In 2007, Google came out with the Google Street View platform that allowed users to access panoramic and interactive images of streets for GPS navigation. To capture a 360° map of the world, Google would use equipment to track and locate Local-Area Networks (LANs), wireless hotspots, and home Wi-Fi networks. Unfortunately, this could – and did – end up doing more than that in 2010 when Google admitted to accidentally gathering extracts of personal web activity from domestic Wi-Fi networks through the Street View cars. While the Google Street View program itself was not maliciously driven and the company chalked it up to a ‘mistake’, it presents as a good example of collecting data using available wireless networks. Smartphones, laptops, and other devices will often pick up on available networks and notify you of their existence when you’re nearby. This is essentially the main goal of wardriving as well. In this article, we demonstrate how a wardrive can unethically collect data and how this can be prevented. First, let’s get a better understanding of the wardriving definition.
What Is Wardriving?
Wardriving – also known as access point mapping - is the tracking and accessing of wireless local area networks within a given area. Typically, a wardriver will use a car to drive around a location and then use their laptop or smartphone to run software allowing them to find and map wireless access points or networks. To properly define wardriving, we need to understand how WLANs can be used to collect information and have a wide range that makes them more accessible to devices outside the network. This means that outsiders can connect to the network freely and possibly access company records, private information, and more.
While some ethical hackers or enthusiasts might consider it a hobby of sorts, it can also be used to carry out cyber-attacks as well. Threat actors can use it to access devices on the network to install malware, steal files, and copy private information. Using wardriving, cybercriminals can map the location of vulnerable wireless networks with weak passwords or no encryption protocols to exploit them.
The premise behind it comes from the 1983 film WarGames where the main character uses a computer to dial multiple phone numbers to find a working modem – this was called war dialing and is where wardriving comes from as well. The term itself was coined by Peter Shipley, a computer security consultant who developed scripts that were able to read the coordinate information on GPS devices - allowing him to plot Wi-Fi access points on a map.

How Does Wardriving Work?
Wardriving uses a combination of hardware and software tools to identify Wi-Fi signals in a location. Wardriving is only possible because Wi-Fi networks will automatically try to connect to nearby devices to ensure seamless connectivity.
Usually, a wardriver will only need:
- A smartphone or laptop
- An antenna or wireless network card
- Wardriving software
- GPS capabilities
The GPS device and antenna connect with the monitoring software to pinpoint access points and easily decrypt routers. Once hackers gain access to a vulnerable network, they can steal data to upload it onto specific wardriving websites or apps that allow users to build a digital map of networks within neighborhoods. Common websites used by wardrivers to map network neighborhoods include:
While it typically involves the use of a vehicle when driving through locations, a wardriver can also walk, cycle, use drones, and more. The main idea is to be able to physically cover a large distance in search of network access. While it may seem intrusive, it can be used as part of an ethical hacker’s activities to find vulnerabilities in a network.
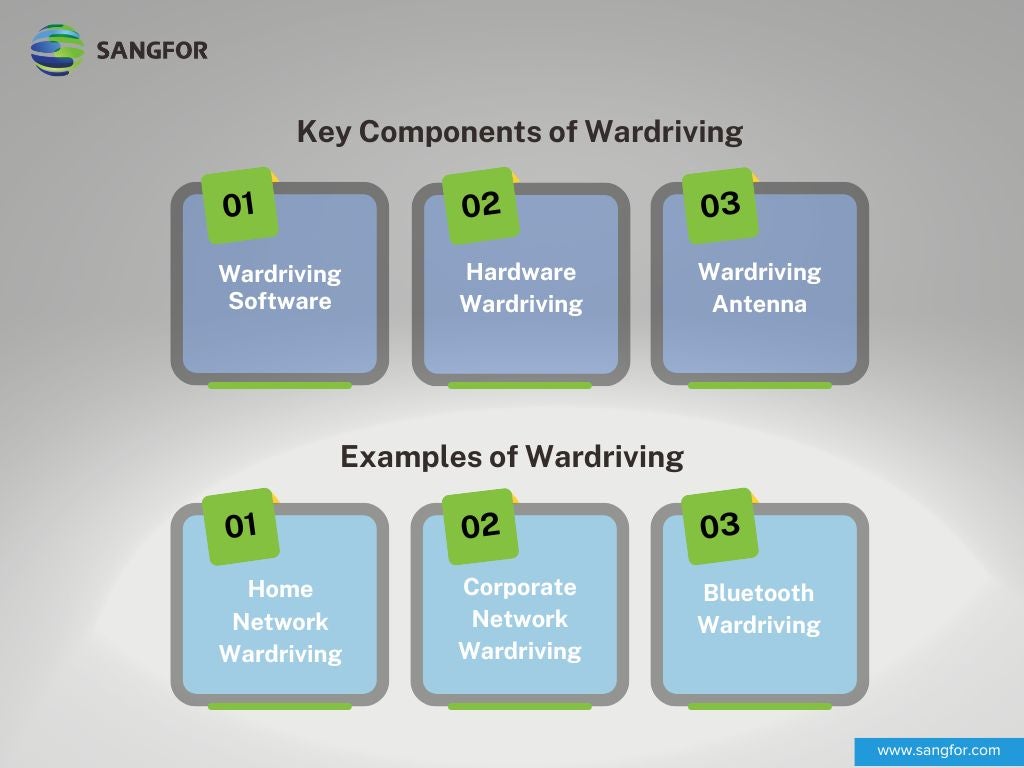
Key Components of Wardriving
Wardriving is a mostly simple way to map access points. Generally, the main components are the same:
- Wardriving Software: These are types of software that allow a wardriver to decrypt routers, uncover passwords, and effectively map networks. Wardriving software and applications are usually downloaded onto the smartphone or laptop used by the wardriver and can be used to crack passwords of WEP and WPA encrypted networks. These include packet sniffers, signal strength testers, and traffic analyzers. Examples of wardriving software are KisMAC, Aircrack, Cain & Able, CoWPAtty, iStumbler, InSSIDer, or WiFiphisher.
- Hardware Wardriving: Wardriving hardware is just as important as the software. Hackers often use generic hardware like a Raspberry Pi computer to connect to a GPS device when looking for access points. Other examples of wardriving hardware include smartphones, laptops, or tablets.
- Wardriving Antenna: Antennas are a great way for wardrivers to identify networks more easily and with a wider range. Several types of antennas can be used depending on the range you need to cover and the frequency you want to pick up on. Wi-Fi wardriving usually operates on a 2.4 GHz radio frequency – making Wi-Fi networks detectable from miles away with an antenna.
These components all work together to gather information about vulnerable access points in your area.
Examples of Wardriving
Wardriving comes in many different forms and has evolved with the emergence of new technologies and better cybersecurity. Let’s take a look at some of the major examples of wardriving seen today:
- Home Network Wardriving: This is the type of wardriving seen in residential areas where the wardriver will move around homes to find vulnerable home W-Fi networks.
- Corporate Network Wardriving: In this form, hackers will map the network access points of businesses and organizations. This is also targeted at guest Wi-Fi networks that are typically left open.
- Bluetooth Wardriving: Wardriving can also be used to detect Bluetooth signals to capture data being broadcast by vulnerable devices. Bluetooth is often automated and also operates on a 2.4 GHz radio frequency which makes Bluetooth wardriving much easier.
While it can be harmless, many hackers might use it with bad intentions. Access points can hold any number of private data that can be used against users by threat actors.
What Is a Wardriving Attack?
The nature of wardriving can seem scary to many people, however, the process in itself is quite harmless. Unauthorized access to a network puts private data at risk and leaves your network and all devices connected to it open to malware. Users need to ensure proper ransomware protection to keep their confidential data from being used against them later on in a cyber-attack. A wardriver attack can lead to massive financial loss and data being leaked onto third-party websites – which all leads to asking if wardriving is even legal at all.
Is Wardriving Illegal?
The simple answer is no. While the gathering of data from wireless networks can be dodgy to most people, it is still a legally sound practice. However, hackers who use this technique with criminal intentions can transform this process into a cyber-attack – which is illegal. Mostly, it tends to operate within a gray area where exploitation of the data is illegal but collecting it is not. Ethical hackers can use it as a Managed Detection and Response solution when implemented correctly to avoid cyber-attacks.
Wardriving can be uncertain, yet it poses no immediate cyber security threat as it is. This all begs the question of ‘what is wardriving in cyber security?’ When the process itself can become a unique danger, the cyber security risks are too high to ignore. This is why we need to know how to prevent it from happening in the first place and how to protect our networks.
How To Prevent Wardriving
Wardriving has the potential to cause data breaches and leaves your network open to several forms of cyber-attacks. To ensure that your network stays safe, you can follow these simple rules to prevent any risks associated with it:
- Installing a proper firewall: Using a firewall ensures that networks are protected at all times by monitoring access requests and blocking suspicious behavior. Firewalls should be constantly updated and switched on to keep your router from being targeted by a wardriving attack. Sangfor’s enterprise firewall offers superior network protection with advanced security layers.
- Switching off unused Wi-Fi networks: By turning off Wi-Fi routers when nobody is using them, you prevent your network from being accessed by hackers.
- Changing default router passwords: Most Wi-Fi router manufacturers will assign a default username and password to help configure routers faster. These passwords are often known by hackers which makes it easier to access your network. Change the password and name of your router to keep access secure.
- Using stronger router passwords: Wi-Fi passwords need to be long and complex so they are more difficult to guess or bypass.
- Using encryption: Routers should be equipped with advanced security protocols and encryption like Wi-Fi Protected Access 2 (WPA2) or WPA3 to ensure that hackers cannot infiltrate them.
- Separating guest and private networks: Wi-Fi access for guests and private networks should be kept separate to protect sensitive information.
- Using multi-factor authentication: Multi-factor authentication (MFA) provides two more layers of security and requires authentication from various devices to give access.
- Using a VPN: Public Wi-Fi networks can be vulnerable and risky to connect to. Using a VPN will ensure that data on your device is secure and cannot be collected or monitored.
- Disabling SSID broadcast: A Service Set Identifier (SSID) is automatically broadcast by your network to allow devices to find it and connect to it. Disabling this feature ensures that your network cannot be identified and hacked by outsiders.
- Using Endpoint Security: Proper end-to-end security will ensure that your network is secure from outsider threats. Sangfor’s EDR security platform protects key elements of the network from suspicious behavior and intrusions.
As cyber-attacks grow and advance, networks become increasingly targeted. Wardriving is a way of mapping access points to help in finding open access networks for free Internet connectivity and mapping networks in your area. While it can be harmless in the right hands, it can be dangerous in the wrong ones.
Wardriving attacks can exploit vulnerable networks and collect private data for personal use. Organizations and individuals alike should ensure that their networks are safe and protected. Sangfor provides cloud computing and cybersecurity solutions that will defend your network while ensuring that you have the best infrastructure. Contact Sangfor Technologies today and secure your digital environment.
Wardriving Frequently Asked Questions
Wardriving is the process of physically moving through areas and searching for open or vulnerable Wi-Fi wireless networks using a laptop or smartphone. Typically, wardriving is used as a form of hacking to gain unauthorized access to networks and collect private data.
- Home network wardriving
- Corporate network wardriving
- Bluetooth wardriving
Wardriving can help find Wi-Fi networks that are unsecured for free Internet access. It can also help you find Wi-Fi networks that are not being used if you are looking for a place to set up your own Wi-Fi network.
Wardriving is used to collect information about open Wi-Fi networks in a given area to build a larger map of vulnerable networks. This is done using a smartphone or laptop, an antenna, wardriving software, and GPS capabilities.
Some of the examples of wardriving software are KisMAC, Aircrack, Cain & Able, CoWPAtty, iStumbler, InSSIDer, or WiFiphisher.
Wardriving is legal, however exploiting network access to carry out cyber-attacks, steal data, or expose private information is illegal.
Wardriving can be prevented by:
- Installing a proper firewall
- Switching off unused Wi-Fi networks
- Changing default router passwords
- Using stronger router passwords
- Using encryption
- Separating guest and private networks
- Using multi-factor authentication
- Using a VPN
- Disabling SSID broadcast
- Using Endpoint Security





