About the Schneider Electric data breach
A well-known French multinational company, Schneider Electric, has suffered a massive data breach by the ransomware group known as Hellcat. The group claims that they have stolen compressed data worth 40 GB. Schneider Electric is an energy giant with more than 100,000 employees globally and reported revenue of $39 billion last year.
Ransom amount demanded by Hellcat Ransomware
Out of the very norm, the Hellcat group demands that the ransom amount of $125,000 must be paid in baguettes; yes, you heard it right, baguettes as in bread. Many firms reached out to Schneider to give a statement if the Hellcat group plans to settle for cryptocurrency or other payment methods, but they have declined to provide any further statement. The official statement from the Hellcat group was posted on the X platform (formerly Twitter) in the following words:
To secure the deletion of this data and prevent its public release, we require a payment of $125,000 USD in Baguettes. Failure to meet this demand will result in the dissemination of the compromised information.
The group further added that the ransom amount would be reduced to 50% if the vendor confirmed the breach.
As Forbes found out, the Hellcat group really wants the $125,000 in Monero cryptocurrency, and they overplayed the baguette part just to get in the headlines and gain spotlight attention.
Reports of Schneider data breach by news firms and agencies
As reported by The Register, they contacted Schneider Electric to take the statement on the matter, and their spokesperson replied the following via email for Schneider data breach:
Our Global Incident Response team has been immediately mobilized to respond to the incident. Schneider Electric's products and services remain unaffected.
In another statement shared by Schneider Electric to the Recorded Future News firm, the company subtly acknowledged the security breach. The official statement goes by:
Schneider Electric is investigating a cybersecurity incident involving unauthorized access to one of our internal project execution tracking platforms which is hosted within an isolated environment.
A security researcher, Hüseyin Can Yuceel at Picus Security, said in a statement to Forbes on this Schneider data breach:
Ransomware is a business model, and we can think of this bizarre baguette demand as a marketing stunt.
The researcher further added that Hellcat is relatively new to the ransomware game and might be doing this baguette stunt to gain popularity and attention.
trying to get attention and establish trust for future victims and associates for a possible Ransomware-as-a-Service operation.
Attack method of Schneider data breach
The group claimed that they had access to the company's Atlassian Jira system. The breach compromised critical data, including projects, issues, plugins, and over 400,000 rows of user data, totaling more than 40GB of compressed data.
They even published evidence of the attack on social media platform X, highlighting how they have gained access to the vendor’s custom Jira system. Following are some of the screenshots that are still live on platform X:
Hellcat ransomware group
Being new to the ransomware game, Hellcat group has already earned its due fame and popularity by playing the baguette stunt. The group shared the following image via the X platform, mentioning the details of the attack and necessary next steps:
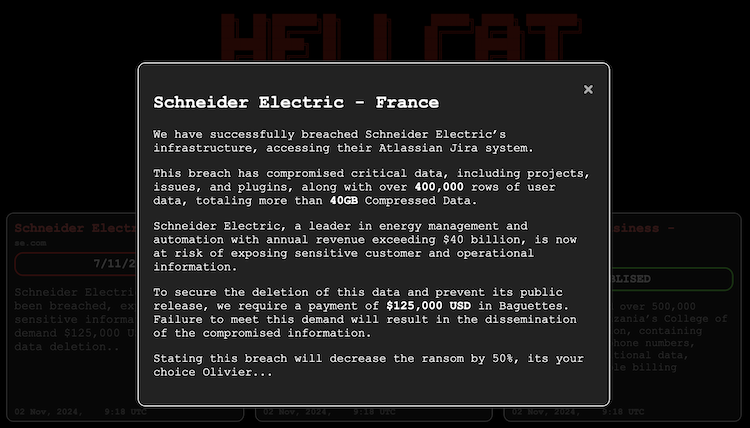
Image source: Cybernews, Schneider Electric hit by another breach, ransomware gang demands $125,000 “in baguettes”
The Hellcat ransomware group gained massive attention in a short time by targeting high-profile entities. They have also recently breached Jordan’s Ministry of Education and College of Business Education, Tanzania, as posted in another X account.
The group has established a substantial reputation by targeting government organizations, educational institutions, and giant firms such as Schneider Electric.
The hellcat ransomware group operates by infiltrating highly sensitive systems, exfiltrating large amounts of sensitive data, and threatening the victims to release it unless their ransom demands are met. Per the norms of ransomware groups, they usually publish a subset of sensitive data on the dark web to gain attention, pressurize the victim to meet their demands, and enhance their visibility.
How can organizations safeguard against ransomware attacks?
Ransomware threat continues to evolve massively, with threat actors finding new and more sophisticated ways to attack their victims. It is crucial for organizations to have a foolproof security strategy to protect their assets, data, systems, and operations. By leveraging a combination of advanced technologies, security tools, and proactive measures discussed below, organizations can substantially enhance their resiliency against damage-inducing attacks.
- Maintain Strong Backup and Recovery Strategies: Organizations must regularly back up their critical data and systems in a secure location. Additionally, organizations should test backup, restoration, and remediation activities from time to time to ensure the readiness and effectiveness of the backup systems in the event of ransomware attacks or system breaches.
- Employ Extended Detection and Response (XDR) Solution: XDR solutions provide a holistic approach to the organization's security by integrating data from different security tools such as endpoint protection, cloud security, threat intelligence platforms, and among others. XDR solutions provide end-to-end network visibility, thus eliminating any blind spots that may be exploited for potential ransomware.
- Employee Awareness Programs: As the saying goes by: employees are the weakest link in an organization's security posture. Eliminate this by training and educating your employees about ransomware attacks, phishing attacks, and social engineering tactics. Educate them that they should not share confidential information online and spot any social engineering tactics that may be used to obtain information or trade secrets.
- Adopt Network Detection and Response (NDR) Solutions: NDR solutions intelligently monitor the network traffic for threats and suspicious activities. NDR solutions can uncover existing security breaches and respond to ransomware propagation attempts. These solutions leverage AI and threat intelligence and can identify indicators of compromise (IOCs).
By implementing these strategies, organizations can significantly bolster their defenses against ransomware, ensuring a more secure and resilient operational environment.





