What is Endpoint Security?
An endpoint is any device that has access to your organization's network. This could be any computer, phone, printer, router, and other devices that your business or employees use for work purposes. Endpoint security refers to the protection of endpoints against unauthorized access, misuse, modification, or destruction at the hands of hackers using malware.
What Are Endpoints in Endpoint Security?
An endpoint is any device that connects to an organization’s network from outside its firewall. Examples include tablets, mobile devices, printers, desktops laptops, IoT devices, smartwatches and servers. An organization can quickly have a large number of endpoints as there is a growing popularity for individuals to bring their own devices into work.

The Importance of Endpoint Security
In today’s digital world, cyber security is a concern for individuals, SMEs, and MNCs alike. The rapid advancement of technology has brought numerous benefits, but it has also made endpoints more vulnerable. Employees now have the ability to access business data from their own devices and non-business networks, increasing the risk of cybercrime incidents. The COVID-19 pandemic has further accelerated this trend, with the use of weaponized AI.
- The shift towards remote work and increased reliance on technology in business processes has made businesses worldwide more susceptible to cyber-attacks. Each endpoint connected to the corporate network can serve as an entry point for cyber attackers. To prevent successful cyber security attacks and mitigate potential financial losses, it is crucial to secure all endpoints that have access to crucial business information. By doing so, businesses can protect themselves from significant financial harm.
- More businesses transit into cloud and IoT services - something that has the potential to streamline and make business processes far more efficient but also more susceptible to cybercrime.
- The penalty of cybercrime extends beyond just monetary cost, however. High opportunity costs, business downtime, damaged reputations, and much more as a result of these attacks are enough to make seemingly stable and successful businesses file for bankruptcy. Despite these alarming facts, up to half of businesses reported they do not have any incident response system in place. Ensuring your business is well protected and secured from cybercrime is necessary for any business striving for growth and success in a post-pandemic world.
- Endpoint security plays a crucial role in helping organizations adhere to regulations. Different industries have specific compliance requirements for safeguarding data, and endpoint security assists in meeting these obligations by implementing necessary security measures and controls.
How Does Endpoint Protection Work?
Organizations can install endpoint protection on devices to prevent threat actors from using malware or other tools to infiltrate their systems. Endpoint security works by examining files, processes, and systems for suspicious activity. It provides administrators with a centralized console to control security for each device remotely. This means that client software can push updates, authenticate login attempts, or administer any system changes from a single location without needing access to the physical device. For example, administrators can always ensure that devices connected to the enterprise networks are up-to-date on software and patches.
If malicious threats are detected, endpoint protection can also block the use of applications that are unsafe or unauthorized. It can also encrypt information to prevent data loss. Furthermore, endpoint security can also be used with other detection and monitoring tools to prevent breaches before they take place and strengthen your cyber security strategy.
Organizations can choose from a variety of endpoint protection solutions, including on-premise security posture, hybrid approaches, and cloud-native approaches. On-premise security posture involves deploying endpoint protection software on local servers, which can provide greater control over security policies and data privacy. Hybrid approaches combine on-premise and cloud-based security solutions to provide a more comprehensive security strategy. Cloud-native approaches, on the other hand, are designed to be deployed and managed entirely in the cloud, providing greater scalability and flexibility with automation and optimization tools to maximize available resources and reduce costs.
Why Is Cloud-Based Architecture Important for Endpoint Security?
Cloud-based architecture is increasingly vital for ensuring robust endpoint security. Here are several reasons why:
- Centralized Management: Cloud-based endpoint security leverages a cloud-based platform, enabling centralized management, analysis, and enforcement. This simplifies security operations across all devices and networks, enhancing overall management efficiency.
- Enhanced Security: Cloud-based endpoint security leverages cutting-edge algorithms, artificial intelligence, and machine learning to comprehensively analyze data from devices and networks. This intelligent approach enables proactive threat detection and prevention, safeguarding against sophisticated cyber-attacks.
- Anywhere Accessibility: Cloud-based endpoint security offers unparalleled accessibility, enabling secure operations from anywhere in the world. This empowers remote workers to seamlessly connect and collaborate while maintaining robust security protocols, regardless of their physical location.
- Resource Optimization: Cloud-based endpoint security optimizes resource allocation and utilization, allowing organizations to maximize their security investments. By eliminating the need for on-premises hardware and software, it liberates valuable resources that can be redirected toward strategic initiatives.
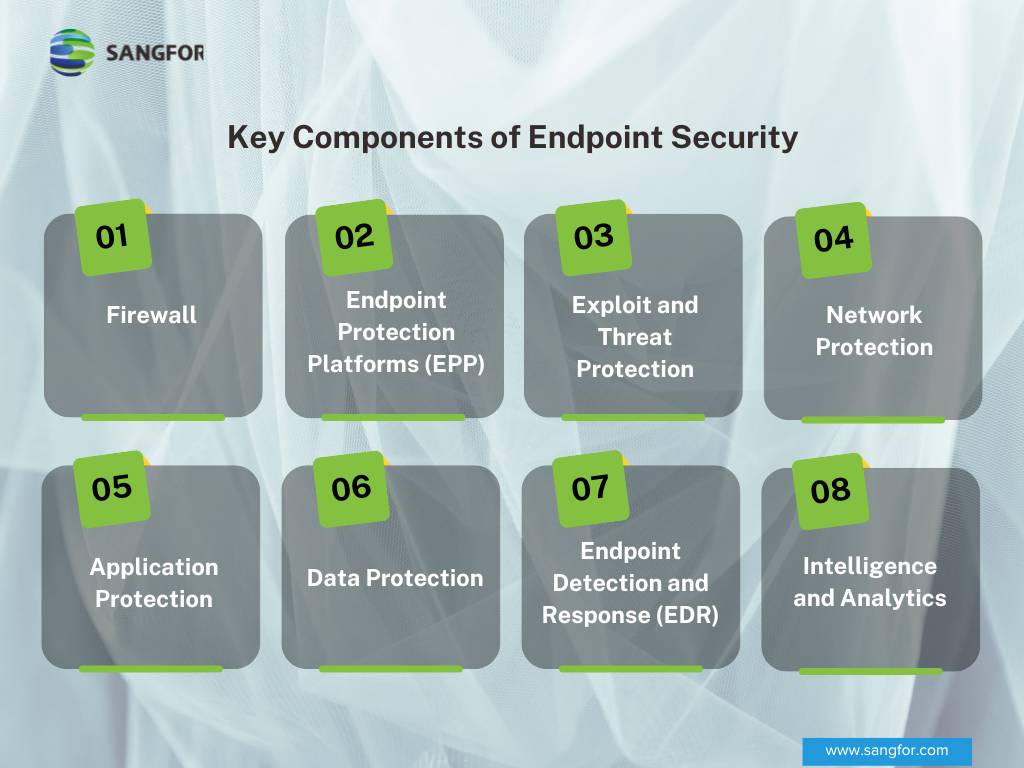
What Are the Key Components of Endpoint Security Software?
Whether on-premises or in the cloud, endpoint security software encompasses the protection and continuous monitoring of endpoints, which include various devices that connect to networks. It is important to explore the key components of endpoint security software to further utilize it:
- Firewall: A pivotal network security solution that diligently examines incoming and outgoing traffic, making informed decisions to either permit or deny access.
- Endpoint Protection Platforms (EPP): A comprehensive platform that covers a wide array of features aimed at mitigating risks to devices and their sensitive data. These include robust protections against malware and ransomware, application blocklisting, efficient patch management, intelligent analytics, anomaly detection, web and email safeguards, as well as data encryption.
- Exploit and Threat Protection: An effective endpoint protection platform extends its protective shield beyond the device itself, actively working to mitigate threats before they even reach the device.
- Network Protection: Endpoint security goes beyond device-level defence and encompasses shielding network assets from potential threats introduced through endpoints.
- Application Protection: Endpoint security software ensures security through application control, preventing users from downloading or accessing unsafe or unauthorized applications as per organizational policies.
- Data Protection: The software employs encryption techniques to safeguard against data loss, ensuring the confidentiality and integrity of sensitive information.
- Endpoint Detection and Response (EDR): An essential component of endpoint security software, EDR focuses on detecting and responding to advanced threats and attacks that may bypass traditional security measures. It provides real-time monitoring, threat hunting, and incident response capabilities, enabling organizations to quickly identify and mitigate sophisticated threats targeting their endpoints.
- Intelligence and Analytics: Endpoint protection systems are designed to swiftly detect, analyze, block, and contain ongoing attacks. They collaborate with other security technologies, providing administrators with valuable visibility into advanced threats enabling faster detection and remediation response times.
Examples of Endpoint Security
Here are some examples of endpoint security protection:
- Firewall services — Firewalls help monitor and control the incoming and outgoing traffic and can allow or deny access. This helps block any malicious traffic to protect endpoint devices.
- Anti-malware services — Endpoint antivirus software helps detect, prevent and remove any malware on devices.
- Encryption services — Encryption helps protect data stored on endpoint devices.
- Access control services — This helps administrators restrict access to endpoint devices and their data.
Are Endpoint Protection and Antivirus Solutions the Same?
While both endpoint protection and antivirus software serve as cybersecurity solutions, they differ in their scope and functionality. Endpoint protection goes beyond the traditional antivirus approach by providing a comprehensive suite of features tailored for network-wide device security. It conducts thorough scans, analyzing not only known viruses and malware but also identifying suspicious behavior and potential threats. Additionally, endpoint protection offers centralized security management, allowing administrators to efficiently monitor and control security measures across the network. However, due to its advanced capabilities and extensive coverage, endpoint protection tends to be priced higher, particularly for organizations with complex networks.
In contrast, antivirus software focuses primarily on monitoring and detecting viruses and malware. It performs regular scans on files and directories, swiftly alerting users if any malicious elements are detected. Alongside this, antivirus software provides web protection features that safeguard against online threats during internet usage. Operating as a standalone product, antivirus software offers a straightforward and simplified approach to device security. However, it lacks the centralized management capabilities found in endpoint protection, meaning that security measures need to be monitored and managed individually on each device.
7 Tips To Boost Your Cybersecurity With Endpoints

Following each of these 7 points will get your business in a good position moving forward.
1) Identify All Endpoints
The success of all endpoint security measures depends on you being able to identify all the endpoints in your business. Work with your employees and network administrators to pinpoint and classify all the different endpoints that connect to your business' network or data.
2) Have Secure Password Policies
One of the easiest yet still effective ways of strengthening your cybersecurity is to secure all your business passwords. Weak passwords are the root of far too many cyber security weaknesses and allow hackers to get their foot in the door. When creating passwords, make sure they all follow these best practices:
- Long and complex phrases
- Use both upper- and lower-case letters as well as numbers and special characters
- Don't use birthdays or other personal information
- Make it 9 characters or longer
- Use a different password for each account
- Don't store or right down your passwords
Remembering all these passwords is a pain, so using a password manager like LastPass is a great idea to keep things both simple and secure moving forward. Read more about keeping your password secure.
3) Implement Secure Access Service Edge (SASE) Software
It seems unavoidable in today's work climate to have your employees unable to access business applications and data remotely - especially when work-from-home policies have become more popular in some countries. Instead of constantly bailing your company out as cyber security incidents happen because of this, Secure Access Service Edge (SASE) software is a great method of endpoint protection to keep all your endpoints secure. Read more about What is SASE here.
SASE Sangfor Acces Secure is a native cloud-based SASE designed to help your employees safely and securely access all the business applications they need to do their job properly from anywhere, at any time. By identifying the user's identity, it will only grant access to those who have been granted prior access.
4) Get a Firewall for Your Business Network
Cyber security is best thought of as a multi-piece puzzle. No single software or solution will keep your business completely secure from potential cyber-attacks - only through a holistic cyber security and endpoint protection plan will you be able to do so.
A firewall is a crucial part of this and is able to keep all your endpoints more secure by eliminating 99% of malware before it even breaches your business perimeter. Firewalls like Sangfor Next-generation Firewall work by filtering and inspecting network traffic coming both in, and out of your business.
5) Eliminate Threats with NDR
Sometimes, advanced malware is able to bypass even the most advanced of firewalls. Having NDR (network detection and response) software like Sangfor Cyber Command uses state-of-the-art technology and artificial intelligence first to identify threats, and then hunt them down. Through a completely transparent process, businesses are then able to get a better understanding of how the attack took place and bolster their defenses next time around. Cyber Command integrates a variety of network and endpoint protection measures in order to respond to threats in a simple, effective, and automated manner.
6) Upgrade Your Corporate Infrastructure
One of the leading causes behind businesses with weak endpoint security is poor or outdated, infrastructure. For growing businesses that want simplified yet secure tech solutions, it's vital to go with next-gen cloud IT architecture. Sangfor Hyper-Converged Infrastructure is an all-in-one solution for computing, storage, network, and security. It provides your business with an efficient and scalable architecture that it can grow alongside while staying completely secure and protecting all endpoints.
7) Work with Cyber Security Experts
If implementing many of these different protection tools seems like a difficult task, there is always another alternative. Working with endpoint protection specialists like those at Sangfor can make the task far simpler and streamlined. Other than the solutions listed above, we offer holistic cybersecurity packages like Sangfor Endpoint Secure that integrate several security solutions to keep an entire organization's endpoints and network secure and protected - all without too much management or operation maintenance needed. Read more about Sangfor Endpoint Secure as well as success stories and more here.
Wach the introduction video to learn more about Sangfor Endpoint Secure.
Sangfor Solutions to Advance Your Cyber Security
Have any further questions about strengthening your endpoint security? Consider Sangfor Endpoint Secure. Our advanced endpoint security solution, Sangfor Endpoint Secure, is designed to defend systems from malware and APT threats with a holistic response and an approach different from NGAV and EDR solutions. It combats infections caused by malware and breaches from APT attacks across your entire organizational network. Whether you need on-premise management, cloud management, or hybrid solutions, Sangfor Endpoint Secure is scalable to meet your business needs.
Sangfor's Endpoint Secure has garnered significant success and helped many organizations improve their security.
- ASST Valle Olona is t is now a well-established healthcare provider responding to the medical needs of up to 32 municipalities in Italy. It used Sangfor Endpoint Secure, and Internet Access Gateway (IAG) to strengthen its data security and malware protection.
- Mahasarakham University (MSU) is the second higher education institution and the fourth university in the Northeast region of Thailand. MSU deployed Sangfor's Endpoint Detection and Response to work together with the other solutions within the organization to enhance protection and facilitate centralized management.
Frequently Asked Questions
No. Antivirus and Firewalls are a component of endpoint security, but endpoint security usually involves much more of a combination of different security measures.
Most organizations choose to deploy a mix of several endpoint solutions to secure their endpoints. This often includes a mix of firewalls, instruction detection, antivirus software and more. By having multiple areas covered in their endpoints, it ensures stronger protections against breaches and attacks.
Organizations first need to identify the risks that need protection in their endpoints. Once security risks have been identified, organizations should choose the right endpoint protection solution to secure them.





