Hospitals Under Cyber Attack: Recent Incidents
July 2019: A new-born baby was delivered with severe brain damage after the umbilical cord had caught around her neck. Her life ended prematurely nine months later. The hospital where she was delivered, the Springhill Medical Center in Alabama, USA, had recently been the victim of a ransomware cyber attack. The hospital’s IT systems were down, including the fetal heartbeat monitors that may have detected the baby’s condition, potentially saving her life through a swift C-section. (Reported by the Wall Street Journal)
September 2020: A 78-year-old German woman tragically lost her life after her ambulance was diverted to a hospital 32km away from the intended hospital, delaying the treatment of her aortic aneurysm by an hour. The original hospital, the University Hospital of Düsseldorf, had been attacked with ransomware. With critical infrastructure paralyzed, the hospital could not have provided her with the necessary medical attention and had no choice but to turn her away. (Reported by Wired)

These two incidents are believed to be the first instances of death caused by ransomware attacks on hospitals. They should make us sit up and reconsider the potential harm and losses caused by cyber-attacks. No longer are they restricted to financial or intellectual property losses, or social and political disruption. Now, they can also take lives.
Hospital cyber-attacks are very real. Healthcare organizations have increasingly found themselves in the crosshairs of cyber-criminal organizations, so much so that cyber-attacks on healthcare have become a common occurrence. According to the 2021 H2 Healthcare Data Breach Report from Critical Insights, the total number of healthcare data breaches in the U.S. reached an all-time high of 679 in 2021, while the number of affected people amounted to 45 million, up from 34 million in 2020. Similarly, the 2021 Internet Crime Report released by FBI’s Internet Crime Complaint Center reported 148 healthcare cyber-attacks in H2 2021, by far the largest proportion of attacks among the various industries in the same time period. Evidently, if the healthcare industry does not tighten up its security fast, the next cyber-inflicted fatality could just be around the corner.
As with solving any problem, causes have to be analyzed before actions can be drawn up and implemented. The following section will look at some of the main reasons why healthcare organizations have become such important targets of cybercriminals, and how the healthcare industry could save themselves from this pandemic.
6 Reasons Why Healthcare Organizations Are Under Cyber-Attack With Security Recommendations and Solutions from Sangfor
1. A Data Treasure Trove
On Sept 5, 2021, a hospital in Thailand province of Saraburi was the victim of a ransomware attack, slowing operations and relying on manual functions, but no demand for payment ever came. Over the next few days, more hospitals were victims of attack including some government facilities.
From a threat actor’s perspective, the goals of carrying out an attack are simple: to obtain something of value, whether it be financial or intellectual; or to cause havoc and disruption, for some other ulterior motive or simply out of spite. With this in mind, it’s not difficult to see why healthcare organizations, especially hospitals, are prime targets of cyber-attack.
Think about it. Hospitals store and operate a huge amount of priceless data—the health records of patients. Now, you might wonder what the value of knowing, say, so and so has a broken arm or so and so has terminal illness is to an attacker. True, this kind of information might not be worth much to an attacker, but they are critical to the patients and to the hospital. Health data is no ordinary data. It’s the data that concerns the health, and potentially the life and death, of people. Cyber criminals are acutely aware of this and often take advantage by targeting hospitals with ransomware attacks.

In a ransomware attack, victims are held in ransom by having their data encrypted, rendering them inaccessible. Ransomware attacks in hospitals cripple their IT systems, depriving hospital staff of critical medical data, severely hampering their ability to provide patients with timely and adequate care. Due to the critical nature of the comprised data, cyber criminals are almost certain of a handsome reward, as hospitals are basically left with no choice but to pay up.
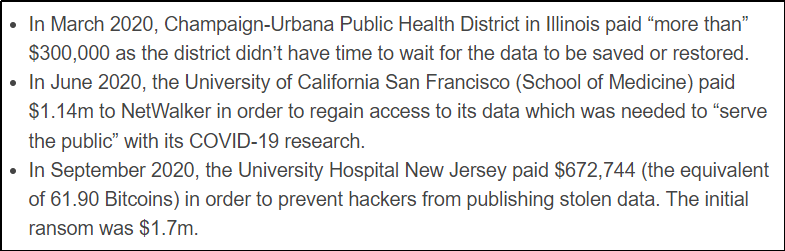
Disclosed ransomware payments by healthcare organizations as reported by Comparitech
Security Recommendations and Solutions from Sangfor to avoid Cyber Attacks on Hospitals:
- Perform regular data backups, especially core data, so that data can be restored in the event of a data encryption during ransomware attack. Use hyperconverged infrastructure (HCI) for the efficient and cost-effective backup and data restoration of large volumes of data.
- Leverage advanced ransomware protection technologies that block every step of the attack kill chain, including AI-powered Next Generation Firewalls (NGAF), Network Detection & Response (NDR), and Endpoint Detection & Response (EDR) to sniff out malicious activity at the perimeter before data can be encrypted.
2. The Perils of Ignorance allowing ransomware to enter healthcare system
Many cyber security outsiders assume that successful cyber attacks are the result of technical failures, for example, the antivirus’ failure to detect and block certain malware. This might well be the case; security software and devices are not 100% foolproof after all. However, a large portion of successful breaches are in fact aided by human errors and lapses. According data compiled by Statistica, insider negligence accounted for around 40% of significant cyber security incidents in U.S. healthcare organizations in 2019 and 2020. Medical professionals and staff may be excellent at carrying out their medical duties but are not the savviest when it comes to cybersecurity. Weak and default passwords, delayed security updates and other poor security practices are a real problem.
However, medical staff appear especially prone to phishing attacks. In a phishing attack, attackers construct and send out e-mails containing malicious links that look perfectly legitimate. After clicking the link, victims are directed to a webpage where malicious files are downloaded, granting attackers access to the system. Such attacks accounted for a sizeable 57% of significant cyber attacks experienced in U.S. healthcare organizations in 2020 according to Statistica. Cybercriminals clearly have a hold on their targets, while healthcare workers are completely in the dark.
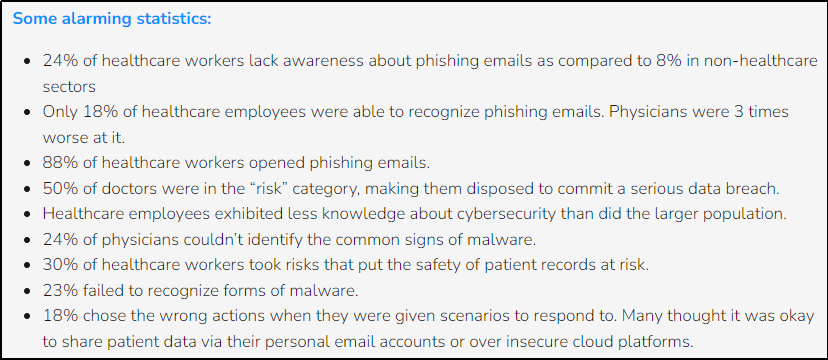
Further data regarding the security awareness of healthcare staff, courtesy of Reliable IT MSP
Security Recommendations and Solutions from Sangfor:
- Staff cybersecurity training and assessments, including phishing attack simulations.
- Learn how to spot phishing e-mails: Top 9 coronavirus phishing scams making the rounds & COVID-19: Screenshots of Phishing Emails
3. A COVID Brewed Storm opening doors for Ransomware attacks in hospitals
The COVID-19 pandemic proved to be the trigger for a new wave of cyber activity. Cyber attacks aimed at hospitals and the healthcare organizations, in particular, reached new heights and broke all kinds of statistical records in 2021. The surge in attack activity can be explained by some of the healthcare sector’s unique circumstances.
For one thing, hospitals across the globe were overwhelmed by the sheer number of infected people requiring medical treatment. The state of havoc created the perfect cover under which cyber criminals could operate with the least amount of attention—hospital staff simply had no time to care about cyber security when people were dying.
Moreover, hospitals became the repositories of another kind of extremely valuable data—COVID-19 treatment and research data. During the pandemic’s infancy, knowledge about the virus was limited, meaning that the various treatments hospitals across the world were experimenting with became priceless and the target of cyber criminals. HIPAA reported a huge 231% MoM spike in the number of breached data records experienced by U.S. healthcare organizations in February 2020, when the COVID pandemic first hit.
Cyber criminals also took advantage of the pandemic by carrying out COVID-themed phishing attacks. Given that COVID was at the overriding agenda of medical workers, they became the easy targets of these highly deceptive scams.
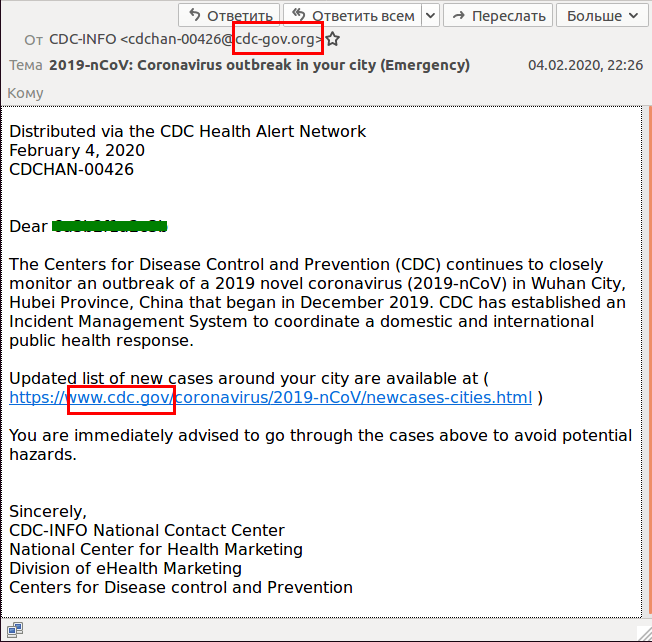
Example of COVID-themed phishing e-mail, courtesy of Kaspersky
Security Recommendations and Solutions from Sangfor:
- Perform regular data backups, especially core data, so that data can be restored in the event of a data encryption during ransomware attack. Use hyperconverged infrastructure (HCI) for the efficient and cost-effective backup and data restoration of large volumes of data.
- Staff cybersecurity training and assessments, including phishing attack simulations.
- Learn how to spot phishing e-mails: Top 9 coronavirus phishing scams making the rounds & COVID-19: Screenshots of Phishing Emails
4. The Double-Edged Sword of IoMT
The healthcare industry has been revolutionized by the introduction of advanced medical equipment and devices, so much that they have been given their own designation—the Internet of Medical Things (IoMT). The IoMT are a host of medical devices and software applications that connect to healthcare IT systems through networking technology, from medical sensors for remote patient monitoring to infusion pumps and MRI scanners. The proliferation of these innovations has undoubtedly enhanced the efficacy and efficiency of medical care, but that has come at the expense of network security.

The majority of IoMT do not have built-in security, leaving hospitals exposed to a cyber attack. Hackers can scour these devices for loopholes or vulnerabilities through which they can infiltrate the network. Cynerio reports 53% of connected medical devices and other IoT devices contain a known critical vulnerability, while a third of bedside IoT devices have an identified critical risk. 73% IV infusion pumps, which account for 38% of a typical hospital’s IoMT inventory, were found to contain a vulnerability.
Worryingly, IoMT are not only points of entry for attackers but can be abused themselves for dangerous purposes. For example, medical scanning equipment can be manipulated to produce faked images, leading to faulty diagnosis. The dosage of infusion pumps can also be altered, possibly to fatal consequences.
Security Recommendations and Solutions from Sangfor:
- Maintain a complete and accurate inventory of all IoMT assets that identifies the last time a software update occurred and version.
- Subscribe to vulnerability bulletins to receive notification if any vulnerabilities are discovered in IoMT operating systems or applications.
- Deploy access control systems like Internet Access Gateways (IAG) to separate networks used for IoMT from administrative and public systems. IAGs will also monitor and audit all traffic to identify attacks against IoMT.
5. An Imbalanced Technological Reform
While significant improvements have been made to medical equipment, there is something peculiar about hospitals in that their PCs are typically old and outdated. Anyone who has visited a hospital may have noticed the bulky computers used by administrative staff and even by doctors. Whatever the reason for their overdue replacement, these legacy systems in healthcare, often running outdated operating systems such as Windows XP, pose a huge threat to network security.
As alluded to above, hackers rely heavily on vulnerabilities or flaws in computer systems, software and processes to gain initial access to a network. Outdated operating systems and software may no longer be compatible with the latest security updates and patches, meaning that only older versions containing vulnerabilities can be used.
Security Recommendations and Solutions from Sangfor:
- Endpoint Detection & Response (EDR) technology to scan PCs for vulnerabilities.
- Unified Endpoint Management Solutions to ensure all devices connected to the network are installed with the latest system and software updates.
- Switch to cloud-based applications to make sure business applications are always installed with the latest security updates.
- Replace computers with Virtual Desktop Infrastructure (VDI) to ensure that applications and desktop operating systems can be quickly restored if compromised and prevent leakage of data.
6. A Matter of Vision and Investment
Ultimately, security weaknesses come down to a lack of vision and investment. Data from Statistica reveals that almost a quarter of U.S. healthcare organizations apportioned a mere 3-6% of their IT budget for cyber security purposes—that is 3-6% of the IT budget, not the overall budget—while only 6% of organizations dedicated over 10%. It is not difficult to conclude from such figures the reason why hospitals and healthcare organizations are so susceptible to cyber attacks.
With a greater focus on solving problems long-term, coupled with greater investment in network security infrastructure, cyber security training for employees, and dedicated cyber security operations and personnel, cyber security risks can be minimized to a large extent.

However, healthcare organizations must not fall into the trap of believing installing security equipment equals total protection. While security devices do an excellent job at detecting and blocking the majority of malware and malicious activity, they are not unassailable. Cyber attacks are becoming so sophisticated and intelligent that they are able to evade the most stringent of detections. Preferably, dedicated cyber security personnel are hired to analyze network activity and detect unsusceptible behavior as well as adjusting security policies in response to the forever-changing network environment. However, there is a global shortage of qualified cyber security personnel. It may not be possible to fill positions with enough expertise.
This is when organizations should leverage the resources that their security partners or vendors offer to backstop until resources can be hired.
Security Recommendations and Solutions from Sangfor:
- Hire expert cyber security service providers to perform a full security assessment to understand the organization’s state of security. Take actions based on security assessment.
- Leverage security partner or vendor resources to supplement security operations and especially for incident response.
- Outsourcing part or all network security operations and maintenance to security service vendor through a Managed Security Service (MSS), and let the professionals take of all things security while medical staff can focus on what they do best.
About Sangfor Technologies
Sangfor Technologies is an APAC-based, global leading vendor of IT infrastructure and security solutions specializing in Network Security and Cloud Computing. Visit us at www.sangfor.com to learn more about how Sangfor's Cloud and Security solutions can make your digital transformation simpler & secure.





