The digital landscape is a dynamic and evolving place. Unfortunately, this makes it the ideal petri dish for cybercriminals to thrive. Hacking groups have become widespread and use increasingly advanced and complex malware to target their victims. Malaysia recently became the main target of a cyber-attack carried out by the R00TK1T hacking group. The Southeast Asian country is no stranger to cybercrime and recorded almost 84 million cyber-attacks daily in 2022’s Q4.
In this blog article, we’ll explore the facts of the developing R00TK1T Malaysia hacking situation, examine the R00TK1T hacking group, and go over the ways that people, businesses, and organizations can stay safe from cyber-attacks in the future.
R00TK1T Hacking Group Threatens Malaysia
On the 26th of January, the R00TK1T hacking group announced on their Telegram channel that they would be launching a cyber-attack campaign against Malaysian infrastructure. The same threat was also posted on the dark web and warned that “chaos is brewing” and that the people of Malaysia should prepare for the collapse of infrastructure. In the ominous message, the hackers also declared that “no system is safe, no data [is] secure.”

Sourced from X
This prompted the National Cyber Coordination and Command Centre (NC4) to issue an advisory about the threat on the 28th of January 2024. In the advisory, the NC4 established that the R00TK1T plan was initially announced on the group’s Telegram group on January 26th. The multi-agency cybersecurity team also believed that the hacking group was part of a “retaliation team” that acts upon cyber-attacks ignited by the ongoing conflict in the Middle East. Based on historical data, the agency also established that the campaign would include web defacement, stealing confidential documents, and network intrusion with or without insider help.
The advisory further stated that the campaign could last weeks and cautioned all Malaysian organizations to “implement essential preventive measures to safeguard against this attack” as failure to do so could result in operational disruptions and compromise the security of the organization’s infrastructure, data, and systems.
On the 30th of January, Aminia, a local Malaysian network solutions and system integrator seemed to be the first victim of the group’s campaign when they shared several screenshots that seemed to depict Aminia’s backend system in their Telegram group. While the company confirmed the breach, they maintained that no sensitive data was compromised.
Then, on the 5th of February, R00TK1T defaced the YouTutor’s website by changing the top banner image of the homepage with the group’s signature message. The group also claimed that it had stolen data for several users that included names, addresses, phone numbers, and more.
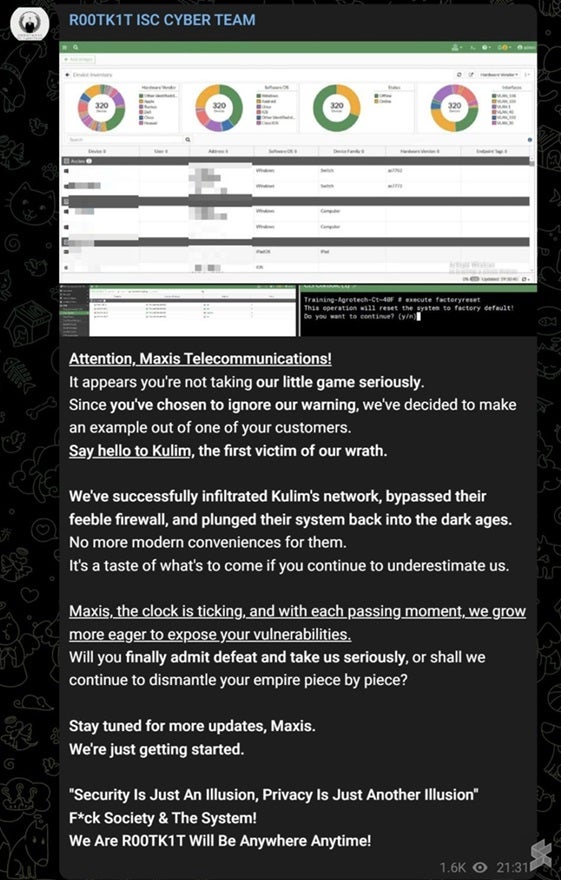
R00TK1T also claimed to have infiltrated Maxis. The group published three screenshots that seem to depict a backend system that belonged to the telecommunications company and were from the same system but each of them features three different router names - including Huawei LG8245 as well as Kaon AR2140 and AR1344E. Maxis then responded to the claim by the hacking group stating that its investigation did not find anything abnormal within its internal system, but it did identify an incident involving third-party vendor systems.
According to MalayMail, R00TK1T has now threatened to unleash further attacks on Maxis after this official response. The hacking group has refuted the claims that only third-party vendor systems were affected and urged Maxis to come clean or else they would unleash further chaos on their network.
At 7.31 pm on February 5th, R00TK1T claimed to have infiltrated what appears to be a Maxis employee’s dashboard to prove that their systems are not as impenetrable as they claim. The group then threatened to shut down their systems and expose sensitive data and vulnerability every two hours if Maxis failed to acknowledge their successful breach.
Sourced from MalayMail
At 9.31 pm, the hacking group then posted more screenshots and claimed to have breached the company’s Kulim Network by bypassing their firewall and seemingly performing a factory reset on one of their Agrotech-related systems.
Two hours later, R00TK1T issued a final warning and shared another screenshot of a system showing the current connections at Quayside Mall in Kota Kemuning. The group added that it has an elite squad of “52 highly skilled mercenaries” who are eagerly awaiting their command.
Sourced from MalayMail
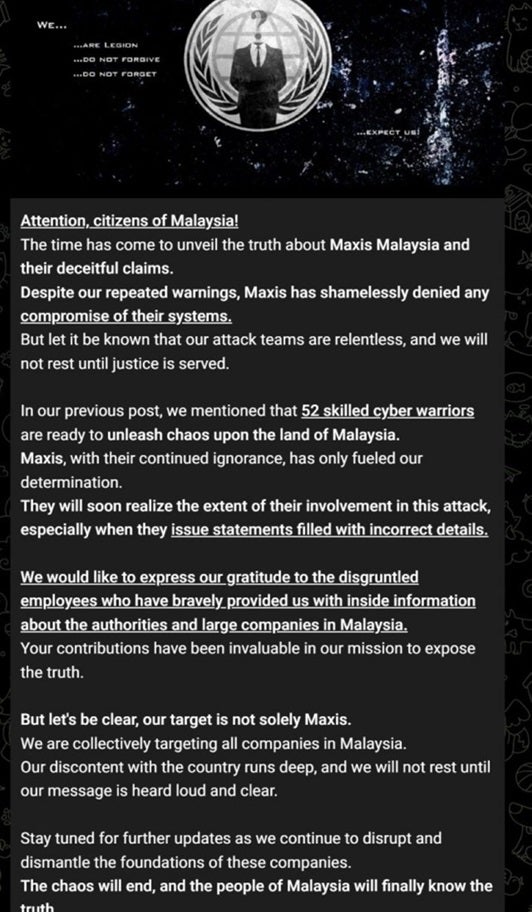
At 3.01 am on the morning of the 6th, the hacking group claimed that the continued ignorance of Maxis has only fielded their determination and that the company will soon realize the full extent of the attack after denying it. R00TK1T also mentioned its gratitude to disgruntled employees who they claim have provided them with inside information about the authorities and large companies in Malaysia.
R00TK1T has further warned that they are collectively targeting all companies in Malaysia and will not stop until their message is heard. Now that we know what R00TK1T has been up to lately, let’s get a better sense of what the hacking group is and what they stand for.
What Is R00TK1T?
The R00TK1T hacking group gets its name from the cyber term “rootkit.” A rootkit is a type of malicious software that allows unauthorized access to a network or system - allowing hackers to steal data and access files undetected. Rootkits use different methods to infiltrate systems. These include:
- Hooking
- Direct Kernel Object Manipulation
- Virtualization
- Firmware-Level Rootkits
- Memory-Based Rootkits
The R00TK1T hacking group is renowned for its covert operations and has previously targeted financial institutions, government databases, and multinational corporations. The group’s main methods involve exploiting software vulnerabilities, deploying malware, and executing sophisticated phishing attacks. Now, let’s take a look at some of the R00TK1T attacks that have taken place before to get a better understanding of the group.
R00TK1T Cyber-Attacks of the Past
The hacking group seems to have a habit of taking advantage of known vulnerabilities and disgruntled employees to compromise systems. The threat actor has targeted several sectors before – including education, healthcare, transport, telecommunications, and more. R00TK1T also claimed responsibility for many high-profile cyber-attacks in the past.
L’Oreal R00TK1T Cyber-Attack
The French cosmetics company L'oreal came under fire when the group claimed to have access to vital databases, compromising customer data, and sensitive company information. While the group touted the alleged L’Oreal intrusion as proof of their ability, skepticism remained as they famously provided minimal evidence of the actual attack.
Qatar Airways R00TK1T Cyber-Attack
Qatar Airways was next on the group’s list of targets. The group claimed to have extracted internal documents, interview recordings, Toolbox Remote Data package for the carrier’s Boeing 787 fleet, and access to its Airbus A350’s navigation software. However, these claims were also mostly unverified by the company itself.
Sodexo R00TK1T Cyber-Attack
R00TK1T warned in a Telegram post that Sodexo should be ready for the “spectacle of chaos” as they will execute cybercriminal activities that would disrupt the company’s operations. The group posted the threat targeting the South African branch of Sodexo on the 15th of January and is allegedly in possession of screenshots that include the Sodexo dashboard, source code, and employee database.
Lebanese Government R00TK1T Cyber-Attack
On the 22nd of January, the Lebanese Social Affairs Ministry confirmed that their website was hacked. R00TK1T claimed responsibility for the attack on their Telegram channel by celebrating “skillfully bypassing [the website’s] feeble security defenses” and “gaining unrestricted access to highly classified personal data.” The group was allegedly hired by Israeli mercenaries to “Stand with Israel” and warned users that over the coming days, they would be publicly publishing “private databases and documents.”
The threat of cyber-attacks, malware, and hacking groups looms over many people, businesses, and governments. While these threat actors are unpredictable and dangerous, there are certain ways that you can ensure your safety in such turbulent times. We’ll now go over some of the ways you can protect yourself from cyber-attacks in the future.
Sangfor's Advice: How to Safeguard Against Cyber-Attacks
When it comes to cybersecurity, it’s best to trust the professionals. This is why Sangfor Technologies can offer you premium advice and security tips to keep your systems and data safe. Some of the main Sangfor top security tips include:
- Installing Endpoint Security Software: The proper endpoint security solutions will ensure that your network is secure from every end.
- Regularly update your software: Regular updates ensure that your system runs smoothly and has access to the latest developments, including security patches that can protect you from vulnerabilities.
- Use firewall protection: Keep your network safe by using a strong next-generation firewall solution to keep malware and threats out. Firewalls like Sangfor’s Next-Generation Firewall work by filtering and inspecting network traffic coming both in, and out of your business.
- Regulate access with Zero-Trust ZTNA: Ensure that only authorized personnel have access to sensitive files by establishing a zero-trust system that requires identification each time.
- Be wary of email links, images, or attachments: Be extra cautious when opening any links regardless of whether you assume it’s from a trusted source or not.
- Use strong passwords: A shocking number of cyber-attacks are a result of people having predictable and easy passwords. Try to use long, unique, and difficult passwords for all your accounts and devices.
- Encourage cyber awareness training: Most breaches occur due to negligence or oblivion on the part of employees. Try to include cyber training for your staff to ensure that they are prepared.
- Build a correlated security protection system: Focusing on the seamless synergy between security products such as firewall and endpoint protection, because an APT can easily bypass a single-point protection.
- Implement defense and proactive response against cyber threats and use security solutions that use the latest AI capabilities.
While we can do several things to safeguard ourselves from cyber threats, they still seem to evolve at a rapid pace that most people cannot keep up with. This is why cybersecurity experts like Sangfor Technologies exist to make your digital transformation simpler and secure..
Choosing Sangfor Solutions for Enhanced Cybersecurity
Sangfor Technologies is a global leading vendor in cybersecurity and cloud computing products & services. With a range of advanced, intelligent, and affordable platforms, products, and services, Sangfor has been a leading force in protecting against cyber threats of every kind. Our unique security solutions offer a proactive approach to cybersecurity that has revolutionized the way threat actors are dealt with.
Seamlessly protect your networks with Sangfor’s Endpoint Secure which is designed to defend systems from malware and APT threats with a holistic response and an approach different from NGAV and EDR solutions. This platform combats infections across your entire organizational network. Whether you need on-premises management, cloud management, or hybrid solutions, Sangfor’s Endpoint Secure is also entirely scalable to meet your business needs.
Go a step further with your threat hunting and make use of Sangfor’s Cyber Command with state-of-the-art technology and artificial intelligence that easily identifies threats and then hunts them down. Through a completely transparent process, businesses can get a better understanding of how the attack took place so they can reinforce their security for the future. Cyber Command integrates a variety of network and endpoint protection measures to respond to threats in a simple, effective, and automated manner.
For most businesses, security is also a matter of access and that’s why the SASE Sangfor Access platform is ideal to help employees safely navigate the network. The native cloud-based design ensures secure and authorized access to all business applications from anywhere and at any time. This makes it perfect for remote or hybrid work environments and ensures overall network security.
Sangfor Cyber Guardian Managed Detection and Response MDR Services
Sangfor’s Cyber Guardian MDR service also ensures an overall defense for your network. This advanced Managed Detection and Response service uses the power of both human intuition and AI technology to detect and respond to security threats in seconds. With 24/7 threat detection, Cyber Guardian uses the latest threat intelligence to provide context-relevant and accurate alerts combined with expert assistance and recommendations in a unique two-stage process.
Sangfor is a trusted and reliable cybersecurity and cloud solutions provider. Ensure the best security for your network when you rely on the best. Contact Sangfor today for any queries or visit www.sangfor.com for more information.





