microsoft in December from 2022 to 2025
Data source: Microsoft security updates
Compared to last year, there has been a decrease in terms of the number of vulnerabilities this year. The number of vulnerabilities addressed by Microsoft in December 2025 has decreased. A total of 70 vulnerability patches, including 3 critical ones, have been reported this month.
Compared to last year, the number of vulnerabilities at the Critical level addressed by Microsoft has decreased, and that of vulnerabilities at the Important/High level has increased. Specifically, 3 vulnerabilities at the Critical level have been addressed, a decrease of about 81%; and 57 vulnerabilities at the Important/High level have been addressed, an increase of about 4%.
In terms of the vulnerability type, both the number of remote code execution (RCE) vulnerabilities and the number of denial-of-service (DoS) vulnerabilities have decreased, whereas the number of elevation of privilege (EoP) vulnerabilities has increased. We should remain highly vigilant because, when combined with social engineering techniques, attackers can exploit RCE vulnerabilities to take over the entire local area network (LAN) and launch attacks.
Details of Key Vulnerabilities
Analysis
Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability (CVE-2025-62221)
Windows Cloud Files Mini Filter Driver is a core driver component in Windows that supports cloud file space optimization and on-demand synchronization. It intercepts and manages access to cloud-hosted files at the file system level, enabling features such as placeholder files, on-demand downloads, and space-saving unloading. The files appear to applications as normal files within the local file system, whereas the driver dynamically fetches or releases data in coordination with the cloud service provider upon access.
An elevation of privilege vulnerability exists in it, which attackers can exploit to gain higher privileges on the target system. This vulnerability is known to have been exploited in the wild, and after assessment, it is considered critical in terms of the threat level. We recommend that users promptly update the Microsoft security patches.
Microsoft Office Remote Code Execution Vulnerability (CVE-2025-62554)
Microsoft Office is an office software suite developed by Microsoft, which includes office tools such as Word, Excel, and PowerPoint.
A remote code execution vulnerability exists in it, which attackers can exploit to execute arbitrary code on the target system. After assessment, it is considered that this vulnerability is critical in terms of the threat level. We recommend that users promptly update the Microsoft security patches.
Affected Versions
| Vulnerability Name & CVE ID | Affected Version |
| Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability (CVE-2025-62221) | Windows Server 2025 (Server Core installation) Windows Server 2025 Windows Server 2022, 23H2 Edition (Server Core installation) Windows Server 2022 (Server Core installation) Windows Server 2022 Windows Server 2019 (Server Core installation) Windows Server 2019 Windows 11 Version 25H2 for x64-based Systems Windows 11 Version 25H2 for ARM64-based Systems Windows 11 Version 24H2 for x64-based Systems Windows 11 Version 24H2 for ARM64-based Systems Windows 11 Version 23H2 for x64-based Systems Windows 11 Version 23H2 for ARM64-based Systems Windows 10 Version 22H2 for x64-based Systems Windows 10 Version 22H2 for ARM64-based Systems Windows 10 Version 22H2 for 32-bit Systems Windows 10 Version 21H2 for x64-based Systems Windows 10 Version 21H2 for ARM64-based Systems Windows 10 Version 21H2 for 32-bit Systems Windows 10 Version 1809 for x64-based Systems Windows 10 Version 1809 for 32-bit Systems |
| Microsoft Office Remote Code Execution Vulnerability (CVE-2025-62554) | Microsoft Office LTSC for Mac 2024 Microsoft Office LTSC for Mac 2021 Microsoft Office LTSC 2024 for 64-bit editions Microsoft Office LTSC 2024 for 32-bit editions Microsoft Office LTSC 2021 for 64-bit editions Microsoft Office LTSC 2021 for 32-bit editions Microsoft Office for Android Microsoft Office 2019 for 64-bit editions Microsoft Office 2019 for 32-bit editions Microsoft Office 2016 (64-bit edition) Microsoft Office 2016 (32-bit edition) Microsoft 365 Apps for Enterprise for 64-bit Systems Microsoft 365 Apps for Enterprise for 32-bit Systems |
Solutions
Official Solution:
Microsoft has released security patches for affected software. Affected users can install the corresponding security patches based on their system versions.
Links:
- https://msrc.microsoft.com/update-guide/advisory/CVE-2025-62221
- https://msrc.microsoft.com/update-guide/advisory/CVE-2025-62554
References
https://msrc.microsoft.com/update-guide/releaseNote/2025-Dec
Timeline
On December 10, 2025, Microsoft released a security bulletin.
On December 10, 2025, Sangfor FarSight Labs released a vulnerability alert.
Learn More
Sangfor FarSight Labs researches the latest cyber threats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyber threats, providing fast and easy protection for customers.





