Every data breach has the potential to bring even the largest companies to their knees. Many organizations today simply cannot afford the reputational and financial losses following a data breach – leaving most industries vulnerable. The entertainment industry is a particularly targeted sector that holds massive amounts of private data. The latest Disney hack just shows the severity of the situation.
In this blog article, we look into the details of the Disney Slack data breach and try to uncover similar incidents before. We also look into the role of insider threats, how they harm ecurity, and how they can be prevented. Now, let’s first get a better understanding of the Disney breach as it happened.

Sourced from Shutterstock
Disney's Internal Slack Chats Leaked
On the 12th of July, a hacktivist group named NullBulge posted a claim on a dark web forum to have accessed and leaked thousands of Disney’s internal Slack messaging channels. They further claimed to have access to information about unreleased projects, raw images, computer codes, links to internal APIs, and login details.
The Disney breach was first reported by the Wall Street Journal which had reviewed several of the stolen files. These included conversations about maintaining Disney’s corporate website, software development, assessments of job candidates, programs for emerging leaders within ESPN, and photos of employees’ pets. The accessed data seems to stretch back to 2019 and indicates a significant breach of the entertainment giant’s communications channels.
While the initial estimation for the stolen data was 2.6GB, the group then posted again stating that they would now “leak the big guns” indicating that much more data had been accessed. The Disney hack seemingly sits at around 1.2 terabytes and is much more damaging than previously thought.
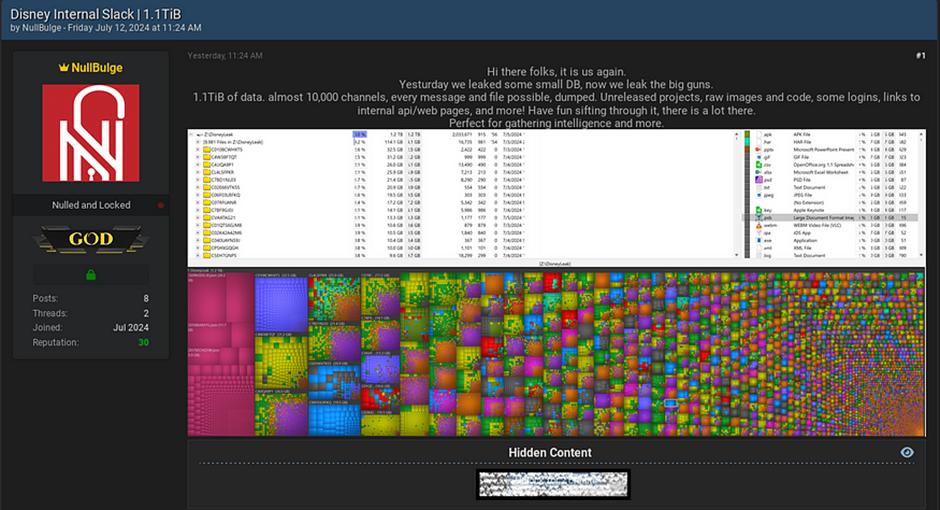
Sourced from Cybersecurity News
In an email to CNN, the hacking group claimed that it had gained access through “a man with Slack access who had cookies,” and that the group was based out of Russia. The group also admitted that its data breach was a result of the Club Penguin fans’ breach that took place almost a month ago.
NullBulge goes on to claim that its Disney hack was not malicious, and the group’s mission is to “enact ways to ensure that theft from artists is reduced and to promote a fair and sustainable ecosystem for creators.” The hackers seek to protect artists – especially in the wake of AI usage in the industry. The group stated in its email that Disney was the target of the attack due to how it handles artist contracts, its approach to AI, and a pretty blatant disregard for consumers. A Disney spokesperson said that the matter is being investigated.
With communications being such a vital element for most companies, the Disney Slack breach does highlight the vulnerability of the messaging services used in a professional setting. Let’s look further into data breaches involving the Slack platform in the past.
Slack Data Breaches
As one of the leading collaborative and team messaging applications on the market, Slack is used widely across various industries to maintain communications, send or receive files, and more. However, this also presents a specific risk to companies using the platform and discussing or transferring confidential information. Here are some of the data breaches that have affected the Slack platform:
- Uber Data Breach: In 2022, a hacker posted an internal message on Uber’s Slack channel claiming to have access to the taxi company’s systems. Initially thought to be a joke, the threat actor then listed confidential company information and posted a hashtag saying that Uber underpays its drivers. The 18-year-old hacker claimed to have used social engineering techniques to steal employee login details and gain access to the Uber system – further stating that it was only done for fun.
- EA Games Data Breach: EA Games was also the victim of a data breach in 2021 when hackers purchased a cookie for US$ 10 that allowed them to infiltrate the US$ 5 billion company’s Slack platform. The threat actor then posed as an employee to convince IT administrators to give them access to the company’s systems. This led to the theft of valuable game source code.
- Twitter Data Breach: X, formally Twitter, also found itself in hot water in 2020 when over 130 high-profile accounts became the targets of a simultaneous hack which led to them tweeting out links to a crypto scam. The hack was eventually traced back to the company’s Slack platform.
- GTA Data Breach: Rockstar game developers also suffered from a data breach when a hacker accessed the company’s Slack account to find and exfiltrate 90 videos of Grand Theft Auto game footage and posted them to the fan site GTAForums.
While monitoring the communication platforms used is important to prevent data breaches like these from happening, the ultimate culprit in these attacks stems from insider threats and social engineering techniques. Let’s get a better understanding of what an inside threat is.
What Is an Insider Threat?
An ‘insider’ can be defined as anyone from within a business that has access to privileged information – therefore an insider threat is any security threat facilitated or enabled by the actions of an insider. While these do mostly include intentional threats from inside a company, an insider threat can also be a negligent or oblivious employee. Hackers will take advantage of insider threats to gain login credentials, access, and information. This can then be used to ransom the company, exfiltrate data, or simply be sold on the dark web.
The Disney data breach can be seen as a type of insider threat due to the hackers gaining access through the use of an employee’s credentials and the implication the group gave of having an inside man. We can now look into how an insider threat can damage an organization’s security.
How an Insider Threat Can Harm an Organization's Security
Naturally, an insider threat poses a security risk for any company. These cybersecurity incidents can cause catastrophic reputational damage to a business if confidential information is leaked. Some of the main ways an insider threat can harm an organization’s security include:
- Data loss: Customer records and crucial information can be lost, leaked, or used as leverage.
- Financial losses: Companies may suffer stock drops after an insider threat and may also succumb to paying a ransom.
- Compliance issues: Most countries have very strict data privacy laws and regulations. When data is breached by an insider threat, companies have to bear the legal responsibility of the incident – resulting in hefty fines, prison time, and other legal implications.
- Reputational loss: A company needs to uphold a strong security posture. After an insider threat incident, a business can suffer devastating reputational damage in the industry that might dissuade potential clients or partners.
- Loss of trade secrets: Intellectual property is a vulnerable and valuable asset for any company that can be put in danger by an insider threat.
These are all valid reasons for a company to maintain its security posture and try to prevent insider threats wherever possible. To learn more about insider threats, let’s delve into some of the more famous insider threat cases to date.
Famous Insider Threat Cases
Forbes reported that insider threat incidents have risen by 44% since 2022. These security breaches need to be recognized when they happen for companies to truly prepare themselves. Some of the more famous insider threat cases in the past include:
- AT&T Data Breach: On the 7th of July, AT&T disclosed that a threat actor stole phone call and text message records from nearly every AT&T customer between May and October of 2022. This totals approximately 109 million people. The threat actor allegedly gained access to AT&T's Snowflake cloud storage account. Earlier this year, another AT&T data breach exposed the data of 7.6 million current customers and 65.4 million former account holders.
- MGM Resorts Data Breach: In 2023, an MGM cyber-attack hit several major MGM hotels and affected operations. The Scattered Spider hacking group behind the attack used social engineering attacks to manipulate people into giving out sensitive information.
- Google Data Breach: In 2016, a former Google employee, Anthony Levandowski, downloaded thousands of company files onto his laptop that were related to Google’s early self-driving car program “Project Chauffeur”. This was meant to provide a competitive edge at his new job at Uber. Google may have lost up to US $1,500,000 due to the theft.
- Proofpoint Data Breach: Ironically, cybersecurity firm Proofpoint was victim to a breach in 2021 when Samuel Boone, a former employee, stole confidential sales enablement data before starting a new job at competitor Abnormal Security.
- Tesla Data Breach: In 2023, Tesla suffered a major data breach orchestrated by two former employees who leaked sensitive personal data to a foreign media outlet. The leaked information exposed customer bank details, production secrets, and complaints about Tesla’s Full Self-Driving feature. It also included names, addresses, phone numbers, employment records, and social security numbers of over 75,000 current and former employees.
While these can be alarming stories to read and the insider threat statistics seem to only be growing, companies can put preventative measures in place to protect themselves, their clients, and their data.
How to Prevent an Insider Threat
For any business struggling to maintain a strong cybersecurity posture in the modern world, insider threats can be a daunting reality to face. Not insider threats are carried out by disgruntled employees with malicious intentions, however, this only widens the possibility of being the victim of a data breach as a simple error in judgment can result in a breach. Here are some ways that companies can prevent insider threats:
- Installing an effective next-generation firewall to isolate suspicious files and protect the network.
- Implementing strict cyber hygiene practices and using cybersecurity training to ensure that employees don’t become victims of social engineering attacks.
- Keeping software and systems updated with the latest patches to avoid vulnerabilities.
- Embracing a system of zero-trust to ensure secure and controlled access management. This will provide access to only authorized personnel and limit risk.
- Ensuring network visibility to monitor for suspicious activity.
- Frequently auditing your cybersecurity and conducting penetration tests to ensure your security posture is strong.
The Disney hack should serve as a reminder that cybersecurity practices need to be adhered to across platforms within a company. Insider threats come in different forms and might be difficult to spot in advance, but with the right tools and practices, you can protect your business as best as possible. Sangfor provides advanced and tailored solutions to actively detect and prevent insider threats. For more information on cloud infrastructure and cybersecurity, visit www.sangfor.com today.





