Supply chains are a necessity in our fast-paced global village. Thousands of industries get affected by disruptions to these crucial spots. This is why a ransomware attack on a supply chain port has devastating effects in the long run. Without the right cybersecurity measures, hackers are finding it easier to target these vulnerable areas. The most recent example would be the recent LockBit ransomware attack on the Nagoya Port in Japan.

Nagoya Port Ransomware Attack
The Nagoya Port is the largest in Japan in terms of cargo. The port is responsible for almost 10% of Japan's total trade volume and handles car exports for major companies like Toyota. In 2021, the port boasted a total cargo throughput of 177.79 million tons.
In the early morning hours of the 4th of July, the Nagoya Port Authority confirmed that a glitch occurred in the computer system that manages container loading, unloading, and transport. By noon, operations were disrupted with the port being unable to load and unload containers from trailers.
A notice in Japanese was sent to customers to confirm that the attack disrupted container operations across all terminals within the port. The cyber-attack initially targeted the Nagoya Port Unified Terminal System which is the controlling body of the port.
The Nagoya Port cyberattack was noticed when a computer failed to start. According to the Nagoya Harbor Transportation Association, a notice was then printed out in English from the office printer detailing that the system’s data had been encoded.
The police launched an investigation and confirmed that the operator received a ransom demand in exchange for the recovery of the port’s system.
According to the Japan Times, the port authority also discovered that the LockBit 3.0 ransomware group was behind the attack. However, the hacking group has not yet claimed responsibility for the attack on their site.
In a release by Nagoya Harbor Transportation Association, the Port of Nagoya is said to have already begun gradually resuming operations on Thursday afternoon.
Who Is the Lockbit Ransomware Gang?
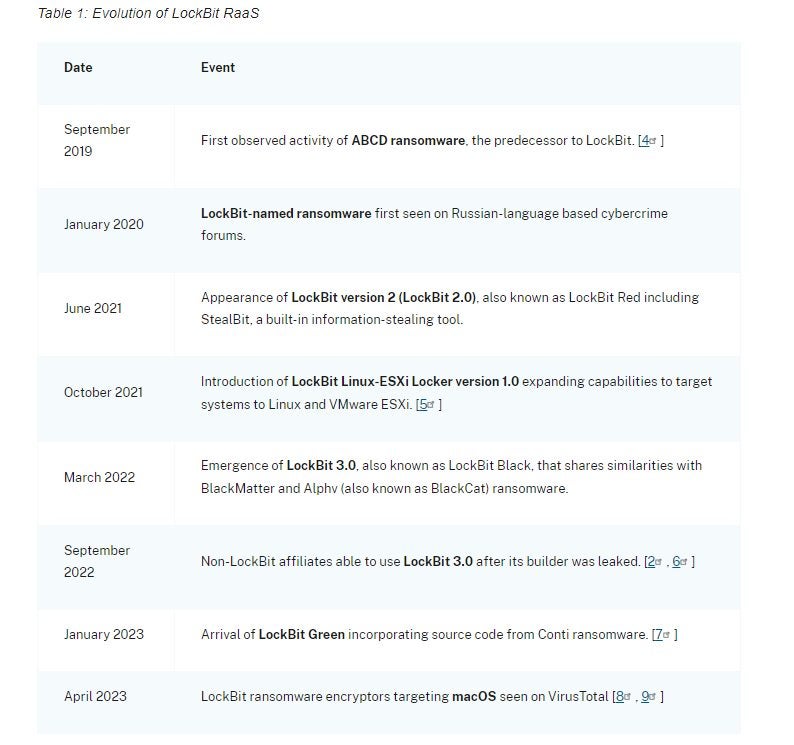
The LockBit ransomware gang is no newcomer to the headlines. LockBit cyber-attacks began in 2019. Initially named the "ABCD Ransomware", it was later renamed “LockBit”. In 2021, LockBit 2.0 appeared and introduced the double extortion technique and automatic encryption of devices across Windows domains.
In 2022, LockBit was the most deployed ransomware variant and Ransomware-as-a-Service (RaaS) provider across the world according to the Cybersecurity and Infrastructure Security Agency.
Some of the methods used by the LockBit ransomware gang have included:
- Giving affiliates their ransom payments before sending a cut to the core group. This is unlike other RaaS groups who pay themselves first and then pay affiliates last.
- Disparaging other RaaS groups in online forums.
- Publicity stunts that include paying people to get LockBit tattoos and putting a US$1 million bounty on information related to the real-world identity of LockBit’s lead who goes by the persona “LockBitSupp.”
- Developing and maintaining a simplified, point-and-click interface for its ransomware which makes it accessible to those with a lower degree of technical skill.
Sourced from the CISA
In 2023, the LockBit ransomware gang released LockBit Green based on the leaked source code of Conti ransomware.
Sangfor’s FarSight Labs discovered in June 2023 that the LockBit ransomware group listed the Taiwan Semiconductor Manufacturing Company (TSMC) on the LockBit 3.0 website. The hacking group made a staggering ransom demand of US$ 70 million - tying for the third-highest ransom ever recorded by a ransomware group.
Why Are Cyber-Attacks Against Ports So Popular?
Supply chains have always been a target for hackers. In 2022, the BBC reported that cyber-attacks on the Los Angeles Port have nearly doubled since the start of the Covid-19 pandemic.
Gene Seroka, the port's executive director, confirmed that the number of monthly attacks targeting the Port of Los Angeles was around 40 million at the time.
Seroka claimed that the threats came mainly from Europe and Russia aiming to disrupt the US economy. He warned that the port has to “stay steps ahead of those who want to hurt international commerce."
The port faces daily ransomware, malware, spear phishing, and credential harvesting attacks. These all try to cause as much disruption as possible to slow down economies.
In April of this year, the Port of Halifax in Nova Scotia and the ports of Montreal and Quebec were also hit by cyber-attacks. The 3 Canadian ports all had their websites taken offline.
A report states that the attacks were part of a denial-of-service attack. Internal data was not compromised in the breaches and operations in 2 of the ports were unaffected.
Supply chains are at constant risk. A few of the reasons why hackers might choose to target ports include:
- Digitalization of Systems – Most modern ports and supply chains have moved entirely over to technology to control not only transactions but also equipment and machinery. This makes them vulnerable to cyber-attacks.
- Remote Working – Since the pandemic, more jobs are moving towards remote or hybrid work environments. Ports and the like are no different. With the increase of home devices logging into the network, a port’s cybersecurity is at risk. Remote work provides a larger surface for attack – especially when members ignore cybersecurity protocols.
- Complex Malware – the modern age comes with a host of new threats. Cyber-attacks are now more advanced and capable of destabilizing larger companies – or entire supply chains.
- Lack of Cybersecurity Skills – A large portion of cyber-attacks are only successful in part due to human error. The lack of expert personnel or an advanced cybersecurity provider will result in a more vulnerable port.
- Increased Pressure – Much like the heatlthcare industry, ransomware attacks on supply chains cause massive commotion and need to be fixed immediately to avoid a domino effect of disruptions. This means that logistics industries are more likely to pay ransoms to get operations going again.
Improving the Cybersecurity of Ports and Terminals
The cybersecurity of ports and terminals is a crucial element for almost every industry. So, how do you enhance the cybersecurity measures in place to protect these vulnerable areas? We’ve drawn up some of the best practices for ports and terminals.
The European Union Agency for Cybersecurity (ENISA) issued a report in 2019 that provides guidelines for Port Authorities, private companies operating in ports, and other stakeholders.
Among the cybersecurity measures recommended are:
- Security measures to implement and maintain an information system security policy.
- Constant identification and management of risks and threats related to port activities.
- Protocols that protect critical data and ensure privacy.
- Efficient asset inventory and mapping systems.
- Cyber resilience that ensures business continuity and data recovery in the event of an attack.
- Endpoint protection on all connected devices.
- Employee training and awareness programs.
- Effective threat detection and response protocols and teams in place.
- Physical protection for data centers and servers.
- Improved access control within the network for authorized personnel.
UK's Department of Transport also released a Good Practice Guide in 2016 that explores the needs of ports and terminals when it comes to cybersecurity.
Within this document, some of the cybersecurity guidelines set up include:
- Develop a Cyber Security Assessment (CSA) to identify, manage, and assess cyber threats to the port facilities.
- Develop a Cyber Security Plan (CSP) to mitigate and respond to threats effectively.
While all these practices can help to maintain the cybersecurity of a supply chain, it’s important to rely on experts. Sangfor Technologies provides advanced and elevated cybersecurity and cloud infrastructure in leading industries around the world.
For more information, please visit www.sangfor.com.





