Joomla Introduction
Joomla is a well-known foreign content management system, belonging to Portal (Enterprise Portal Website) type, which is more suitable for business. Joomla, one of the most popular open-source CMS content management systems in the world, uses PHP language and MySQL database to develop website content management system and supports execution on different platforms such as Linux, indows and Mac OS X.
Vulnerability Analytics
The cause of vulnerability is similar to the previous CVE-2015-8562. The \0 encoding conversion changes bits of serialized data, closes the original serialized data based on the difference in bits, allows the attacker to insert the crafted malicious serialized data after the closed serialized data, and send it to the server to perform deserialization parsing and execute the malicious code therein. The new PoC is different from the previous one in that the new PoC has been added || $a=’http//’; The added code is mainly to satisfy the feed_url parameter assignment in the call_user_func function in the simplepie.php file.
VULNERABILITY REPRODUCTION
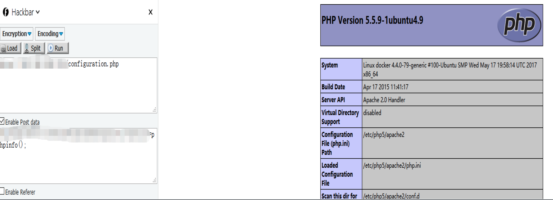
Access the index.php/component/users path, pass malicious serialized data in this path, or directly use the exp script exposed in the exploit-db to exploit the vulnerability. Vulnerability exploit can be achieved by writing Trojan directly to configuration.php, as shown in the following figure:
Globally, there are over 617135 Struts2-based assets are open to the Internet, among which 1,218 are in China,
Affected Joomla version:
Joomla 3.0.0 - 3.4.6
Reference
https://blog.hacktivesecurity.com/index.php?controller=post&action=view&id_post=41
Solution
Sangfor Security Cloud has been updated in the first place and gained the ability to scan websites for this vulnerability and ensure user security. If you are not sure whether your business systems have this vulnerability, sign in to Sangfor Visioner to apply for a 30-day free trial and check security health.
Sangfor Host Security has updated in the first place, customers can easily and quickly detect this high-risk attack by selecting vulnerability detection.
For Sangfor NGAF customers, simply turn on the corresponding security protection feature.
Sangfor CloudWAF has automatically updated the protection rules in the first place. Customers can defend against this high risk without any operation.
Remediation
The officially-released latest version has fixed the vulnerability. Joomla Users of the affected version can download the latest version for defense. Download link: https://downloads.joomla.org/cms/joomla3.





