1. Overview of LockBit Green Ransomware
| Malware Family | LockBit |
|---|---|
| Released On | February 20, 2023 |
| Threat Type | Ransomware |
| Description | Recently, the LockBit ransomware group released a new strain of ransomware, dubbed LockBit Green. The latest strain is based on the leaked source code of Conti ransomware. It follows LockBit’s trend of creating new variants from other existing ransomware. For example, they previously released LockBit Black, which bears close similarities to the BlackMatter ransomware. |
2. Analysis of LockBit Green Ransomware
2.1 Introduction
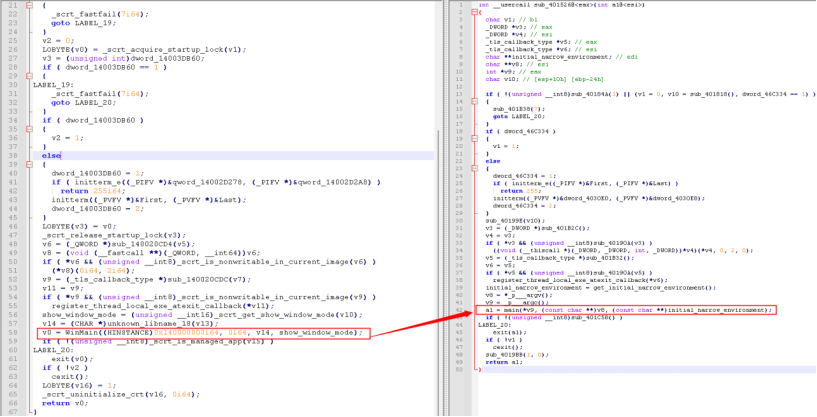
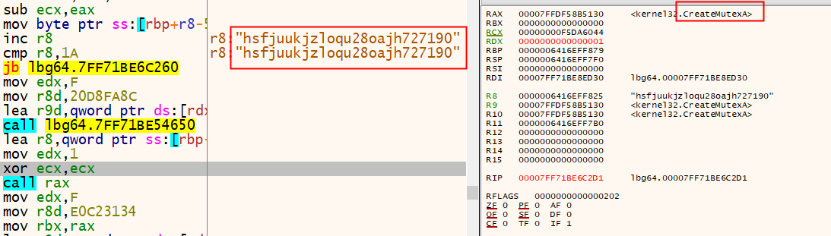
In February 2022, an anonymous person used the Twitter account "@ContiLeaks" to release information about the Conti group, including Jabber chat logs, detailed information about their infrastructure, internal documents, and the source code of the Conti ransomware. In May 2022, the Conti ransomware group decided to reorganize and rebrand. The figure below shows the code of the main function of the Conti ransomware and LockBit Green, and the logic is very similar. In addition, both of them use the same mutex named "hsfjuukjzloqu28oajh727190". LockBit Green uses the new Conti-based encryptor. Since the LockBit family's own encryptor is working normally, the use of the new Conti-based encryptor suggests cooperation between the two ransomware groups. Reusing and adapting the source code of a competitor can help reduce development costs and time.
History of the LockBit Ransomware Family
| September 2019 | LockBit attacks began in 2019. At first, it was dubbed the "ABCD Ransomware" and later renamed to LockBit. |
| June 2021 | LockBit 2.0 appeared in June 2021 and introduced the double extortion technique and automatic encryption of devices across Windows domains. |
| October 2021 | LockBit began infiltrating Linux servers, targeting ESXi servers. The LockBit ransomware group also introduced StealBit, a malware tool used for encryption. |
| June 2022 | LockBit 3.0, also known as LockBit Black, was discovered in June 2022, introducing the first ransomware bug bounty program and leaking new extortion tactics and Zcash cryptocurrency payment options. LockBit 3.0's code is very similar to that of the famed BlackMatter and DarkSide ransomware. |
| September 2022 | In September 2022, an allegedly disgruntled developer leaked the builder for LockBit 3.0's encryptor on Twitter. This is a blow to the ransomware group as the build tools’ data allows anyone to start their own ransomware kit with an encryptor, decryptor, and specialized tools and to launch the decryptor in certain ways. The Bl00dy ransomware gang has developed an encryptor using the leaked build tool and has used it in attacks on Ukrainian entities. |
| January 2023 | The LockBit ransomware gang released LockBit Green, which is based on the leaked source code of Conti ransomware. |
2.2 Analysis
Two samples were found in this ransomware attack. The first sample, LBB.malz, is a 32-bit ransomware known as LockBitBlack in the LockBit family. An analysis of the sample is available at https://mp.weixin.qq.com/s/zT1GbqXFkj0FHiUhNlisZg. The second sample, LBG64.malz, is a 64-bit ransomware called LockBit Green, a new member of LockBit 3.0. The following is an analysis that mainly focuses on LBG64.malz.
| File Name | Hash | Compilation Timestamp |
|---|---|---|
| LBG64.malz | 6147afcb98efab7f0621a910a843878c | 2022/12/26 |
| LBG.malz | 426eea06802387c3a24e2eceb892600e | 2022/7/14 |
After LBG64.malz is executed, the suffix ".fb7c204e" is appended to the encrypted files by default. The name of the ransom note file is "!!!-Restore-My-Files-!!!.txt", as shown in the figure below. Each victim has a unique ID. The Victim can use the Tor browser or a normal browser to get in touch with the attacker through a link. The ransom note does not state the ransom amount but advises the victim not to contact cyber insurance companies and data recovery organizations and explains why.
Ransom Note: !!!-Restore-My-Files-!!!.txt
Encrypted Files
MITRE ATT&CK
| Operation | Tactic | Technique | Sub-Technique |
|---|---|---|---|
| Obtain the types of disk drives using GetLogicalDriveStringsW() and enumerate all disk drives from C:\ to Z:\ | Discovery (TA0007) | File and Discovery (T1083) | N/A |
| Encryption using AES-256 and XChaCha20 | Impact (TA0040) | Data Encrypted for Impact (T1486) | N/A |
| Dynamically parse APIs and strings | Defense Evasion (TA0005) | Deobfuscate/Decode Files or Information (T1140) | N/A |
| Lateral movement over port 445 and IPC$ shares | Lateral Movement (TA0008) | Remote Services (T1021) | SMB/Windows Admin Shares (T1021.002) |
| Call SetFileAttributesW to set read and write permissions | Defense Evasion (TA0005) | File and Directory Permissions Modification (T1222) | Windows File and Directory Permissions Modification (T1222.001) |
| Enumerate all running processes in the system using CreateToolhelp32Snapshot, Process32First, and Process32Next | Discovery (TA0007) | Process Discovery (T1057) | N/A |
| Enumerate the names of network shares, such as IPC$ share | Discovery (TA0007) | Network Share Discovery (T1135) | N/A |
Delete volume shadows using wmic.exe |
Impact (TA0040) | Inhibit System Recovery (T1490) | N/A |
| Delete volume shadow copies using wmic.exe | Execution (TA0002) | Windows Management Instrumentation (T1047) | N/A |
Analysis of Techniques
Startup Parameters
The sample can be started without parameters or with optional parameters (as shown below). GetCommandLineW and CommandLineToArgvW functions are used to obtain the command line string used for running the malware. The output of these two functions will be used to check if extra parameters were used when executing the malware.
-p Single-thread encryption for a given directory
-m Multithreading encryption for multiple files
Lateral Movement
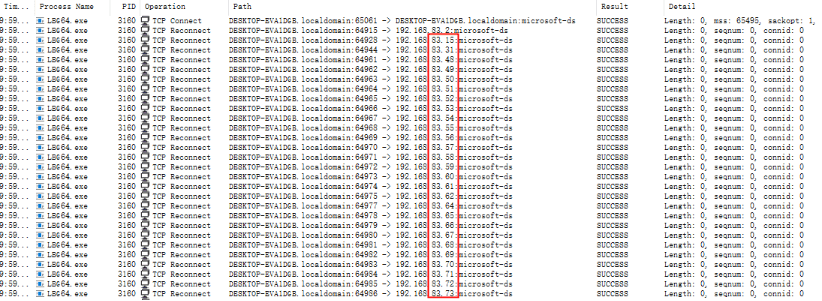
The sample scans the same network subnet and tries to connect to devices on the same network segment using SMB (port 445) to infect them.
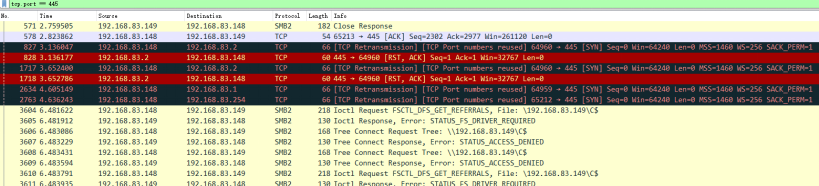
In the figure below, Process Monitor captured the ransomware attempting to connect to IP addresses from 192.168.83.1 to 192.168.83.254 over TCP.
Defense Evasion
1. Dynamic Decryption of API
The ransomware obfuscates all its API calls and library names and resolves them dynamically at runtime. This obfuscation technique makes sure that the ransomware can still access all its APIs without writing them directly to the import table, which completely hides them from reverse engineers.
It dynamically resolves module names and loads them for execution. The ransomware resolves module names, including netapi32.dll, apphelp.dll, kernelbase.dll, msvcp_win.dll, win32u.dll, gdi32full.dll, ucrtbase.dll, msvcrt.dll, rpcrt4.dll, kernel32.dll, user32. dll, imm32.dll, ws2_32.dll, gdi32.dll, and ntdll.dll.
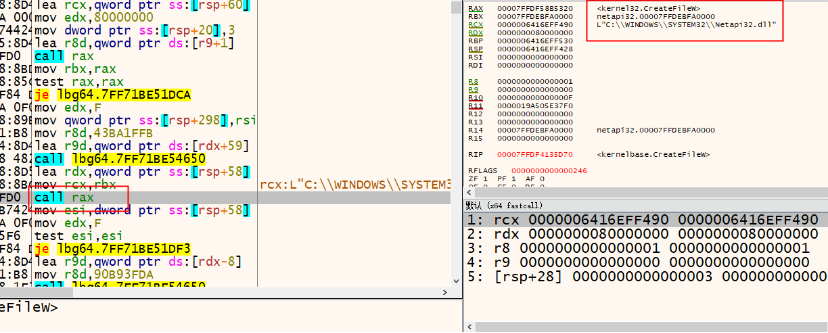
The ransomware creates a mutex named "hsfjuukjzloqu28oajh727190" to ensure that only one instance of malware is running on the victim's machine. Running multiple instances can hamper and slow down the encryption process. It should be noted that some samples of Putin and Conti ransomware also create the "hsfjuukjzloqu28oajh727190" mutex.
Discovery
1. File and Directory Discovery
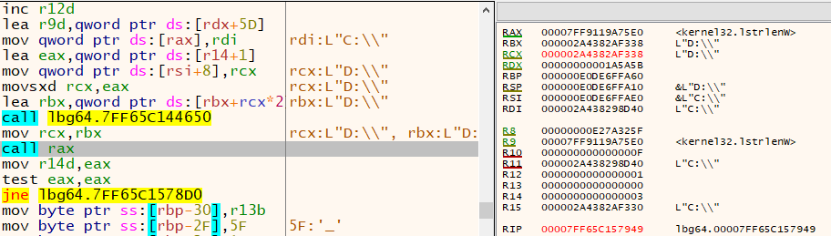
Calls GetLogicalDriveStringsW() to obtain drive information.
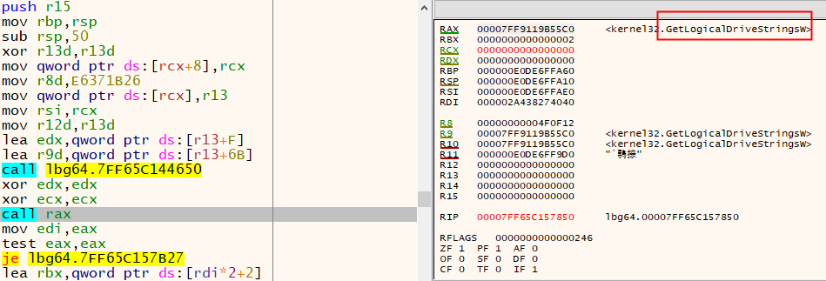
Enumerates all disk drives from C:\ to Z:\.
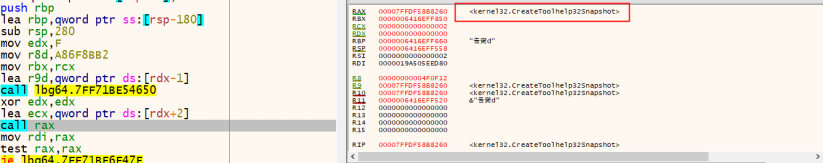
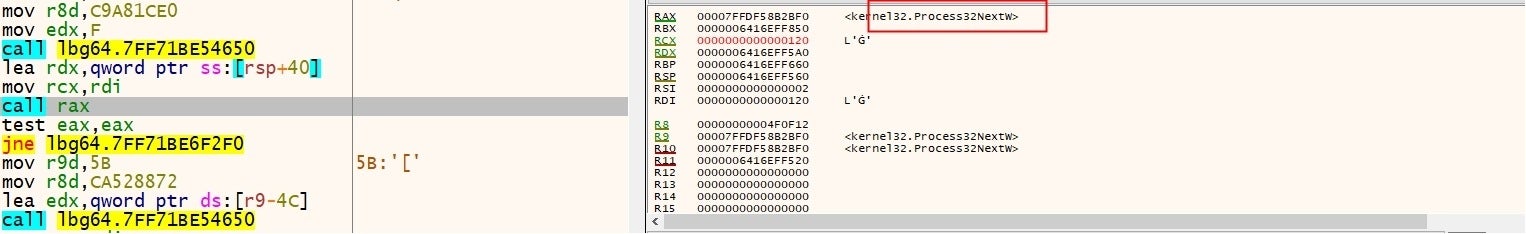
2. Process Enumeration
Calls CreateToolhelp32Snapshot to take a snapshot of all running processes.
Calls Process32FirstW to find the first directory or the first file under a given directory and get the handle.
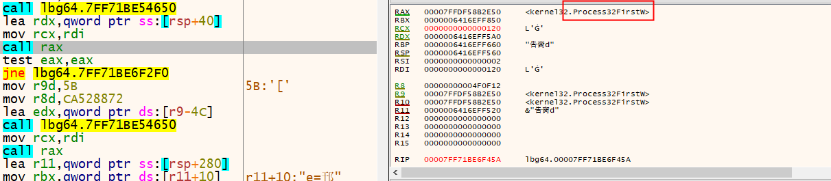
Calls Process32NextW to search for other files and directories according to the handle.
Impact
1. Inhibit System Recovery
Deletes shadow volumes from the infected system to prevent recovery.
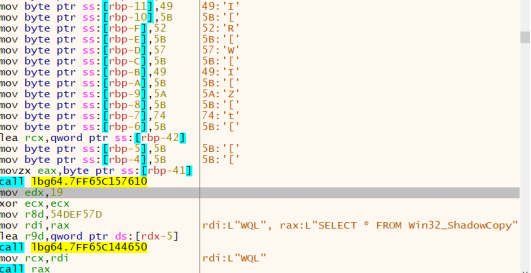
%windir%\System32\wbem\WMIC.exe shadowcopy where "ID='{CEED47F6-B476-421D-8D81-35633F2315E2}'" delete
2. Data Encrypted for Impact
Skips the following files and files with the following extensions during encryption.
.exe
.dll
.lnk
.sys
.msi
.bat
CONTI_LOG.txt
!!!-Restore-My-Files-!!!.txt
Skips the following directories during the encryption.
Temp
$Recycle Bin
System Volume Information
winnt
thumb
Windows Boot
perflogs
Trend Micro
After encryption is complete, the ransomware appends the ".fb7c204e" extension to the end of each encrypted file.
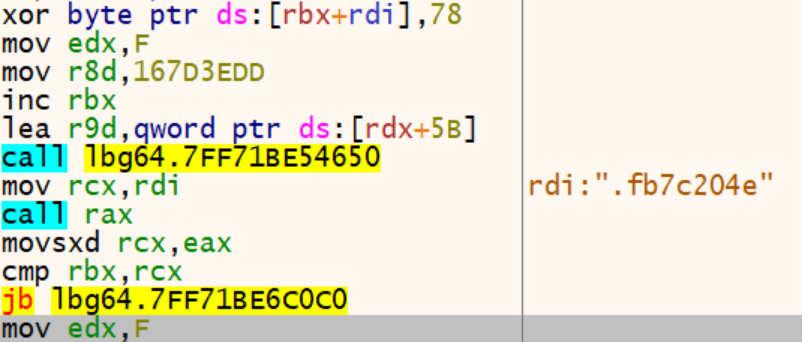
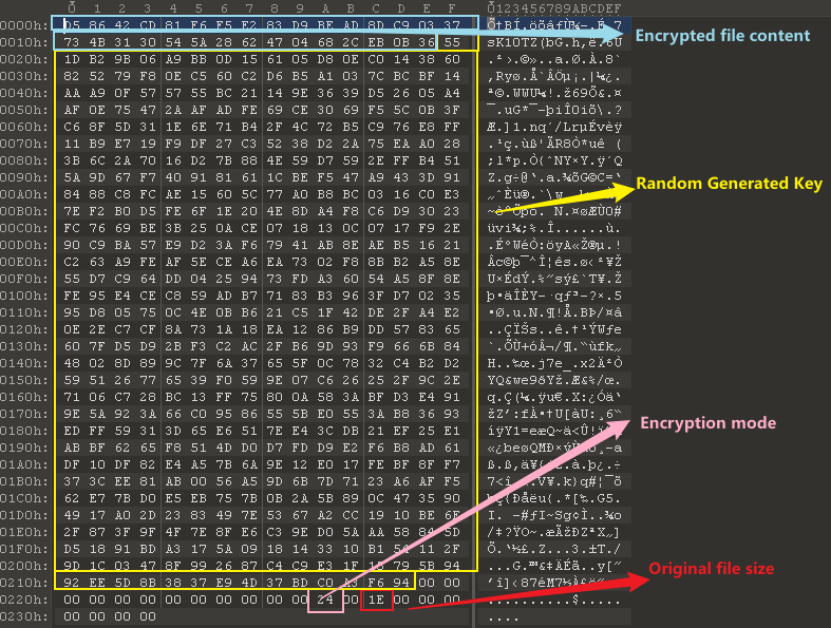
This sample encrypts files using a combination of AES-256 and XChaCha20 algorithms and in three different modes (i.e., 0x24, 0x25, and 0x26) according to file size and type.
0x24: Full encryption, as shown in the figure below.
0x25: Block encryption, which means the ransomware divides a file into several blocks, and only encrypts the data of some blocks.
0x26: Only the first 1 MB is encrypted, and then the encrypted content is written back into the file, followed by the unencrypted file content, the encryption key, and the original file size.
2.3 Indicators of Compromise (IOCs)
Tor browser links:
http://lockbitapt2d73krlbewgv27tquljgxr33xbwwsp6rkyieto7u4ncead.onion
http://lockbitapt2yfbt7lchxejug47kmqvqqxvvjpqkmevv4l3azl3gy6pyd.onion
http://lockbitapt34kvrip6xojylohhxrwsvpzdffgs5z4pbbsywnzsbdguqd.onion
http://lockbitapt5x4zkjbcqmz6frdhecqqgadevyiwqxukksspnlidyvd7qd.onion
http://lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd.onion
http://lockbitapt72iw55njgnqpymggskg5yp75ry7rirtdg4m7i42artsbqd.onion
http://lockbitaptawjl6udhpd323uehekiyatj6ftcxmkwe5sezs4fqgpjpid.onion
http://lockbitaptbdiajqtplcrigzgdjprwugkkut63nbvy2d5r4w2agyekqd.onion
http://lockbitaptc2iq4atewz2ise62q63wfktyrl4qtwuk5qax262kgtzjqd.onion
Links for normal browsers:
http://lockbitapt2d73krlbewgv27tquljgxr33xbwwsp6rkyieto7u4ncead.onion.ly
http://lockbitapt2yfbt7lchxejug47kmqvqqxvvjpqkmevv4l3azl3gy6pyd.onion.ly
http://lockbitapt34kvrip6xojylohhxrwsvpzdffgs5z4pbbsywnzsbdguqd.onion.ly
http://lockbitapt5x4zkjbcqmz6frdhecqqgadevyiwqxukksspnlidyvd7qd.onion.ly
http://lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd.onion.ly
http://lockbitapt72iw55njgnqpymggskg5yp75ry7rirtdg4m7i42artsbqd.onion.ly
http://lockbitaptawjl6udhpd323uehekiyatj6ftcxmkwe5sezs4fqgpjpid.onion.ly
http://lockbitaptbdiajqtplcrigzgdjprwugkkut63nbvy2d5r4w2agyekqd.onion.ly
http://lockbitaptc2iq4atewz2ise62q63wfktyrl4qtwuk5qax262kgtzjqd.onion.ly
Unique link for the victim
http://lockbitsupuhswh4izvoucoxsbnotkmgq6durg7kficg6u33zfvq3oyd.onion
Links for communication
http://lockbitsupa7e3b4pkn4mgkgojrl5iqgx24clbzc4xm7i6jeetsia3qd.onion
http://lockbitsupdwon76nzykzblcplixwts4n4zoecugz2bxabtapqvmzqqd.onion
http://lockbitsupn2h6be2cnqpvncyhj4rgmnwn44633hnzzmtxdvjoqlp7yd.onion
http://lockbitsupo7vv5vcl3jxpsdviopwvasljqcstym6efhh6oze7c6xjad.onion
http://lockbitsupq3g62dni2f36snrdb4n5qzqvovbtkt5xffw3draxk6gwqd.onion
http://lockbitsupqfyacidr6upt6nhhyipujvaablubuevxj6xy3frthvr3yd.onion
http://lockbitsupt7nr3fa6e7xyb73lk6bw6rcneqhoyblniiabj4uwvzapqd.onion
http://lockbitsupuhswh4izvoucoxsbnotkmgq6durg7kficg6u33zfvq3oyd.onion
http://lockbitsupxcjntihbmat4rrh7ktowips2qzywh6zer5r3xafhviyhqd.onion
MD5
426eea06802387c3a24e2eceb892600e
6147afcb98efab7f0621a910a843878c
730f72a73ff216d15473d2789818f00c
aacef4e2151c264dc30963823bd3bb17
37355f4fd63e7abd89bdc841ed98229f
ea34ac6bf9e8a70bec84e37afeea458a
3. Solutions
3.1 Ransomware Prevention Strategies
- Do not make services available on an external network. In cases where this is unavoidable, then use strong passwords.
- Do not open suspicious or unexpected emails, especially the links and attachments in them. Use antivirus software to scan an unknown file before opening it (if you have to do so).
- Install antivirus software, perform regular system scans, remove detected threats, and regularly install updates and patches.
- Download products via official and verified channels, and activate and update products using tools/functions provided by the official developer. Illegal activation tools and third-party downloaders are not recommended as they are often used to distribute malicious content.
- Implement a dual backup strategy for important data or back it up in the cloud.