As everyone from my company has been working from home for months, I have several daily concerns:
- Is there a chance of malware infection coming from staff PCs to the organization’s network?
- Were there any targeted attacks from the Internet, or successful attacks the organizational network during this period?
- Will attacks bypass existing network security products and successfully compromise critical servers?
- Are employees performing suspicious activities during this period of uncertainty?
You are not alone…

These concerns are shared by many Chief Information Security Officers (CISO) and IT Directors. Due to COVID-19, many organizations have shifted their working culture from office to work-from-home (WFH). Most organizations either purchase SSL VPN or Virtual Desktop Infrastructure (VDI), and some even migrate their critical servers and businesses to cloud-based, in order to maintain consistent business operation.

Allowing employees to work from home is a good way to keep personnel safe, while simultaneously keeping the business running. However, cybersecurity issues have surfaced. Most non-IT employees or employees with minimum and limited IT knowledge and security awareness struggle keep their personal PCs and laptops as secure and clean as the organization’s workstations. Once they browse non-work-related websites or click on certain email attachments, there is no alert or countermeasure to prevent backlinks, malicious downloads or social engineering traps. Employees are often not aware if they are being attacked or if their laptops or PCs are infected.

When employees without knowledge of their laptop or PC security status connect their devices to organization’s network, either by means of Remote Desktop Protocol (RDP) or SSL VPN, they will likely spread malware from the public network to organization’s internal network by bypassing the gateway protection of gateway firewall, Intrusion Prevention System (IPS), and Web Application Firewall (WAF).

Finally, all malware that hide inside infected laptops will take this opportunity to spread into the organization network. The malware will start on searching for victim servers with the following vulnerabilities or weaknesses:
- Unpatched servers or workstations
- Accounts with weak passwords
- Servers or workstations with outdated and vulnerable software and applications
Once the malware successfully gains access to at least one server, it will start the next step, depending on the type of malware, often establishing a Command and Control server, downloading an exploit kit, implanting a backdoor, using resources for cryptocurrency mining, or worst of all, encrypting files and demanding a ransom.
Sound scary? Yes, it does. Nobody wants their corporate network infected by unnoticed malware that will significantly impact their environment.
What approach can we take to ensure network cyber health hygiene during this post-pandemic period?
Sangfor's Threat Identification, Analysis and Risk Assessment (TIARA)
Threat Identification, Analysis and Risk Assessment (TIARA) is a set of cybersecurity services that leverage the automated detection and response capability of Sangfor’s threat intelligence platform, delivered by Sangfor security consultation experts, to help customers with insufficient security expertise understand their threat landscape, improve their detection time, and rapidly improve their security posture or overall security infrastructure.
Now, let’s look at the three main components of TIARA that could greatly assist an organization.
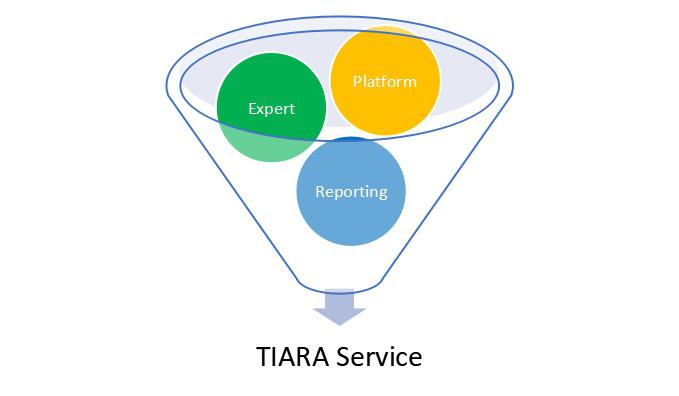
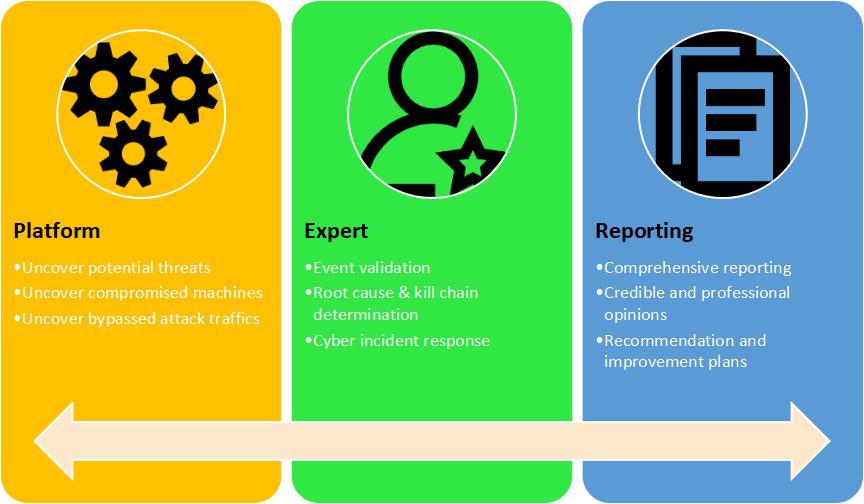
How TIARA Services Benefit an Organization
- Awareness of current security status provides a clear direction to enhance and improve overall security posture of the organization
- Greatly reduce risk of exposure and security incident impact
- Increases the effectiveness and efficiency of internal resources
- Increases security and risk awareness among internal employees
The TIARA service scope consists of validation, analysis, investigation, and remediation, including but not limited to the following events:
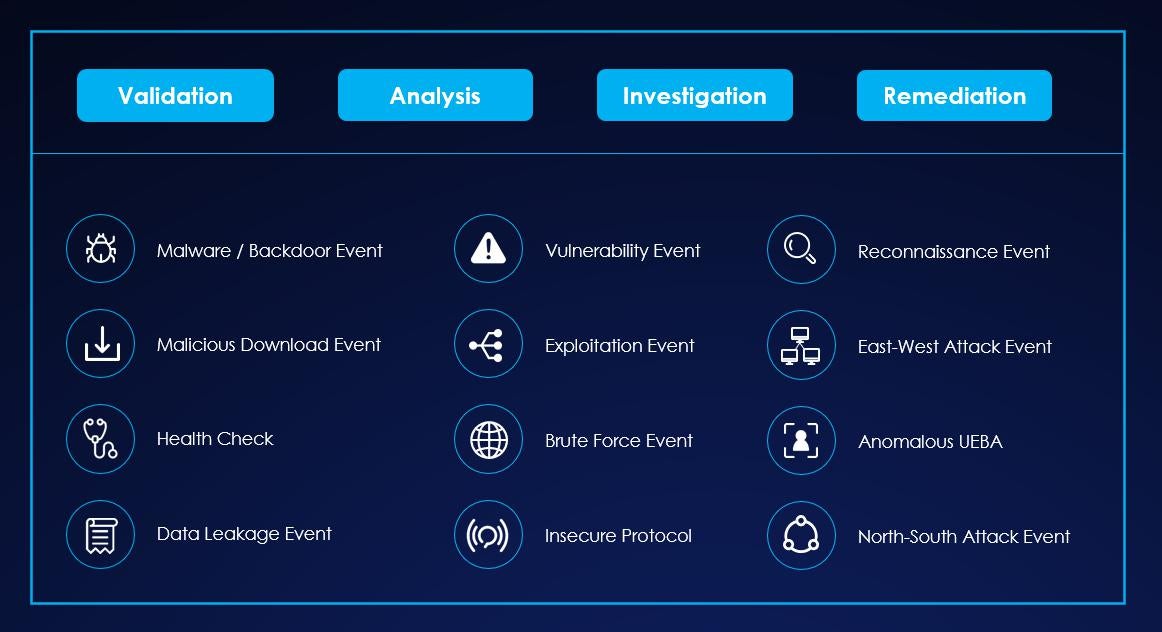
Refer to TIARA & MDR Service to download the brochure.
In the event of an attack, you may approach Sangfor for Cyber Incident Response Service to stop the damage and remediate risks.
Why Sangfor?
Sangfor Technologies is an APAC-based, global leading vendor of IT infrastructure solutions specializing in Network Security and Cloud Computing. Visit us at www.sangfor.com to learn more about Sangfor’s Security solutions, and let Sangfor make your IT simpler, more secure and valuable.





