Malware remains one of the most persistent cybersecurity threats facing organizations. In 2025, it has evolved into more stealthy, adaptive, and financially damaging variants than ever before.
According to the latest CISA Malware Analysis Reports and the Sophos Threat Report, top malware families include ransomware, infostealers, remote access trojans (RATs), and fileless malware.
To defend against modern attacks, it's critical to understand what malware types exist and how they infiltrate systems.
Types of Malware
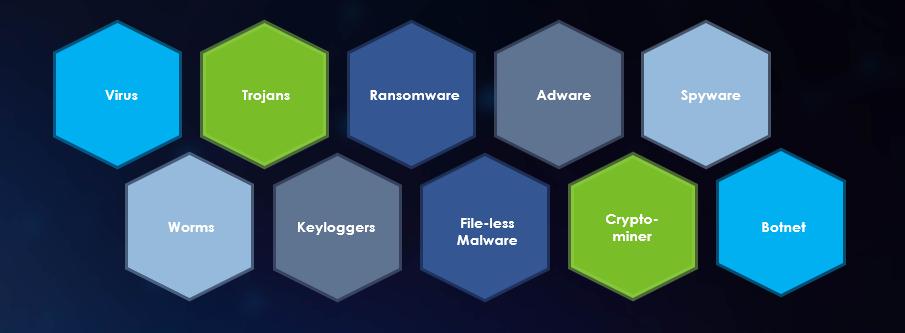
1. Ransomware
Encrypts data and demands payment for decryption keys. In 2024, the average ransomware payment hit USD $850,000. Double extortion tactics—encrypting data and threatening to leak it—are now common.
2. Trojan Horse
Masquerades as legitimate software while secretly installing backdoors for attackers. Trojans are commonly spread through phishing emails and fake downloads.
3. Worms
Self-replicating programs that spread through networks autonomously. They often carry payloads like ransomware and are capable of causing significant system disruption.
4. Spyware
Silently collects user information—keystrokes, login credentials, browsing habits—and transmits it to attackers. Commonly bundled with freeware or browser extensions.
5. Adware
Displays intrusive ads and can slow down system performance. While not always malicious, it opens the door to more severe threats.
6. Rootkits
Designed to hide malware deep inside systems, even from security tools. Rootkits often operate at the kernel level, making them hard to detect or remove.
7. Fileless Malware
Operates in memory without writing files to disk. It uses tools like PowerShell or WMI to blend in with legitimate processes, making detection by antivirus extremely difficult.
8. Keyloggers
Record every keystroke typed by a user, capturing login credentials, card numbers, and sensitive communications. Often installed via Trojans.
9. Botnets
A network of compromised devices controlled remotely by cybercriminals. Botnets are used to launch DDoS attacks, send spam, or carry out credential stuffing.
10. Infostealers
Specialized malware such as RedLine or Vidar that extracts browser passwords, cryptocurrency wallets, and saved credentials. Frequently spread through phishing or cracked software.
How Does Malware Transmit?
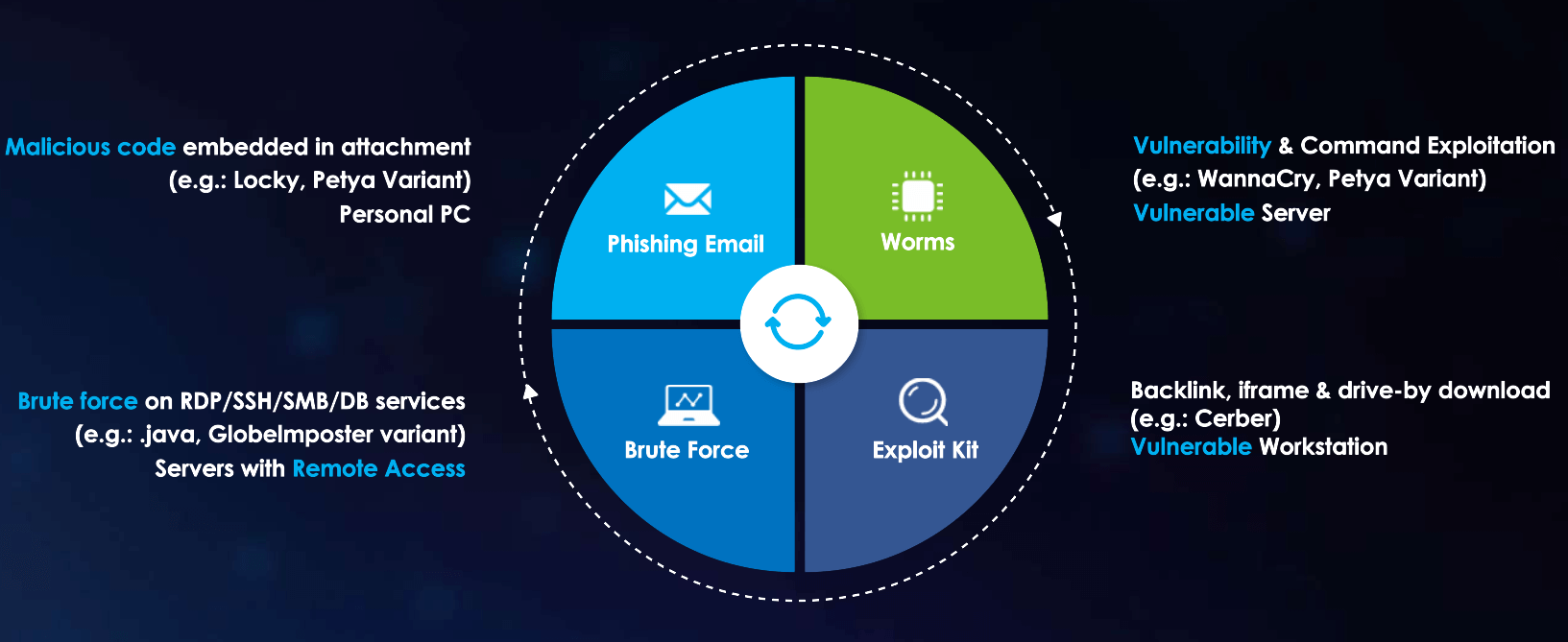
If organizations understand how malware is transmitted or spread, they could review their attack surfaces from time to time, and remediate any risks as necessary. Let’s have a look how each type of Malware transmits.
1.Phishing Emails:

As most of us know, phishing emails are one of the most common social engineering tricks used to spread malware or viruses. According to Webroot.com, “Phishing is a type of online scam where criminals impersonate legitimate organizations via email, text message, advertisement, or other means, to steal sensitive information. This attack is usually done by including a link that will appear to take you to the company’s website to input your information – but the website is a clever fake, and the information you provide goes straight to the crooks behind the scam.” It usually involves an innocent victim who lacks security awareness for this attack to be a success.
2.Worms and Vulnerabilities:
Worms and the vulnerabilities are another common malware type attackers use to infiltrate a system. Worms exploit vulnerabilities, especially using a remote command execution vulnerability to access applications, operating systems, and firmware. It’s easier for malware to propagate and spread to neighboring machines if software and patches are not being applied and updated on a regular basis.
3.Backlink, iFrame and Drive-By Download:

Some employees like to visit non-work-related websites, increasing the risk of being attacked and infected by backlink, iframe and drive-by download. These are different types of Malware found in many non-work-related websites like online gambling, adult sites, community forums, online streaming, and many others, which are littered with hidden backlinks or malicious codes. Employees are tricked into clicking on malicious content, leading to drive-by download. The files usually masquerade as legitimate word documents or PDF files that, when clicked, will run background process on downloading additional files – which are usually dropper, malware or trojans.
4.Brute Force Attack:

A fourth common malware transmission method is the brute force attack. This method is very commonly used by hackers when organizations have exposed high-risk ports or services, like;
- Desktop protocol (TCP/3389),
- Secure shell (TCP/22) or
- Server message block (TCP/445) services, to the Internet.
Attackers can perform dictionary attacks or crack the administrator password to gain access to the victims’ machine. Although some organizations customize their service port to a random port number, such as TCP/23456, this method is ineffective at defending against attack, as attackers can use various service probing tools against all ports on an organization's IP address range. It is easy to fingerprint the services running behind a specific port, and once these services have been identified, attackers can fine-tune and proceed with different attack strategies accordingly.

How to Defend Against Malware in 2025
- Use Endpoint Detection & Response (EDR): Deploy tools like Sangfor Endpoint Secure for real-time detection, response, and remediation.
- Implement Network Segmentation: Limit lateral movement with microsegmentation, making it harder for malware to spread.
- Apply Regular Patching: Address known vulnerabilities quickly. Automate updates for OS, applications, and firmware.
- Conduct Security Awareness Training: Equip employees to recognize phishing and suspicious behavior. Human error remains the top infection vector.
- Monitor with AI-Powered Threat Detection: Use platforms like Sangfor Cyber Command for continuous anomaly detection and threat correlation.
How Sangfor Helps Secure You Against Malware
Sangfor provides an integrated cybersecurity framework that addresses malware across the entire attack lifecycle:
- Sangfor Network Secure – Detect and block malware at the network perimeter
- Sangfor Endpoint Secure – Comprehensive EDR for ransomware and fileless attack prevention
- Sangfor Cyber Command – Network Detection and Response (NDR) powered by behavioral analytics
- Sangfor IAG – Enforce safe internet access and limit exposure to known malware hosts
Conclusion
As malware threats grow in complexity, so must your defense strategies. Understanding the evolving threat landscape is the first step. With layered protection, real-time monitoring, and user education, your organization can reduce its malware risk significantly.
Don’t wait for an attack to expose your vulnerabilities—explore Sangfor’s solutions today and secure your future.





