1 Analysis of Mallox Ransomware
1.1 Introduction
Sangfor FarSight Labs detected a new variant of the Mallox ransomware family during recent operations. This variant uses a complex control flow obfuscation technique to modify its binary signatures, allowing it to avoid static analysis by security software. Mallox can be detected and blocked using Sangfor Endpoint Secure.
In this incident, the attacker gained access to the victim’s system through a brute-force attack on their SQL Server. They then conducted initial reconnaissance to collect information about the environment. Subsequently, they installed the remote desktop software AnyDesk to take control of the system and execute the ransomware. The attacker engaged in double extortion ransomware by exfiltrating system files before encryption. The encrypted files were appended with the ".Mallox" extension, and the attacker released a ransom note demanding payment for the decryption and deletion of the stolen data.
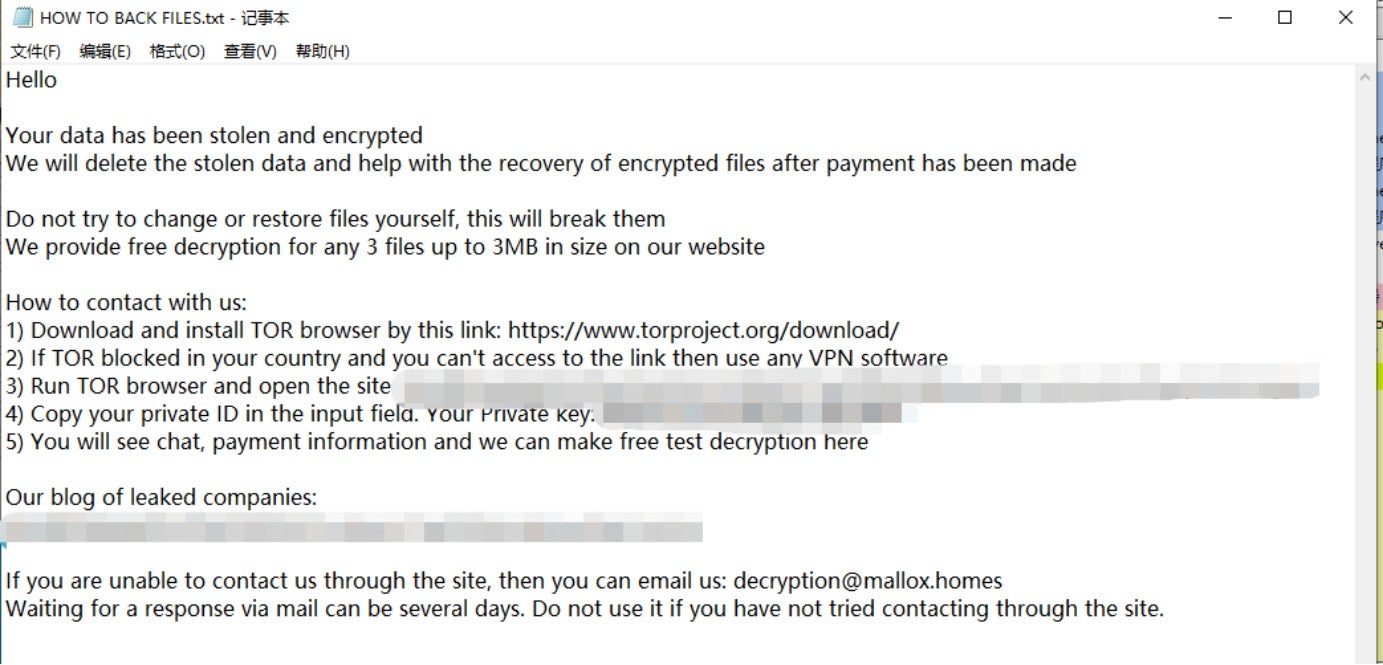
According to Mallox’s data leaks site, the ransomware group became active again in March of this year.
1.2 Sample Analysis
1.2.1 Static Analysis Evasion
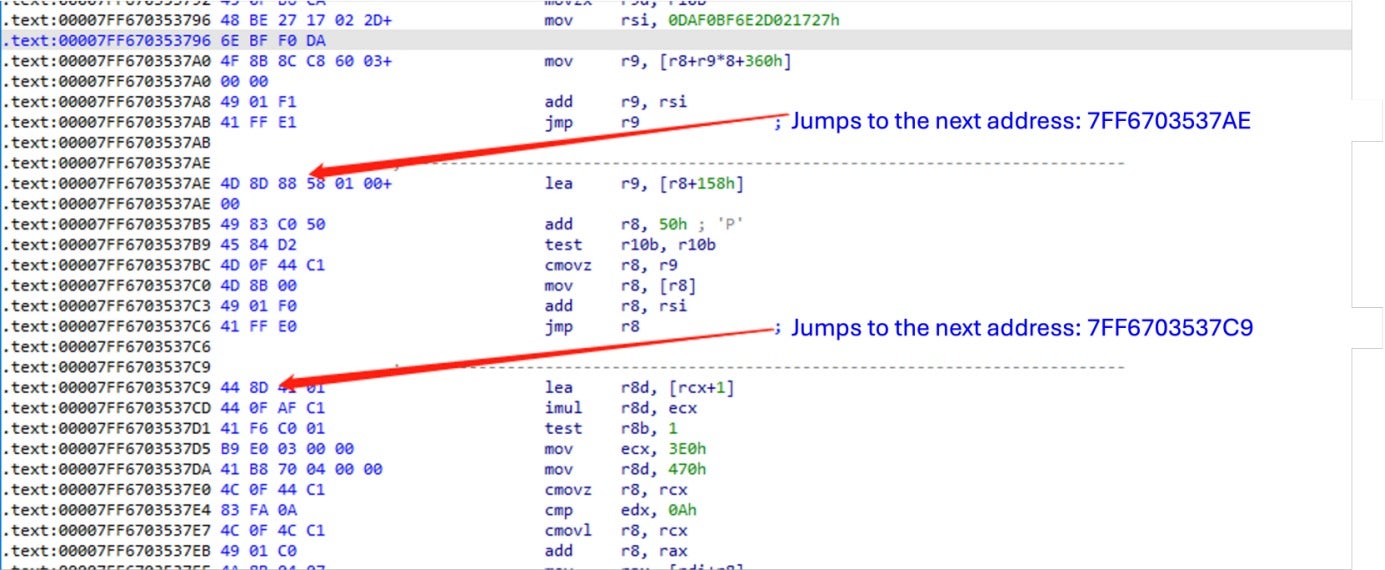
To evade static analysis by security software, the ransomware sample uses the control flow obfuscation technique. Specifically, it inserts numerous meaningless jump code blocks between instruction segments. These code blocks jump to pre-calculated addresses using JMP instructions, thereby increasing the difficulty of analyzing the code. During dynamic debugging, these obfuscated code segments can be skipped by writing runtime scripts provided by the debugger.
1.2.2 Preparation for File Encryption
- Creates an event object named 89A72EF01 to prevent files from being encrypted multiple times.
- Loads powrprof.dll and calls the PowerSetActiveScheme function to set the power plan to High Performance, with a GUID of 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c.
- Enables the SeTakeOwnershipPrivilege and SeDebugPrivilege privileges of the process by calling the OpenProcessToken and AdjustTokenPrivileges functions.
- Creates a window and calls the ShutdownBlockReasonCreate function to display the following message when users try to shut down their computers: Do NOT shut down OR reboot your PC: this might damage your files permanently!
- Removes the Shut down, Restart, and Sign out options from the Start menu by modifying the following registry entries:
SOFTWARE\Microsoft\PolicyManager\default\Start\HideShutDown SOFTWARE\Microsoft\PolicyManager\default\Start\HideRestart SOFTWARE\Microsoft\PolicyManager\default\Start\HideSignOut - Disables User Account Control (UAC) by modifying the following registry entry: SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- Calls CMD to disable recovery mode with the following command: bcdedit /set {current} bootstatuspolicy ignoreallfailures, bcdedit /set {current} recoveryenabled no.
- Uses vssadmin to delete volume shadow copies with the following command: C:\Windows\sysnative\vssadmin.exe delete shadows /all /quiet.
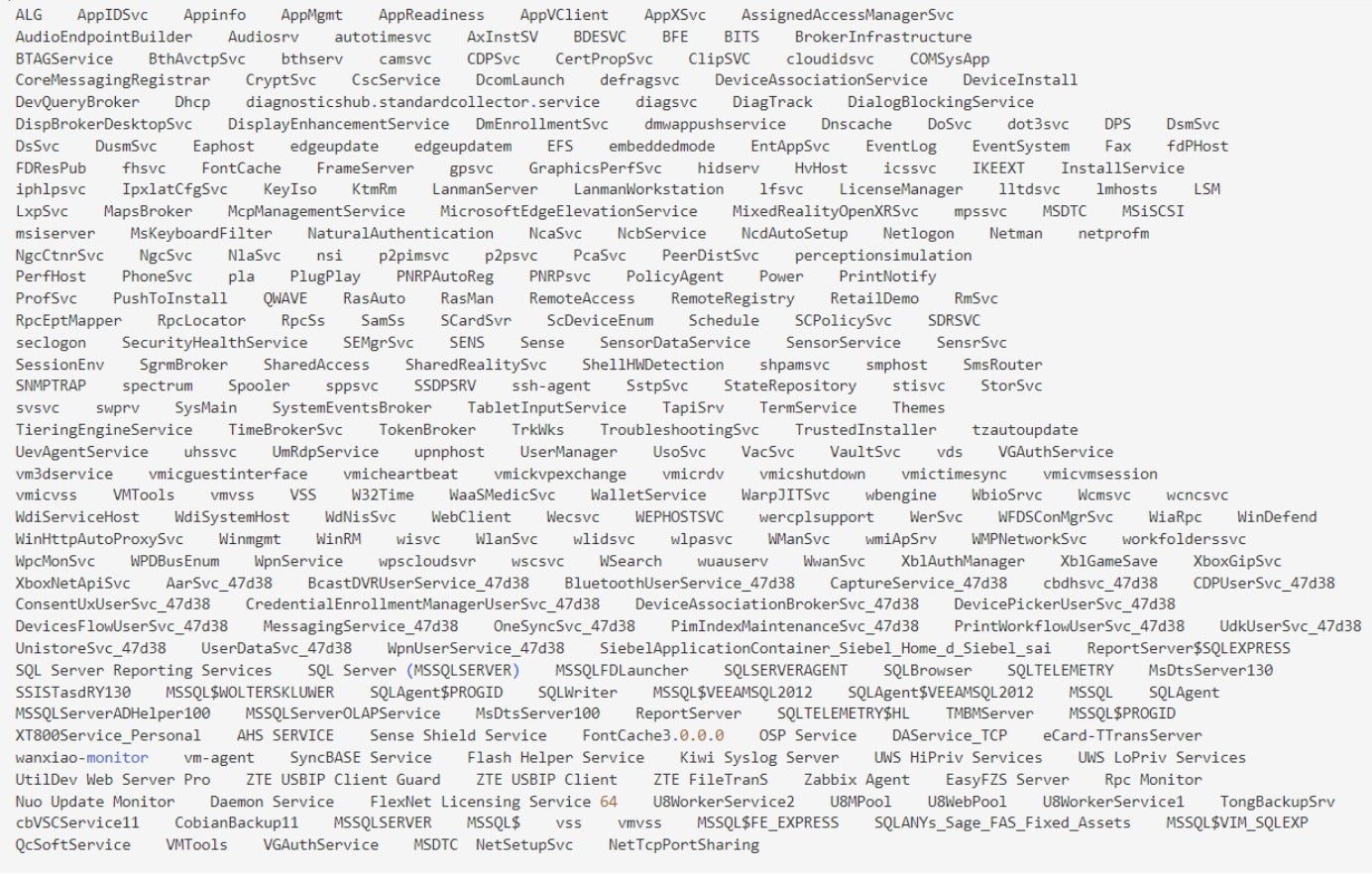
- Terminates services that may affect the encryption process.
1.2.3 Encryption Operation
After completing the preceding preparations, the sample launches the encryption module. It obtains information about all the drives in the system using the GetLogicalDrives function, enumerates all files using the FindFirstFile function, and encrypts files using Microsoft’s Crypt series of functions.
The files in the following directories are not encrypted.

The following files are not encrypted.
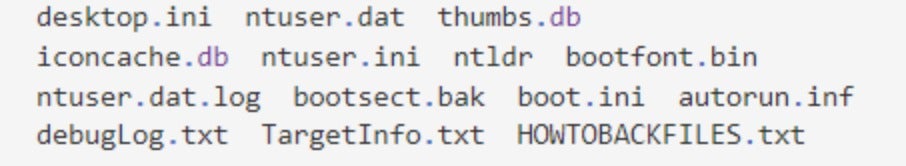
The files with the following extensions are not encrypted.
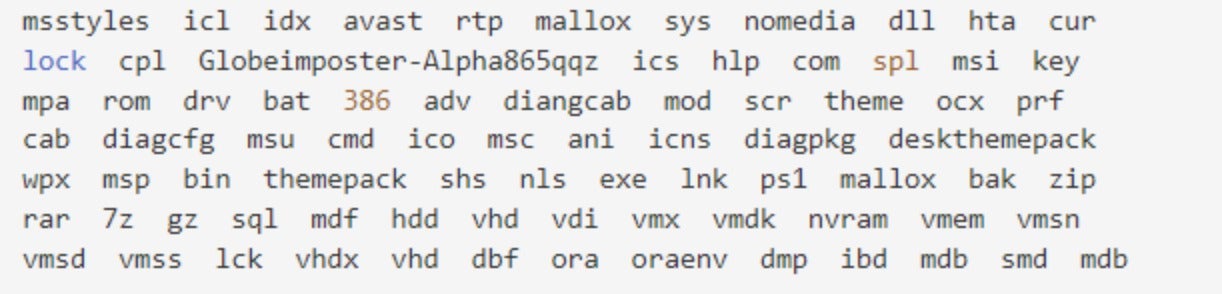
1.3 Indicators of Compromise (IOCs)
URL:
http://91.215.85.142/QWEwqdsvsf/ap.php
HASH:
1C459E171A2FB806F4D284B954D221D9
2 Solutions
2.1 Ransomware Prevention Strategies
- Do not make services available on an external network. Use strong passwords in cases where this is unavoidable.
- Do not open suspicious or unexpected emails, especially the links and attachments in them. Use antivirus software to scan an unknown file before opening it (if you have to do so).
- Install antivirus software, perform regular system scans, remove detected threats, and regularly install updates and patches.
- Download products via official and verified channels and activate and update products using tools or functions provided by the official developer. Illegal activation tools and third-party downloaders are not recommended, as they are often used to distribute malicious content.
- Implement a dual backup strategy for important data or back it up in the cloud.
2.2 Sangfor Solutions
2.2.1 Sangfor Endpoint Secure
Sangfor Endpoint Secure detects and blocks Mallox virus files using dynamic and static AI-based detection engines. The static AI engine blocks unknown ransomware files when they land on endpoints, while the dynamic AI engine defends against ransomware payload execution. This combination achieves a 100% detection accuracy of known ransomware and 99.83% detection accuracy of unknown ransomware in as little as 3 seconds. Protection is provided without requiring the latest updates. However, it is recommended to update to the latest version for enhanced protection.





