Coronavirus pandemic has caused many organizations to allow their employees to work from home and some of them are working hybrid mode for critical onsite services or frontliners. Working from home used to be a novelty for many employees and now, remote work has become the norm for many and could become a mainstay for some companies. Besides that, hybrid in-office work also becoming new ways for people to do their daily jobs. (Source: https://www.helpnetsecurity.com/2020/11/02/enterprise-it-security-teams)

This paradigm shift has poses huge cyber security challenges such as new vulnerabilities and cyberattacks surface to both remote and hybrid workers. It is challenging for companies on providing secure work environment. Here are a few recommendations that can assist you in securing your remote and hybrid workers.
1. VPN with a protection policy
While VPN does encrypt traffic from the user and a corporate network, but it does not necessarily stop the threat from accessing and compromising the internal network. A protection policy within a VPN connection will greatly assist to detect any possible threat before it reaches the internal network.
2. Audit and Risk Mitigation
Client audit protection will ensure confidential data from being exfiltrate and any such attempt will be recorded in the logs. Ideally, it should apply to both users who are working remotely and in-office networks.
3. Software Patches
Update and installing patches can also be tricky and tedious especially those devices such as notebook are not connected to the corporate network or authorized sources to receive those patches. For the work security, an organization can enforce policies to ensure all those devices are updated with the latest critical patches before they can allow connecting back to the corporate network.
4. Ability to control application
Employees may not consider company acceptance use policies when working at home or anywhere from the office especially those devices are company assets, which is a threat to work security. For example, employees may allow their children or another person to use a corporate notebook to surf unnecessary websites or even play games. Besides that, some employees may attempt to disable these controls because they are “slowing them down” in certain aspects. Any employees should always make sure these devices are being used according to the company acceptance use policies and more so, not to violate or abuse their company assets. In such cases, securing your remote employees is challenging. An organization can deploy policies and control these important applications from being exit or providing some form of messages to remind their employees about their notebook usage.
5. Ransomware/Malware Protection
Infected documents or drive-by downloads are very common forms of causing these ransomware and malware infection. For example, remote work security compromises when employees unknowingly open a malware-infected document on their corporate notebook at home. Organizations need not only signature-based protection to prevent such incidents happen but more often than not, they also need protection against zero-day malware.
6. Incident Response
Responding to a compromise case can be challenging and most likely those incident response team are also working from home which can make investigating a breach more difficult. For example, an incident response team cannot go to the person's house and perform an incident investigation if any employee device such as a notebook is compromised. What an organization need is pre-incident to assess any possible attack surface and vulnerabilities before the attack occurs. Click here to know more about incident response.

Sangfor Approach
In Sangfor, we take pride in providing the best Cybersecurity solution covering the end-to-end solution. We provide work from home solutions for secure remote work. Our 360 holistic solutions ensure companies and their employees are being well protected not only on-premise standpoint but remote or hybrid workers.
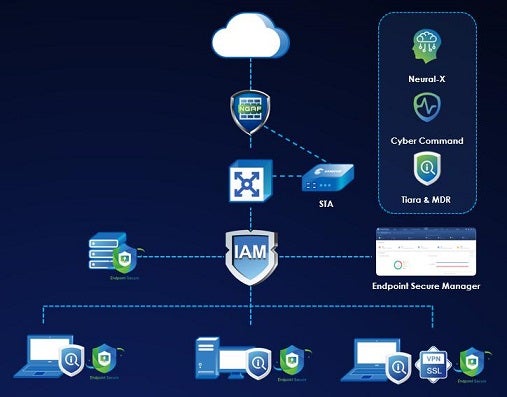
For more info, please visit https://www.sangfor.com/





