vBulletin is a global leader in forum and community software. Featuring strong security, robust management, good user experience, and the capability to serve more than 40,000 online communities, it is a very popular platform used by many major forums. Customers include well-known game company EA, game platform Steam, Sony, NASA, etc. It has many large customers in China including forums with tens of thousands of users such as Fengniao, 51 group buying, and OceanTribe.
Vulnerability Introduction
On August 11, 2020, Sangfor FarSight Labs followed a zero-day vBulletin 5.x remote code execution vulnerability identified by security researcher Amir Etemadieh (Zenofex). The zero-day vulnerability bypasses the released patch for CVE-2019-16759, a vBulletin vulnerability disclosed in 2019. The new zero-day does not have a CVE designation assigned yet, but the severity is identified as critical due to its simplicity and its ability to remotely execute commands on vulnerable vBulletin servers. Remote attackers can execute arbitrary code through specially crafted malicious parameters to control the target server or steal sensitive user information. This vulnerability affects all versions of vBulletin 5.x and exploit attacks have started to appear in the wild. vBulletin has recently released a fix for the vulnerability.
Vulnerability Reproduction
We reproduced this vulnerability in vBulletin 5.x by executing echo command, as shown in figures below:
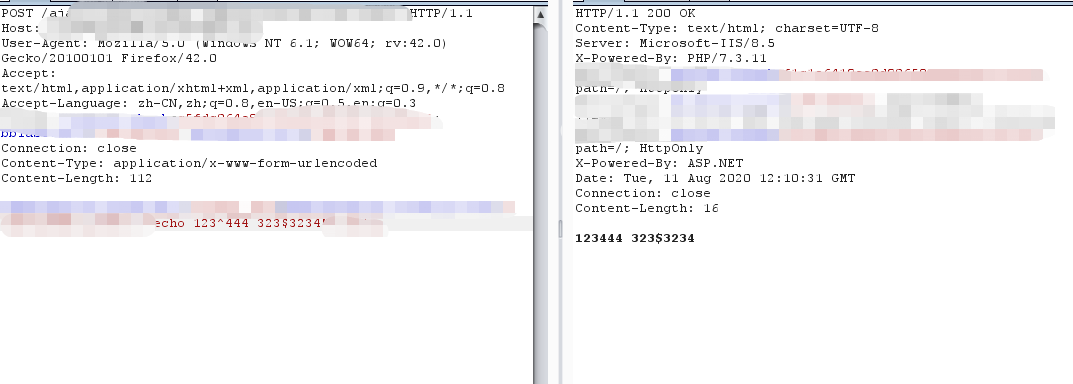
Impacts
By searching from the Internet, we know that there are nearly 30,000 public-facing websites using vBulletin worldwide, and many of them are international community forums maintained by large international companies, so the vulnerability causes huge impact.
Affected versions:vBulletin 5.x
Timeline
Aug 11, 2020 Sangfor security team tracked a zero-day vulnerability, vBulletin 5.x remote code execution vulnerability.
Aug 12, 2020 Sangfor FarSight Labs reproduced this vulnerability successfully and released a vulnerability alert with remediation steps.
Remediation
1. vBulletin announced that patches were available for the 5.6.0, 5.6.1, and 5.6.2 versions of vBulletin Connect. The fixes remove the PHP Module. A full patch will be included in the next build of 5.6.3 and the PHP Module will be completely removed in vBulletin 5.6.4. For affected users, please follow its official website to obtain the latest patches: https://www.vbulletin.com/.
2. Sites running older versions of vBulletin need to be upgraded to vBulletin 5.6.2 as soon as possible according to vBulletin.
Temporary Remediation
vBulletin administrators can modify settings to prevent this vulnerability from being exploited by following these steps:
a) Log in to vBulletin Administrator Control Panel.
b) Click "Settings" on the left menu and click "Options" in the drop-down menu.
c) Select "General Settings" and click "Edit Settings".
d) Look for "Disable PHP, Static HTML, and Ad Module rending" and set to "YES", then Click Save.
Sangfor Solution
1. For Sangfor NGAF customers, update NGAF security protection.
2. Sangfor Cloud WAF has automatically updated its database in the cloud. These users are already protected from this vulnerability without needing to perform any additional operations.
3. Sangfor Cyber Command is capable of detecting attacks which exploit this vulnerability and can alert users in real-time. Users can correlate Cyber Command to Sangfor NGAF to block an attacker's IP address.
4. Sangfor SOC has Sangfor security specialists available 24/7 to help you resolve any security issues. For users with vulnerabilities, the SOC regularly reviews and updates device policies to ensure protection against this vulnerability.





