Phishing is one of the most persistent cyber threats in today’s digital world. By preying on human emotions like trust and sense of urgency, attackers use deceptive methods to steal sensitive information or compromise systems. Whether it is done through fake emails, texts, or calls, phishing remains a critical risk for individuals and organizations alike.
This article explores the meaning of phishing, various types of attacks, and real-world examples. Understand how phishing works and recognize the warning signs to take steps to protect yourself and your digital assets.
What is a Phishing Attack - Definition
A phishing attack is a type of cyber-attack where attackers craft fraudulent yet convincing messages to manipulate recipients into performing harmful actions. These actions can include clicking on malicious links, opening infected attachments, providing sensitive information, or transferring money.
The term phishing originates from "fishing," as attackers "cast a wide net" to catch unsuspecting victims. Unlike technical hacking methods, phishing leverages human behavior—exploiting trust, fear, and urgency—to bypass technical defenses and directly target individuals or organizations.
Why Are Phishing Attacks Dangerous?
- Human Manipulation: Attackers exploit emotions like fear or urgency to make victims act impulsively.
- Multiple Delivery Methods: Phishing attacks can be sent via email, text, phone call, or social media, increasing their reach.
- Severe Impact: Victims can face identity theft, financial loss, or system breaches, often with lasting consequences.
- Credible Deception: By impersonating trusted entities like banks or government agencies, attackers create a false sense of security.
- High Success Rate: The reliance on human error and increasingly realistic tactics makes phishing a persistent and effective threat.
How Do Phishing Attacks Work?
Phishing attacks are carefully orchestrated to deceive victims into taking harmful actions, such as clicking on malicious links or providing sensitive information. By combining technical deception with psychological tactics, attackers craft fraudulent messages to achieve their objectives. Below is a step-by-step breakdown of how phishing works:
Target Research and Content Crafting
The success of a phishing attack hinges on convincing the recipient that the message is legitimate. To achieve this, attackers conduct thorough research on their target and craft messages tailored to appear relevant and credible.
For mass phishing campaigns, attackers impersonate well-known brands like DHL, Amazon, and Google. For targeted attacks, such as spear phishing, attackers research specific organizations or individuals, often finding email addresses and other details on company websites or social media platforms.
Attackers ensure that their messages align with the tone, language, and style of the trusted entity they are mimicking. For example, LinkedIn was reported as the most impersonated brand in phishing attacks during Q1 2022, illustrating how cybercriminals exploit widely recognized names to increase credibility.
Objective 1: Information Theft
Some phishing emails are designed to steal personal information by pretending to be from trusted organizations like banks or government agencies. These emails often create a sense of urgency, prompting recipients to provide sensitive details, such as:
- Login credentials
- Financial data
- Personal identification information
The stolen information is then sold on the dark web or used for fraudulent activities like applying for credit cards or making unauthorized transactions.
Objective 2: Financial Fraud
Many phishing scams aim to deceive recipients into transferring funds to fraudulent accounts. These emails often impersonate someone with authority, such as a company executive or a financial institution, and present situations requiring immediate attention. Victims may be left too anxious to check the credibility of the email and end up making the transfer.
In a new public service announcement, the FBI's IC3 reported that business email compromise (BEC) scams cost companies around the world $43 billion between June 2016 and December 2021.
Objective 3: Network Intrusion
Phishing attacks can be used to breach enterprise networks to achieve bigger objectives, such as ransomware infection and data theft. In fact, they are one of the most common ways bad actors gain initial access to enterprise networks. According to the Cisco 2021 Cybersecurity Threat Trends report, 90% of data breaches involve phishing. It can achieve network infiltration in two main ways:
- Phishing links: Most phishing emails contain links leading to malicious websites. These websites may automatically download malware onto the victim’s device or mimic login portals to steal credentials. According to Statista, 611,877 phishing sites were detected worldwide in Q1 2021, a sharp increase from 165,722 in Q1 2020.
- Phishing attachments: Attackers frequently attach malicious files to emails. These attachments, such as Word or Excel files, can appear harmless but may contain embedded macros or scripts that execute malware once opened. The macro function can also act as a loader to download and execute another malware payload. Other common phishing attachments include .exe, .zip, .rar, .pdf, and .iso files.
Once malicious tools or files are installed, attackers use more sophisticated techniques to escalate their attack, gaining further access to sensitive systems and data.

Types of Phishing Attacks
Phishing attacks can be carried out in a number of different ways, targeting a wide range of victims through various methods. Below are the most common types:
Phishing Campaign
In a phishing campaign, attackers send emails to thousands or even millions of users. These messages are generic but relevant to a broad audience. For example, emails claiming suspicious activity on an account often prompt recipients to reset their passwords. The primary goal is to steal credentials, such as usernames, passwords, phone numbers, or financial information.
Spear Phishing Attack
Spear phishing is a more targeted form of phishing attack aimed at specific individuals, organizations, or industries. Attackers often conduct in-depth research on their targets to craft highly personalized and convincing messages. For example, attackers may tailor emails using details like a person’s name or position to gain trust. According to Symantec’s Internet Security Threat Report 2019, 65% of threat actors used spear phishing as a primary attack method.
Internal Spear Phishing Attack
An internal spear phishing attack occurs when a legitimate user’s email account is compromised and used to send spear phishing messages to other employees or external contacts. Because the email originates from a trusted source, recipients are more likely to engage with links or attachments. This method is often used for lateral movement within an organization’s network as opposed to an initial breach.
Whale Phishing Attack
Whale phishing, also known as CEO fraud, targets high-ranking individuals like executives or CEOs. Attackers impersonate these individuals to issue fraudulent instructions to subordinates, such as authorizing wire transfers. Due to the authority associated with such figures, recipients are more likely to comply. According to newly released data by Statista, the global volume of CEO fraud increased from 9,708 in 2017 to 17,607 in 2020. FBI’s IC3 report found that BEC was responsible for $2.4 billion in losses to U.S. companies in 2021.
Social Media Phishing Attack
As the name suggests, it occurs on platforms like Facebook, X (formerly Twitter), and LinkedIn. Attackers may post fake offers, create fraudulent accounts, or interact with users under false pretenses to gain trust. These tactics often lead victims to reveal credentials or download malicious files.
Smishing
Smishing, or SMS phishing, involves cybercriminals sending deceptive text messages designed to trick victims into clicking malicious links. These messages often appear urgent, such as notifications about account issues or delivery delays. Victims who click are redirected to fake websites where sensitive information, like login credentials or payment details, is collected.
Vishing
Vishing, also called voice phishing, involves using phone calls to impersonate trusted sources, such as banks or government agencies. Attackers create a sense of urgency by claiming fraudulent activity on accounts or offering fake solutions to technical issues. Victims are pressured into sharing confidential details, such as PINs, passwords, or personal identification numbers.
Angler Phishing
Angler phishing is a targeted form of social media phishing where attackers impersonate customer service representatives on platforms like X or Facebook. It differs from general social media phishing by focusing specifically on users seeking support. For example, a victim asking a brand for help online might receive a reply from a fake account directing them to a fraudulent site to steal personal information.
Phishing Examples
Here are some real-life examples of phishing attacks, demonstrating how attackers exploit trust, urgency, and fear to achieve their objectives:
COVID-19 Phishing Campaigns (Mass Phishing Campaigns)
In the early days of the COVID-19 pandemic, the FBI reported a significant increase in phishing scams. Attackers capitalized on the crisis by launching COVID-themed phishing campaigns, focusing on topics such as financial relief, vaccine information, and case updates. Many emails impersonated trusted organizations like the Centers for Disease Control and Prevention (CDC), tricking recipients into sharing sensitive information or clicking on malicious links. These actions often led to malware or ransomware infections.
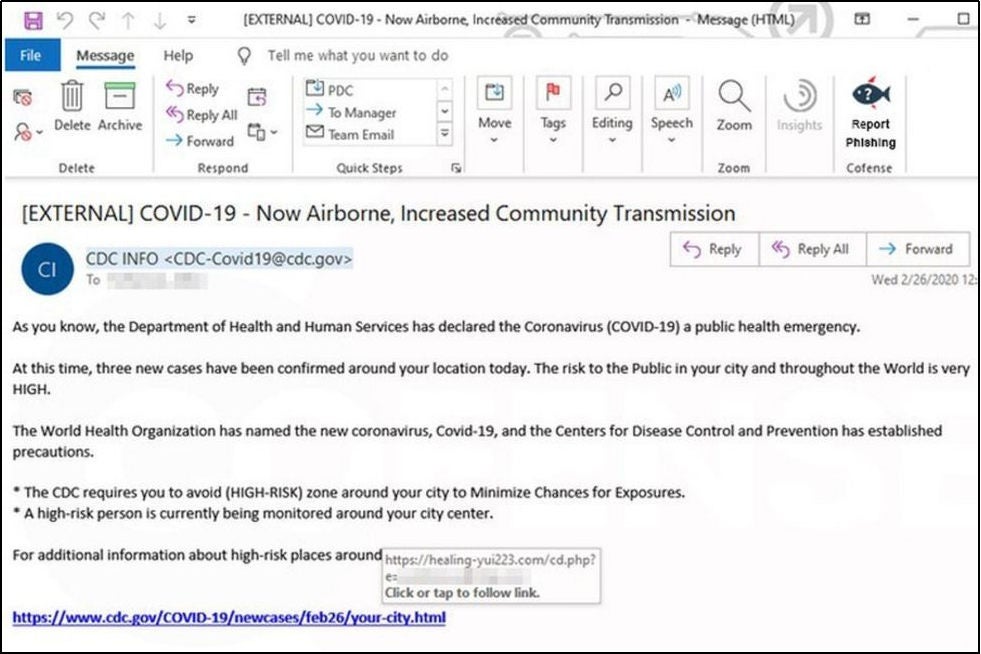
Image of COVID-themed phishing email that posed as the CDC, courtesy of BBC
Ireland Health Service Executive Ransomware Attack (Spear Phishing)
In May 2021, a ransomware attack hit Ireland’s Health Service Executive (HSE), with the attacker demanding a ransom of $20M. HSE has published a post-incident review of the attack. It was discovered that the breach occurred after an internal user opened a malicious Excel file attached to a spear phishing email. The attacker had infiltrated the network for eight weeks before deploying ransomware on May 14, 2021, that encrypted 80% of HSE’s systems. The attack compromised 700GB of personal data, affecting thousands of Irish citizens.
Financial Times Cyber-Attack (Internal Spear Phishing)
In May 2013, the Syrian Electronic Army (SEA) targeted the Financial Times (FT) with an internal spear phishing attack. Hackers gained access to an FT employee’s corporate email account and used it to send phishing emails to FT employees. These emails contained links that appeared to direct users to CNN web pages but instead led to malicious sites. To escalate the attack, SEA mimicked IT department warning emails, tricking even more employees into falling for the scam.
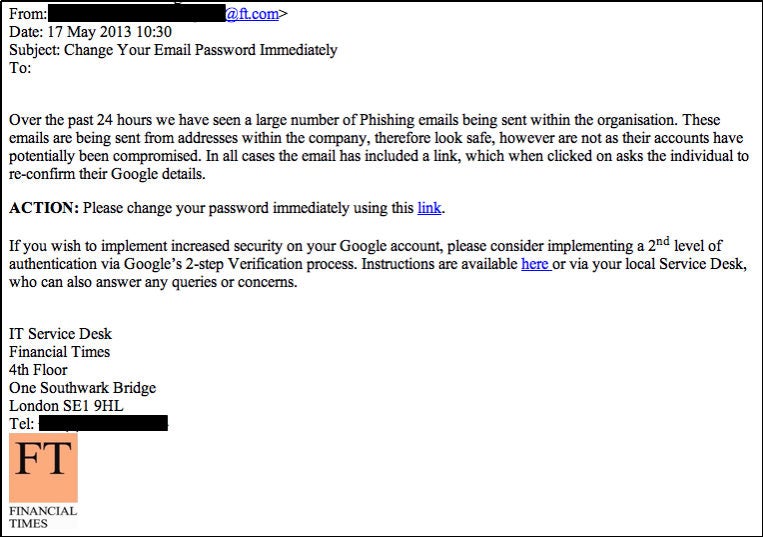
Image of spear phishing email that mimicked the IT department’s warning message, courtesy of FT Labs
FACC Phishing Attack (Whale Phishing/CEO Fraud)
In January 2016, Austrian aerospace parts maker FACC suffered a €50 million loss in one of the most significant CEO fraud scams. An attacker posing as FACC’s CEO sent an email to the finance department requesting funds for an acquisition project. Trusting the email's legitimacy, an employee obliged, and the money was transferred to an account under the attacker’s control. This phishing attack led to serious consequences, including the dismissal of the CEO and CFO for negligence.
Attack on Security Researchers (Social Media Phishing)
On January 25, 2021, Google’s Threat Analysis Group (TAG) reported a series of attacks targeting security researchers. Attackers created fake research blogs and Twitter accounts, posing as fellow researchers to establish credibility. They then proposed collaborating with the researchers on vulnerability research. Victims were sent a VS project that contained the attacker’s custom malware in the form of a DLL file. The DLL was used for command and control (C2), and the attack led to the theft of valuable research.
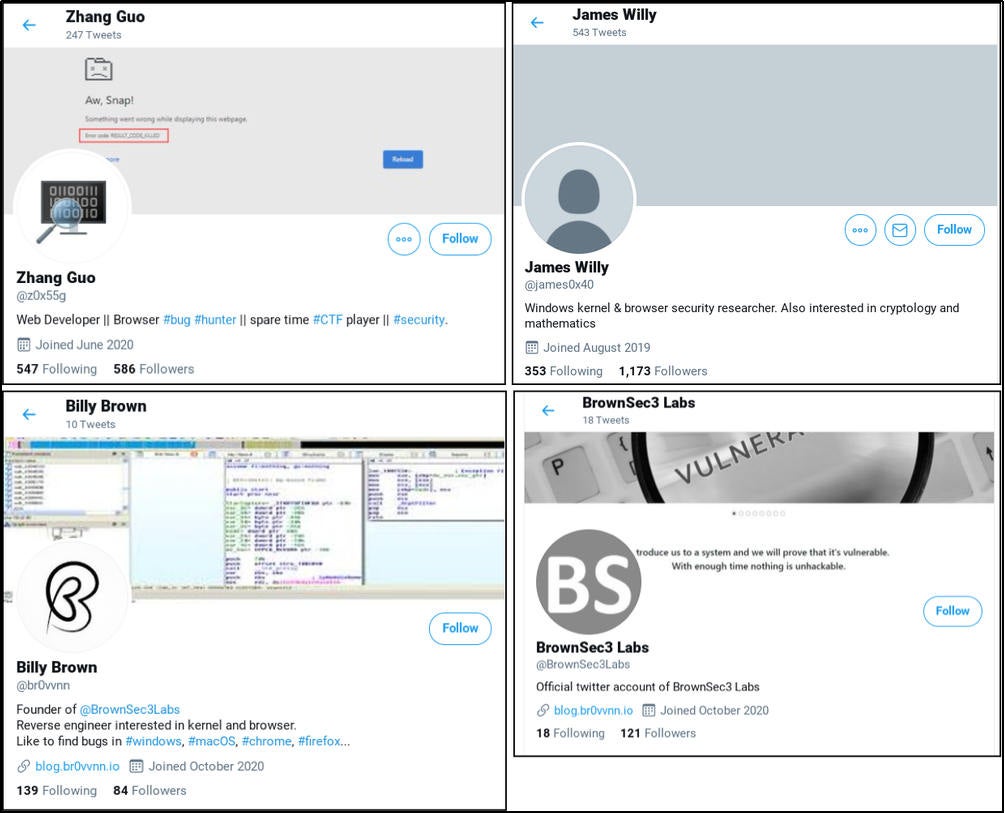
Images of Twitter profiles of attackers posing as security researchers, courtesy of Microsoft TAG
Industries Most Affected by Phishing
Phishing attacks target industries with high-value data or financial assets. These industries are especially vulnerable due to the sensitive nature of the information they handle and their reliance on digital systems:
- Financial Services: Banks, credit unions, and payment processors are frequent targets due to their access to financial information. Phishing schemes often aim to steal login credentials for online banking or access to corporate accounts, enabling fraudulent transfers or unauthorized purchases.
- E-commerce: Online stores are attacked to intercept customer payment details, such as credit card numbers and billing information. Attackers may also steal customer accounts to commit fraud, like purchasing goods for resale or exploiting loyalty points.
- Healthcare: Medical records contain a wealth of personal information, including social security numbers, insurance details, and health data. Attackers often target healthcare providers to sell this information on the dark web or to impersonate patients for insurance fraud.
- IT and Telecommunications: These industries face frequent phishing attacks aimed at compromising internal systems, stealing intellectual property, or gaining access to broader networks. Cybercriminals often use phishing as an entry point for larger attacks, like ransomware.
- Social Media: Social platforms are exploited to hijack user accounts or impersonate individuals. Once compromised, attackers use these accounts to launch further phishing campaigns, spread malware, or conduct scams targeting the victim's connections.
The Dangers of Falling for Phishing
Falling victim to a phishing attack can have far-reaching consequences for both individuals and businesses. Here’s a detailed breakdown of the risks:
For Individuals
- Financial Loss: Attackers may use stolen banking details or credit card numbers to withdraw funds, make unauthorized purchases, or even apply for loans under the victim’s name.
- Identity Theft: Cybercriminals can use stolen personal information to commit identity theft, which can lead to legal complications or damaged credit scores.
- Account Takeovers: Losing access to key accounts, such as email or social media, can result in the attacker misusing these accounts for further scams or spreading malware to the victim’s contacts.
For Businesses
- Data Breaches: Phishing can give attackers access to confidential customer or internal data. This often results in financial penalties for non-compliance with data protection laws like GDPR or HIPAA.
- Reputational Damage: A data breach can severely harm a business's reputation, eroding customer trust and impacting future revenue.
- Operational Disruption: Compromised systems or ransomware attacks stemming from phishing can halt operations, leading to revenue loss and additional recovery costs.
- Financial Penalties: Businesses may face fines or lawsuits for failing to secure their data or for breaches caused by phishing attacks.
Why Phishing Attacks are So Successful
Phishing attacks are one of the most favored attack vectors (network entry points) by attackers. This is due in part to their high success rate. It essentially boils down to two fundamental reasons.
- Weak Email Security: Phishing attacks are successful largely because phishing emails are not always blocked from reaching the mailbox. This is down to weak email filtering and is made worse by a technique called email spoofing. This allows attackers to forge the sender’s address. The wide scope of business email communication means that it would be impractical to have strict email settings. For example, to only accept emails from contacts or block certain file attachments. Even so, employees may still fall victim to internal spear phishing sent from a trusted account. As long as these emails land in the mailbox, there is always a chance of deceiving the recipient.
- The Human Element: Phishing attacks belong to a category of cyber-attacks known as social engineering. Social engineering involves human interaction and tricking people into specific actions. Humans are considered the weak links in a computer network. Most employees have little to no knowledge of network security. This is due to a lack of cybersecurity training to raise security awareness and teach best practices. However, even if employees have a certain degree of security awareness, it is almost impossible to be vigilant at all times. Sometimes you are simply in a rush or too tired to inspect every email. Attackers are acutely aware of this and exploit it in full.
Best Practices to Avoid Falling for Phishing Attacks
Protecting yourself from phishing starts with knowing what to look for. Simple steps like verifying email authenticity and avoiding suspicious links can make a big difference. Follow these tips to stay one step ahead of attackers.
Verify the Email’s Authenticity
Phishing emails often mimic trusted organizations, but there are subtle clues that can help you identify them:
- Email Header
- Carefully examine the sender’s email address. Fake addresses may look similar but often contain irregularities such as misspellings (e.g., "support@yourb4nk.com") or unusual punctuation.
- Check the “cc” field. Phishing emails are frequently sent to multiple recipients indiscriminately, whereas legitimate emails about personal matters are not.
- Email Content
- Ensure the content is relevant. For example, an email warning about issues with a service you don’t use is likely fake.
- Watch for poor grammar or spelling errors, as many phishing attempts originate from non-native speakers of the target’s language.
- Be cautious of unreasonable requests, such as transferring funds or disclosing sensitive information. When in doubt, confirm the request via an alternative communication channel.
- Links
- Hover over links to reveal their actual destination. Verify that the domain matches the organization’s official site, as fraudulent links often redirect to malicious domains.
- Ensure links begin with "https," which indicates a secure connection. Links with "http" alone can be unsafe.
- Attachments
- Examine the full file name and extension before opening attachments. Suspicious indicators include overly long file names, inconsistent file names, or unexpected formats (e.g., .exe files disguised as documents).
Access Your Real Account
Phishing emails may prompt you to act urgently by claiming your account requires immediate attention. Instead of clicking on links within the email, manually access your account through the organization’s official website or app. For instance, if prompted to change a password, visit the website directly and initiate the process securely.
Reach Out to the Organization
When in doubt, contact the organization directly using verified contact details, such as those on their official website. Avoid replying to the suspicious email or using the provided contact
information, as it may lead back to the attacker. While this may take extra time, it is a crucial step to ensure your security.
Additional tips for phishing Prevention
- Use Email Filtering: Activate spam filters to block phishing attempts before they reach your inbox.
- Install Security Software: Employ anti-phishing tools and antivirus software to detect and neutralize threats.
- Enable Two-Factor Authentication (2FA): This adds a second layer of protection. Even if your credentials are stolen, attackers cannot access your account without the additional authentication factor.
What to Do If You Fall Victim to Phishing
Falling victim to phishing can be alarming, but quick action can minimize the damage. Follow these steps to protect yourself and limit the impact of an attack:
1. Change Passwords Immediately
Start by updating the passwords of any compromised accounts. Use strong, unique passwords that include a mix of uppercase and lowercase letters, numbers, and symbols. Avoid reusing old passwords across multiple accounts.
- Why It’s Important: Changing passwords prevents attackers from accessing your accounts, especially if they’ve been used to log in from suspicious locations.
- Pro Tip: Consider using a password manager to generate and store strong passwords securely.
- Example: If you entered your email login credentials on a fake login page, immediately change your email password. This ensures the attacker cannot access your emails or reset passwords for your other accounts linked to that email.
2. Notify Relevant Parties
Inform the organization connected to the compromised account. For financial accounts, notify your bank or credit card provider immediately. Most institutions have a fraud department to assist in preventing unauthorized transactions.
- Why It’s Important: Prompt notification allows the organization to freeze compromised accounts, monitor for suspicious activity, and issue fraud alerts to prevent further damage.
- Example: If you provided your credit card number on a phishing site, call your bank to cancel the card and request a replacement. They can also help you dispute fraudulent charges.
3. Monitor Your Accounts
Review your financial statements, credit reports, and account activity regularly for unusual changes or transactions. Where possible, enable real-time alerts for account activity.
- Why It’s Important: Early detection of unauthorized transactions or changes can help you respond quickly and prevent larger financial losses.
- Example: If you notice a small unauthorized charge, report it immediately—such charges are often "test runs" by attackers before making bigger fraudulent purchases.
4. Report the Attack
File a report with relevant authorities or organizations, such as your local cybersecurity agency, financial fraud hotline, or the FTC (in the U.S.). Notify your workplace if the phishing incident involved your professional email.
- Why It’s Important: Reporting helps authorities trace and shut down phishing operations, protects others from falling victim, and provides official documentation for disputing unauthorized charges or transactions.
- Example: Forward phishing emails to the fraud department of the organization the email claimed to represent (e.g., "fraud@yourbank.com"). This helps them investigate and warn other customers.
5. Scan Your Devices for Malware
Run a comprehensive scan using trusted antivirus or anti-malware software. Ensure the software is updated to detect and remove the latest threats.
- Why It’s Important: Phishing scams often use malicious links or attachments to install malware, such as keyloggers or ransomware, on your device. Removing malware promptly prevents further damage.
- Example: After opening a suspicious attachment, your computer starts acting sluggish. A scan reveals a keylogger tracking your keystrokes. Removing it immediately safeguards your sensitive data.
6. Freeze Your Credit
If you’ve provided sensitive financial information, such as your Social Security number or bank account details, consider placing a credit freeze. This blocks unauthorized parties from opening accounts in your name.
- Why It’s Important: A credit freeze limits fraudsters' ability to exploit your information for financial gain, such as applying for loans or credit cards.
- Example: After falling victim to a phishing scam, you place a credit freeze with major credit bureaus to prevent attackers from taking out loans in your name.
The Role of AI in Phishing
Artificial intelligence (AI) has transformed the phishing landscape, enabling attackers to craft more convincing scams while helping defenders enhance cybersecurity measures.
For Attackers
AI allows cybercriminals to automate and personalize phishing campaigns. By analyzing publicly available data, AI can create targeted, realistic emails that increase the chances of deception. Advanced tools, such as deepfake technology, further enable attackers to impersonate voices or videos, making phishing attempts even more convincing.
For Defenders
AI-powered tools play a critical role in detecting and preventing phishing attacks. These systems identify suspicious patterns, such as unusual sender details or links, and flag them before they reach users. AI also supports phishing simulations to train employees, helping organizations build resilience against evolving threats.
Protect Against Phishing with Sangfor Security Solutions
Sangfor provides advanced tools like Network Secure, Endpoint Secure, and Cyber Command to defend against phishing and other cyber threats. These solutions deliver comprehensive, multi-layered protection for individuals and organizations.
Sangfor Network Secure (NGFW)
Sangfor Network Secure is the world’s first AI-enabled next-generation firewall (NGFW). While traditional firewalls rely on signatures to block threats, next-gen firewalls integrate a range of advanced capabilities.
In the case of phishing attacks, Sangfor Network Secure connects with Threat Intelligence (TI), a component of Neural-X, to inspect the reputation of IPs, URLs, and files in real time. If a phishing victim is lured into clicking a link, Sangfor Network Secure sends the URL to Neural-X TI for analysis. Connection to the URL is blocked if it is deemed malicious.
Sangfor Network Secure also benefits from the integration of Sangfor Engine Zero, a world-class AI-powered malware detection engine. Engine Zero has been pitted against tens and millions of malware samples to train its malware detection accuracy and efficiency. Engine Zero detects known and unknown malware by learning to recognize the characteristics of malware. Phishing attachments are thoroughly scanned to detect maliciousness, such as irregular code that indicates tampering. Such files are blocked from being accessed or downloaded by Sangfor Network Secure to prevent malware infection. With Sangfor Network Secure deployed, 99% of malware is prevented from breaching the network.
Sangfor Endpoint Secure (EDR)
Sangfor Endpoint Secure is an endpoint detection and response (EDR) solution that goes beyond traditional endpoint security software like antivirus. Endpoint Secure stands ready to clean up malicious files that managed to sneak past the firewall and download onto the endpoint.
As with Network Secure, Endpoint Secure is integrated with Engine Zero and performs AI-powered malware analysis on files loaded onto endpoints. However, Endpoint Secure has the added ability to detect malicious files based on their behavior and not solely on features. For example, malicious files downloaded from phishing links or attachments usually connect to the internet to download additional files, run automated commands, or create new files on the endpoint. The intelligent detection of Engine Zero can detect these malware-like behaviors. The perpetrating files will be blocked from running and quarantined.
Endpoint Secure can not only stop malicious files but also correlates with Network Secure to kill the chain of infection in one click. For example, Endpoint Secure can work with Network Secure to identify and quarantine the malicious process that is making C2 communication.
Sangfor Cyber Command (NDR)
While Network Secure and Endpoint Secure are great at detecting malware and threats, we understand that nothing is 100% foolproof. Sangfor Cyber Command provides a crucial layer of protection for a multi-layered defense against cyber-attacks.
Sangfor Cyber Command is a network detection and response (NDR) solution that analyses real-time network traffic to detect hidden threats. To do this, Cyber Command uses machine learning to build and learn baselines of normal network activity. AI-powered behavioral analytics analyses real-time network traffic and compares results with these baselines to detect anomalies.
The idea is that the breach of one device is usually no good to an attacker. To achieve bigger objectives, attackers need to move inside the network and establish communication with their own infrastructure. These activities show up in network traffic. Given that malicious operations are different from normal network behavior, NDR solutions can detect them as anomalies and unearth the threat. Cyber Command further correlates with Network Secure and Endpoint Secure to map the kill chain and instruct them to take remedial action, such as isolating compromised hosts.
When used in conjunction, Sangfor’s cutting-edge security solutions deliver a holistic multi-layered protection system against all types of advanced cyber threats.
Frequently Asked Questions
A phishing attack is a type of cyberattack in which attackers create fraudulent but convincing messages to manipulate victims into taking harmful actions. These methods can include clicking malicious links, opening dangerous attachments, or sharing sensitive information like passwords or financial details.
Standard phishing attacks target a broad audience with generic messages, often sent to thousands of recipients at once. In contrast, spear phishing attacks are highly targeted and aimed at specific individuals, organizations, or industries. These attacks use detailed research to create personalized and convincing messages, making them more effective and dangerous.
- Preventing phishing attacks requires a combination of awareness and technical measures:
Always verify sender details and hover over links to check their authenticity.
Use email filtering tools to block suspicious messages.
Educate employees with phishing awareness training and conduct simulated phishing tests to improve their ability to recognize scams.
Enable two-factor authentication (2FA) to add an extra layer of security to your accounts.
Organizations can deploy advanced security solutions to detect and respond to phishing threats:
- Next-generation firewalls (NGFWs): Block malicious links and prevent malware downloads.
- Endpoint detection and response (EDR): Detect and quarantine malware installed via phishing emails.
- Network detection and response (NDR): Monitor and identify suspicious activity within the network, limiting the spread of an attack.
These tools, combined with user training, form a strong defense against phishing threats.
If you suspect or confirm a phishing attack, act quickly to minimize the damage:
- Change passwords: Immediately update passwords for compromised accounts and ensure they are strong and unique.
- Notify relevant parties: Inform your bank, email provider, or IT team to freeze compromised accounts or monitor for suspicious activity.
- Monitor accounts: Regularly review financial statements and account activity for unauthorized transactions.
- Report the incident: Alert the relevant authorities, such as your country’s cybersecurity agency or the organization the phishing email claimed to represent.
- Scan devices: Use trusted antivirus software to remove any malware that may have been installed.
- Place a credit freeze: Contact credit bureaus to restrict access to your credit report, preventing attackers from opening new accounts or loans in your name.





