 Gigabyte, a Taiwanese computer motherboard and component manufacturer, known for their graphics cards, data centre servers, laptops and even monitors, was recently hit hard by the RansomEXX ransomware group, who stole 112GB of data then threatened to publish it.
Gigabyte, a Taiwanese computer motherboard and component manufacturer, known for their graphics cards, data centre servers, laptops and even monitors, was recently hit hard by the RansomEXX ransomware group, who stole 112GB of data then threatened to publish it.
The attack went down late Tuesday night, into Wednesday morning, when the company was forced to shut down their Taiwan-based offices. The Taiwanese portion of the website was affected, as well as other sites and functions.
Recent RansomEXX Activity
In the ransom note, published on BleepingComputer.com, you can see the gang warning Gigabyte to not panic and start changing things and causing damage.
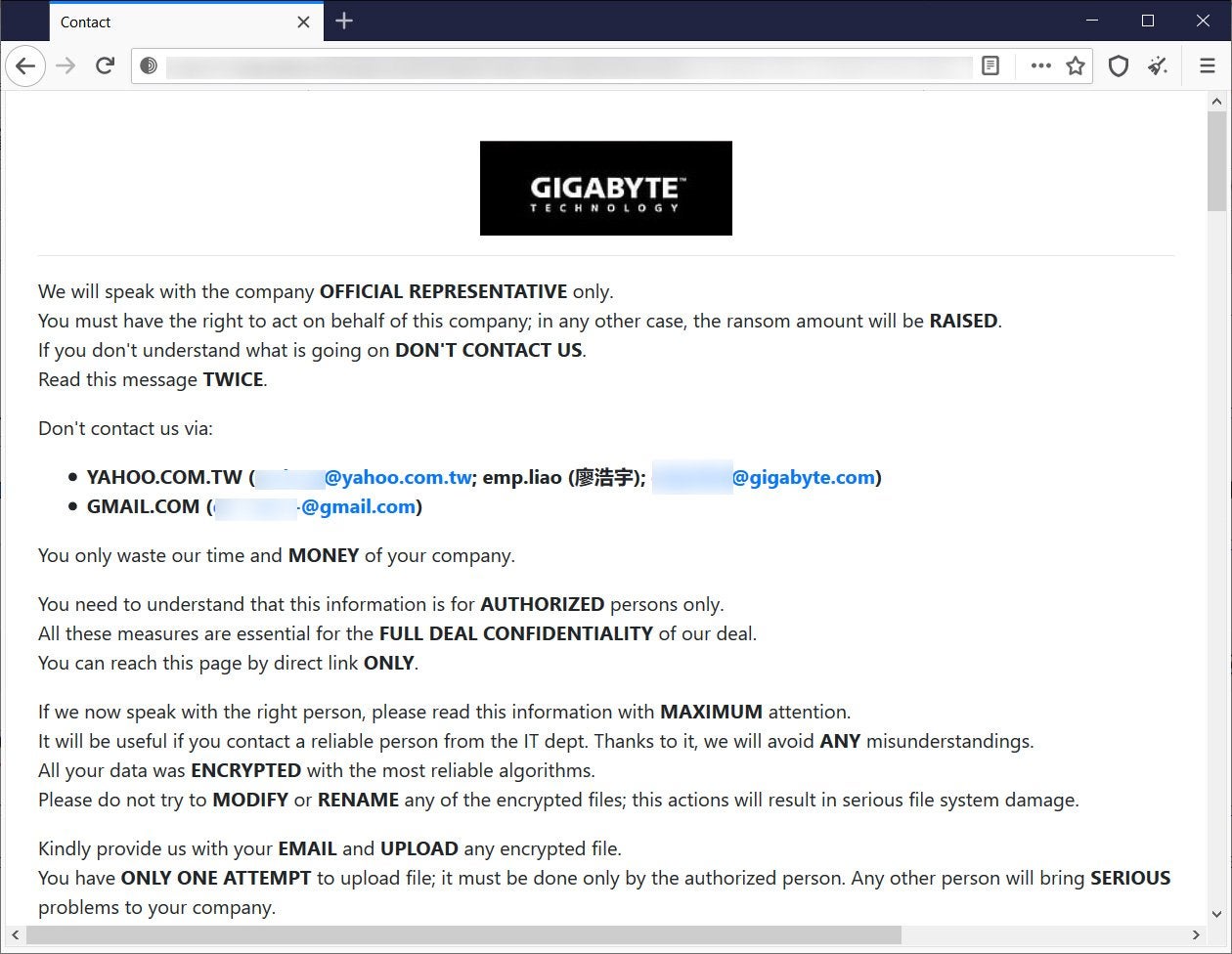
Non-Public Gigabyte data leak page
Analysis by the Cybereason Nocturnus Team discovered:
- Human-operated targeted attacks: RansomEXX is used with multi-stage, human-operated attacks, targeting various government related entities and tech companies.
- Disables security products: The Windows variant disables various security products for easier execution.
- Multi-Platform: RansomEXX started as Windows based, but a Linux variant was discovered in early 2021.
- File-less ransomware: RansomEXX is delivered as a secondary, in-memory payload, making it harder to detect.
Last month, CNT, Ecuador's state-run telecommunication carrier, suffered a RansomEXX ransomware attack which affected its business operations, payment portal, and customer support.

Hidden RansomEXX data leak page for CNT
In English, the alert Customer read, "Today, July 16, 2021, the National Telecommunications Corporation, CNT EP, filed a complaint with the State Attorney General's Office for the crime of “attack on computer systems "so that the preliminary investigation is carried out and the responsible."
We can see a strongly branded consistency between the two messages, indicating a certain level of organization. This could be a cyber-criminal organization who cares about image, so we expect to see more – at least as long as they stay successful!
PC Maker Ransomware Targets!
We all watched as Acer, Quanta, and by association, Apple, were hit hard by REvil ransomware attacks earlier in 2021, and tech-company Gigabyte is just the latest target. It seems to be a medal of honour to be able to hack a tech company. The tech industry is estimated to be worth 5 trillion USD, with over a third market share from North America, and with Asia the largest contributor to the global IT industry, with 32% market share. Technology companies are advised to look carefully at their network security and see if it’s still defensible!
Gigabyte Ransomware Attack
Apparently, while the attack hit the internal business servers hard and fast, day to day manufacturing operations are not affected. IT teams reportedly found the attack quickly and worked tirelessly to stop it but customer support operations such as access to updates were affected. Among the data stolen was documentation from technology companies Intel, American Megatrends and AMD. Although all these companies are now involved, Gigabyte has been quiet in the media about the details, just as Acer, Quanta, and Apple were.
Recorded Future reports that they have seen a private page on the dark web with sample files from the attack. “We have downloaded 112 GB (120,971,743,713 bytes) of your files and we are ready to PUBLISH it. Many of them are under NDA (Intel, AMD, American Megatrends),” the extortion page says.
What Did We Learn?
Gigabyte had back-ups at the ready, and some sort of protection for their manufacturing processes in place before the attack. Other recent attacks in the USA could have avoided costly downtime with proper back-ups. Even Colonial Oil had backups! And they were forced to use them when the paid for ransomware decryption key worked so slowly they couldn’t wait any longer. Gigabyte is lucky to have their manufacturing up and running but stands to lose industry secrets if any of the stolen data is published. It’s important to think about cyberattacks and network security before it becomes a problem. Consider working with an incident response team (IR) to secure your network from threats, and have professionals available to help if the worst happens.
Many enterprises are considering upgrading their network firewalls. They are looking at AI-powered, convergent technologies like the Sangfor Next Generation Application Firewall (NGAF). Current endpoint security solutions are being re-examined to see if they can protect against the new generations of AI-enable ransomware. Does the endpoint detection & response (EDR) solution have robust protection like a ransomware honeypot instead of guessing what files to backup before being encrypted? For more information on ways you can future-proof and better secure your business, visit your local Sangfor Technologies reseller, experts in network security and ransomware preparedness, and see how Sangfor can make your IT simpler, more secure and valuable.





