
Did REvil Disappear Quietly?
After many high-profile REvil ransomware attacks, and immediately following the massive ransomware attack on Kaseya, affecting almost 1,500 organizations. American President Joe Biden spoke directly to Russian President Vladamir Putin last week, describing the conversation as a step forward.
"I made it very clear to him that the United States expects when a ransomware operation is coming from his soil, even though it's not sponsored by the state, we expect them to act if we give them enough information to act on who that is," Biden said.
"And secondly, we've set up a means of communication now on a regular basis to be able to communicate with one another when each of us thinks something is happening in another country that affects the home country. And so it went well. I'm optimistic."
On July 13th, all the websites related to the REvil ransomware group disappeared mysteriously. At present, when users visit the REvil website, they are greeted with a message saying, "Onionsite Not Found."
There has been no definitive word on why the websites were taken down, but we’d say the recent conversation between world leaders is the ultimate catalyst.
National Telecommunications Company in Ecuador Suffers Ransomware Attack
On July 16, Ecuador's national telecommunications company CNT issued an announcement that the operation of their integrated service center and contact center was attacked by ransomware, with business operations, payment channels, and customer support interrupted. Global media disclosed that CNT was attacked by the RansomEXX's ransomware organization, successfully stealing 190GB of files and demanded a ransom of CNT.

The type of urban infrastructure under attack lately is responsible for guaranteeing the supply of day-to-day resources and goods for citizens. Individuals are feeling the sting of these attacks in their daily lives, just as many were affected by the Colonial Oil attack in early June 2021.
Forefront Dermatology Clinic
Medical centers are responsible for the collection and storage of masses of sensitive information and have become increasingly vulnerable targets amid the recent pandemic. Even small medical facilities are at risk in 2021, with Forefront Dermatology disclosing a report of a ransomware attack in July. The follow-up investigation determined that the medical information of 2.41 million patients was affected. The clinic is currently notifying the patients involved, but Forefront Dermatology representatives found some of the stolen files available for free on the Cuba Ransomware leak site.

HelloKitty Ransomware Attacks Increase
Security researchers have discovered several “Hello Kitty” ransomware variants targeting Linux systems, designed to target and secretly host virtual machines on VMware ESXi servers. This malware attempts to shut down VMs running on target servers and encrypt files.
HelloKitty ransomware uses SonicWall vulnerabilities to launch attacks. SonicWall has issued an emergency security notice recommending that users reinforce their SonicWall system as soon as possible.
HelloKitty ransomware is far from the only ransomware targeting ESXi servers. BAduk, RansomExx, Mespinoza and Darkside also have variants that target the same vulnerabilities in this server. Based on the best practices of nearly 1,000 users, Sangfor has several recommendations on how to fortify yourself against HelloKitty and other types of ransomware that exploit this vulnerability.
The Sangfor Ransomware Security Solutions
The Sangfor Ransomware Security Solution provides an innovative strategy that successfully mitigates ransomware attacks by breaking every step in the kill chain.
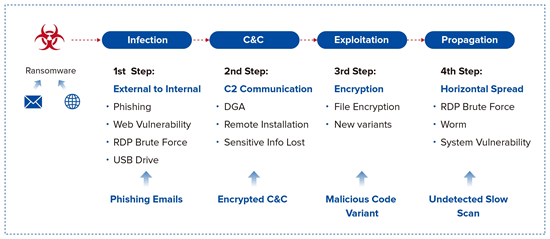
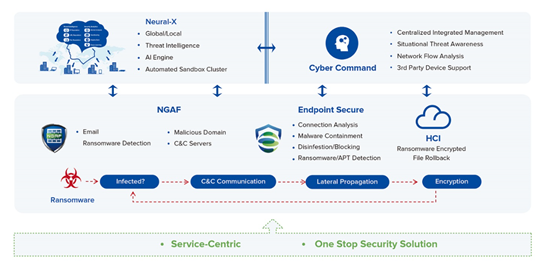
8 Tips for Daily Ransomware Protection
- Deploy automatic detection and protections during non-business hours
- Plan for extra security staff and deploy extra protections during holiday periods
- Deploy more stringent protections for Windows servers and Linux servers
- Plan for regular cold or remote backups
- As staff and users are the weakest link in the corporate security chain, improve internal security awareness of the dangers of weak passwords and phishing, and adopt a zero-trust scheme
- Strength any access controls of core data assets
- Perform daily patching for botnets and vulnerabilities
- Deploy a private network for each branch of the business, and deploy border control equipment like firewall to isolate and control the system.





