
What's the Difference Between REvil and Other Ransomware?
Background of REvil Ransomware:
The REvil (a.k.a. Sodinokibi) ransomware group has been quite active in 2021, the latest attack against a computer giant, encrypting devices and stealing data. In April 2021 REvil was used to invade Taiwanese Apple supplier Quanta, asking for a ransom of US$50 million for the return of Apple Watch design data.
Sangfor FarSight Labs has been tracking the technical evolution and model development of the REvil ransomware group, capturing the current ransomware matrix in this attack. Technical analysis shows that REvil has made improvements to its anti-virus evasion technology, forging of digital signatures for both its matrix and components, staged operation first through file release and then using DLL calls, and passing function codes through multi-layer payload decryption.
Analysts have found that the ransomware attack files have some differences from previous ransomware attack files,. The directory keywords excluded from encryption no longer contain "tencent files," and "wechat files".
Technical Analysis
The REvil ransomware virus matrix includes two parts: an EXE file and a DLL file, which are all encapsulated in an executable file named svchost.exe. They have forged digital signatures for all three files, with svchost.exe and MpSvc.dll using the same forgery signature, and MsMpEng.exe forging Microsoft's signature.
Double-click to run the svchost.exe, then the MsMpEng.exe and MpSvc.dll will run looking for resources:
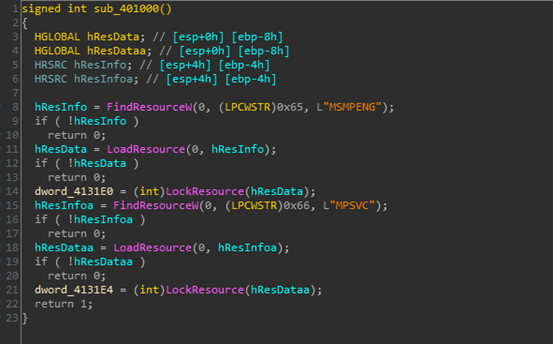
The two files are placed into the temp directory, then cmd.exe is run using the /c parameter to execute MsMpEng.exe in the background:
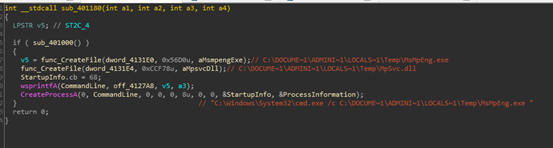
MsMpEng.exe itself is not malicious. It just loads the exported function ServiceCrtMain() in MpSvc.dll:
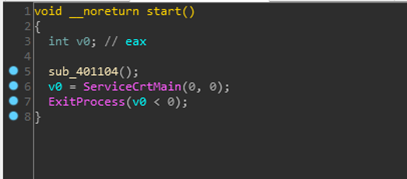
After decrypting the two layers of payload in MpSvc.dll, it starts to execute malicious functions. First, it decrypts the required character resource collection from the memory:
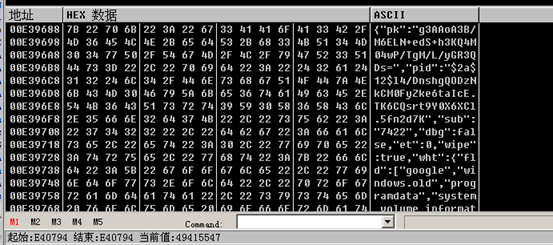
You can see the x4WHjRs value of the registry key BlackLivesMatter under HKEY_LOCAL_MACHINE\SOFTWARE and HKEY_LOCAL_USER\SOFTWARE. If the value does not exist, a 7-bit encrypted suffix is generated, the key value will be created later, and the value will be set as the encrypted suffix:
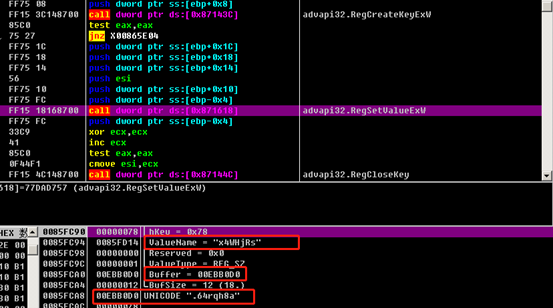
Basic host information is collected, including username, host name, disk type, and the values of the following registry keys:
hKey = HKEY_LOCAL_MACHINE
Subkey = "SYSTEM\CurrentControlSet\services\Tcpip\Parameters"
ValueName = "Domain"
hKey = HKEY_CURRENT_USER
Subkey = "Control Panel\International"
ValueName = "LocaleName"
hKey = HKEY_LOCAL_MACHINE
Subkey = "SOFTWARE\Microsoft\Windows NT\CurrentVersion"
ValueName = "productName"
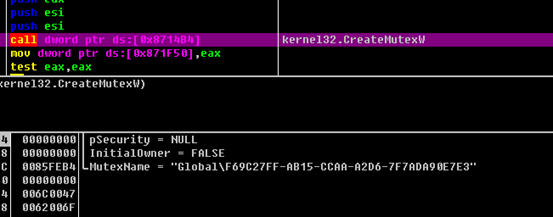
A mutex is created to prevent repeated execution:
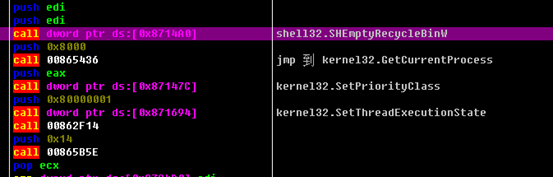
The SHEmptyRecycleBinW function empties the recycle bin, and SetThreadExecutionState is used to prevent the host from entering the sleep mode:
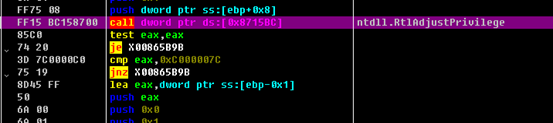
REvil then increases the permissions of its own processes:
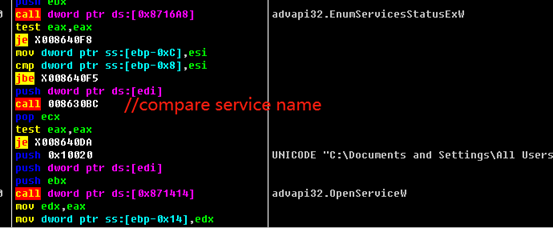
Services are enumerated and checked whether a service name is in the following list, deleting the service if it is included in the list:
"svc": ["sophos”, “svc$", "sql", "mepocs", "vss", "backupбмукшефы", "veeam", "memtas"]
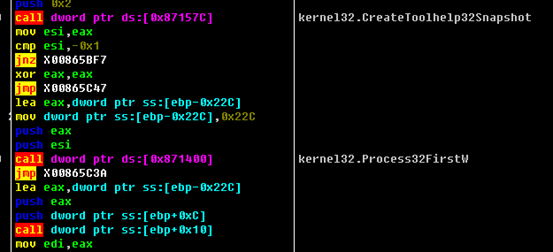
Processes are then listed to see if the following processes exist, and terminated them if they do exist:
"prc":["allegro", "steam", "xtop", "ocssd", "xfssvccon", "onenote", "isqlplussvc", "msaccess", "powerpnt", "cad", "sqbcoreservice", "thunderbird", "oracle", "infopath", "dbeng50", "pro_comm_msg", "agntsvc", "thebat", "firefox", "ocautoupds", "winword", "synctime", "tbirdconfig", "mspub", "visio", "sql", "ocomm", "orcad", "mydesktopservice", "dbsnmp", "outlook", "cadence", "excel", "wordpad", "creoagent", "encsvc", "mydesktopqos"]
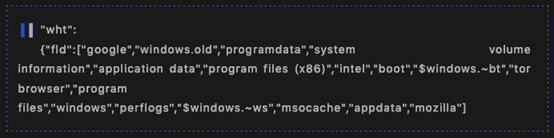
The files are encrypted by traversing all directories, with the directories shown below excluded:
The following files are excluded:
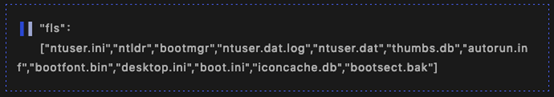
The following suffixes are excluded:
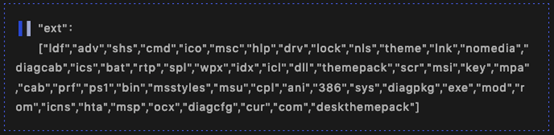
A ransom information txt file is created in each directory:
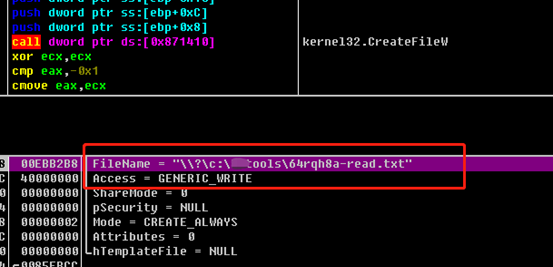
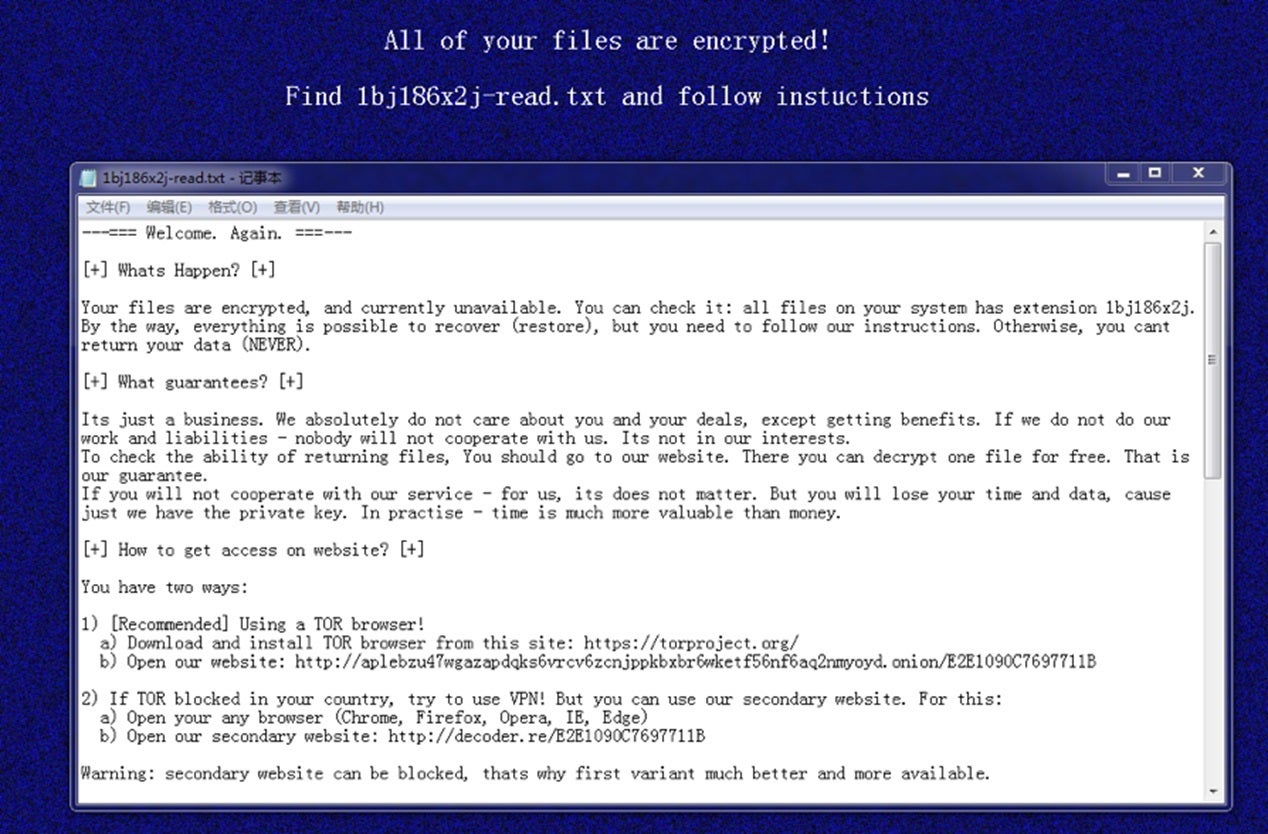
After encryption is completed, the host desktop background is changed to the iconic blue background with a message stating the ransomware attack occurred and name of the ransom note:
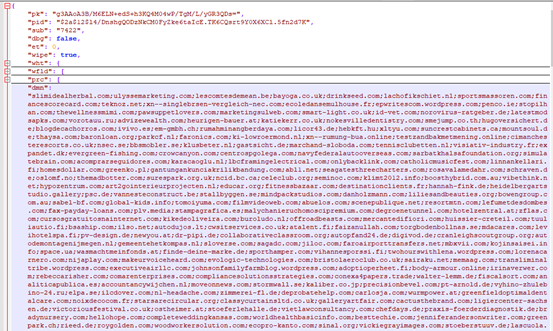
If the NET field is configured as “True“ (default is false), basic information about the victim host and the generated Key will be sent to the C&C server. The domain name configuration contains 1229 characters:
Ransomware Prevention Best Practices
- Set up access permissions on important data files and disable any unnecessary file sharing functions.
- Regularly perform non-local backups.
- Please set a strong host password and avoid using the same password on multiple devices. Check out our article on 8 Simple Tips for Secure Password Practices published on World Password Day 2021
- Do not directly map ports like 3389 to external networks to prevent brute force cracking attacks.
- Do not open any unknown email, web link or software.
- Only download and install software from official websites with valid SSL certificates. If the downloaded file type does not match the icon, scan using AV software.
- Regularly scan for system vulnerabilities and download patches to update the system.
Sangfor Ransomware Security Products & Solutions
- Sangfor provides free anti-virus tools for users. You can download the following tools for detection of viruses below:
- 64-bit system download link: https://page.sangfor.com/anti-bot-tool
- 32-bit system download link: https://page.sangfor.com/anti-bot-tool
- Sangfor Incident Response, Next-Generation Firewall (NGAF), and Endpoint Secure users should upgrade their software to the latest version and connect to Neural-X using the cloud inspection services to detect and defend against new threats
- Sangfor's security products integrate with Sangfor Engine Zero AI based malware detection engine, using its innovative analysis capabilities to accurately detect and defend against unknown malware.
- Sangfor Security Services help users quickly improve their security posture. Security services include security device policy inspection, security threat inspection, and related vulnerability inspection to ensure that risks are detected, and security strategies are updated in a timely manner.





